With Sophos Firewall v20 now available for early access, we will be covering some of the top new features every week leading up to launch.
Last week’s article covered the new streamlined management features in Sophos Firewall v20.
This week, we’ll have a look at the latest enhancements to VPN with Sophos Firewall v20.
Check out this quick video overview of the new VPN enhancements…
Here’s an overview of the VPN enhancements in Sophos Firewall v20:

 New secure VPN portal – Sophos Firewall v20 introduces a new hardened and highly secure, containerized self-service VPN portal for remote access users. It provides remote-access self-service options such as downloads for the Sophos Connect Client, VPN configurations, auto-provisioning, and clientless VPN bookmarks.
New secure VPN portal – Sophos Firewall v20 introduces a new hardened and highly secure, containerized self-service VPN portal for remote access users. It provides remote-access self-service options such as downloads for the Sophos Connect Client, VPN configurations, auto-provisioning, and clientless VPN bookmarks.
The new portal is accessed from the previous user portal port of 443 to maintain compatibility and can share a common port with the WAF or SSL VPN.
The legacy user portal is now accessed via port 4443 or 65009 and continues to offer additional services such as other client downloads, email quarantine management, policy overrides, and hotspots.
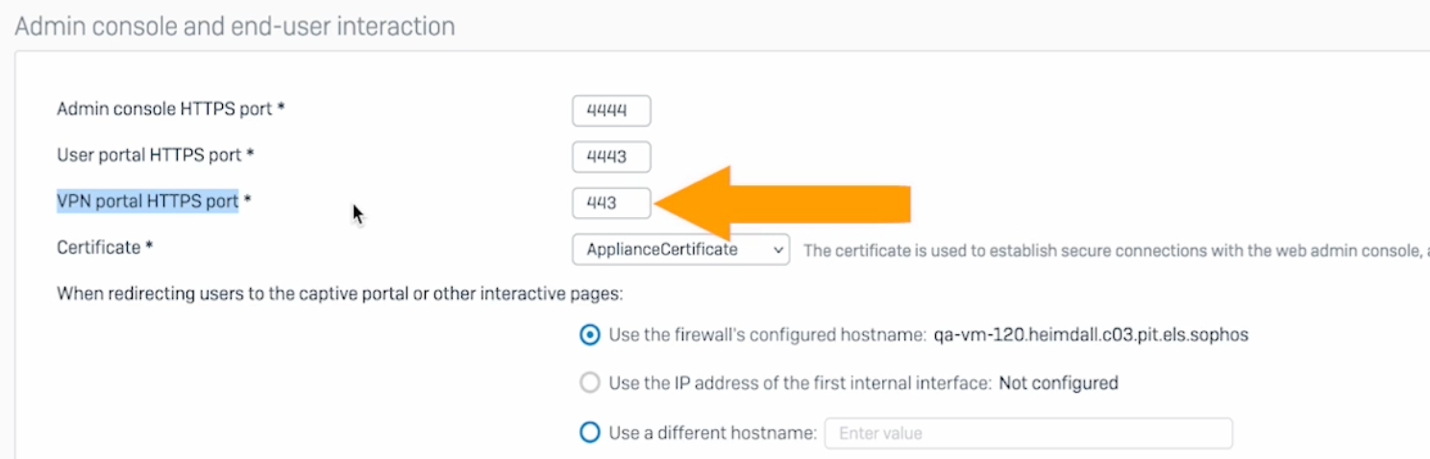
Please note that we strongly recommend that customers DO NOT expose the legacy user portal to the WAN and only use the new VPN portal from outside the firewall.
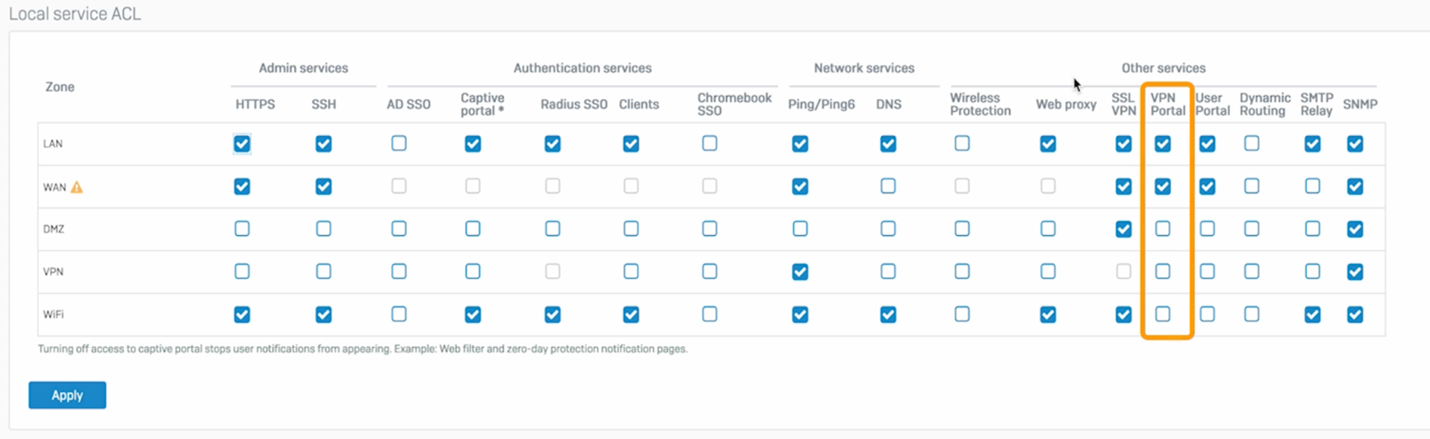
Access control for the new VPN portal is provided alongside the existing user portal:
IPsec connection stateful HA failover – Adds seamless transitioning for RBVPN, PBVPN, and remote access VPN without losing a session in the event of a high-availability failover. It also adds new command-line interface (CLI) options to manage settings.
FQDN host support for SSLVPN – Adds fully qualified domain name (FQDN) host and group support for SSLVPN remote access and site-to-site VPN.
IPsec VPN tunnel status monitoring via SNMP – Adds support for monitoring IPsec VPN tunnel status via SNMP.
Multiple 0.0.0.0 (=*/ ANY) remote gateway support for RBVPN – Eliminates the need for explicit DDNS in distributed multi-location deployments.
Unique PSK support – Now supports unique PSK for VPN connections with the same local and remote gateway connections using IKEv2 policy with unique local and remote IDs.
DH Group 27-30 / RFC6954 – Support for IPsec VPN.
Early Access Program
Please note that the early access program has ended – we expect to announce general availability very soon! A special thanks to all who have participated in the program.