It’s Week 4 of Cybersecurity Awareness Month (CSAM), and this week’s #CyberAware theme is Your Evolving Digital Life.
As the CSAM organisers put it, the idea is to highlight:
The "smart world" we live in and the importance of educating all citizens on cybersecurity as more and more of the devices we use – from phones and tablets to homes and medical devices – become connected to the internet.
That means, of course, the so-called Internet of Things (IoT), and includes not just serious devices such as home thermostats and drug pumps…
…but also groovy stuff stuff like light bulbs and kettles!
Indeed, as industry hack Darren Pauli of our chums at The Register just reminded us, there’s the iKettle, pictured above.
It’s down to a mere £89.99 this week [2015-10-20T11:53Z].
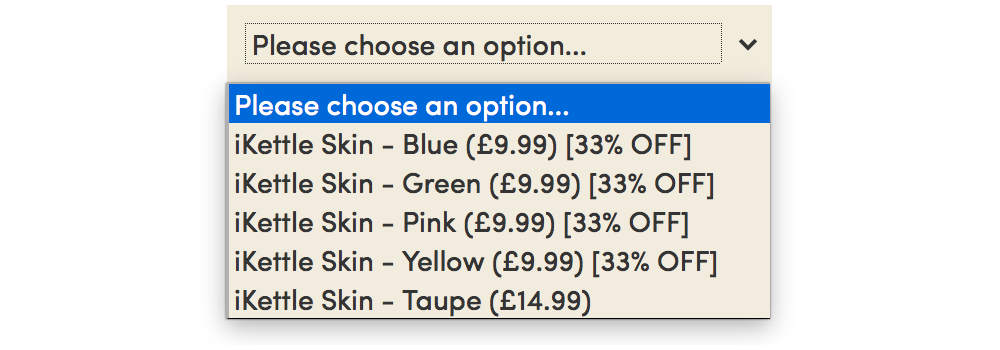
That’s ten quid off, which you could spend on a skin to give you a whole new choice of colours:
(From the pricing, it looks like taupe is the new black, folks. No discount!)
As the advert unashamedly puts it:
✓ Boil your kettle with your smart phone, anywhere in your home. ✓ The most satisfying wake-up call of all time ✓ Welcomes you home by asking if you'd like to pop the kettle on ✓ Match your kettle to your kitchen with the insulating iKettle skins ✓ Embrace laziness and enjoy perfect hot drinks, what's not to like?
The problem in “what’s not to like” is that security seems to have taken second place to coolness, if that’s not a bit of an oxymoron in respect of a kettle.
Indeed, Ken Munro, a UK penetration tester who once persuaded Talking Barbie to say some, well, very un-Barbie-like things, found out earlier this year that the iKettle simply isn’t up to scratch cryptographically.
Munro took up from where a researcher called Mark Cox got to back in 2014 when the iKettle came out.
Greatly simplified, if cybercrooks have you in their sights, your iKettle could help them out tremendously, like this:
1. Find someone who has an iKettle on their network.
2. Stand outside their house or apartment advertising a Wi-Fi network with the same name.
3. Kick the iKettle off its current network and wait for it to connect back…to your network.
A directional antenna should as good as guarantee a stronger signal from your rogue access point.
4. Use telnet on port 23 to connect to the kettle.
This gives you what is effectively a serial-line login, because the iKettle uses a Wi-Fi-to-serial interface for remote access.
5. Guess the kettle’s 6-digit PIN using brute force.
Or try 000000, apparently the default if you have used the Android app instead of the iOS one.)
6. Ask the kettle to list its settings.
This apparently includes the Wi-Fi password in plain text.
7. Now join the victim’s real Wi-Fi network.
This lets you take up a attacking position on the inside.
Does it matter?
This can be written off as a far-fetched attack, not least because the crooks would have to know you had an iKettle, and be nearby, and be interested in hacking you.
But that’s the wrong way to think about security.
Firstly, even a few very simple programming changes can avoid a hole like this in the first place.
Secondly, if the crooks have already decided that they are interested in you, then an insecure IoT device is exactly what they are hoping for, even if they have to pay someone else in your area to go and take a sniff.
What to do?
Any of the following would help from a programming point of view:
- Once a Wi-Fi password is set, require it when connecting. This means an imposter network would need to know your Wi-Fi key (which is private) as well as the network name (which is not).
- Use a PIN longer than 6 digits. This PIN is supposed to be supplied by an app when it connects, not typed in by a human. It might as well be 24, 48 or even 64 digits long.
- Avoid telnet altogether. Encrypt your device control communications, so you never have to worry about someone else on the network seeing secret content they shouldn’t.
- Consider some sort of rate limiting on logins. After a reasonable number of incorrect attempts to connect to the device, make the attacker wait. This greatly reduces the effectiveness of brute force attacks.
And if you’re a consumer, keen to acquire and integrate the latest and coolest IoT stuff into your home?
You could start voting with your wallet, starting now, and take a long-term position on being #CyberAware.
Favour vendors who can show they treat security as a first-class problem for any connected device, and who show in their programming that they care.
If security is too expensive for the vendor to build into a consumer product, maybe that vendor is too cheap for you to give any money to in the first place?


Mahhn
Quick call an Exorcist, the tea kettle is alive! no honey, we need a tech, it’s been hacked. Guess we won’t be on the ghost hunter TV show then huh,,,
MossyRock
A great many of these IoT offerings are quite laughable and silly and amount to nothing useful except as playtoys.
I’ll say “no, thanks” to this one… I’ll just walk over from the next room to push the button to turn it on.
Anonymous
Or you could set your wifi network to not broadcast its SSID..
Paul Ducklin
You need to watch this video:
https://nakedsecurity.sophos.com/2013/05/22/busting-wireless-security-myths-video/
If your network can be connected to, its SSID can be recovered. Easily.
tartanrose
It’s far too easy as it is for me to get into Hot Water!
Whereas my new motto is………..Dance like no one’s watching
Encrypt like everyone is………..When it comes to household appliances I’ll stick with the old school stuff.
Thanks for yet another excellent article. I’m just off to put my chain store kettle on.
SizzleBizzle
Leaving the security bit away from my comment…..
So, it boils based on a prompt from a phone app? It’s hardly the next Goblin Teasmaid, is it? The product is complete trash and anyone who buys it should also receive an automated fist which punches them in the face repeatedly every time they use it.
Look forward to news reports of exploding iKettles when the owners forget to put the water in it the night before.
“The most satisfying wake-up call of all time” !!KABOOM!!