Remember the early days of mobile phones?
You’d be watching TV, or listening to the radio, and you’d hear a sound like Chzzzt – Chzzzt – Chzzzt, and you’d know someone’s phone was about to ring.
The interference was a side-effect of your phone waking up and saying to the local network, “Here I am! You can put that call through to me here.”
Obviously, a mobile phone is supposed to give out electromagnetic radiation, but the strength and the pattern of the “Here I am” communication was especially noticeable and recognisable, even when the eavesdropping circuitry was no more sophisticated than the wiring and the loudspeaker inside some nearby device.
As you can probably imagine, you can dig much more precisely into what a phone is up to if you introduce a targeted receiver and a dedicated signal-processing computer.
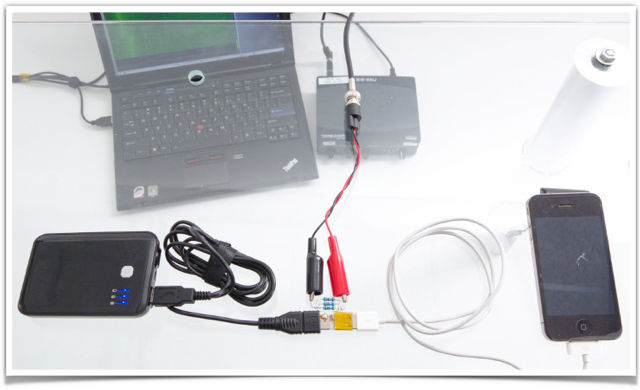
And that’s what researchers from Israel and Australia did recently when they set out to see what they could learn from you if they were able – literally and figuratively – to hide under the table while you used your iPhone:
Click on the image to see it in the original article…
The receiver coil in the photo is a magnetic probe (the researchers say it cost about $2, but you could wind your own if you wanted to) that generates a tiny and ever-changing current as the electromagnetic fields around it wax and wane.
The signal processing is done by a sound digitiser, which conveniently converts the output of the coil into a waveform that is sent over USB, and by the laptop that receives the waveform.
The researchers focused specifically on the emissions that happened when specific parts of specific software ran, namely the programming responsible for certain sorts of digital signature validation in the following cryptographic libraries:
- OpenSSL, included in numerous mobile apps.
- The iOS CommonCrypto library, the core operating system component used by a wide variety of iOS apps.
- CoreBitcoin, used by various Bitcoin wallet programs.
- Bitcoin Core, another library common in the Bitcoin ecosystem. (They got nowhere with this one.)
The researchers found that they could sometimes differentiate between two special sorts of arithmetic calculation inside the code used for a specific sort of digital signature called the Elliptic Curve Digital Signature Algorithm (ECDSA).
In particular, they could tell when the code was doing a DOUBLE (multiplying by 2) and when it was doing an ADD.
You’re probably thinking, “You can tell when the program is doing plus and when it is doing times. So what?”
Cryptographic arithmetic isn’t usually quite as easy as 2+2 or 3×5, because the numbers involved are often hundreds of digits long. The calculations are more like “multiply the number of protons in the universe by all the possible games of chess, and add the distance to Alpha Centauri in nanometres.”
But it turns out that by tracking which operations happen in what order, you can tell what’s happening inside the algorithm; those patterns, in turn, are determined by the values of the individual bits in the input.
So, if the input is the cryptographic key itself, its internal structure produces a sort-of electromagnetic rhythm that leaks information about which bits are 1 and which bits are 0.
By way of analogy, imagine that you asked me to add up a long column of digits aloud, one by one, moving the point of my pen down the column to keep track of the process.
If all you knew is how long my pen spent pointing at each digit, you’d still almost certainly be able to guess where the zeros were, because I’d skip over them and not say anything, so they’d stand out in your timing data.
You might also find I’d be a bit slower adding the 8s and 9s than I would be adding the 1s and 2s, so you could use that to guess at yet more of the digits in the list, and so on.
The researchers also claim that they can attack an iPhone attack by monitoring power supply fluctuations, rather then emitted radiation, using a booby-trapped charger cable:
Click on the image to see it in the original article…
They tried Android phones, too, but apparently had some trouble, because they needed lab-grade equipment to sniff out the DOUBLEs and ADDs on their Xperia x10:
Click on the image to see it in the original article…
What to do?
Don’t panic.
This attack is difficult to pull off, unless you regularly hang out in coffee shops where bringing your own lab equipment is de rigueur.
Attacker also need measurements from several thousand different digital signatures using the same key in order to have a chance of figuring it out – and that’s an awful lot of activity on Apple Pay or in the Google Play Store.
Better yet, if you have iOS 9 or later, any apps that use Apple’s built-in crypto library appear to be immune anyway.
In other words, even the richest and most determined attacker is unlikely to try this approach, given its very low chance of success, the complexity of setting the whole thing up in the first place, and the plethora of easier ways to get data out of unsuspecting users.
However, if you’re a cryptographic programmer, especially if you work on special-purpose hardware that’s supposed to be resilient even to expensive and cumbersome attacks, it’s a pertinent reminder.
Algorithmic speed is not as important as algorithmic consistency, because anything that leaves behind a pattern that depends on the current inputs could be used in what’s called a side-channel attack, or a “side door.”
As cryptographers are always keen to remind us, “Plan ahead, because attacks only ever get better.”



R Sieber
sensationalist and misleading headlines — you’re gonna become the boy who cried “wolf!”
what you’re actually reporting is that there is a very small opening for a very long and incredibly difficult attack requiring arduous work and ridiculous sophistication. Under a headline proclaiming that a back door already exists and that keys can already be stolen. That’s incredibly irresponsible.
Paul Ducklin
That’s the most hyperbolic paragraph I’ve read in ages. (You shouldn’t use the word “incredibly” in the way you have. Nor the word “ridiculous.” I do not think they mean what you think they mean.)
In any case, hypebole or not, this attack is not “ridiculously sophisticated”. That’s part of the point of the article: it can be mounted using commodity equipment. As for the veracity of the headline…well, I sort-of get your point, but this *is* a “side door attack”, and it *can* steal keys. That’s the whole point. Practicable or not, the researchers actually succeeded, and that’s interesting and important, if not actually immediately dangerous.
And maybe you missed the bit where I wrote:
“Even the richest and most determined attacker is unlikely to try this approach, given its very low chance of success, the complexity of setting the whole thing up in the first place, and the plethora of easier ways to get data out of unsuspecting users. However, if you’re a cryptographic programmer, especially if you work on special-purpose hardware that’s supposed to be resilient even to expensive and cumbersome attacks, it’s a pertinent reminder. […] As cryptographers are always keen to remind us, “Plan ahead, because attacks only ever get better.”
R Sieber
I certainly didn’t miss this bit, but it seems the headline writer did:
“Even the richest and most determined attacker is unlikely to try this approach, given its very low chance of success, the complexity of setting the whole thing up in the first place, and the plethora of easier ways to get data out of unsuspecting users. However, if you’re a cryptographic programmer, especially if you work on special-purpose hardware that’s supposed to be resilient even to expensive and cumbersome attacks, it’s a pertinent reminder. ”
That’s what I mean by ridiculously sophisticated — to put it in your own words: “absurdly difficult.”
Because the important thing is that there is no attack here. You describe a *potential* vector which could be attacked, not an existing sidedoor. The difference undermines your credibility. Especially since, way down below, you admit that current OS no longer has this vulnerability.
I use the word “incredibly” in the most literal sense: I cannot believe you are being so irresponsible as to headline this statement:
‘anything that leaves behind a pattern that depends on the current inputs could be used in what’s called a side-channel attack, or a “side door.”’
with this headline:
“Forget iPhone backdoors, here’s a *side* door that can steal your keys”.
What did you say about hyperbole?
Paul Ducklin
*I* wrote the headline, not a headline writer, and I am not going to change it. (But I did remove the word “absurdly” from the article.)
Headlines are meant to be interesting, intriguing, and inviting…as long as they are honest. And there *is* a side door, and you *can* steal keys with it, because the researchers did so.
That’s the thing. From your insistence on the word “incredible,” I assume you have formed the opinion that the researchers didn’t pull the attack off at all. I’m siding with them. I reckon they did do it, so we shall have to disagree.
[This thread is now closed.]
John Harris
My fellow techs and I figured the NSA was probably capable of this last week regarding “the iPhone.” But I like the sentence after “Don’t panic.” I want to know where that coffee shop is located.
Paul Ducklin
The coffee shop where cool lab equipment might look normal… CERN, perhaps? CCFE? Lawrence Livermore?
Anonymous
Google “electromagnetic analysis pda” and you’ll find some interesting reads from 2005.
LindaB
Perhaps the LAPD could use this technique to resoplve the recent high profile case?
Paul Ducklin
Probably not, because the phone needs to be on and actively doing the right sort of cryptographic calculations at the time you do the eavesdropping. That’s not every likely in a phone that’s been turned off for a while, and then rebooted back to the lock screen. But I like your thinking…I wonder if the FBI has tried a side-channel attack, and, if so, whether that will come out in the court case?