I’m on the road at the moment, staying in a business hotel with three pleasant surprises.
There’s an inexpensive restaurant with fantastic pizzas, an amazing vista, and a generous free Wi-Fi allowance. (Perhaps that’s four surprises.)
None of those spongy, rubbery pseudopizzas with thick bases like stale loaves; no room view into the back of a haulage yard; and none of that “200MB for $20 network access” that you find in some parts of the world.
FAST FREE WI-FI
Fast, free Wi-Fi sounds handy, and it is, but we’ve written about the potential problems with open Wi-Fi hotspots several times before.
Some of the risks you face are:
- The hotspot could be run by anyone, and there’s almost no way of telling who that might be.
- Anyone in the vicinity, whether they’re on the network or not, can “sniff” (eavesdrop on) and record all your network traffic.
- Your DNS requests, which turn server names into network numbers, are visible to anyone, so even if you subsequently use secure HTTPS connections only, the services you are using are nevertheless revealed.
- The hotspot can send you bogus DNS replies, redirecting you to imposter servers, blocking your access to security updates, and more.
USING A VPN
One handy countermeasure is to use a VPN, short for Virtual Private Network.
That’s where you get your computer to encrypt all your network data before it leaves your laptop or phone, and send the scrambled stream of data back to your own network.
When the scrambled data is safely back on home turf, it is decrypted and sent out onto the internet just as if you were at home, effectively sidestepping the hotspot and its numerous risks.
Of course, many free Wi-Fi networks make you jump through some sort of simple authentication process first, directing you to what’s called a captive portal – a special web page that pops up in place of the site you’re trying to visit.
Captive portals may ask you to accept various terms and conditions, show you a few ads, or ask you for some sort of identifier to track your usage.
The latter is common in hotels, often to differentiate between paying guests, day visitors attending a conference, and unentitled passers-by.
In other words, even if you want to use a VPN, you typically need to spend a short while online with your network shields down, until you can get past the captive portal.
Only then will the hotspot let your network traffic out into the real world so your VPN can call home.
SHIELDS DOWN
Here’s what happened in my hotel during my brief “shields down” period:
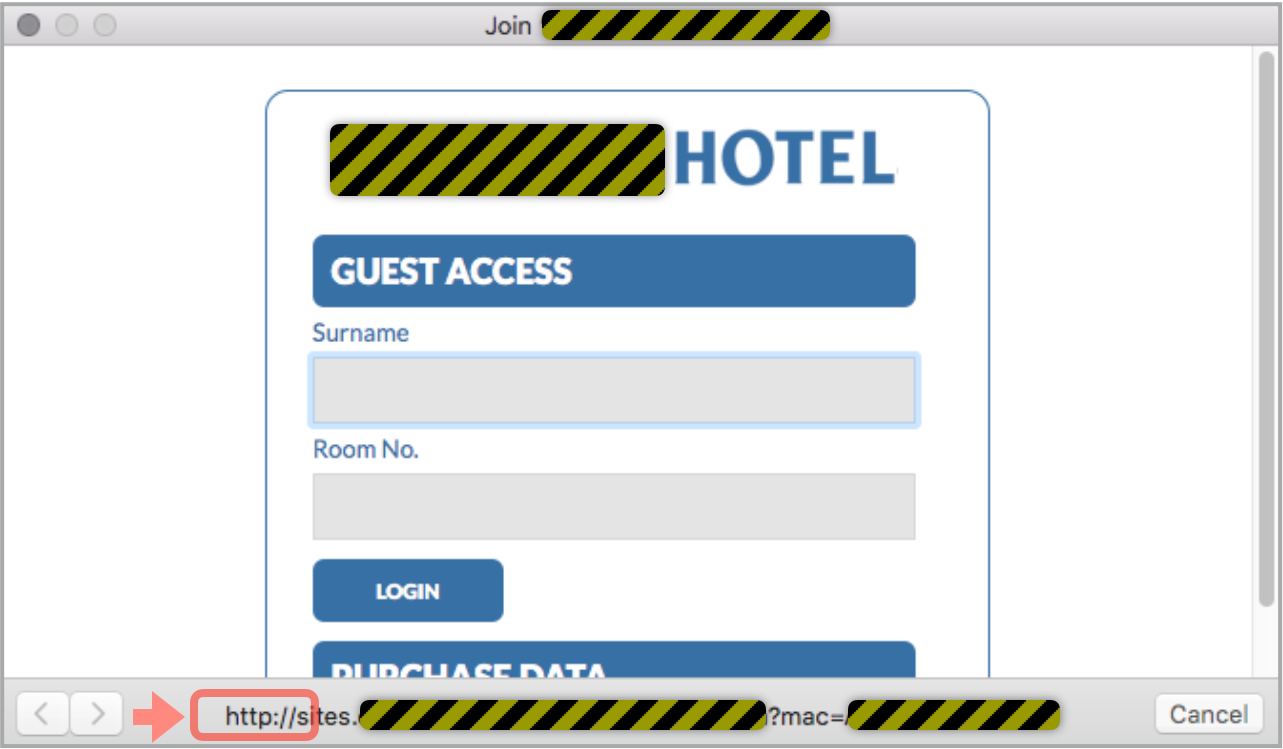
I’m sure you can spot the problem here.
To activate my connection, the hotel wants to validate that I’m a guest, so it uses exactly the same information that it might do in the poolside bar or when signing the bill in the pizza restaurant: name and room number.
Room keys don’t have numbers on them, so this is a simple, customer-friendly and reasonably satisfactory way of regulating your room charges.
Except that in this case, the hotel’s hotspot service is run by an external company whose logon portal expects you to hand over your name and room number over an unencrypted HTTP connection.
As a result, any nearby computer running a network sniffer (I used Wireshark) can read those fields out of the ether:
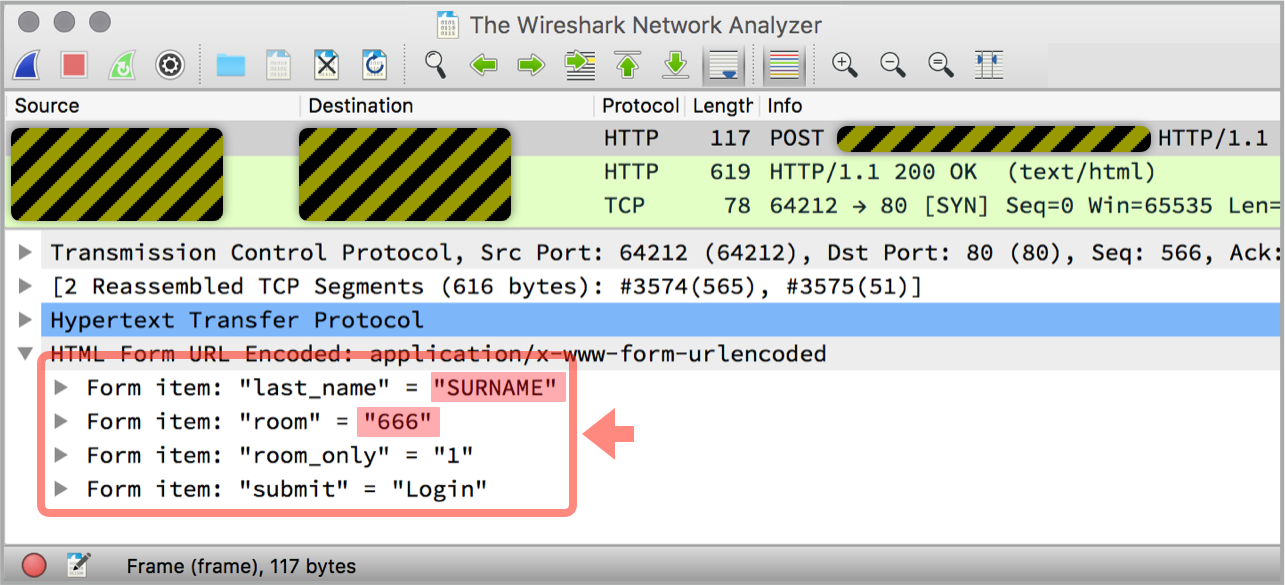
You have to tell the truth, too, because making up an answer for safety’s sake won’t work:
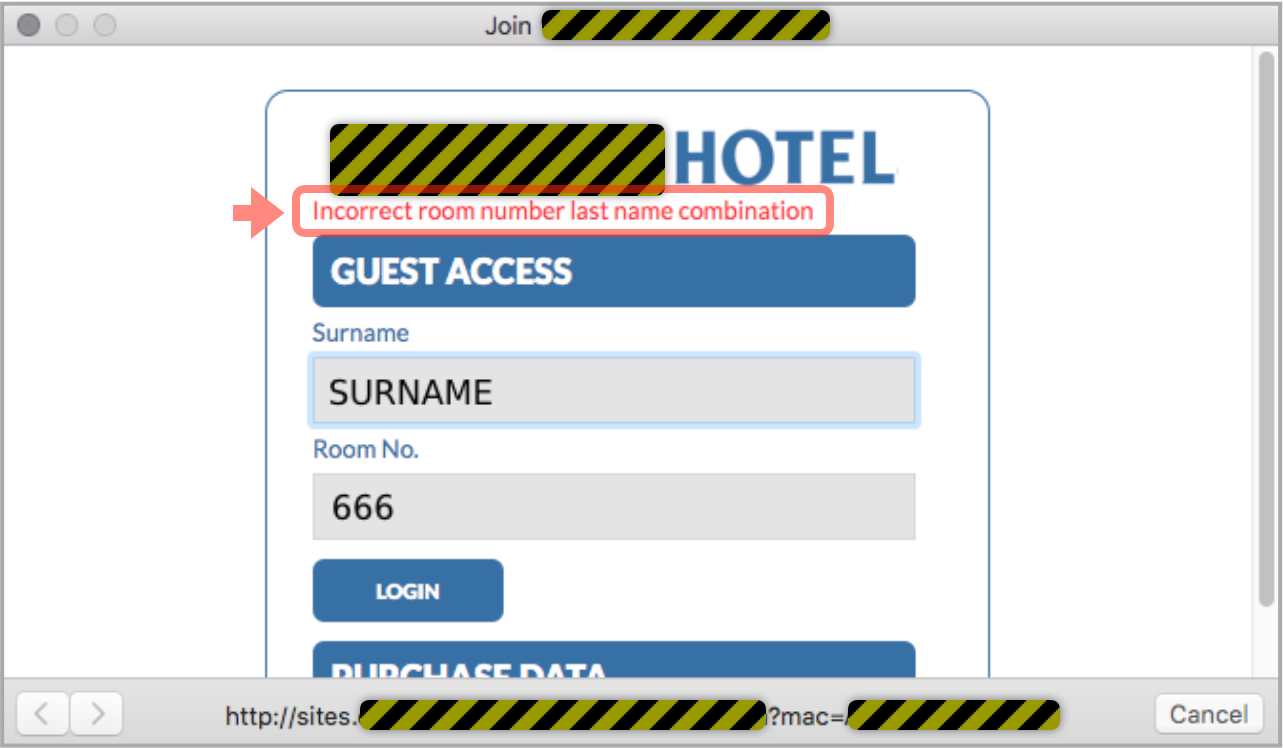
IF IN DOUBT, DON’T GIVE IT OUT
When I checked in to the hotel, I wasn’t asked if I wanted to make use of the free Wi-Fi service, nor whether I consented to having the details of my stay shared in some way with the Wi-Fi portal company for Wi-Fi validation purposes.
If I’d known, I’d have declined, on the principle of “if in doubt, don’t give it out“.
In the end, I used my trusty fallback: a pre-paid mobile phone SIM with enough inexpensive data loaded on it to tide me over, with my phone acting as my very own hotspot.
At least in the USA, you’re always able to do that these days, following a court ruling that hotels aren’t allowed to use technological tricks to stop you using your own hotspot.

tartanrose
Thank you for your timely and helpful article. Some good hints.
I’m seriously envious of the sound of your hotel………..and………given that it’s just about 1am AEDST, I suddenly realise I haven’t eaten much dinner and really like the sound of that pizza!
Nothing like that in the kitchen here………….I don’t think toast and vegemite will cut it, compared to your pizza.
Loving all these holiday safety articles and reminders.
Anonymous
I managed to lock myself out of my hotel room last week. What did they ask me for before handing me a new key? Yep, last name and room number. Nothing more!
Paul Ducklin
That’s bad. I’ve been in hotel where I left my key and my ID in the room, and they insisted on sending a security guard up with the new key, who then verified my ID in the room. I was pleasantly surprised at how they got both service and security in great balance.
David Bennett
So suppose I choose Google.com as the site I want to go to and then as soon as I get online the VPN kicks in. What does the sniffer see that is sensitive? If it is just my room number, that isn’t a worry is it?
Anonymous
>staying in a business hotel
Do they have a computer for guest use? If so, go sit at it for five minutes, then go ask the front desk person if they will install Adobe Reader for you, so you can look at a PDF (or something similar.) Every time I’ve done that I’ve walked away with a post-it note with the manager’s password written on it.
Anonymous
Thank you. I will remember this. Will you also have an article about the hotel keys? I have learned that when you check out to take your key card with you. The keycard can and sometimes contains your credit card information. If you don’t take it with you and dispose of it properly anyone can read the encrypted information contained on it.
Merry Christmas.
Paul Ducklin
I don’t think that any magstripe hotel keys contain your credit card number. There’s no need for them to do so – though it was a popular urban myth a few years ago.
We could revisit that story…though many hotel locks are going RFID/NFC these days.