A month ago, we wrote about a serious cryptographic blunder by a company that really ought to have known better.
That company was WoSign, a Chinese certificate authority, or CA.
As we explained back in August 2016, a CA’s primary job is to vouch for security certificates on your behalf.
Imagine, for example, that you want a digital certificate you can use on your website to assert your identity, or a certificate you can use to sign your software to stop crooks making imposter copies and passing them off as yours.
You can create and sign your own certificates, which is a start, but no one’s browser or operating system will trust them by default, so your users will see security warnings like this one when they visit your website:
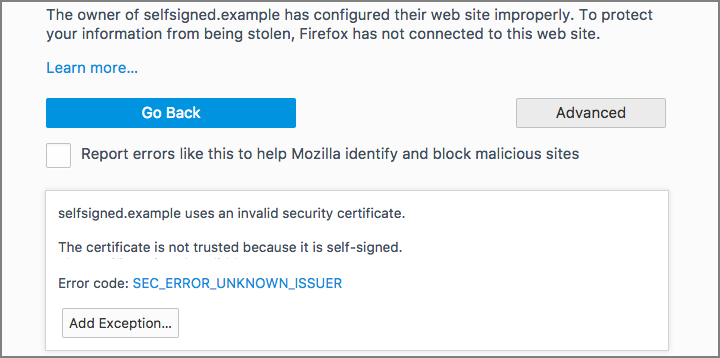
But if you create a certificate and a trusted CA signs it for you – a CA that is already on the list of trusted root authorities in your browser or your operating system – then you will automatically be trusted, too.
This chain of trust is a key component of TLS, the system that puts the padlock in your browser.
WoSign, it turned out, wasn’t very careful about how it vouched for its customers’ websites.
A user found this out when he applied for a certificate vouching that he was authorised to run a specific subdomain of the University of Central Florida, namely the medical faculty’s site med.ucf.edu.
To his surprise, he also ended up with a certificate vouching that he owned the University’s main website, at www.ucf.edu, even though that server was outside his bailiwick.
Even more alarmingly, he applied for a certificate for a subdomain he owned on the well-known public code hosting service Github, and ended up with a certificate for all of github.com and github.io, too. (He also got www.github.io, just to make matters worse.)
This all came to light in a series of discussions in Mozilla’s security policy discussion forum last month.
Commenters on Naked Security were almost universally in favour of kicking WoSign out of the privileged club of trusted CA without further delay:
Bryan: A CA should absolutely be excommunicated if they can’t can’t rapidly right their wrongs and document quite publicly that it’s being done.
Blake: If Mozilla maintains WoSign in their default trusted CA list, that’s a statement that Mozilla believes WoSign is trustworthy. Personally, I have doubts about any organization that makes repeated mistakes, and doesn’t own up to them, being included in this small circle.
Bbusschots: How can anyone have any faith in the CA system if breaches of the rule don’t have consequences? This CA literally put the entire internet at risk, and it looks to me like they simply do not understand the mangnitude of their failings.
Tony Cross: The key word here is ‘trust’. WoSign have clearly demonstrated that they can’t be trusted. That’s the bottom line.
Mozilla has now published a lengthy overview of WoSign’s failings, which go beyond just giving a random person the key to impersonate all of Github, and it makes depressing reading.
Amongst other things, it seems that WoSign also:
- Backdated certificates to beat a deadline banning the use of the now-deprecated SHA1 hashing algorithm.
- Acquired another CA called StartCom without reporting the change of ownership, as required by Mozilla.
- Denied the change in ownership when questioned.
Unsurprisingly, Mozilla’s slow-but-steady conclusion mirrors the off-the-cuff opinions stated by Naked Security readers a month ago:
Mozilla’s CA team has lost confidence in the ability of WoSign/StartCom to faithfully and competently discharge the functions of a CA.
What next?
You can probably guess what happens now, at least for users of Mozilla products based on Mozilla’s own list of trusted CAs, such as the Firefox browser and the Thunderbird email client.
WoSign gets kicked out of the trusted CA’s club, right?
Wrong.
Mozilla is still taking the softly-softly approach:
Therefore we propose that, starting on a date to be determined in the near future, Mozilla products will no longer trust newly-issued certificates issued by the [WoSign or StartCom] CA brands.
In other words, any certificates already issued will continue to be trusted, and even those that the company issues in the future will still be trusted until a future date to be set at a future date.
What do you think?
Does the CA ecosystem need a softly-softly approach that minimises disruption, or the occasional short, sharp shock that sets the strictest standards?

John C.
Clearly Mozilla is playing softball, and is doing too little to instill trust in the system. If they feel the need to give WoSign time to correct the errors, they need to set a very short horizon.
This article doesn’t mention other browsers. What have thy done about this?
Dale
I’d suggest that Mozilla, and for that matter other browsers as well, should put this decision into the hands of their users. They should pool CA certificates into 3 pools:
1) Known, trusted CA certs. These are the ones where the CA is publicly known and that the browser team has no known reason to distrust.
2) Known, distrusted CA certs. These are the ones where there is a known, credible reason to reject them. Cases where the encryption deprecated because it is known to be insecure, or the signing key is known to have been compromised would fall into this category.
3) Questionable CAs. This case would fall into this last category. Allow the user to accept all, reject all, or configure individually for each CA in this category.
This strategy would allow Mozilla to play softball by not putting a CA directly into the known, distrusted category, but to downgrade them from known, trusted rapidly.
Kyle Saia
I’m wondering what the big dogs on the block are thinking about this. did Microsoft or Apple have anything to say?
danzaph
Apple does not have WoSign in the Root CA list on OS X 10.12 so they have taken action.
NorthVandea
While my professional side absolutely advocates ending trust of the offending CA immediately for maximum security protection. Lets play this out logically for a moment:
1) Mozilla kicks WoSign out of the trusted CA club immediately
2) Every company who purchased WoSign certificates in good faith find themselves with instantly invalid certificates
3) A customer visits a company’s website buy something for example, and they’re greeted by the increasing scary looking certificate error message and get scared and opt to purchase said item elsewhere
4) While instantly cutting of WoSign will harm the offending CA, it will do much more immediate damage to WoSign’s customers. A company simply trying to do the right thing an use HTTPS and trusted certs everywhere will find themselves losing customers due to circumstances completely outside their control.
When you really think about this Mozilla would do far more immediate damage to innocent third-party companies then they would for the naughty CA; therefore they need to give those companies a chance to get off the crappy CA and move to a better one, and that for most companies is not something they’re prepared to do with 1 business day of notice.
Goose@gmail.com
You’ve missed the point entirely, it’s not about punishing the CA or the CA’s ustomers, it’s about protecting users and the fact the system has failed.
How much notice do these companies that host WoSign certs need then, whos taking the responsibility of notifying them that the certs they use are inadequate?
The lack of action taken by Mozilla is pathetic and even worse so for Google, Microsoft etc who have done nothing.
clifford cuellar
ALL certificates signed by the [WoSign or StartCom] CA brands should ummedately be prefaced by a warning message. Such a draconian measure, while causing immediate short-range problems, wtll force the [WoSign or StartCom] CA brands to immediately get their house in order and restore trust in the system..
Blake
I believe Mozilla’s approach is very well reasoned. While it may, at first indication, seem soft, the proposed solution is the best possible one to act in favor of both improved security and user experience.
Ripping out WoSign/Start CA entirely would immediately invalidate many SSL certs. This would A) Cause urgent issues for site/server admins, B) Create user experience problems, and C) train even more users to blindly trust certs that are otherwise untrusted. This would hurt security and hurt users.
Mozilla’s proposed solution to trust existing certs, but not trust WoSign/Start certs issued after a given date, revoking known bad certificates (~50 of them), and not trusting any future audits conducted by the Ernst and Young of HK auditors removes the urgency for admins, improves user experience, and acts as a warning against these types of actions in the future. This improves security while maintaining continuity for admins and users.
The only stronger action I see possible is to put a lifetime ban on all WoSign directors & officers from working in a CA in the future. However, I suspect that if any of these individuals is hired or starts a new CA that they will be highly scrutinized to ensure that lessons have been learned and are not repeated.
Bryan
C) train even more users to blindly trust certs that are otherwise untrusted.
Hear hear! Conditioning users to blithely dismiss alerts has already made amazing progress with UAC, and we don’t need any more of that.
Peter Nelson
Calling this a “softly-softly” approach is, I think, misunderstanding the situation:
– Distrusting the CA and distrusting them over a year-long period will have roughly the same effect on WoSign/StartCom. This will totally devastate their business.
– Completely distrusting a CA (including already issued certs) negatively impacts lots of consumers. This leads to the “too big to fail” problem. A small CA could be vulnerable to this ban-hammer, but a really huge CA can rest easy knowing that no one will distrust them, no matter how crappy they are. This action by Mozilla (which is possible to enact in part due to certificate transparency) sends a message to big CAs that they are vulnerable too.
Todd
What has Microsoft and Google done about WoSign though?
Marvin
Those of us concerned can always remove the Wosign entries from the list of certificate authorities in our own browsers. Presumably SysAdmins can propogate something like this across a corporate network.
Industrial IT
Any word on what Google thinks about WoSign?
zengator
I’m not certain whether Mozilla will re-install the WoSign certs I just distrusted/deleted from both my browser and email client, but if they do, it will take me all of about 15 seconds to distrust them again. Preferences ==> Advanced ==> Certificates ==> View Certificates, scroll down to WoSign, select them all, press “delete”, and . . . . Bob’s your uncle.
Paul Ducklin
I do wish that Firefox’s certificate GUI would make it clearer which root certificates you’d “untrusted”. When you hit Delete, the certificate actually remains in the list but has all its trust flags turned off. If you later want to verify which ones are untrusted, you have to click into every certificate, one by one! Some sort of visual marker in the list view to flag “dead” certs would be nice.
zengator
Yes, the lack of a clear indicator is aggravating.
On the positive side: through one update (v## to v(##+1)), my choice to distrust was honored and not reverted by Mozilla.