
A controversial hacking company recently ran a competition offering $3m for up to three click-to-own exploits against Apple’s iOS. The exploits would be sold on to “eligible customers” only.
The competition is now closed, but one exploit apparently met the grade and will earn $1,000,000.
We investigate: what “click-to-own” means, why exploits of this sort are valuable, and whether this sort of competition works for the greater good.
Whether you’re a cybercrook who wants to spread money-making malware…
…or a warrant-wielding law enforcement agent trying to investigate a person of interest using surveillance software…
…there are two techniques that stand above the rest for delivering your payload.
The big two are: open-and-own, and click-to-own.
They work just as the names suggest.
Invisibly-delivered exploits
Open-and-own means you can send your victims a believable-looking document: a pay slip, an invoice, even an innocent-looking research paper.
When they open it, the application crashes in such a way that a tiny program hidden in the booby-trapped document takes over.
Your victims probably won’t even notice, especially if you rig up the attack so that a second, completely genuine, document pops up instead.
And click-to-own is the same sort of thing, but using a web link or phone message.
Visit the page, view the content, and – pop! – in the background, a tiny program hidden in the booby-trapped web page takes over.
Indeed, whenever you install security updates that say something like “this fixes a remote code execution flaw in {your browser, the image file viewer, your word processor, the video player, the font rendering software}”, you are patching exactly the sort of bug that could be used for click-to-own or open-and-own.
Click-to-own on iOS
One platform has been surprisingly resilient to this sort of attack in recent years: Apple’s iOS.
Apple has a triple reason for making it hard for you to “reprogram” your iPhone or iPad at all, let alone to do just with just a booby-trapped file or web page:
- Security. Whatever you think of the company’s policy on commercial lockdown, Apple prides itself on the safety and security of iOS against malware, especially compared to Android.
- Control. Apple doesn’t let partners make rival iDevices or derived operating systems, so Apple iDevices can only run iOS, and iOS can only run on iDevices.
- Software sales. Apple doesn’t allow software from third party marketplaces. So iOS is locked down so that you can only shop at the company mall: the App Store.
Apple’s success in the strictness of its lockdown has even led to a difference in vocabulary.
Users who take control of a locked-down Android device are said to have rooted it – slang for “getting admin-level access” (named after the admin account, called root).
But doing the same thing on iOS is jailbreaking, because it’s generally a lot tougher to do, by design.
Most iOS jailbreaks require physical access to the device, plus a cable connection, together with a fair bit of noticeable fiddling around – not the kind of thing that suits the average cybercrook or investigator.
The last click-to-own jailbreak for iOS was back at iOS 7 (we’re now at iOS 9.1), and once jailbreak holes are known, Apple typically patches them fairly quickly.
Enter Zerodium
Enter Zerodium, a recently-formed, controversial hacking company that offered up to $3,000,000 for jailbreak exploits.
Starting from 21 September 2015, the company offered to buy up to three full-on click-to-own iOS vulnerabilities for $1m each.
Zerodium’s founder is Chaouki Bekar, formerly of controversial bug-finding company Vupen.
Vupen figured out exploits – with some conspicuous success, winning numerous bounties in the PWN2OWN contest.
The company also sold on exploits to customers that reportedly included the NSA, the German BND and epic-security-fail Italian hacking company Hacking Team.
Vupen closed earlier this year, and Zerodium opened up in its wake, calling itself a “vulnerability and exploit acquisition program,” rather than a team of bug finders.
Loosely speaking, then, Zerodium, is pitching itself as an exploit broker: you sell them your exploit and they sell it on, presumably for a profit, to “eligible corporations and organisations.”
Officially, Zerodium says no more about its eligible customers that to describe them as an undisclosed list of “major corporations in defense, technology, and finance, in need of advanced zero-day protection, as well as government organizations in need of specific and tailored cybersecurity capabilities.”
Anyway, it seems that one of the $1,000,000 payouts has been claimed.
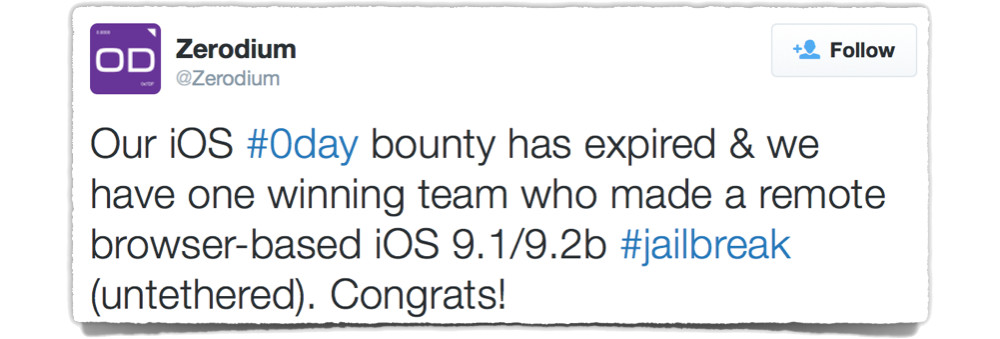
Unofficially, for now, the company is claiming via Twitter that:
Our iOS #0day bounty has expired & we have one winning team who made a remote browser-based iOS 9.1/9.2b #jailbreak (untethered). Congrats!
What now?
That’s hard to say.
If the exploit is real, and you’re one of Zerodium’s defensive-capability customers, you’ll no doubt want to tell Apple so that the company can work on an official patch.
But Zerodium’s offensive-capability customers won’t want you to tell Apple, because an official patch would close the hole for everyone.
Indeed, we’ll assume that your contract with Zerodium would prevent you telling Apple, thanks to some sort of NDA (non-disclosure agreement).
If so, that NDA could end up reducing your security rather than boosting it.
Oh,what a tangled web we weave, when first we practise to buy in security information that we can’t then use as we might reasonably need to…
Of course, this could all be be smoke and mirrors.
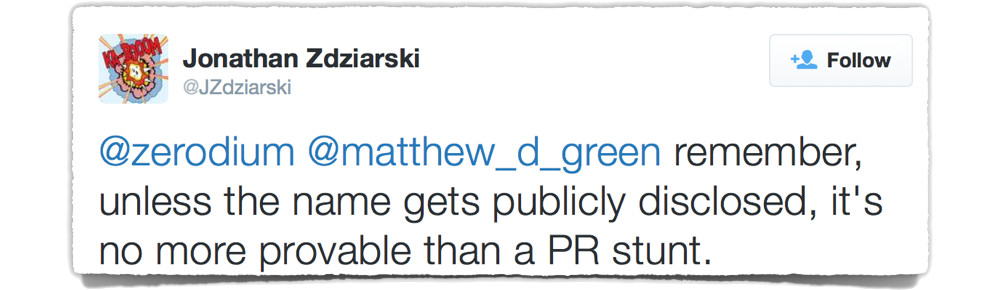
As well-known security researcher Jonathan Zdziarski replied to Zerodium’s tweet:
Remember, unless the name gets publicly disclosed, it's no more provable than a PR stunt.
Where do you stand on all of this?
Have your say in the comments below.
(Simply leave the name field blank if you wish to appear as Anonymous.)
Phone imagery courtesy of Shutterstock.


jandoggen
So, even in this area, we now have ‘companies’ who only sell/resell without adding any value in the chain – just increasing the price.
justiceISfake
I think its greedy if it is real and hinders security for everyone… but that is what runs the USofA. Otherwise we wouldn’t have Trump/Clinton’s/Bush’s/etc making a mockery of the political system.
Mark Stockley
Or iPhones
justiceISfake
Android devices are already insecure as a majority due to fragmentation but yes this specifically related to iPhones not everyone
Mark Stockley
Ah, I was messing with you: I meant to say that what “runs the USofA” delivers what you said, and it delivers iPhones too :)
But, putting my sensible hat on, yes this after-market it zero day exploits is worrying indeed and bad for security. There isn’t a bug bounty program in the world that can compete with a $1m prize.
LonerVamp
Company offers huge bounty for security holes. People submit unknown security issues to them. Company walks away with lots of new, unpatched goodies. I don’t much care what they do about the payout, but…
saxonrau
Of course if one were to also submit the exploit to Apple under strictest confidence for a further bounty one could likely increase ones profits significantly. Ditto ditto for any one of a number of national security enterprises…
Let’s hope greed overcomes the bug finders eh? They would be in breach of a contract naturally but if they were overly bothered with legal niceties they wouldn’t be hacking computers for a living and selling the results…
Mahhn
Criminals are so bold these days. Publicly buying hacks to sell to those that would commit crimes with them. The world is full of evil greedy people. May they choke on the ashes of their victims.
jejaffe
On the third hand the company could offer the exploit to Apple under an NDA for more than a million dollars and make a profit as a middle man.
Fourth – Apple may have contracted with the company to offer the prize as a proactive “red team” defense. Maintaining its hard-to-hack status is worth much more than three million dollars.
Jonathan @NC3mobi
roger
i currently have an iphone 6s with the “Apple fixed updated 10.3.1” guess what, im still hacked! double check your phones….