Stefan Esser is well known in the Apple iOS jailbreaking and security research community.
Four years ago, at the CanSecWest conference, he presented a paper entitled iOS 5 – An Exploitation Nightmare?
Our own Chester Wisniewski attended that talk, which recounted the nature of the arms race between jailbreakers and Apple.
Esser admitted, back in 2012, that jailbreaking was getting harder, and the timing of jailbreaks more critical, as Apple crammed anti-jailbreak code into every new release of the operating system.
Jailbreakers aim to remove Apple’s artificial restrictions on what their iPhones can do, not only for the freedom to run a wider collection of apps, but also to install security patches and controls that Apple hasn’t got around to yet.
Apple, on the other hand, wants an iOS ecosystem that is contained inside its own “walled garden,” not only to give it a better chance of keeping crooks and rogue software out, but also for reasons of commercial control.
Once you have bought an iPhone, you can only shop at the company store.
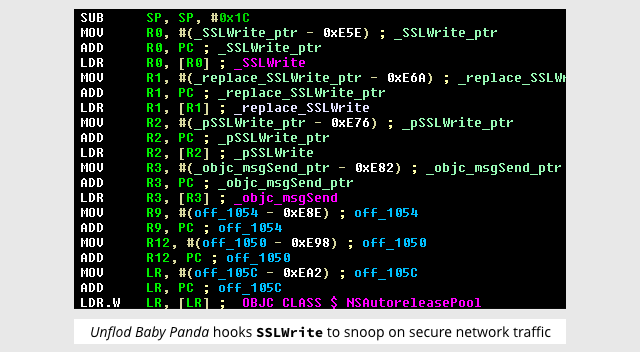
Two years ago, Esser showed his curiously humorous side when he gave the name Baby Panda (no, we never found out why) to data-stealing iOS malware that was also known as Unflod, apparently due to the malware developer mis-spelling the word “Unfold”.
Unflod Baby Panda had a bunch of nasty hidden tricks, including tapping into the TLS/SSL code inside the operating system so that the malware could secretly take a look at any encrypted data you were about to send, just before it was encrypted.
Fortunately, the malware was easy to avoid because it only worked on jailbroken devices, which did no harm to Apple’s strict “no jailbreaking” stance.
Success in the App Store
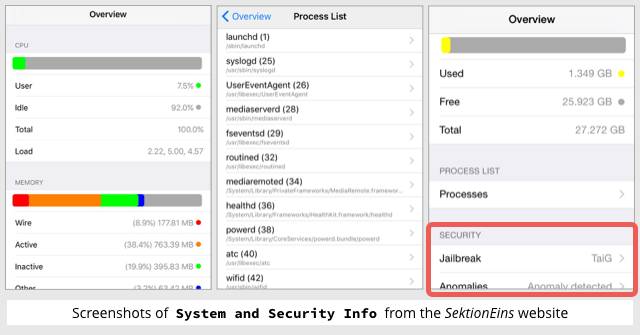
Fast forward to last week, and Esser was flying high in the App Store with a new app called System and Security Info.
According to 9to5Mac, Esser’s app even reached the top of the paid apps chart in the USA.
At €0.99 a time, you’d have to imagine that SektionEins, Esser’s company, was making a tidy income out of a utility that was popular because lots of users found it handy.
That sounds like a win-win-win scenario, with a positive outcome for SektionEins, Apple and their mutual customers.
As well as tracking the CPU and memory usage of other apps, the program would look out for potential security problems caused by the misbehaviour of other apps:
The key features of this app are the ability to show the list of running processes in iOS 9 and a jailbreak and security anomaly detection that can help security concerned users to check for potential privacy issues and security threats.
Apple famously doesn’t allow proper anti-virus software in the App Store, a restriction that applies to OS X as well as to iOS software.
The limitations imposed on submissions pretty much make third-party threat prevention software, such as a real-time anti-virus, a technical impossibility in the App Store.
Fortunately, on OS X, you can install software from outside the App Store – by default from trusted developers, and, by changing a system setting, from anyone you like.
On iOS, where it’s the App Store or nothing, you’re out of luck.
If you’ve ever wondered why you get Sophos Home for OS X from Sophos and not from the App Store, now you know. To get Sophos Anti-Virus into the App Store, we’d have to emasculate it by removing features such as on-access protection, also known as real-time scanning. But those are the most useful parts, because they prevent rather than merely detect malware.
Nevertheless, Esser’s program, despite its real-time security anomaly detection, had Apple’s blessing…
…until the start of this week.
Ironically, a bug reported as a side-effect of 9to5Mac’s positive review of the software may have led to Esser’s downfall.
Esser tweeted late last week that:
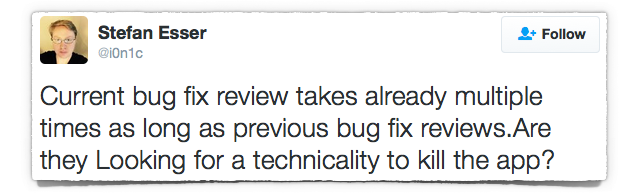
Current bug fix review takes already multiple times as long as previous bug fix reviews. Are they Looking for a technicality to kill the app?
In the end, that’s what happened.
According to The Register, Apple’s reason for chucking the app out of the App Store was that:
Currently, there is no publicly available infrastructure to support iOS diagnostic analysis. Therefore your app may report inaccurate information which could mislead or confuse your users.
Translated into plain English, Apple means that Esser was using undocumented features in iOS that he’d figured out himself.
Programmers usually try to avoid doing that sort of thing in security software, not least because undocumented features are subject to change without warning.
But in the absence of documentation, “figuring it out for yourself” is sometimes the only way forward.
Esser has hit back at Apple on Twitter, pointing out that:

iOS 9.3.2 was just released – our app still works.
In other words, Esser is suggesting Apple knew, or could have verified, that the app would still work after the next update, which plays down the risks that the app might “mislead or confuse […] users” due to upcoming changes in the undocumented parts of iOS.
Have your say
Where do you stand on this?
Is Apple’s self-contained vision for the App Store the best way forward?
Or is it time for Apple to become more open about security research into iOS, and to let third-party security developers show some threat prevention innovation in the App Store, perhaps under stricter conditions than regular apps, and after a more detailed verification process?
Opening up the low-level parts of Windows to independent software vendors worked out well for Microsoft in the early 2000s…why not for Apple, 15 years later?

Joe
Apple’s walled garden approach is beyond annoying. It’s my hardware. I bought it, and I own it, and I should be able to do anything I like with it, including burn it in a fire or repurpose it, or run whatever I like on it. I’m an adult, and have seriously outgrown the need for a nanny. I very reluctantly use iOs devices for what they do, and am very glad I can still run whatever I like on OS X, Windows, and *NIX.
Paul Ducklin
To be fair, you can’t do *anything* you like with it. (There are FCC regulations, for instance, to do with the telephone and Wi-Fi parts.)
And you can jailbreak it, or at least try. Apple, in turn, can try to stop you, but they can’t sue you if you succeed. (IANAL – I am pretty sure they can’t.)
It would be nice, IMO, if Apple would voluntarily meet the jailbreakers in the middle. Even if they made you formally give away your warranty, where that’s allowed by law, so that thoe who are merely inquisitive would be discouraged, I reckon it would help us all. The jailbreakers could get on with finding security holes and reporting them quickly to Apple for everyone’s benefit, instead of sitting on them until an opportune moment, knowing Apple will unilaterally close them anyway.
linacguy
Joe, sounds like an android device might be more to your liking?
Marc Zimmermann
As far as I am concerned, walled garden approaches are unacceptable. I’ve “grown up” in the Windows Mobile ecosystem (the Pocket PC era, not Windows Phone) and always been able to “sideload” whatever I wanted to. When I was looking for a new platform to turn to as Microsoft dropped all binary compatibility with its new mobile OS, the closed ecosystems were no-gos for me. Even though I pretty much always keep my Android devices to permit only Google Play supplied apps, I can easily change that if I want/need to for some special app (e.g. Amazon Prime Video). I simply can’t accept that the device vendor wants to decide which apps/content I’m allowed to use.
Paul Ducklin
Of course, in the Android ecosystem many device vendors decide what pre-installed apps you aren’t allowed to remove…which is not quite the same thing, but takes a silver medal in lack of openness. Thus the active “rooting” scene on Android – it’s not quite jailbreaking, but it’s close.
Thomas Bodrey
It depends on the vendor, some include a lot of bloatware, and some are known to include little to none; aka, specialty, not-so mainstream vendors like one plus, for instance. And on most Android devices, the user has the ability to install custom recoveries and custom ROMs. Sometimes you can do that without rooting by using the hardware features. For instance, Samsung/LG has a “download mode” recovery option much similar to dfu mode on Apple iCrap, only without needing the software to be “signed” by Apple. If your Android device feels like an iPhone, aka, very limited, has tons of bloatware like stocks, iBullshit, and s’moreiBullshit that you can’t remove, you can jailbreak or root and remove them. However the beauty of Android devices is that you can install a custom recovery and a custom ROM like Cyanogenmod and not put up with that crap at all.(Sidenote: I have TWRP recovery and CM13 on my LG G3 and it is great, it’s based off of Android 6 and is how to get the next Android months before the OEM releases it… I did it, however, because I ran a Verizon update and it pretty much messed up my phone, so I installed a custom ROM and voilà, no bloatware or restrictions from the OEM or the carrier). And, custom ROMs usually come with root so you can customize them as you will, freely. You’ll get no better mobile control on a phone or tablet than on one with a custom ROM and recovery. And for those reading this, who are interested in security without the walled garden, or someone’s approval, you don’t need root or a custom ROM to install antivirus. Lol 😉😂.
gldriggs
IMHO, it’s less hassle to just buy a Nexus or OnePlus device so you can start with a cleaner baseline & stock Android experience.
Anonymous
Wow. Just wow. Apple really needs to ditch its “view” on security. Remember MacDefender? Apple said “No malware” In my book MacDefender = malware. They also removed Intego’s VirusBarrier from the App Store in 2014. Yet again, exposing their users to security risks because they want to have a monopoly. The “MacDefender” issue is going to happen all over again isn’t it?