We’ve had a steady stream of questions about BlackNurse in the past few days, so we thought we’d answer them all in one place.
Here goes.
What is the BlackNurse attack?
BlackNurse isn’t really an “attack”.
It’s more of a reminder of why DDoSes work: if you bombard the network port on a router with lots of redundant packets, you force the router to do purposeless extra work.
The extra work steals some of the router’s performance away from legitimate users, and thus legitimate traffic gets held up in the snarl.
Unfortunately, if you pick your time-wasting packets carefully, you may be able to find some router models that do even more extra work than you might expect in order to dispose of your malicious traffic.
At that point, you can cause additional harm to those routers, simply by picking the content that makes them work hardest.
BlackNurse’s “extra harm” traffic turns out to be a special sort of network packet known as an ICMP reply, short for Internet Control Message Protocol.
How does BlackNurse work?
BlackNurse works by sending fake control message packets to your firewall or router.
As you can imagine, there are many types of ICMP message in common use, denoted by two byte-sized data values in the packet known as Type and Code, such as:
- ECHO REQUEST (Type 8 code 0). Sent out when you use the
pingcommand to see if another computer is online. - ECHO REPLY (Type 0 Code 0). Sent back by the computer you pinged to confirm it’s there.
- TIME EXCEEDED (Type 11 Code 0). Your connection didn’t get through fast enough.
- HOST UNREACHABLE (Type 3 Code 1). You’re trying to connect to a server that doesn’t exist.
- PORT UNREACHABLE (Type 3 Code 3). The server is there but the service you are trying to connect to isn’t running.
An example of a Type 3 Code 3 ICMP error is when you try to look up a domain name such as sophos.com by asking a computer that isn’t a DNS server.
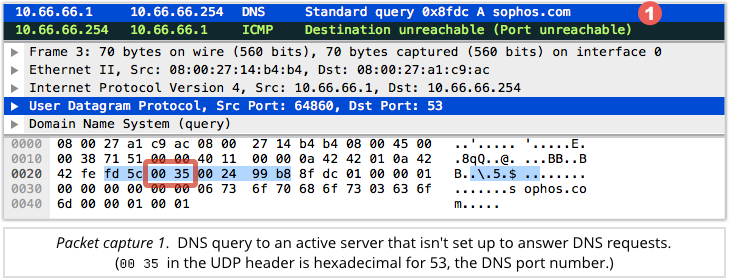
Technically speaking, your computer will send a UDP request to port 53 of the DNS server, but that server won’t be processing requests on port 53, so no DNS reply will ever come back. (You can think of the server as a PBX, and the port as a telephone extension.)
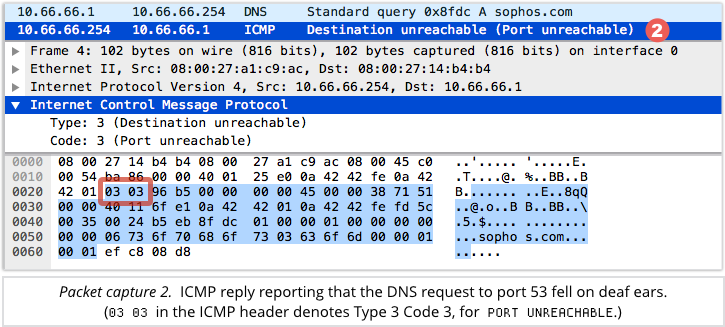
To help your IT team troubleshoot the problem, the server sends a PORT UNREACHABLE message using ICMP.
If your network is set up to accept ICMP messages, that gives a handy hint of what went wrong: to continue with the PBX analogy, you got through to a working switchboard, but there was no extension 53 connected.
The creators of BlackNurse found PORT UNREACHABLE messages to be troublesome for some firewalls.
Why PORT UNREACHABLE messages in particular?
We don’t know, other than that those messages in particular happened to produce a newsworthy result.
It’s important to remember that even if a firewall quietly discards certain packets, it still has to look at them, albeit briefly, to decide that it isn’t interested.
The BlackNurse “attack” apparently needs about 50,000 packets per second, which works out at a whopping 180 million packets an hour.
That’s the sort of load that is going to put any modestly-sized router under pressure, regardless of the packets involved.
That’s why even the most basic denial of service attack is illegal in many countries: forcing someone’s network to process an hourly load of 180 million packets when you have no intention of making legitimate use of that network’s services is deliberate harm, and that’s that.
The creators of BlackNurse, however, found that a small selection of firewalls required more effort than usual to deal with Type 3 Code 3 packets compared to other packet types; the extra effort involved was apparently just enough to make those firewalls unresponsive rather than merely slow.
Is that all there is to it?
Yes.
By pushing out enough malicious traffic to slow down most routers anyway, you can make some routers slow down enough to cause trouble.
It’s a bit like flinging bricks at a selection of modern household windows: they’re not plain glass, like in the old days, so they won’t shatter.
Some of them may crack badly enough to break, but they’ll all crack.
What if I think my firewall is affected?
One easily implemented response that’s being suggested online is simply to drop every ICMP packet arriving from the internet.
That will work, but you may find the cure worse than the disease.
For example, anyone inside your network using the ping command to see if a server is alive will never get a reply.
(If you look at the list above, you’ll see that ping relies on Type 8 Code 0 ICMP requests going out and corresponding Type 0 Code 0 ICMP replies coming back.)
If you think your firewall is of a sort that might get bogged dowm by BlackNurse, we suggest that you add a rule to block just ICMP Type 3 Code 3 packets, thus causing the least change in behaviour for the desired result.
Note that, according to the creators of BlackNurse, firewalls that are based on Linux and use a component called iptables to process packets are not affected.
Both the Sophos UTM and Sophos XG firewall products use iptables.
In addition, the Sophos products use the Linux connection tracker to spot that the offending ICMP replies are answers to requests that were never sent, so the BlackNurse packets are obviously bogus and can be dumped without fanfare.
In our testing we found that neither Sophos product was vulnerable to this “attack”, thus supporting the suggestion that any iptables-based product ought to be unaffected.
Why is it called BlackNurse?
It’s one of a class of what we have taken to calling BWAINs, short for Bugs With An Impressive Name.
These are security issues that have caught the world’s attention not necessarily because they are critical, or even particularly important, but because they have been branded with a catchy name and perhaps a logo.
Some of the names we’ve seen recently are witty or self-explanatory.
Heartbleed, for example, was a bug that haemorrhaged data when you used the TLS heartbeat command, while LOGJAM attacked an encryption algorithm based on discrete logarithms by jamming bogus messages into your network traffic.
As for BlackNurse, who knows?
We’re guessing that it’s black in the sense of doom, and nurse because the abused messages are very vaguely to do with network health.

Lenny Hansson
Why is it called Blacknurse ?
That is a good question we have seen a lot of talk about :-)
Well more the 20 years ago. The tow persons that discovered the attack was working in other areas. One was a nurse and the other was a blacksmith….
One from the team joked about it and called it “the blacknurse attack” This name just got stuck in the team, and every time we was working with the attack, we could just refer to that name.
That simple…..
\Lenny Hansson