The FBI on Saturday arrested the alleged owner of Deer.io: a Russia-based marketplace for buying and selling credentials for hacked accounts siphoned off of malware-infected computers, victims’ personally identifiable information (PII), as well as financial and corporate data.
According to the arrest warrant, the suspect, Kirill Victorovich Firsov, was arrested at the John F. Kennedy Airport, in New York.
The unsealed indictment claims that Deer.io started up around October 2013 and claims to host over 24,000 active shops. They’re doing brisk business, with sales exceeding $17 million to date, selling hacked accounts for video streaming services like Netflix and Hulu and social media platforms such as Facebook, Twitter and Vkontakte (the Russian equivalent of Facebook). It also sells phony social media accounts, which are popular for crooks running online dating scams.
Court documents claim that Firsov is a Russian hacker and allegedly the administrator of Deer.io. He not only managed the platform, the indictment alleges; he also advertised it on other cyber forums that catered to hackers.
Out of all the shops on Deer.io, the FBI still hasn’t found a single legitimate business advertising its services and/or products, and it’s been looking. The Bureau reviewed about 250 storefronts and found thousands of compromised accounts posted for sale, including gamer accounts, along with files containing user names, passwords, US taxpayer IDs, dates of birth, and addresses for victims, who are largely located in Europe and the US.
Deer.io offers a “turnkey” online storefront design and hosting platform on Russian servers that are beyond the reach of US law enforcement, according to court papers. Besides helping cybercrooks to advertise and sell their products, much like an underworld Shopify or Squarespace, Deer.io also offers services, such as help with criminal hacking.
Buying a storefront to peddle your criminal products and services is quite cheap at around 800 Russian Rubles (USD $11) per month, and Deer.io guides the seller through an automated set-up to upload their wares and to configure cryptocurrency wallets to collect payments.
A criminal who wants to purchase from stores on the Deer.io platform can just use a web browser – there’s no fussing with tools to get to Dark Web hidden sites. The site even contains a search function, so buyers can search for hacked accounts from specific companies or PII from specific countries.
Earlier this month, the FBI went shopping. It bought approximately 1,100 compromised gamer accounts from a Deer.io store for under $20 in Bitcoin. That got it user names and passwords – which would be enough to enable someone to make purchases from those accounts at the expense of their real owners.
For about $170 in Bitcoin, the FBI also picked up about 999 individual PII accounts. On the same day, it bought another 2,650 accounts for about $522 in Bitcoin. That got the agents names, dates of birth and US Social Security numbers: all the data you need to do identity theft and pull off financial fraud. All of these purchases confirmed that Deer.io shops are selling the real deal: it was all authentic information, as opposed to fake data.
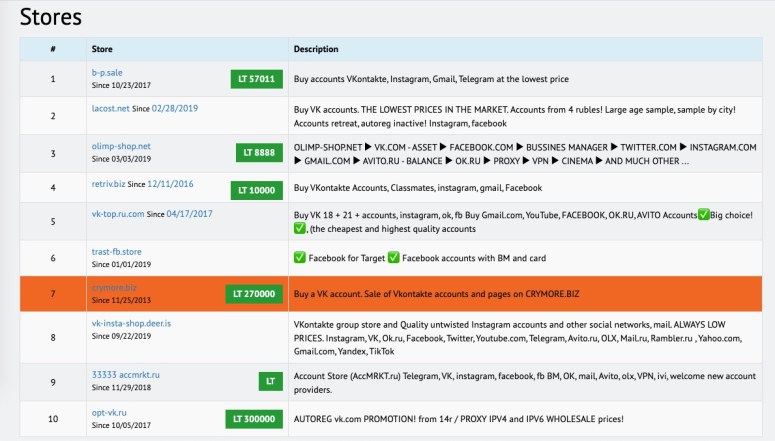
As of Tuesday morning, this was what some of the Deer.io storefronts were offering for sale:
According to ZDNet, Deer.io first came to light in a now-removed Digital Shadows report published in June 2016. Its first claim to fame came when a well-known hacker – Tessa88 – used a Deer.io shop to sell user data hacked from MySpace and LinkedIn.
According to ZDNet’s Catalin Cimpanu, he got a message from the Deer.io admin – believed to have been Firsov – back in 2016. The admin ducked Cimpanu’s question about selling hacked data, but they did claim that the site was working within Russian law. From that email:
deer.io works according to the laws of the Russian Federation.
Our clients can create shops that do not violate the laws of the Russian Federation. We block shops that sell drugs/stolen bank accounts. We will also block any shop if requested by Roskomnadzor or the competent authorities of the Russian Federation.
(Roskomnadzor, also known as the Federal Service for Supervision of Communications, Information Technology and Mass Media, is the Russian federal executive body responsible for censorship in media and telecommunications.)
The Feds haven’t outlined what led them to finger Firsov as the alleged admin of Deer.io, but security journalist Brian Krebs has traced a line of clues, starting with a Twitter profile that says he’s a security researcher and developer who currently lives in Moscow.
That account includes tweets about Firsov having discovered a number of serious security flaws in the Telegram messaging app, as well as references to winning multiple “capture the flag” hacking competitions.
Krebs goes on to note that the admin for a popular online crime forum posted on Tuesday about Firsov being a 28-year-old from Krasnodar, Russia who studied at the Moscow Border Institute – a division of the Russian Federal Security Service (FSB).
Firsov is slated to be arraigned later this week. He’ll be facing two felony counts: aiding and abetting of trafficking, and trafficking of stolen information.
Latest Naked Security podcast
LISTEN NOW
Click-and-drag on the soundwaves below to skip to any point in the podcast. You can also listen directly on Soundcloud.
