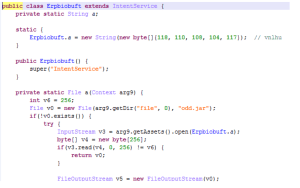
Take a good look at this find in Google Play. It goes by the name Super Free Music Player and has so far attracted between 5,000 and 10,000 downloads:
Now that you’ve had a good look, take our advice and don’t download it. It’s malware.
According to SophosLabs researcher Rowland Yu, the application was uploaded to Google Play on March 31, and uses sophisticated techniques formerly found in BrainTest malware to bypass detection by Google and security researchers. Those techniques include:
- Use of time bombs
- Domain and/or IP mapping
- Use of dynamic code loading and use of reflection
- Use of multiple layers
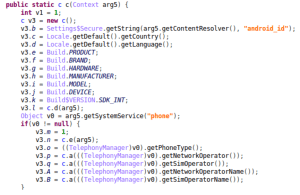
The malware is able to download additional payloads from remote websites and upload device information, including installed applications and the country, language, manufacture, model, SDK version, and so on, Yu said.
- Related article: SophosLabs report examines Top 10 Android malware
Check Point discovered BrainTest on a Nexus 5 smartphone in 2015. It used multiple techniques to avoid Google Play malware detection and to maintain persistency on infected devices. Google Play removed it, but attackers simply repurposed it, Yu said, adding:
It came back to Google Play as Super Free Music Player and attracted 5,000 – 10,000 Downloads. Sophos has detected them as Andr/Axent-DS.
Technical analysis
SophosLabs has identified the following characteristics of Super Free Music Player:
- The dropper downloaded from Google Play is named com.superfreemusic.songapp.
- The payload is decrypted and planted on Android devices by the dropper.
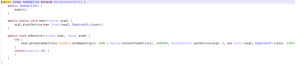
First, the dropper starts a service called com.hole.content.Erpbiobuft to decrypt and drop the payload. It will continues running this service every hour:
It decrypts and drops the payload:
It then continues running this service every hour. The dropper then uses dynamic code and reflection to load the payload method (com.fb.content.core.enter):
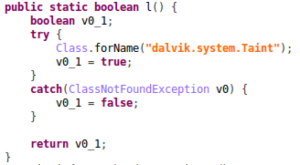
To avoid detection from Google Play, the payload will verify if a device is an emulator by checking several properties such as the emulator phone number (15555215554, 15555215556…) and specific strings such as (/system/lib/libc_malloc_debug_qemu.so, /sys/qemu_trace …). Moreover, it is able to check if a popular Android research sandbox, TaintDroid, is used. Also, another time bomb is used to avoid detection.
Com.fb.content.core. is entered into the payload:
A string checklist for the Android emulator is added:
It then checks to see if an Android research sandbox or TaintDroid exists:
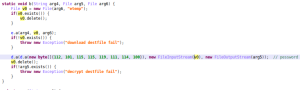
The second time bomb will wait for eight hours to start the malicious payload. The malicious app is able to download more encrypted payloads from remote websites:
It will then submit a list of device info to hxxp://s1.deepcups.com/s2/ and hxxp://s1.deepcups.com/s1/:
Defensive measures
As we mentioned above, SophosLabs has identified this as Andr/Axent-DS and protected Sophos users against it.
Our advice to non-Sophos customers is not to download this app if you see it in Google Play. We’ve told Google Play about our discovery.
The continued onslaught of malicious Android apps demonstrates the need to use an Android anti-virus such as our free Sophos Mobile Security for Android.
By blocking the install of malicious and unwanted apps, even if they come from Google Play, you can spare yourself lots of trouble.


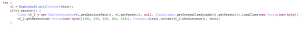


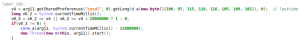
Mahhn
Any other (non-google) site that constantly hosted hundreds of malware apps would be flagged as malicious. It’s time to call the Google Play Store what it is, a malware distribution site.
SubSurge
Both app stores let one slip by now and then because of obfuscation techniques such as those described above. Both Google and Apple have been critiqued for needing a more thorough vetting process for apps, but where there is human factor, there is always vulnerability. No, the Google Play Store is not a “malware distribution site” by any stretch of the imagination, as 99.999% of the software it hosts is harmless. The iTunes App store is in the same boat, by that definition; and you may as well call any website out there the same, for the odd malvertising campaign that slips through… or the whole Internet if we’re painting things with a broad stroke. If you want a device that will never, ever get a bad app, find yourself a flip phone and call it a day.
Mahhn
“let one slip by now and then” It’s actually several hundred+ a year. From another story “Over 400 instances of Dresscode malware found on Google Play” that was from only one type of malware in one year. It’s nice that they want to have a place for safe software, but it’s not good enough. Another site says: “23 of the top 500 Google Play Apps considered to be malware”
Clearly their vetting process is not adequate. If people don’t pressure them to do better vetting, it will continue to be the site that gets more Android user infected than any other app site. I won’t criticize people for wanting all kinds of cool software to get the most of their phone, should we criticize them for trusting google? or maybe google should put a disclaimer that all the software not coded by them should not be trusted? I don’t know. But there needs to be better vetting. It’s not about what I want (flip phone is fine though thank you :) ) its about – if you’re advertising that you are a safe place to get software, you should be.