Successful ransomware families including CryptoWall, TeslaCrypt and Locky encrypt the data files on your hard drive and require you to pay a ransom to get the key to decrypt them.
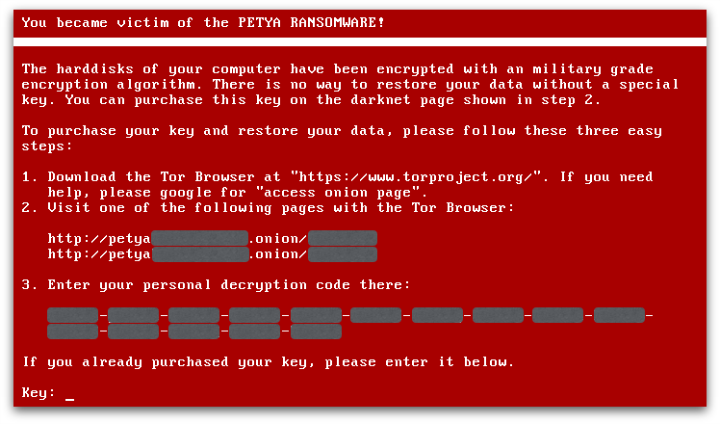
But the Petya ransomware, which we wrote about recently, is somewhat different.
Petya leaves your files alone, but scrambles the Master File Table (MFT) of your C: drive so your computer can’t boot up Windows at all.
The bad news is, normally, the ransomware crooks do a good enough job with the cryptographic parts of the malware to make it all but impossible to break the encryption – and unless you have backups, you have little choice but to pay the ransom if you want your files back.
The good news is that you probably won’t get hit by Petya – this ransomware is pretty rare, according to SophosLabs statistics – but if you are one of the unlucky Petya victims, there’s good news for you, too.
You may not need to pay the ransom at all, because this time, the malware authors weren’t very careful and it’s possible to crack the encryption.
A researcher by the name of “Leo Stone” has figured out how to crack Petya’s encryption, and created a free online “Petya pay no ransom” tool you can use to generate the encryption key without paying.
Petya victims just need to enter some data strings from the affected disk into the online tool, and it uses an algorithm to generate the key, a process described in a GitHub post by leo-stone.
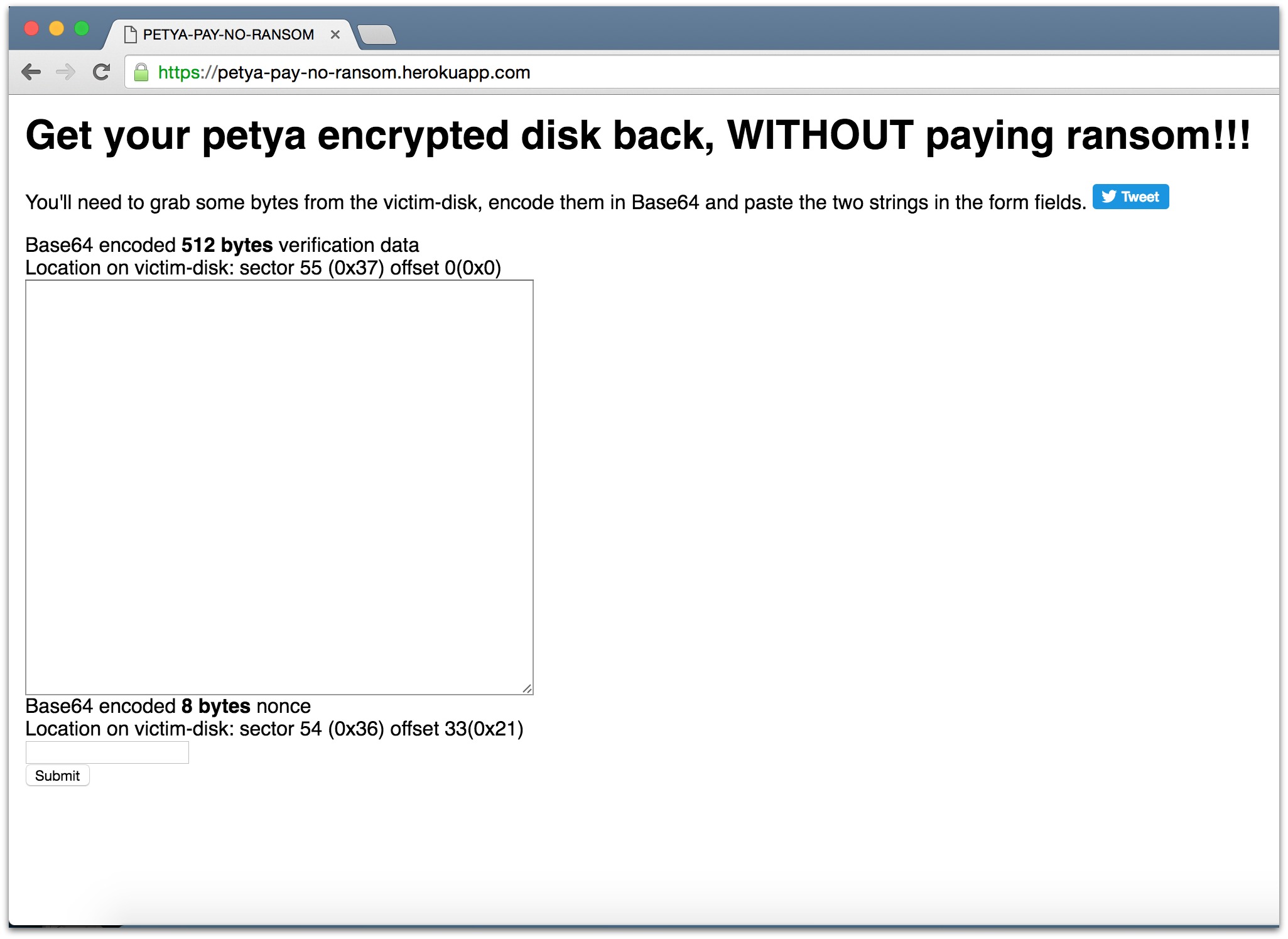
You’ll need to attach your infected hard drive to another working computer to extract the necessary data (BleepingComputer has a step-by-step guide for the whole process).
After you enter the data in the tool, it spits out your key, which you next need to enter into the Petya ransom page on your infected computer.
How to prevent ransomware
It’s good news that Petya was relatively easy to crack, but the truth is, today’s ransomware mostly avoids this kind of mistake.
Prevention is far better than a cure, so here are some tips you can use to protect yourself against ransomware.
1. Back up your files regularly and keep a recent backup off-site.
Backups can protect your data against more than just ransomware: theft, fire, flood or accidental deletion all have the same effect. Make sure you encrypt the backed up data so only you can restore it.
2. Don’t enable macros.
A lot of ransomware is distributed in Office documents that trick you into enabling macros. Microsoft has just released a new tool in Office 2016 that can limit the functionality of macros by preventing you from enabling them on documents downloaded from the internet.
3. Consider using Microsoft Office viewers.
They allow you to see what a Word or Excel document looks like without macros. The viewers don’t support macros so you can’t enable them by mistake, either.
4. Be very careful about opening unsolicited attachments.
Most Windows ransomware in recent months has been embedded in documents distributed as email attachments.
5. Don’t give yourself more login power than necessary.
Don’t stay logged in as an administrator any longer than necessary. Avoid browsing, opening documents or other regular work activities while logged in as administrator.
6. Patch, patch, patch.
Malware often relies on bugs in software and applications. When you apply security patches, you give the cybercriminals fewer options for infecting you with ransomware.
7. Train and retrain employees in your business.
Your users can be your weakest link if you don’t teach them how to avoid booby-trapped documents and malicious emails.
8. Segment the company network.
Separate functional areas with a firewall, e.g., the client and server networks, so systems and services can only be accessed if really necessary.
Learn more about how to prevent ransomware
Sophos experts have created a free guide explaining How to stay protected against ransomware.
Image of broken chain courtesy of Shutterstock.com.


brett reeve
Seen this plenty in Australia. i run a local IT repairer and deal with this ransom ware constantly. Unfortunately only 1 client had a backup that was salvageable. all the others, full wipe and re installation. Ive seen it target backup drives sometimes also
SubSurge
Decryption tools are also available for Locker, TorLocker, TeslaCrypt, Rakhni, Coinvault, Bitcryptor, Linux.Encoder.1, DecryptorMax/CryptInfinite, Radamant, some versions of CryptoLocker, Hydracrypt, Umbrecrypt, and the new Jigsaw ransomware (which allegedly deletes files every hour you delay payment and the remainder after 72 hours – in addition to wiping 1,000 files when you attempt to reboot or kill the process). Not all heroes wear capes, but many wear white hats!
Ritesh
My files are encrypted by cerber3 ramsonware can you please give me procedure to decrypt files.