Thanks to Andrew O’Donnell of SophosLabs for his behind-the-scenes work on this article.
There’s a new fake support scam in town, hiding behind a file calling itself Microsoft Security Essentials, and it’s trying to trick victims into contacting bogus help centers.
The malware, known to Sophos as Troj/Diztakun-A (Microsoft calls it Hicurdismos), is strangely reminiscent of what many readers will know as lockscreen ransomware from back in 2012.
Lockscreen ransomware froze your computer with a web page that tried to squeeze you into paying a “fine”, often for alleged copyright infringement or porn-viewing “offences”, after which the lock screen would be removed.
Malware of this sort, such as the once-widespread Reveton, did its best to stop you switching away from the lockscreen, so that you couldn’t hack your way out of trouble using system tools such as Task Manager.
With Diztakun, the principle is similar but the outcomes are different.
Diztakun locks you up at a fake Blue Screen of Death (BSoD) screen, but instead of demanding payment via a web page, it kindly suggests that you might want to call for technical support, handily providing a toll free number to call.
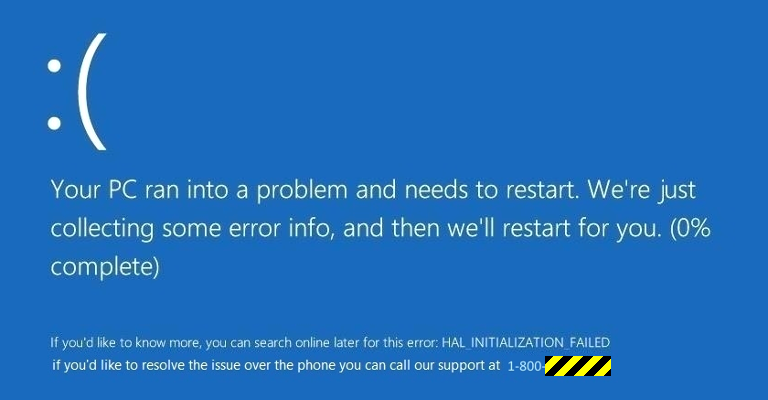
These days, BSoDs are thankfully much rarer than they were, and usually vanish quickly of their own accord when your computer reboots automatically, but that’s not what happens with Diztakun.
The malware does the following so that you’ll think your system is truly locked up:
- Shows a frozen mouse cursor.
- Disables Task Manager to stop you from terminating the process.
- Fills the screen with the fake BSoD image.
Who’s at risk?
Microsoft Security Essentials is Microsoft’s anti-malware component for Windows 7 and earlier.
In Windows 8.1 and Windows, 10, you get Windows Defender instead; some users might not be aware of that, and assume that by installing a utility called Security Essentials, they’d be increasing their security rather than infecting themselves.
Whatever you do, if you see the fake BSoD above, don’t call the number! That won’t fix anything.
Instead, you’ll end up connected to a fake support call scammer, and your troubles will only get worse.
What to do?
When you need help with your computer, turn to someone you know, like and trust.
In this case, when we say “someone you know,” we mean “someone you’ve actually met in person,” as opposed to just online.
On Windows 10, Windows Defender is built in, so there’s no need to install Microsoft Security Essentials.
Tech support scams aren’t going away anytime soon, so keep an eye out for those that mimic real Windows messages.
And remember that old-school scams, where the crooks cold-call you instead of waiting for you to contact them, aren’t going away anytime soon, either.
For those classic attempts to con you out of your money, check out our brief podcast about how to hang up and stay safe:
DEALING WITH FAKE SUPPORT CALLS
Here’s a short podcast you can recommend to friends and family. We make it clear it clear that these guys are scammers (and why), and offer some practical advice on how to deal with them.
(Originally recorded 05 Nov 2010, duration 6’15”, download size 4.5MB)
How to remove Dizaktun by hand
A few commenters asked about removing the specific sample described here by hand, so here’s how.
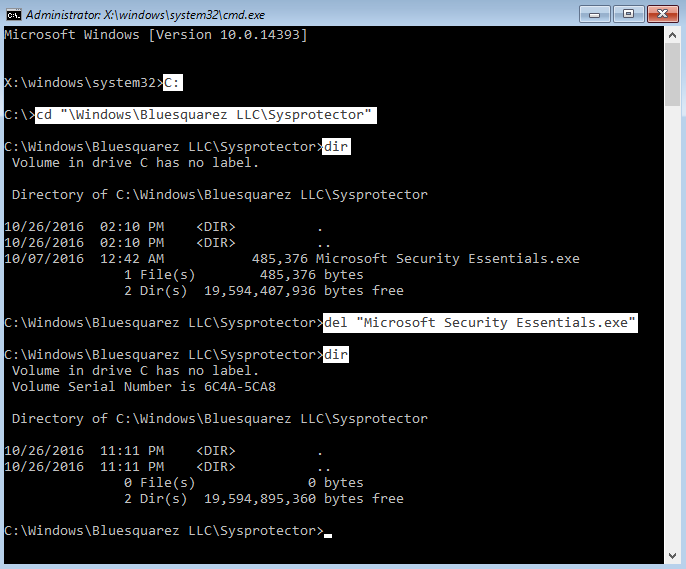
This sample described above installs itself as:
C:\Windows\Bluesquarez LLC\Sysprotector\Microsoft Security Essentials.exe
Deleting this file will remove the fake BSoD lock, but beating the malware to the punch after logging out and back in is tricky, because the fake BSoD appears again quickly.
Fortunately, however, Diztakun sets itself to run automatically only when the user who first ran the malware file logs back in.
If you have more than one user set up on your computer, you can log out and back in as a different user and should then be able to find and remove the abovementioned file.
If not, this worked for us on Windows 10:
- Use
Ctrl-Alt-Delat the fake BSoD to get back to the logon control screen. - Click the power-off icon, hold down
Shiftand chooseRestart. - At the
Choose an optionscreen, clickTroubleshoot|Advanced options|Command Prompt. - Log in with your usual username and password.
- At the command prompt, switch to the C: drive and delete the abovementioned file.
- Type
exitto return toChoose an optionand clickContinue.
If you’re unfamiliar with the command prompt, this is how it goes (with the parts you type in shown in highlighted text):
When you log back in and next try to run Task Manager, you will probably see a popup telling you that Task Manager has been turned off:
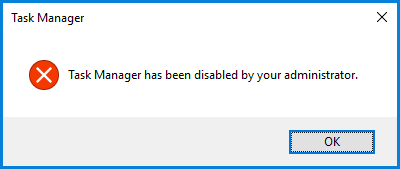
To fix this you will need to delete this registry entry:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\system\DisableTaskMgr
You can do this using the Registry Editor; if you don’t have experience with this utility, you may want to ask a friend (but see above!) for help.
Image of Blue screen of death courtesy of JaysonPhotography / Shutterstock.com
Anonymous
Saw this on a client a few days ago.
First thing that tipped me off was the image quality. You could tell it was not actual text but rather an image. Better luck to them next time.
MIke Johnson
Paying Client I hope!
KEN
would havel iked this more if you gave instruction on getting away from the lock screen image.
Paul Ducklin
Check now.
Jaime
You didn’t report what to do to get your computer out of the mode. Does only restarting work and take care of the problem? or do we need to go full fledged and spend a day running anti-malware / spyware and antivirus software. this would be helpful to know.
Paul Ducklin
Restarting typically doesn’t give you enough time to sneak in there and fix it. But for this malware there’s a trick using a second account (if you have one et up), or you can use recovery mode to get rid of the malware file. See the article, updated with some blow-by-blow instructions.
B
couldnt you just run safe mode and disable it?
Gnume
Little disappointed in the “What do you Do” section of this article. I thought it might actually tell me what to do outside of “Call someone you trust” or at least provide me to a link that provides that answer.
Paul Ducklin
That advice was meant to be very general: how to avoid ending up talking to scammers, regardless of how they pitch you with fear, whether they col-call you or trick/squeeze you into calling them.
I think I’ll add something specific for this malware sample, as a sort of addendum, just in case. Give me a moment :-)
Steve
Refreshed the page and found the update. Excellent! Thank you, Paul.
Paul Ducklin
You’re welcome.
Paul Ducklin
OK, now done. Which is nice, as it’s bedtime…1am :-)
Anonymous
Typo: The correct spelling of the malware “Hicurdismos”
Paul Ducklin
Fixed, thanks. Don’t know how that happened :-)
More Info pls
Hey Paul,
What happened to your “addendum”? ;)
I would also like to know if there is a way to prevent someone from disabling your Task Manager, some change that you can make as admin in Windows? Task Manager has helped me out of many bad situations.
TKU
Paul Ducklin
I was working on it :-)
Look now. Fixing a blocked Task Manager block is explained, too…
Bryan
Duck, I interpreted the above question as “can we prevent this registry key from being set in the first place?” Maybe along the lines of locking it in the “off” position. The key exists or doesn’t (as opposed to being a boolean), so I doubt that’s possible.
If there’s no preferable alternative what are your thoughts on a small batch file tucked away in startup (or scheduled tasks) to simply delete that key? Seems like taking an aspirin every hour to preempt the possibility of a headache, but some headaches are worth preventing…
Cetin A.
I think something called “Task Manager” should never ever be disable-able, but that’s just me :)
skyhack
One way to handle the file would be to reboot using a usb/cd live distro (I like Linux, but a Windows PM disk will do) and remove the file from there. I would then reboot the machine, enable the built-in admin account, go into said account, and enable task manager. While you’re there, give the admin account a secure password (can’t hurt). Windows malware seldom goes after the admin account, since it is disabled by default. When you’re back in your normal account, disable the admin account again. The password gives it an extra level of protection, keeping an admin user from inadvertently allowing the admin account to be accessed from a malicious “net user” command.
Paul Ducklin
You might want to try Sophos Bootable Anti-Virus (via ISO or USB), see how you like it :-)
https://community.sophos.com/kb/en-us/52011
L.Mayer
Advanced users could:
1. Boot from a live CD and make changes?
2. Restore a prior system image?