Some dark web sites are unwittingly giving away their secret locations thanks to a basic configuration mistake that’s been cropping up on regular websites for years.
Dark web sites (known as hidden services or .onion sites) use the sophisticated, multi-layered encryption of the Tor network to hide themselves and the source of their traffic but actually run on the same plain vanilla web server software that normal web sites do.
The most widely used web server software of all is Apache which has been top dog since 1995 and still commands a market share approaching 40%.
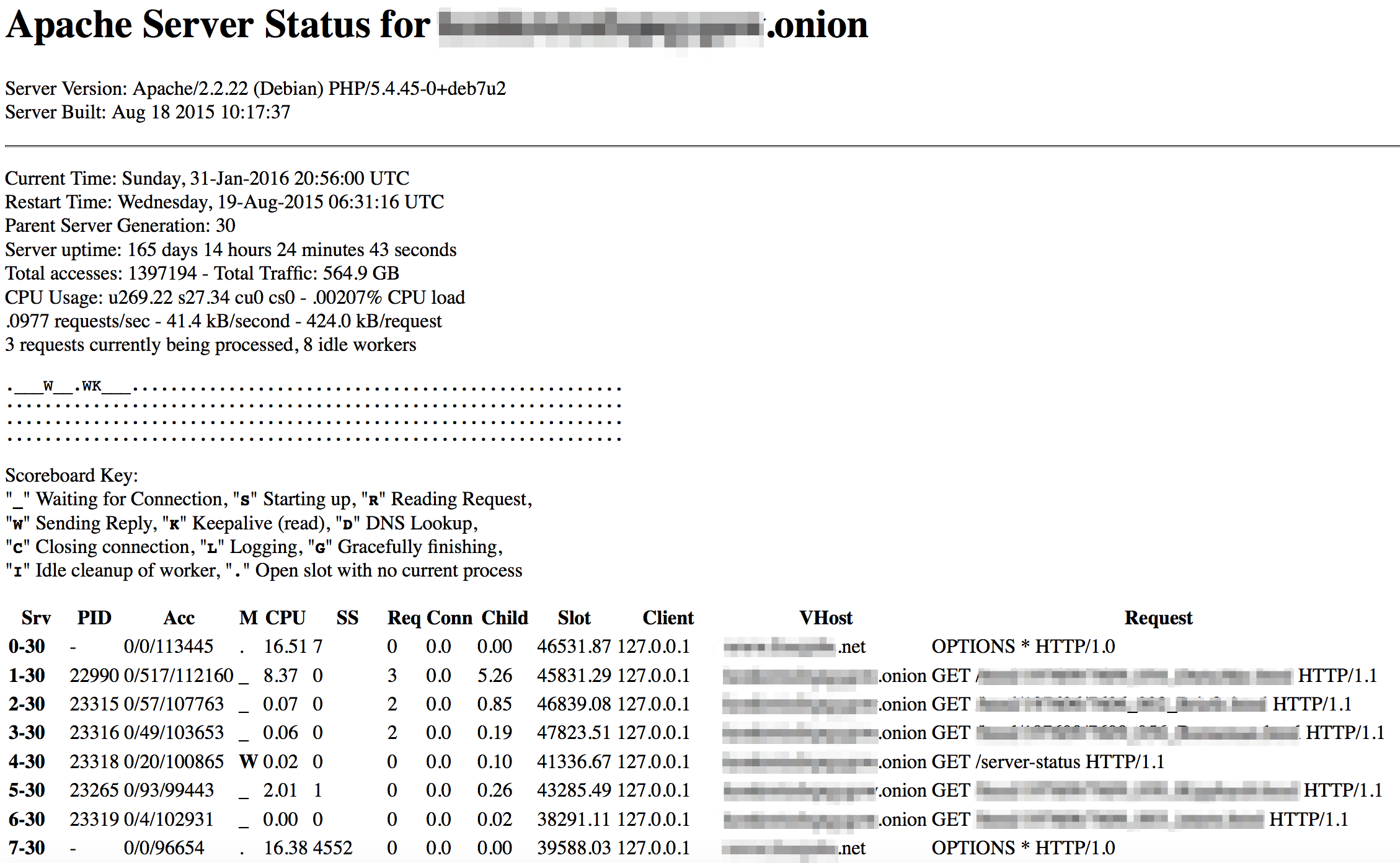
Apache comes with an optional module, mod_status, that sets up a server status page displaying useful information about the server, such as the number of requests per second, CPU usage and the most recent HTTP requests the server received – requests that can contain sensitive information.
Because they can leak sensitive information, server status pages are supposed to be for administrators’ eyes only, but they can end up visible to the outside world if the a web server isn’t set up correctly.
I first wrote about the problem in 2012 after an investigation by HD Moore revealed a number of popular websites were leaking passwords via their server status pages.
Back then it was a problem for the regular web, but with the same server software and the same administrators setting up camp on the dark web the same problems are occurring there too and, thanks to the way Tor works, it’s probably happening much more often.
As Facebook’s Alec Muffet explains, Apache’s out-of-the-box configuration is designed to hide the server-status page, but has the unintended consequence of exposing it on the dark web.
On most distributions, Apache ships with a handy feature called mod_status enabled … For security reasons, it’s only accessible from localhost by default.
This seems fairly reasonable, until you realize the Tor daemon runs on localhost. Consequently, any hidden service using Apache’s default config has /server-status exposed to the world.
Not only is the problem likely to be more common on the dark web, the consequences for users and site owners could be more serious too.
The HTTP requests displayed on server status pages include details about each page (URL path and query string) that the server has been asked for – data that would be hidden from hackers snooping on-the-wire.
As HD Moore found in 2012, those page requests can occasionally deliver the hacker’s jackpot of passwords and session IDs, although that’s rare.
More commonly they leak smaller and less significant bits of information about what pages have been viewed, what files have been downloaded and what actions have been performed.
In late 2015, Muffet found a dark web search engine with a leaky status page that showed what people were searching for and, this being the dark web, some of the searches were, well, pretty dark.
Amongst the searches that survived his redactions for distastefulness was the question “how to get rid of 2 bodys”.
If a malicious actor had found that page instead of Muffet they could have used it to assemble a trove of search data and, as we learned from the 2006 AOL search data leak, that can be enough Big Data to start unmasking people.
You might think that would take a lot of luck, time and effort, and you’d be right, but nobody could accuse the agencies who’ve taken on Tor of lacking patience or resources.
And it gets worse.
Exposed server status pages are a potential threat to users, but under some circumstances, with a bit of luck and no effort at all, they can completely unravel the protection that Tor provides to hidden websites.
The screen shot below shows the server status page for a European, left-wing magazine that I found on Tor. The page reveals that the magazine, a .onion site, is sharing a server with a completely unrelated .net job website.
The job site isn’t on Tor so its location is public and can be discovered in seconds.
Find the job site’s location and you’ve found the magazine too.
If you’re running a .onion site with a visible server-status page then you might want to turn off mod_status entirely or familiarise yourself more closely with Apache’s numerous access control options.
Image of Page curl, conceptual courtesy of Shutterstock.com.

David Pottage
Just to play devil’s advocate here, but in the case of the left wing magazine, it is possible that the web site owners are running it as a .onion site to protect their readership, and not because they want to stay anonymous themselves.
You wrote an article a few weeks ago about how facebook can now be accessed via facebookcorewwwi.onion but clearly Facebook are not trying to hide themselves, they are just offering protection to their users who need to connect anonymously.
Of course, there are plenty of other reasons why you might not want to make your server stats public, (such as not giving the stats to competitors) and the majority of darknet operators will want to hide their identity.
Mark Stockley
I suspect that you’re right about the magazine, I don’t think they’re trying too hard to hide themselves, I was simply looking for a live site to illustrate the point and I didn’t have to spend long looking.
Wilderness
Until software companies put security higher on their priority list regarding default settings like this, these things will keep happening…not that I mind it happening to illegal websites.
Mex5150
Every now and again, I’ll have a scan through and see which tor sites still have mod_status enabled. It’s not as bad as it used to be, but there is still a surprising number that still leak this info (including a popular webmail service I noticed a few weeks ago!)