On Monday, we wrote about a Netgear router bug that opened up a gaping remote access hole.
Simply put, if your router has the bug, then anyone who can make a web request to it can send it any Unix command they like, and the router will run that command as the root user.
An attacker could therefore read and change your network configuration; spy on your traffic; co-opt you into a botnet; redirect you to ads, unsavoury sites or malware; and much more.
Here’s what you need to know.
Our immediate advice was :
- Make sure that your router’s web management interface is not visible from the internet so that any attack would have to come from inside your network.
- Watch Netgear’s security advisory for a firmware update to patch the problem.
- Consider turning the bug against itself by using the exploit to shut down the web management interface where the bug is found.
The good news is that Netgear is rising to the challenge of addressing this, testing routers in its range to find the extent of the vulnerability, and working on firmware updates for those models that have the bug.
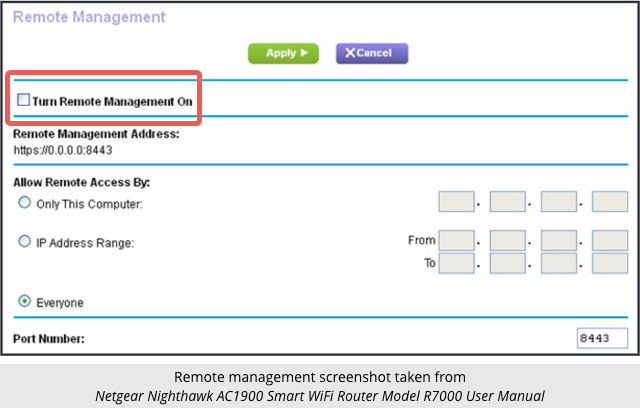
The bad news is that the vulnerability is more serious, or at least it is very much easier to exploit, than we first thought when we advised you simply to check that the Remote Management feature was turned off.
Here’s where we are now.
Q. Which routers are vulnerable?
As at 2016-12-21T00:25Z, Netgear listed the following models: R6250, R6400, R6700, R6900, R7000, R7100LG, R7300DST, R7300, R7900, R8000, D6220, D6400.
This list may change, so check from time to time with Netgear on its appropriate support page, Security Advisory for VU 582384.
Q. Can I be hacked directly from outside?
Only if an attacker can directly connect to the web interface on your router from the internet (the WAN port on your router).
This requires the Remote Management option to be turned on; fortunately it is off by default and so the web interface is only accessible via your router’s LAN ports or Wi-Fi.
You can check this setting by following the instructions in our earlier article.
Q. Can I be hacked directly from the inside?
Anyone on your network, such as friends who know your Wi-Fi password (or others who can guess it), could issue a malicious web request and mess with your router.
Q. Can I be hacked indirectly from the outside?
Unfortunately, yes.
As a commenter on our earlier article pointed out, most Netgear routers have a default network address (IP number) of 192.168.1.1.
So, anyone who sends you an email or attracts you to a web page could booby-trap it with a malicious URL starting http://192.168.1.1/cgi-bin that, if innocently clicked by a user inside your network, could trigger the bug.
Worse still, as others have pointed out, a booby-trapped web page could be rigged up to refer to an image file supposedly stored at http://192.168.1.1.
If you were to load the page, the page would try to load the image, and your browser would try to visit the dangerous URL.
Of course, no image would load, but by then the damage could already have been done.
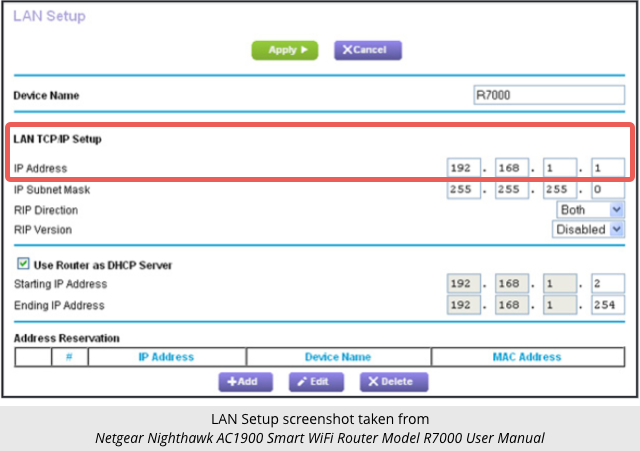
Q. Can I change my network’s IP number?
Yes. You can use any of the so-called private network number ranges consisting of 10.x.x.x, 192.168.x.x or 172.[16-31].x.x, giving you a wide choice of network numberings to make it harder for crooks to guess.
To do this, use the Advanced | Setup | LAN Setup screen in your router’s web interface.
Q. Will changing my network numbering help?
Sort of, because crooks won’t easily be able to guess the numbers you used.
In theory, though, they could use a booby-trapped web page containing JavaScript that tries to load an image from each possible router IP number in turn.
Fortunately, with about 16 million to choose from in the 10.x.x.x.x range (plus another million in 172.[16-31].x.x and about 65,000 in 192.168.x.x), this could take ages and you would probably notice.
But there’s another problem.
So that you don’t have to remember your network number, Netgear routers automatically convert the domain name routerlogin.net into the IP address of your router if try to access it from your own LAN.
Sadly, this convenience is handy for crooks, too, because they no longer need to guess your IP number.
Q. Can I turn off the routerlogin.net redirection feature?
We don’t think so.
The redirection is performed by the DNS server in your router, and if your computer gets its network configuration from the router (this is called DHCP, short for Dynamic Host Configuration Protocol), it will be told to rely on the router for its DNS.
You would need to override the DNS setting manually on your computer, for example to rely on Google’s free DNS at 8.8.8.8 instead, but that wouldn’t reconfigure other computers that might connect to your network.
Q. Can I test my own router?
Try visiting this URL:
http://routerlogin.net/cgi-bin/;uname
That should send a web request to the potentially vulnerable software component in your router.
If the exploit works, your router will run the command uname, a Unix utility that prints out the identity of the operating system, which is Linux on Netgear routers.
So, if you see a regular-looking error message, we think you are safe because your router didn’t run the unwanted command.
But if you see a web page including output that consists of the word Linux, you should assume the exploit worked because the command named in the URL ran.
Q. Can I use the exploit to fix the bug?
As we explained in our earlier article, a UK security researcher has suggested using this URL as a trick to tell your router to kill off the web interface, which temporarily kills off the bug at the same time.
http://routerlogin.net/cgi-bin/;killall$IFS'httpd'
Don’t forget that if your router reboots, for example after a power outage, the web interface will come back up, too.
Q. Is there a patch for my router yet?
Check with Netgear on its appropriate support page, Security Advisory for VU 582384.
As at 2016-12-21T00:25Z, eleven router models had firmware updates available (four had official updates; seven had beta updates). Check the list above for the latest update list.

Adam Dawidziuk
Maybe we can actually change the DNS server on the actual router (rather than on the individual machines)?
Paul Ducklin
I dont have a Netgear router to muck about with so I am relying on the (close to 200 pages of :-) manual and I don’t think you can do it that way – I checked because I thought that would be a nice tip.
You can change the upstream DNS server that your router uses to resolve DNS queries, but I couldn’t find a way to change the DNS server that the router tells clients to use when it answers DHCP requests. (DHCP is usually used to tell clients [a] what IP number and netmask to use [b] where the gateway is and [c] which DNS server to rely on. In Netgear’s DHCP configuration options I could only find out how to change [a]. The gateway and DNS server are just set to be the router itself.)
In other words, the router always seems to act as a caching name server for any computers on the LAN that are configured via DHCP. Therefore the router sees your queries before they go out onto the internet, and thus always gets the chance to do its redirection trick.
Dan Louie
@Paul Duklin. When I did the vulnerability test. I got a 0 on screen. Since it did not show Linux on screen. Can I safely assume the 0 an error message? And it’s okay to use the router?
Paul Ducklin
If you didn’t see “Linux” you ought to be OK, but without seeing what happened for myself I can’t really say for sure.
Have you checked for a firmware update for your router model? Is is one of those officially listed by Netgear?