What if the security controls added by Facebook to make it harder for snoopers and ne’er-do-wells to attack the company’s servers…
…makes things harder for researchers who are trying to hunt for bugs legitimately?
That’s what’s been happening, bug hunters have told Facebook via its Whitehat survey.
Nearly all Facebook-owned apps make it as hard as they can to stop tricks such as Man-in-the-Middle (MiTM) attacks, which could allow rogues in your local coffee shop to spy on you, but this also makes it tough for ethical hackers and security researchers to intercept and analyze network traffic to find server-side security vulnerabilities.
That’s why Facebook decided to help them out by giving them Researcher Settings so they can dial back their connection security and pretend that it’s still 2009.
Facebook’s Whitehat Settings
Facebook’s Bug Bounty program announced on Friday that it’s implemented what it’s calling Whitehat Settings.
These “backed off” connection settings will help security researchers analyze network traffic on Facebook, Messenger and Instagram Android applications – on their own accounts, that is.
In other words, these less secure settings don’t affect other people using Facebook, and don’t let researchers spy on traffic that isn’t theirs to start with.
The new settings allow researchers to run Facebook’s mobile apps in “watch what happens” mode by:
- Disabling Facebook’s TLS 1.3 support.
- Enabling proxying for Platform API requests.
- Using user-installed security certificates.
Facebook recommends that in order to ensure that the settings show up in each mobile app, researchers need to sign out from each mobile app, close it, then re-open the app and sign in again.
The sign in process will fetch the new configuration and setting updates you have just made. You only need to do this once, or whenever you make changes to these settings.
Keep in mind that these settings reduce the security available for apps. That’s why the social media platform advises researchers to turn off the settings when they’re not bug-hunting:
For the security of your account, we advise turning these settings off when not testing our platform to find Whitehat bug bounty vulnerabilities.
One security researcher, at least, thinks the Whitehat settings are a “cool idea”:
Facebook rolled out "Whitehat settings" to help analyse traffic in its mobile apps (for #security #vulnerability testing). Such a cool thing to do!https://t.co/AV6KSdzX16#infosec #bugbounty
— payloadartist (@payloadartist) March 23, 2019
Naked Security’s own Paul Ducklin put it like this:
Facebook is helping security researchers have their cake and eat it, too. By default, you’re protected against other people sniffing out your network traffic, which stops them seeing what data you’re sending to Facebook. But now you can carefully snoop on yourself when you need to, so you can see how Facebook is sending your data. That’s good for security, privacy and transparency.
How to put on your Whitehat
Facebook’s new Whitehat settings aren’t visible by default. Rather, bug hunters have to explicitly turn them on, which you can do here.
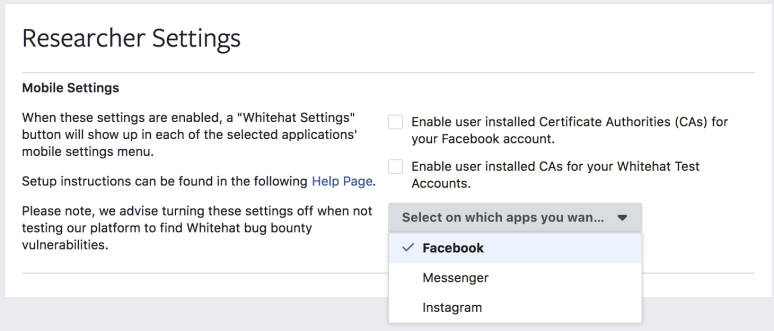
You can also get setup instructions, including video tutorials, on this help page.

Anonymous
Typo: “Ass Naked Security’s own Paul Ducklin put it:” should say “As Naked Security…” There’s an extra s in as.
Paul Ducklin
Q. How can you be sure the typo wasn’t a missing hyphen (“ass-naked”) and not an extra letter (“ass” for “as”).
A1.. The sayer of the quote says so.
A2. The speed it was changed.
A3. The fact that we changed it to get the word “as” out of there entirely.
Jerry
Well, it is called Naked Security, so one would expect (ass-)naked writers.
Paul Ducklin
I’m sticking to my story. You have to take my word for it – I was there!
Lisa Vaas
Favorite typo ever.
Paul Ducklin
Well, technically, *you* wrote that bit. (Though I am obliged to admit that I typed that bit into the text myself, oh dear me, hahahaha.)
Steve
It was indeed a tasty morsel, made ever so much more delicious by the source being named “Naked Security”!