As far as Google is concerned, unencrypted HTTP web connections should be nearing the end of the road.
In 2014 at the I/O conference, it declared “HTTPS everywhere” as a security priority for all web traffic, followed in 2015 by the decision to downrank plain HTTP URLs in search results in favour of ones using HTTPS (where the latter was available).
A year ago, it started labelling sites offering logins or collecting credit cards without HTTPS as ‘not secure’.
In a symbolic moment, it has now confirmed that with the release of Chrome 68 in July, this label will be applied to all websites not using HTTPS.
It’s a small change that streamlines the slightly confusing way Chrome denotes the presence or absence of HTTPS in address bars. From July, the ambiguous grey ‘i’ icon used to tag many non-HTTPS sites today will be supplemented by a clearer ‘not secure’ label. This will look like:
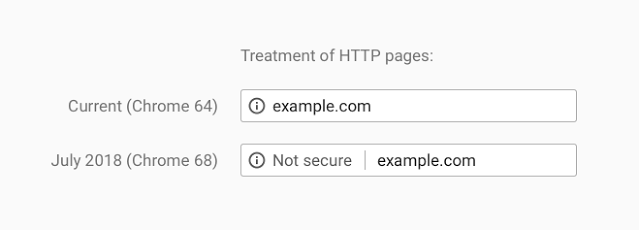
Other browsers (Firefox, Edge, Opera) rely on green or grey padlock symbols to denote HTTPS sites, dropping back to more than one type of grey icon for non-secure HTTP.
But Google’s Chrome is the only one to use words and not simply symbols and colours to denote the use of HTTPS. Explains Google:
Chrome’s new interface will help users understand that all HTTP sites are not secure, and continue to move the web towards a secure HTTPS web by default.
Getting there?
A look at Google’s figures suggests this strategy of coaxing website owners and users to see HTTPS as important is working, with 68% of Chrome traffic on Android and Windows connecting to HTTPS sites. Eighty-one of the top 100 web destinations use it by default.
Some surprisingly big sites such as the BBC apply it inconsistently, using HTTPS for its homepages but dropping back to HTTP for individual content pages (compared to, say the New York Times, which uses HTTPS for everything).
But as more and more sites adopt HTTPS, history suggests getting the last few percent of holdouts to sign up might take a while.
Google’s other problem is the old adage about being careful what you wish for: criminals have been seen to exploit HTTPS to gain the trust of users.
No matter how worthy Google’s dream of HTTPS everywhere, there’s still a lot of work ahead.

Mahhn
If say, I have a web page that I post images and text on, no log-in for visitors, no shopping cart. What would be the point of using https?
Paul Ducklin
Integrity and authenticity.
HTTPS/TLS isn’t just about confidentiality (which is what most people think of when they hear the word encryption), but about stopping imposter sites, and about stopping servers between the website and your browser from tampering with what gets delivered. Without HTTPS, your website could become the perfect disguise for crooks at a coffee shop to deliver malware, trick trusting users into downloading fake files, and much more.
In some jurisdictions, you are obliged to lock your car when you park and leave it unattended – whether you care about it being stolen or not. The idea is to reduce the ease with which joyriders can make off in it and harm others. HTTPS has a sort-of public order side to it along those lines, too.
gilzow
“Integrity and authenticity.”
Except that is not correct. I can get a cert from Let’s Encrypt but that does not prove my authenticity. https just means you have a certificate, and can encrypt the communications. Authenticity only comes into play if you have purchased an Organizational Validate certificate or an Extended Validation certificate. Most of what Let’s Encrypt gives out is a domain validated (DV) cert which does no validation on the entity requesting the certificate.
Let’s Encrypt issue a DV cert to anyone (including bad actors), and in a couple of instances have issued certs to people they shouldn’t have. Also, having ssl/tls on your site does *not* make the site secure. All it does is encrypt the connection between your end user and your server that handles the decryption (which may or may not be your web server). The site itself could be completely insecure.
I’m not saying I disagree with the idea of encrypting all traffic, but what I worry about is what you’ve just exemplified: people thinking https means the site itself is “secure” and it doesn’t.
Paul Ducklin
It says nothing (OK, next to nothing about the site’s security). But a TLS certificate does provide *some* accountability and it means that what leaves the server reaches you unmodified.
So my opinion is that you are still way better off than with plain HTTP.
ejhonda
Completely agree with the “what’s the point” perspective for some websites. I run two car club websites, no PII, no state secrets, no logins – just info for folks who are interested in joining or participating in events. Both are non-profits and any added cost is a burden – which is what most hosting wants for adding SSL to your site. I’m a security professional and even I think this is overkill for some sites.
Jeremy
Let’s Encrypt, free encryption, no added cost, no burden. You don’t even have to renew each year. It is automatic. However, as previously mentioned it is only a DV cert.
Scott Johnson
As long as the sites still load – good, I’m on a chromebook and have no option but to use chrome. Google downranking plain http is just not right but I guess their search results have nothing to do with the quality of the information at the site. One more reason to use duckduckgo.
Paul Ducklin
Seriously? You care about privacy and protection from data collection and surveillance enough to use Duckduckgo, but you think that trying to stamp out unprotected HTTP traffic is “just not right”? Does not compute!
Steve
Scott did not say that “trying to stamp out unprotected HTTP traffic is “just not right””. Rather, he stated that “Google downranking plain http is just not right”. BIG difference.
If Google chose to display search results with a big flashing red highlight to indicate they were not secure, WITHOUT tinkering with the ranking of the search results, then fine. But for an outfit whose success and reputation are built on the effectiveness of their searches to actually modify the search results is essentially the same as altering facts to fit their narrative.
Paul Ducklin
Except that HTTP sites really are insecure, compared to HTTPS. Anyone can tamper with the content aong the way, which has the same utlimate effect as hacking your server and changing the files on it. There is essentially nothing you can trust on an HTTP page. If you insist that Google is “altering facts to suit its narrative’…then, seriously, you need to find something more pertinent for which to criticie Google. Put another way, why should the many sites that have made an effort to respect their readers that bit more not get upranked?
If Google or its partners stood to squeeze you for $99/year for the certificate you needed to get the higher ranking, your point would be well-made. But now that certificates are free, I think your moan has evaporated.
s31064
I completely agree that https is not only a more secure communication channel (it says nothing about the site’s content), but that in today’s world, anyone that puts up a site without it is just plain nuts. However, to say “Put another way, why should the many sites that have made an effort to respect their readers that bit more not get upranked?”, is ludicrous. Google may have it’s fingers in many more pies (too many, in my opinion), but their primary focus, and the focus of this story, is their search engine. When I search, I want results based on my search criteria, not some arbitrary ranking based on some trumped up rules that could benefit the search engine in some way. Give me the results in the proper order, and I will make the decision as to what site I go to.
Larry Marks
> A look at Google’s figures suggests this strategy of coaxing website owners and users to see HTTPS as important is working…
Coaxing, or bullying. There are a lot of sites run by small non-profits that simply deliver information, soliciting no information at all–no logins or credit cards. Some are humanitarian, religious, or address obscure diseases. Price of a certificate+renewal can be burdensome. Even a free certificate from Let’s Encrypt can involve consultant fees due to the unnecessarily complicated process that is required. This seems to fall into the category of features users don’t need.
Paul Ducklin
Humanitarian, religious and “obscure disease” sites really ought to care more about confidentiality, integrity and authneticity than that. All websites solicit information, *by definition*, because HTTP is a “client speaks first” protocol. The cost of adding a TLS certificate these days, compared to the cost of having a purposeful website that doesn’t have regular outages, seems pretty tiny to me.
mike@gmail.com
What exactly about running an encryption scheme stops your website from having outages? Really curious to hear this…
Mark Stockley
He didn’t say that running an encryption scheme stops outages.
Duck said “The cost of adding a TLS certificate these days, compared to the cost of having a purposeful website that doesn’t have regular outages…”
He’s saying that the financial cost of creating a website that is both interesting and reliable (does not suffer outages) is non-zero. The additional financial cost of adding HTTPS is insignificant.
I agree.
In my experience the biggest cost, *by far*, when producing or maintaining a website is in the coding and/or content creation. The cost of hosting and DNS is at least an order of magnitude less, often many more. The cost of adding HTTPS on top of that is tiny. On my preferred web host a Let’s Encrypt TLS certificate can be added, by ticking a box, for $0 and about two minutes of my time logging in and navigating to the right screen. A certificate from another vendor can be added for ~$50.
Paul Ducklin
What he said I said,.
Larry Marks
This clownish maneuver on Google’s part demonstrates ignorance of basic user interface principles, namely that the user should never be surprised by the software behavior.
Here’s an example. My work sometimes involves looking up a series of items (patents). I use Google Patents and the Google Chrome browser. The long URLs end in a seven-digit US patent number.
The easiest way to move from one patent to the next is to click on the URL bar, backspace over the last few digits, and enter the next ones. With Google’s”clever” scheme, as soon as you do this, the place where you are entering data jumps an inch to the left, because the Secure/Insecure indicia is in the same field as the URL, not a separate one.. It’s very disconcerting.
It seems to be an instance of usability sacrificed for poorly thought-out security.
Bryan
Larry, Google’s 100% encryption goal is separate from the usability of the browser.
However, I’m with you on the layout being unfortunate. Since GoDaddy dumped their multi-DNS manager, updating DNS lies somewhere between excruciating and infuriating. I discovered the URL contains
…/manage/(example[dot]com)/dns
or something like that, and changing the url will drop you right into the tool you need. It’s stupid clumsy but better than ClickClickBackClickClickClick. I feel your pain buddy.
Judith Bakley
Let me guess, Paul, you work for Google? Stop thinking that your opinion is more important than everyone else’s. I will NEVER get a https site due to the extra cost. If we HAVE to get it, the price shouldn’t be so high.
Paul Ducklin
Well, Let’s Encrypt will sell you a TLS certificate for the princely sum of $0, so if you want it any cheaper than that, you’re asking to be given money and a certificate.
If your objection is that “it’s hard”, well, so is installing an operating system; configuring a web server; checking that it’s secure; creating some content; complying with all the relevant laws to do with things like cookies, data retention and so on; purchasing bandwidth to serve it to your users; and investing time in the online community you’ve created.
Moaning about the cost of a free TLS certificate is a bit like moaning that you are expected not only to have rear seatbelts fitted to your car, but – Lord forfend! – to insist that your passengers wear them, too, even though they are an imperceptible imposition and improve everyone’s safety enormously.
John E Dunn
Equally, hut how much will it cost if Chrome users stop visiting your website because they see the words “not secure” in the address bar?
Mark Stockley
In fact, there is *already* a cost to not using HTTP.
HTTPS has been a ranking factor for Google Search for three and a half years so, all other things being equal, pages from sites using HTTPS will rank higher than pages from sites using HTTP.
What’s the cost of a being a few places lower than you otherwise would be in the search rankings for your most popular search term? It’s not nothing and, whatever it is, it’s ground and revenue ceded to direct competitors.
Anonymous
Weel, Judith, if you NEVER go HTTPS I can guarantee that myself and many others will NEVER visit your site. Food for thought, mayhap?
Jeremy
So if all pages need to be https, what is Google’s solution to captive portals and https…
Paul Ducklin
You’ll get a warning if a site doesn’t use HTTPS – just like I’ve been getting on Firefox for ages now. What you do with that warning is still up to you.
mike@gmail.com
This is stupid, but it may be a necessary stupid. It also may drive users away from Chrome and into IE.
Dave Waddell
Actually, you can get HTTPS, and more, for free and with no effort on your part. Just go over to Cloudflare and sign up for them to take care of your name service. Not only will they do name service for free but you can also get a TLS certificate, and they automatically create HTTPS for you AND cache all of your data on their servers around the world.
PS I have no affiliation with Cloudflare except as a satisfied customer for all five of my websites.
Anonymous
This is the reason I use chrome as default, but keep Firefox focus, as a alternative(it’s like a private browser tab on steroids) If I need to go sensitive, I use chrome, if I don’t give a dam, but no ads, and fast response, I use focus. In Android, I can start both, in split-screen mode, with one icon( no moving the app to set it up) using a app called split-screen creator. You can still have the best of both worlds, no matter new rules.
Bryan
That sounds neat.
…except the thought of my Tiny Android Screen(TM) reduced to 50% size because of apps sharing the space.
Anonymous
Seriously why are people making this out to be bigger than it should be? Its a small change that just simply states factual information about the site to the user. If its HTTP is insecure.. simple as that no arguments to be had. Some people really do find the truth hard to swallow.
A point that was raised is cost, but as pointed out you can easily obtain a certificate for $0. In any case, the sites that still use HTTP are not being interfered with in any way shape or form, you are still able to browse these sites just as you have been for the last how many years? All that has changed is a factual notification to say its insecure.. which it is.
Its a good thing that sites are moving to HTTPS and this is a good way of doing it, a gentle nudge in the right direction by bringing light to what is fact, HTTP = insecure.
Another point is some say it is a unneeded feature, but once again as previously pointed out its something that stops data from being injected into pages during transfer and various other advantages. Useful? Yes, because as soon as you become a victim of such attack you’ll be wishing there was a small bit of effort put in so it could have been avoided in the first place. One example used was that of a car seat belt. 90%-99% of you time (you could say) a seat belt is never ‘used’ however when the day comes that it is, you’re very thankful it was there.
s31064
“All that has changed is a factual notification to say its insecure.. which it is.”
No, that’s not all that’s changed. If that was the only problem, I doubt there’d be more than five comments on this article. What’s changed (and not all that recently, unfortunately) is Google’s high and mighty attitude in deciding “You’re not playing by the rules that we want to see, so we’re going to penalize you by dropping your ranking into the toilet.” That is costing perfectly legitimate websites a lot of traffic. (How often do you go to sixth, seventh, or umpteenth page in a search?) It’s my website, and I’ll decide how I run it, and when I’m searching, I want results based on facts, not the arbitrary decision of a company that makes Microsoft look like Miss Goodie-Two-Shoes.
Paul Ducklin
AFAIK, that change happened some years ago already. This article isn’t about that change. It’s about wording in the browser to remind you that the site you are looking at is one of a dwindling minority that hasn’t bothered to apply even the most modest form of tamper resistance for its readers.
Mark
Serious question…
if your website offers nothing to download, no login forms etc. If it’s just a website for you to read something, does it need HTTPS / a CA?
s31064
Short answer, yes. HTTPS helps guarantee that what you’re delivering to the client is what’s on your website, not something that was interfered with in between website and browser. It DOESN’T guarantee that what’s on your website is secure and malware free.
What your question implies is what many people believe; reading a website occurs on the website. Anytime you look at a website, you’re downloading a bunch of code from the website to your computer that will get viewed in your browser. It’s not like RDPing into a file server and reading a Word doc locally. It’s more like mapping a file server and reading a Word doc using the Office on your PC.
Jay
Google, probably the most privacy violating entity around the Internet is concerned with HTTPS?
Mark Stockley
Consistently over many years, yes.
Mike T
Does any one know how Chrome would handle redirected sites? For example, if I had a site http COLON SLASH SLASH insecure DOT example that redirects to https COLON SLASH SLASH mysecuresite DOT example; do I need to get an SSL cert for that first domain? I have a number of domains that simply redirect to a main site.
Paul Ducklin
If you are serious about using HTTPS, the answer is, “Yes.” You need a TLS certificate for your redirector sites, too. Otherwise your redirections are insecure and could be rewritten to send a visitor off anywhere (inlcuding to an HTTPS site run by the crooks).
(Remember when banks had those “secure areas” where they put their ATMs in order to keep them well-illuminated and stamp out skimming? Then they put an automatic door in front of the secure ATMs to stop vagrants wandering in at night and kipping on the floor, and they made you swipe your card to enter the “secure area”, to discourage casual entry? Guess where the crooks put their skimming devices?)
Mark Stockley
Everything Duck says in his reply plus… please add HSTS.
ShotRu
Next step: prevent access to any resource that is not secured by DNSSEC. For instance, sophos.com.
Paul Ducklin
I think we’re as far from global DNSSEC as we are from IPv6.
David Smyth
I’m pretty sure that there is a non trivial overhead for making a TLS or HTTPS connection. This is asymmetrical encryption after all. Not a problem when connecting from a laptop or desktop PC, but it takes processor effort for a mobile device. Not everyone has the latest generation smartphone with a beefy CPU. Checking public information like flight arrival times, bus and train timetables, etc. can take out the battery life of a run of the mill mobile phone if everything required full encryption.
brad
Incredibly the websites I have the most trouble with as far as showing not secure are yahoo and aol!