Microsoft on Tuesday released 117 patches touching 15 product families. Three of the addressed issues, affecting Configuration Manager, Visual Studio, and Windows, are considered by Microsoft to be of Critical severity. At release time, two of the issues addressed are known to be under exploit in the wild, with eight additional CVEs more likely to be exploited in the next 30 days by the company’s estimation. Three of this month’s issues are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches, the release includes advisory information on four Edge-related CVEs and one related to curl (affecting CBL Mariner and Windows), along with the usual servicing stack updates. We are as always including at the end of this post additional appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
By the numbers
- Total CVEs: 117
- Publicly disclosed: 4
- Exploited detected: 2
- Severity
- Critical: 3
- Important: 110
- Moderate: 3
- Low: 1
- Impact
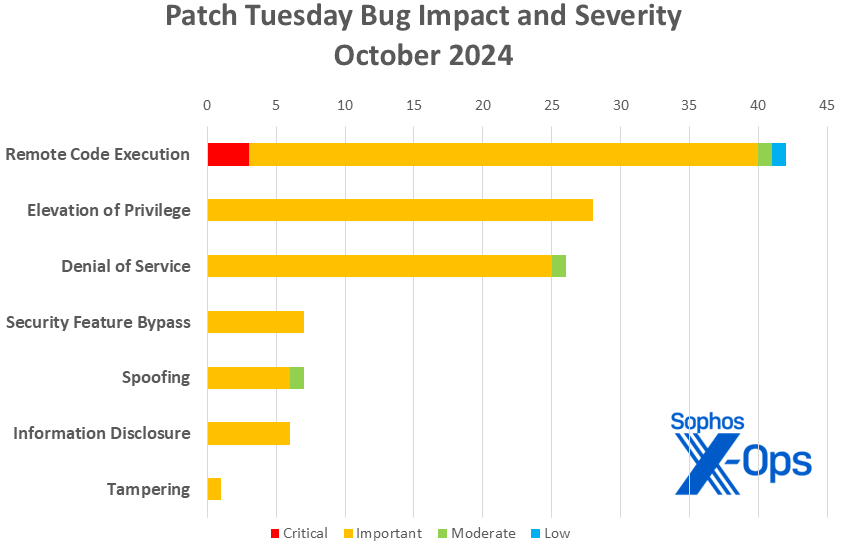
- Remote Code Execution: 42
- Elevation of Privilege: 28
- Denial of Service: 26
- Security Feature Bypass: 7
- Spoofing: 7
- Information Disclosure: 6
- Tampering: 1
- CVSS base score 9.0 or greater: 2
- CVSS base score 8.0 or greater: 25
Figure 1: Denial of service issues make a remarkable showing in this month’s patch collection thanks in part to a large number of Windows Mobile broadband-driver patches; more on that in a moment
Products
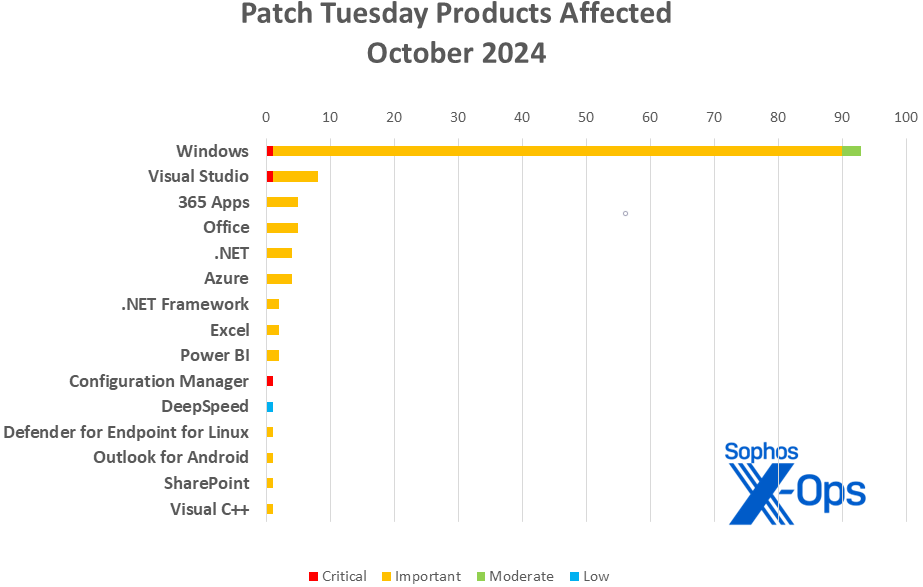
- Windows: 93
- Visual Studio: 8
- 365 Apps: 5
- Office: 5
- .NET: 4
- Azure: 4
- .NET Framework: 2
- Excel: 2
- Power BI: 2
- Configuration Manager: 1
- DeepSpeed: 1
- Defender for Endpoint for Linux: 1
- Outlook for Android: 1
- SharePoint: 1
- Visual C++: 1
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect.
Figure 2: A few rarely seen product families make an appearance in this month’s chart, but Windows rules the roost
Notable October updates
In addition to the issues discussed above, a number of specific items merit attention.
CVE-2024-38124 – Windows Netlogon Elevation of Privilege Vulnerability
CVE-2024-43468 — Microsoft Configuration Manager Remote Code Execution Vulnerability
Both of this month’s CVEs with CVSS base scores of 9.0 or above come with mitigation advice. The Config Manager issue (CVE-2024-43468), the more severe of the two with a 9.8 CVSS, also has special instructions. For the Netlogon issue (CVE-2024-38124), the following mitigations are offered (text courtesy of Microsoft):
- Predictable Naming Conventions: Avoid using predictable naming conventions for domain controllers to prevent attackers from renaming their machines to match the next name to be assigned to a new domain controller.
- Secure Channel Validation: Ensure that the secure channel is validated against more than just the computer name of the machine it was delivered to. This can help prevent attackers from impersonating the domain controller by obtaining the handle and waiting for the appointment to happen.
- Monitor for Renaming Activities: Implement monitoring for any suspicious renaming activities of computers within the network. This can help with early detection and prevention of potential attacks.
- Enhanced Authentication Mechanisms: Consider using enhanced authentication mechanisms that go beyond the current validation methods to ensure the authenticity of the domain controller and the secure channel.
As for the Configuration Manager issue, there are extra steps required (text, again, courtesy of Microsoft):
Customers using a version of Configuration Manager specified in the Security Updates table of this CVE need to install an in-console update to be protected. Guidance for how to install Configuration Manager in-console updates is available here: Install in-console updates for Configuration Manager.
The mitigation guidance for the Configuration Manager issue also recommends that administrators specify an alternate service account, rather than the Computer account; more information is available here.
[15 CVEs] – Windows Mobile Broadband Driver DoS and RCE issues
None of these issues are as concerning as the Critical-severity CVE-2024-38161 mobile broadband driver issue patched back in July, but the sheer volume is remarkable, as is the fact that all of these require physical access (to plug in a USB drive) or proximity (sufficient for radio transmission).
CVE-2024-43485 — .NET and Visual Studio Denial of Service Vulnerability
This Important-severity Denial of Service issue casts its .net rather widely, affecting the platform not only on Windows but on Linux and macOS.
CVE-2024-43497 — DeepSpeed Remote Code Execution Vulnerability
It’s not common for a Low-severity issue to be named in the Patch Tuesday release, but this one’s interesting for another reason – it affects DeepSpeed, Microsoft’s speed-and-scale optimization booster for deep-learning training. (We believe this to be the first-ever Patch Tuesday bug affecting DeepSpeed, as well as the first Microsoft find credited to an AI-specific bug-bounty program.)
CVE-2024-43527 — Windows Kernel Elevation of Privilege Vulnerability
CVE-2024-43571 — Sudo for Windows Spoofing Vulnerability
These two patches are less notable for what they are (though some observers may be startled to see talk of sudo in a Patch Tuesday post) than for what version of Windows they affect. Both of these Important-severity patches affect only Windows 11 24H2, the OS version entering general release this week.
CVE-2024-43573 — Windows MSHTML Platform Spoofing Vulnerability
One of the two vulnerabilities known to be under active exploit in the wild, this Moderate-severity Spoofing issue gets into the Halloween spirit by invoking the ghost of Internet Explorer. Customers who receive Security Only updates are encouraged to apply the IE Cumulative updates to exorcise this vulnerability.
Figure 3: As we enter the last quarter of the year, Denial of Service issues are catapulted into third place on the leaderboard, while the DeepSpeed bug puts a Low-severity patch on the board for the first time in 2024
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-43502 | Exp/2443502-A | Exp/2443502-A |
| CVE-2024-43572 | SID: 2310213; Troj/XML-AA, Troj/PastaLdr-A | SID: 2310213 |
| CVE-2024-43573 | SID: 2310220, 2310222; Exp/2443573-A | SID: 2310220, 2310221 |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of October patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (42 CVEs)
| Critical severity | |
| CVE-2024-43468 | Microsoft Configuration Manager Remote Code Execution Vulnerability |
| CVE-2024-43488 | Visual Studio Code extension for Arduino Remote Code Execution Vulnerability |
| CVE-2024-43582 | Remote Desktop Protocol Server Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-30092 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-38029 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-38212 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38229 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-38261 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38262 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability |
| CVE-2024-38265 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43453 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43480 | Azure Service Fabric for Linux Remote Code Execution Vulnerability |
| CVE-2024-43504 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-43505 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2024-43517 | Microsoft ActiveX Data Objects Remote Code Execution Vulnerability |
| CVE-2024-43518 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43519 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-43523 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43524 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43525 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43526 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43533 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2024-43536 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43543 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43549 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43552 | Windows Shell Remote Code Execution Vulnerability |
| CVE-2024-43564 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43574 | Microsoft Speech Application Programming Interface (SAPI) Remote Code Execution Vulnerability |
| CVE-2024-43576 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-43581 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-43589 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43592 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43593 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43599 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2024-43601 | Visual Studio Code for Linux Remote Code Execution Vulnerability |
| CVE-2024-43607 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43608 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43611 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43615 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-43616 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30092 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-38029 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-38212 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38229 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-38261 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| Moderate Severity | |
| CVE-2024-43572 | Microsoft Management Console Remote Code Execution Vulnerability |
| Low Severity | |
| CVE-2024-43497 | DeepSpeed Remote Code Execution Vulnerability |
Elevation of Privilege (28 CVEs)
| Important severity | |
| CVE-2024-37979 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38097 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-38124 | Windows Netlogon Elevation of Privilege Vulnerability |
| CVE-2024-38129 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-38179 | Azure Stack Hyperconverged Infrastructure (HCI) Elevation of Privilege Vulnerability |
| CVE-2024-43501 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43502 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43503 | Microsoft SharePoint Elevation of Privilege Vulnerability |
| CVE-2024-43509 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43511 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43514 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-43516 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43522 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2024-43527 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43528 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43529 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-43532 | Remote Registry Service Elevation of Privilege Vulnerability |
| CVE-2024-43535 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-43551 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-43553 | NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43556 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43560 | Microsoft Windows Storage Port Driver Elevation of Privilege Vulnerability |
| CVE-2024-43563 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-43570 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43583 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-43590 | Visual C++ Redistributable Installer Elevation of Privilege Vulnerability |
| CVE-2024-43591 | Azure Command Line Integration (CLI) Elevation of Privilege Vulnerability |
| CVE-2024-43604 | Outlook for Android Elevation of Privilege Vulnerability |
Denial of Service (26 CVEs)
| Important severity | |
| CVE-2024-38149 | BranchCache Denial of Service Vulnerability |
| CVE-2024-43483 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43484 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43485 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43506 | BranchCache Denial of Service Vulnerability |
| CVE-2024-43512 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2024-43515 | Internet Small Computer Systems Interface (iSCSI) Denial of Service Vulnerability |
| CVE-2024-43521 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43537 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43538 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43540 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43541 | Microsoft Simple Certificate Enrollment Protocol Denial of Service Vulnerability |
| CVE-2024-43542 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43544 | Microsoft Simple Certificate Enrollment Protocol Denial of Service Vulnerability |
| CVE-2024-43545 | Windows Online Certificate Status Protocol (OCSP) Server Denial of Service Vulnerability |
| CVE-2024-43555 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43557 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43558 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43559 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43561 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43562 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-43565 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-43567 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43575 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43603 | Visual Studio Collector Service Denial of Service Vulnerability |
| Moderate severity | |
| CVE-2024-43520 | Windows Kernel Denial of Service Vulnerability |
Security Feature Bypass (7 CVEs)
| Important severity | |
| CVE-2024-20659 | Windows Hyper-V Security Feature Bypass Vulnerability |
| CVE-2024-37976 | Windows Resume Extensible Firmware Interface Security Feature Bypass Vulnerability |
| CVE-2024-37982 | Windows Resume Extensible Firmware Interface Security Feature Bypass Vulnerability |
| CVE-2024-37983 | Windows Resume Extensible Firmware Interface Security Feature Bypass Vulnerability |
| CVE-2024-43513 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2024-43584 | Windows Scripting Engine Security Feature Bypass Vulnerability |
| CVE-2024-43585 | Code Integrity Guard Security Feature Bypass Vulnerability |
Spoofing (7 CVEs)
| Important severity | |
| CVE-2024-43481 | Power BI Report Server Spoofing Vulnerability |
| CVE-2024-43550 | Windows Secure Channel Spoofing Vulnerability |
| CVE-2024-43571 | Sudo for Windows Spoofing Vulnerability |
| CVE-2024-43609 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-43612 | Power BI Report Server Spoofing Vulnerability |
| CVE-2024-43614 | Microsoft Defender for Endpoint for Linux Spoofing Vulnerability |
| Moderate severity | |
| CVE-2024-43573 | Windows MSHTML Platform Spoofing Vulnerability |
Information Disclosure (6 CVEs)
| Important severity | |
| CVE-2024-43500 | Windows Resilient File System (ReFS) Information Disclosure Vulnerability |
| CVE-2024-43508 | Windows Graphics Component Information Disclosure Vulnerability |
| CVE-2024-43534 | Windows Graphics Component Information Disclosure Vulnerability |
| CVE-2024-43546 | Windows Cryptographic Information Disclosure Vulnerability |
| CVE-2024-43547 | Windows Kerberos Information Disclosure Vulnerability |
| CVE-2024-43554 | Windows Kernel-Mode Driver Information Disclosure Vulnerability |
Tampering (1 CVE)
| Important severity | |
| CVE-2024-43456 | Windows Remote Desktop Services Tampering Vulnerability |
Appendix B: Exploitability
This is a list of the October CVEs judged by Microsoft to be either under exploitation in the wild or more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation detected | |
| CVE-2024-43572 | Microsoft Management Console Remote Code Execution Vulnerability |
| CVE-2024-43573 | Windows MSHTML Platform Spoofing Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2024-43502 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43509 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43556 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43560 | Microsoft Windows Storage Port Driver Elevation of Privilege Vulnerability |
| CVE-2024-43581 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-43583 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-43609 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-43615 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of October’s patches sorted by product family, then sub-sorted by severity. Each list is further listed by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (93 CVEs)
| Critical severity | |
| CVE-2024-43582 | Remote Desktop Protocol Server Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-20659 | Windows Hyper-V Security Feature Bypass Vulnerability |
| CVE-2024-30092 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-37976 | Windows Resume Extensible Firmware Interface Security Feature Bypass Vulnerability |
| CVE-2024-37979 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-37982 | Windows Resume Extensible Firmware Interface Security Feature Bypass Vulnerability |
| CVE-2024-37983 | Windows Resume Extensible Firmware Interface Security Feature Bypass Vulnerability |
| CVE-2024-38029 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-38124 | Windows Netlogon Elevation of Privilege Vulnerability |
| CVE-2024-38129 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-38149 | BranchCache Denial of Service Vulnerability |
| CVE-2024-38212 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38261 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38262 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability |
| CVE-2024-38265 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43453 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43456 | Windows Remote Desktop Services Tampering Vulnerability |
| CVE-2024-43500 | Windows Resilient File System (ReFS) Information Disclosure Vulnerability |
| CVE-2024-43501 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-43502 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43506 | BranchCache Denial of Service Vulnerability |
| CVE-2024-43508 | Windows Graphics Component Information Disclosure Vulnerability |
| CVE-2024-43509 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43511 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43512 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2024-43513 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2024-43514 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-43515 | Internet Small Computer Systems Interface (iSCSI) Denial of Service Vulnerability |
| CVE-2024-43516 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43517 | Microsoft ActiveX Data Objects Remote Code Execution Vulnerability |
| CVE-2024-43518 | Windows Telephony Server Remote Code Execution Vulnerability |
| CVE-2024-43519 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-43521 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43522 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2024-43523 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43524 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43525 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43526 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43527 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43528 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-43529 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-43532 | Remote Registry Service Elevation of Privilege Vulnerability |
| CVE-2024-43533 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2024-43534 | Windows Graphics Component Information Disclosure Vulnerability |
| CVE-2024-43535 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-43536 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43537 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43538 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43540 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43541 | Microsoft Simple Certificate Enrollment Protocol Denial of Service Vulnerability |
| CVE-2024-43542 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43543 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-43544 | Microsoft Simple Certificate Enrollment Protocol Denial of Service Vulnerability |
| CVE-2024-43545 | Windows Online Certificate Status Protocol (OCSP) Server Denial of Service Vulnerability |
| CVE-2024-43546 | Windows Cryptographic Information Disclosure Vulnerability |
| CVE-2024-43547 | Windows Kerberos Information Disclosure Vulnerability |
| CVE-2024-43549 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43550 | Windows Secure Channel Spoofing Vulnerability |
| CVE-2024-43551 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-43552 | Windows Shell Remote Code Execution Vulnerability |
| CVE-2024-43553 | NT OS Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43554 | Windows Kernel-Mode Driver Information Disclosure Vulnerability |
| CVE-2024-43555 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43556 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-43557 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43558 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43559 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43560 | Microsoft Windows Storage Port Driver Elevation of Privilege Vulnerability |
| CVE-2024-43561 | Windows Mobile Broadband Driver Denial of Service Vulnerability |
| CVE-2024-43562 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-43563 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-43564 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43565 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-43567 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43570 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-43571 | Sudo for Windows Spoofing Vulnerability |
| CVE-2024-43574 | Microsoft Speech Application Programming Interface (SAPI) Remote Code Execution Vulnerability |
| CVE-2024-43575 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-43581 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| CVE-2024-43583 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-43584 | Windows Scripting Engine Security Feature Bypass Vulnerability |
| CVE-2024-43585 | Code Integrity Guard Security Feature Bypass Vulnerability |
| CVE-2024-43589 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43592 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43593 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43599 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2024-43607 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43608 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43611 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-43615 | Microsoft OpenSSH for Windows Remote Code Execution Vulnerability |
| Moderate severity | |
| CVE-2024-43520 | Windows Kernel Denial of Service Vulnerability |
| CVE-2024-43572 | Microsoft Management Console Remote Code Execution Vulnerability |
| CVE-2024-43573 | Windows MSHTML Platform Spoofing Vulnerability |
Visual Studio (8 CVEs)
| Critical severity | |
| CVE-2024-43488 | Visual Studio Code extension for Arduino Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-38229 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-43483 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43484 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43485 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43590 | Visual C++ Redistributable Installer Elevation of Privilege Vulnerability |
| CVE-2024-43601 | Visual Studio Code for Linux Remote Code Execution Vulnerability |
| CVE-2024-43603 | Visual Studio Collector Service Denial of Service Vulnerability |
365 Apps (5 CVEs)
| Important severity | |
| CVE-2024-43504 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-43505 | Microsoft Office Visio Remote Code Execution Vulnerability* |
| CVE-2024-43576 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-43609 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-43616 | Microsoft Office Remote Code Execution Vulnerability |
* Despite the name, the information for this CVE does not list any Visio-specific applicability
Office (5 CVEs)
| Important severity | |
| CVE-2024-43504 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-43505 | Microsoft Office Visio Remote Code Execution Vulnerability* |
| CVE-2024-43576 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-43609 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-43616 | Microsoft Office Remote Code Execution Vulnerability |
* Despite the name, the information for this CVE does not list any Visio-specific applicability
.NET (4 CVEs)
| Important severity | |
| CVE-2024-38229 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-43483 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43484 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43485 | .NET and Visual Studio Denial of Service Vulnerability |
Azure (4 CVEs)
| Important severity | |
| CVE-2024-38097 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-38179 | Azure Stack Hyperconverged Infrastructure (HCI) Elevation of Privilege Vulnerability |
| CVE-2024-43591 | Azure Command Line Integration (CLI) Elevation of Privilege Vulnerability |
| CVE-2024-43480 | Azure Service Fabric for Linux Remote Code Execution Vulnerability |
.NET Framework (2 CVEs)
| Important severity | |
| CVE-2024-43483 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
| CVE-2024-43484 | .NET, .NET Framework, and Visual Studio Denial of Service Vulnerability |
Excel (2 CVEs)
| Important severity | |
| CVE-2024-43504 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-43609 | Microsoft Office Spoofing Vulnerability |
Power BI (2 CVEs)
| Important severity | |
| CVE-2024-43481 | Power BI Report Server Spoofing Vulnerability |
| CVE-2024-43612 | Power BI Report Server Spoofing Vulnerability |
Configuration Manager (1 CVE)
| Critical severity | |
| CVE-2024-43468 | Microsoft Configuration Manager Remote Code Execution Vulnerability |
DeepSpeed (1 CVE)
| Low severity | |
| CVE-2024-43497 | DeepSpeed Remote Code Execution Vulnerability |
Defender for Endpoint for Linux (1 CVE)
| Important severity | |
| CVE-2024-43614 | Microsoft Defender for Endpoint for Linux Spoofing Vulnerability |
Outlook for Android (1 CVE)
| Important severity | |
| CVE-2024-43604 | Outlook for Android Elevation of Privilege Vulnerability |
SharePoint (1 CVE)
| Important severity | |
| CVE-2024-43503 | Microsoft SharePoint Elevation of Privilege Vulnerability |
Visual C++ (1 CVE)
| Important severity | |
| CVE-2024-43590 | Visual C++ Redistributable Installer Elevation of Privilege Vulnerability |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the October release.
| ADV990001 | Latest Servicing Stack Updates | |
| CVE-2024-6197 | CBL Mariner, Windows | curl: CVE-2024-6197: freeing stack buffer in utf8asn1str |
| CVE-2024-7025 | Edge | Microsoft Edge Chromium: CVE-2024-7025 Integer overflow in Layout |
| CVE-2024-9369 | Edge | Microsoft Edge Chromium: CVE-2024-9369 Insufficient data validation in Mojo |
| CVE-2024-9370 | Edge | Microsoft Edge Chromium: CVE-2024-9370 Inappropriate implementation in V8 |
| CVE-2024-43566 | Edge | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |