Thanks to Graham Chantry and Tad Heppner of SophosLabs for their help with this article.
Many UK residents woke up yesterday to a rude internet shock: a scam email that greeted them with their real name and home address.
Collectively, we’re getting better and better at spotting emails that don’t come from where they say, for example because our real bank doesn’t call us Dear Customer, and because our real mortgage provider knows how to spell its own kompani nayme without making absurd misteaks.
But in this case, the email wasn’t trying to disguise that it came from a ne’er-do-well.
Indeed, the scamminess of the text made the email more worrisome, and thus perhaps paradoxically more likely to squeeze victims into action than a well-written email from an obviously unlikely source.
The text in the emails vary slightly from sample to sample, but examples seen by SophosLabs go something like this:
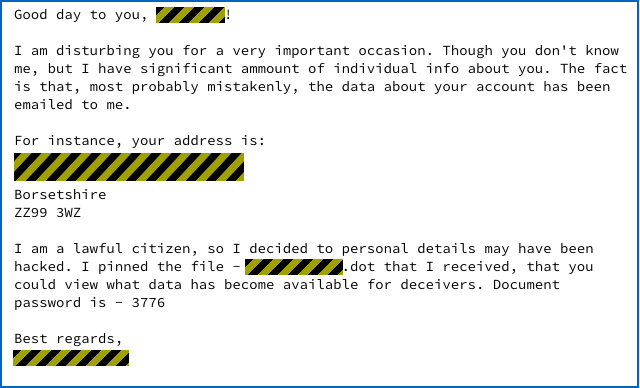
Or like this:
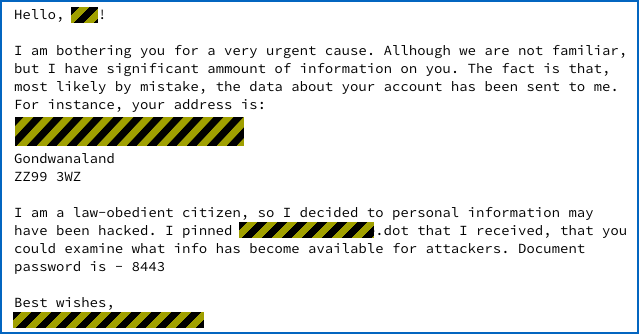
The salutation uses your first name (given name); the filename is your surname (family name); and the address is your home address, complete with postcode.
You know it’s a scam, not only from the terrible mistakes in spelling and grammar, but also from the fact that no official organisation would dare write what amounts to a veiled threat of this sort.
So it feels wrong and risky to open it to see how much is in there.
On the other hand, there must be some truth in the claims about a data leak, because the crooks know your name and address – and not just vaguely, but precisely, so who knows what else they know about you?
With so many data breaches in the news recently, it’s perfectly reasonably to wonder, “How serious is this?”
So it feels wrong and risky not to open it to see how much is in there.
What happens next?
If you do open the attachment, which is portentously called Yoursurname.dot, Word prompts you for a password, just as the scammers warned you to expect:
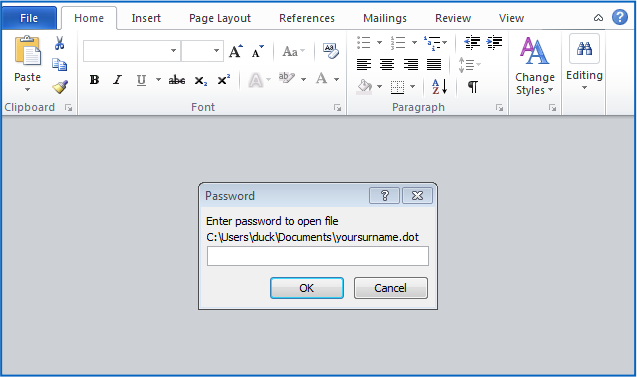
The password is randomly chosen for each recipient, and you really do need to use the one in your own email to open the file:
At this point, the crooks are aiming to persuade you to enable macros in the open document, which means you’ll be running program code stored in the file by the crooks themselves.
This is a feature of Word – you can write extensive and powerful Word extensions as macros, using Microsoft’s Visual Basic for Applications (VBA) programming language – but because macros that arrive from outside can be super-dangerous, they don’t run by default.
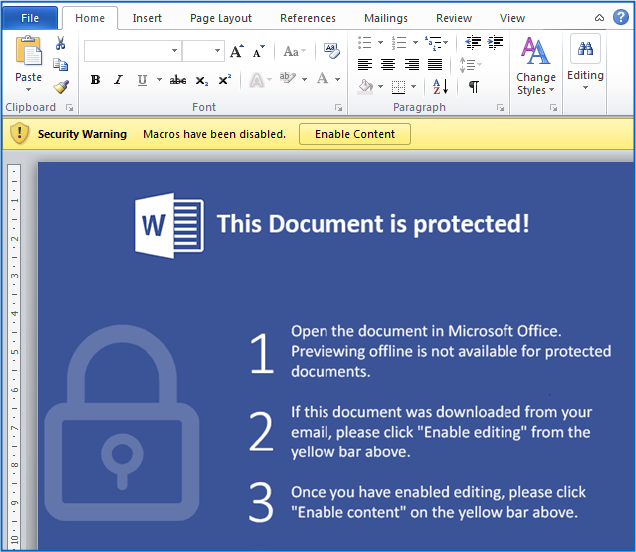
To get you to agree to run their malicious macro program, the crooks use what you might call a bait-and-switch trick.
The document presents an official-looking help page that tells you that you need to “Enable editing” to view its content.
Somehow, this sounds less suspicious that enabling macros, as though you’re just agreeing to view what’s inside the document, not trusting it to the point of letting it run untrusted program code inside Word.
If you click on [Enable Content], you’re agreeing to execute a malicious VBA program that tries two different web pages, hosted on hacked web servers, and downloads what looks like a GIF file.
GIF is short for Graphics Interchange Format, an old but still-common type of image file.
In fact, the GIF file has just 10 bytes of valid header data, followed by a 256-byte decryption key, followed by about 0.5MB of binary data scrambled by XORing it with the decryption key repeated over and over. (This is known as a Vigenère cipher, named after a cryptographer from the 1500s who didn’t actually invent it.)
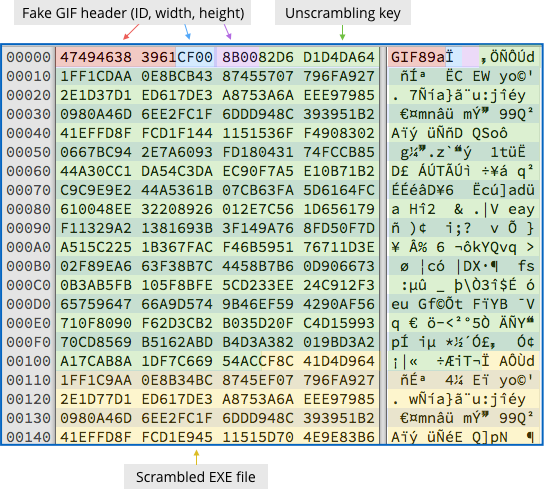
The GIF header makes the file look innocent, even though it won’t display as an image, and the Vigenère scrambling means that the suspicious parts of the file aren’t obvious.
Malware unscrambled
Of course, the scrambling also means that the fake GIF file is harmless on its own, so the malicious macro includes a decryption loop that strips out the executable code, unscrambles it and writes it to %TEMP%, the special folder where Windows saves your temporary files.
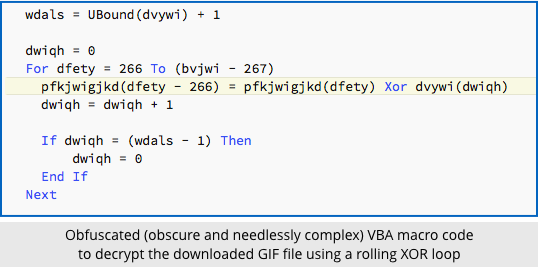
The malware ends up with a randomly-chosen numeric name, such as 05643.EXE
When we tested out this attack in SophosLabs, the downloaded malware was Troj/Agent-AURH, a strain of bot or zombie malware that calls home to a so-called command-and-control (C&C) network for further instructions.
Our zombified computer didn’t receive any instructions during our test, but it’s important to remember that in attacks of this sort:
- The crooks can vary the downloaded malware as they see fit, changing it according to your timezone, your location, your language settings or simply their own whim.
- The crooks can vary the instructions they send to some or all of the bots in their botnet, typically including updating or changing the bot itself, or downloading additional malware.
The malicious macro in the original document has two more tricks up its sleeve to go along with the “fake GIF file” unscrambling shenanigans.
If the macro gets an unexpected response on its first attempt to download the fake GIF, the crooks assume that some sort of firewall or web-filtering anti-virus blocked the download, so they try to talk you into turning your security filtering off:
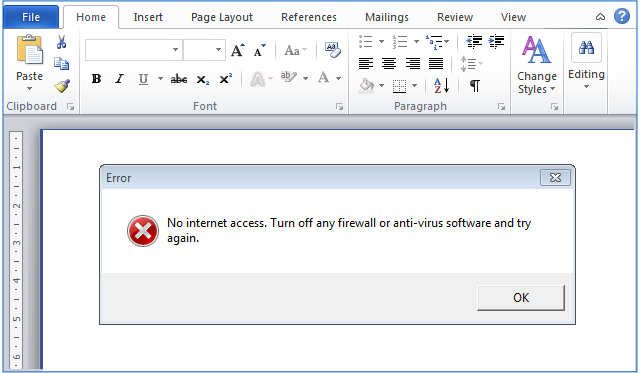
It’s easy to assume that the popup comes from Word, or even Windows itself, but that’s the crooks talking to you.
Equally sneakily, the crooks pop up the following message, right at the very end:
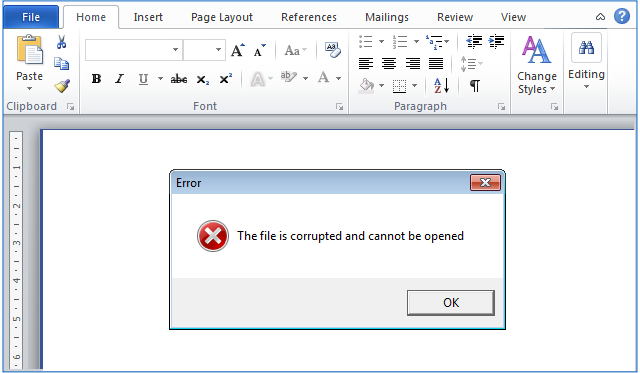 ,
,
It’s all a pack of lies: the “file is corrupted” message means exactly the opposite of what it says, because it only appears after the malware has been downloaded, unscrambled, saved to disk and launched in the background.
Should you be afraid?
It’s understandable to feel a touch of fear when you receive a scam email that knows your name and home address, because of the lurking question, “Why me?”
The good news, if you can call it that, is that through articles and advisories like this one, you’ll soon see that you aren’t alone, and that the crooks are targeting a much wider group than just you.
Sadly, however, it’s likely that the home addresses they’re using were stolen in one or more data breaches, and then sold on in the computer underground for criminal abuse of this sort.
At least in the UK, many companies that collect addresses put them through some kind of standardisation algorithm to produce address data in the format preferred by the Post Office, so it can be hard to figure out the likely source of the breach.
What to do?
- Don’t open unsolicited or unexpected attachments, especially not on the say-so of an unknown sender.
Even if the document claims to be an invoice you don’t owe, or threatens you in some way, don’t let fear or uncertainty get the better of you. After all, if you’re concerned about the trustworthiness of the sender, the worst thing you can do is to take their “advice” about computer security!
- Don’t turn off important security settings such as “macros have been disabled”, especially not on the say-so of an unknown sender.
The crooks have come up with many ways to trick you into clicking [Enable content], usually by making it sound as though it somehow increases security, for example by decrypting or unlocking confidential information. But Microsoft turned Word macros off by default years ago to improve security, so turning macros back on will leave you less secure.
- If you’re unsure what to do, ask someone you actually know and trust, such as a friend or family member.
Never ask the sender of the email for advice. They will simply tell you what they want you to hear, not what you need to know. And if you’re a friend who gets asked for help, try using our short-and-sweet motto, and stick to your guns: “Don’t buy, don’t try, don’t reply.”
- If you think a targeted email of this sort really is a personal attack on you, for example by a stalker, rather than part of a wider cybercrime campaign, and you are genuinely concerned for your safety, contact law enforcement locally.
Be prepared to explain yourself clearly, which typically means keeping suspicious emails and messages.
Have you recently opened an email that you now have reason to distrust, or are you concerned that you may have let malware sneak in by taking risky advice that came from someone you don’t know? If so, you can download our free Sophos Virus Removal Tool to search for malware that may be lurking undetected. You don’t need to uninstall your existing anti-virus first – our Virus Removal Tool is designed to work alongside other security products.

Darren higgins
All UK name and address information is available via the electroral register which there are commercial vrsions to purchase UK info disk used to be a good one. 192.com holds the same info for a subscription fee and credits. So names and addresses don’t need to originate from a data breach when the info is sold freely anyway
William Quinton
Yes, you’re right Darren, but only for electors who don’t opt out of the open register. If you do opt out, then your data is only available to certain organisations, like licensed credit reference agencies, who will (we understand) protect your data.
Paul Ducklin
That’s my understanding: a subset of the data in the electoral register is always public, and the rest of it is openly sold by HM Government unless you opt out. Quite how anyone thinks that is acceptable behaviour for a database that is supposed to regulate your elegibility to participate in secret ballots that are supposedly the cornerstone of modern democracy…
…I feel a rhetorical question coming on.
Mahhn
I’ll bite. – what if a hacker group has a front business that is solely used to purchase user data? Which can play back the ISPs in the US being able to harvest and sell all customer data – the hackers can buy it, even if by proxy.. Once our data is out there, it’s there…
Paul Ducklin
As you say…once out there, it’s out there :-(
That’s why breaches can be so pernicious. A breach of your data by company X doesn’t put just your account with X in jeopardy – it probably puts your accounts with other organisations at risk too. (You only have one date of birth, one SSN, one national ID number, one mother’s maiden name, one home address… and all of those are somewhere from hard to impossible to change.)
olson@sayvillelibrary.org
The same is true in the US, voter registration information is publicly available, and in some states the information is freely available through commercial sites. The information includes: name, address, DOB, political affiliation, last date voted, etc. Since most people have their personal information on social media and data collection sites, it would be easy to find an e-mail address, either through a data breach or just searching.
Conrad Longmore
There was a previous wave of similar spam which included a valid telephone number. In the case of this spam run and that one, all the email addresses, postal addresses and phone numbers seemed to be a few years old and not current. Also, in one case the email was addressed to the recipient’s spouse and had the spouse’s work address. All recipients were in the UK only.
Of course, the electoral register doesn’t contain email addresses, phone numbers and the addresses would be up-to-date. It certainly wouldn’t have the work address of a spouse in it. A check of haveibeenpwned.com for those recipients indicates no common data breach. The data has definitely leaked out from somewhere, but as yet I don’t know where..
Pete Speller
OK, so I got suckered and did open the file – have since run Avast and Sophos Virus Removal Tool, but came up with no hits – have I got away with it?
ejhonda
I’d run something like Malwarebytes just for another check of your assets. You could also install and run SysInternal’s Process Explorer (edited to remove link) to see if you have any processes running that are identified by Virus Total as being malicious. Good luck!
Paul Ducklin
Even if you opened the attachment then you are probably fine as long as you did *not* also do these:
* Enter the four-digit passsord from the email. Until you do that the document is technically not open – it’s just scrambled data, including scrambled macro code that can’t run. If
* Click [Enable Content]. If you don’t do that then the macros just lie around in memory but never get executed, so no harm done.
* See the bogus “file is corrupt” message. If that message doesn’t appear, the macro code to fire up the downloaded malware probably didn’t work properly.
You could also look by hand in your TEMP folder, see if there is a file with a name of consisting of a few numeric digits followed by “.EXE”. If there is, then it could be the malware…a good hint is if it has a timestamp that matches the moment when you opened the DOT file. If there isn’t such a file then it looks as though you got away with it.
anon
To make matters worse, Microsoft actually does ask you to log in to turn on the edit function if you have their Android view only version of Word.
ejhonda
On 3/24 I received an interesting email that was placed by Gmail in my spam folder. The twist was it had three pieces of information in it that I haven’t typically found bundled together: my full name, my mailing address, and my email address. It claimed to be a notice for a failed package delivery. I’ve seen the fake package delivery notices, but this was a first with correct mailing address and full name included. It has a Word document attachment that is identified as infected by Gmail – likely very similar to what you’ve documented here.
F Dodds
Same here but in addition, they had my mobile number (new number) !!!! asking me to visit a website to track a delivery for an order I have not placed from a company. Problem is the company does exist but is in the US.
Not happy at all that they manage to get hold of my phone number :-(
Scott
I received an e-mail claiming that I sent someone a money request using Paypal in which the phishers simply pulled my actual name and mailing address from Paypal. Paul, if you are reading this, check my forward from e-mail address in the last two weeks, to your “is-spam@labs.sophos.com” address. It is the same scam, using an encrypted word document and macros. It would appear it’s not just those in the UK targeted, but also the US.
P
I received one.
I deleted it.
Good article.
JM
Why does the malicious file go to http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab and download this? Noticed that a lot of malware does this- why? Thanks
Josh
I think its because since malware is run inside a windows virtual machine, these requests to windows update are legitimate.
Phil.
I got one of these today – claiming to be an order invoice, rather than threatening to dox me.
But because they’ve used a rather odd variant of my name, I know they got the data from ebay (or an ebay seller). Will ebay care? Doubt it.
James
Myself, my wife and daughter have all had one of these emails today, just the Word Doc and invoice. Because of the emails it was sent to and the address details we can work out it is data that only eBay was holding. How can you report this?
Stevie
Oh the power of the Internet!!, thanks for flagging this up guys…I received an email today (edited to remove link) very similar to ones described above starting with ‘good day to you’ then my home address (which was the worrying part) and a word doc attachment…I am pretty much aware of the scams etc but I nearly feel for this…until I noticed they Got my name slightly wrong..(using one I once registered when I opened a google account using a variation of my name)
I binned the message resisting the temptation to open the attachment.
Peter B in Florida
It’s odd that the document (.dot) is actually a template – a document that’s used to create other documents. I wonder if that’s significant? Or was the sender just that incompetent they didn’t know what they were sending? I don’t recall .dot files having vulnerabilities that .doc* files lack…
Paul Ducklin
DOT files can have macros in them, that’s why the .DOT was used.
speeednet
I have just received one of these, the address , county and postcode were all spot on. I have about 12 active email addresses that I use for various things and websites, the email address that this arrived in is one that to the best of my knowledge is only used by Ebay and Paypal. Anybody else found a similar occurrence?
Michael
My wife got one of these using s form of her name that is as far as we know only used on her eBay account. Make of that what you will… it’s not impossible the it is a coincidental formatting error, but it might not be.
Anonymous
Hello,
I received an email this morning from an individual first name and surname @sfr.fr
The email contained my full name and home address with a zip file surname.zip telling me the contract was attached and gave me the password to open the file.
I stupidly clicked on the zip file from my iphone but fortunately it didn’t open as I can’t even open legitimate zip files on my iphone.
Despite the zip file not opening do you think my iphone could still be at risk since I still opened the email and clicked on the zip file?
Thanks
A
Got exactly the same just now, iPhone isn’t at risk IMO. Just in case I just wanted to see what DodgyWare it might be and run the file through online virus scanner. Nothing suspicious was detected. Domain of the sender was some german company I have no connection to. Header looks ok, so I think sender account has been hacked. I looked up on google and just stumbled upon this post, so I’m (sorry guys) glad that it wasn’t only me. Bin/forget
Kaz
Just had an email with my old name and address on with a zip file attached, did not open it as it seemed really odd, it had a pass number on it too, said it was a statement! The @bit was wanadoo.fr
Benjamin
I received one of these today – zip file with password. It looked so legit that I tried to open on my iphone but it wouldn’t work. I assume that I’m OK and that the malware hasn’t been placed on the phone? I also replied to the email asking who the person was – then I googled when I got home and found this. Assume I am OK as long as I didn’t open the attachment on my PC?
Paul Ducklin
I think that’s a safe assumption. The attack as it unfolded for us ended up with a Windows-specific program (the malware). That means it wouldn’t work on an iPhone. (It is possible in theory for crooks to adapt their downloads to match the operating system you are using, but I don’t think that was the case here.)
However, if you weren’t able to open the ZIP file in the first place, then you didn’t even get to the beginning of the beginning of the attack, let alone to the beginning of the end. So I think you are golden.
As an aside: if you are ever concerned about the legitimacy of an email (or a text message, IM, phone call, etc.) then never rely on replying or calling back to the original sender to ask if they’re honest. If they are, they’ll tell you they are…and if they aren’t, they’ll still tell you they are :-)