 In the past few years, a lot of media outlets, and even some security vendors, have hyped up the threat of so-called advanced persistent threats (APTs), frequently associating them with nation-state attackers using unheard of zero-day exploits to break into high-profile targets.
In the past few years, a lot of media outlets, and even some security vendors, have hyped up the threat of so-called advanced persistent threats (APTs), frequently associating them with nation-state attackers using unheard of zero-day exploits to break into high-profile targets.
In fact, there’s a lot of disagreement about how we should define APTs. How do you define “advanced” attacks when so many APTs leverage old exploits that have available security patches, and social engineering techniques frequently used by “common” cybercriminals? This leads to confusion among IT professionals and small businesses, many of whom don’t know what an APT is.
More sober minds tend to favor the term “targeted attacks.” Nevertheless, there are plenty of security products on the market today that offer protection against “APTs,” which poses a conundrum: how can you test these products to find out if they adequately protect against these threats without an agreed-upon definition of APTs?
SophosLabs Principal Researcher Gabor Szappanos has come up with a convincing answer in a recent paper titled Effectively Testing APT Defenses. Instead of getting bogged down in semantics, Gabor and his co-authors describe a method for testing defenses that could resolve disagreements about definitions, while answering many of the objections raised by security vendors who obviously want realistic and accurate tests.
To start, Gabor and his co-authors demonstrate how many different ways APTs are defined by various vendors and analysts, and cut through the confusion with a simple explanation – since the terms “APTs” and “targeted attacks” are often used interchangeably, it makes sense to use the more-easily-defined “targeted attack” when establishing tests.
Their definition:
A targeted attack is an infection scenario executed against a limited and pre-selected set of high-value assets or physical systems with the explicit purpose of data exfiltration or damage.
With that out of the way, the authors are able to tackle another conundrum – it’s difficult to test APT defenses because of obstacles to replicating “real world” attacks in a test environment.
There’s also the matter of attackers not relying on a single point of entry or attack technique – because they are “persistent,” attackers aren’t going to “throw in the towel” when they reach an obstacle, but will instead look for another way past defenses.
Another obstacle to testing is that effective defenses are necessarily dynamic, which might not be easy to capture in static, repeatable tests.
Gabor and colleagues explain some of the obstacles to APT defense testing and some possible solutions in the following table:
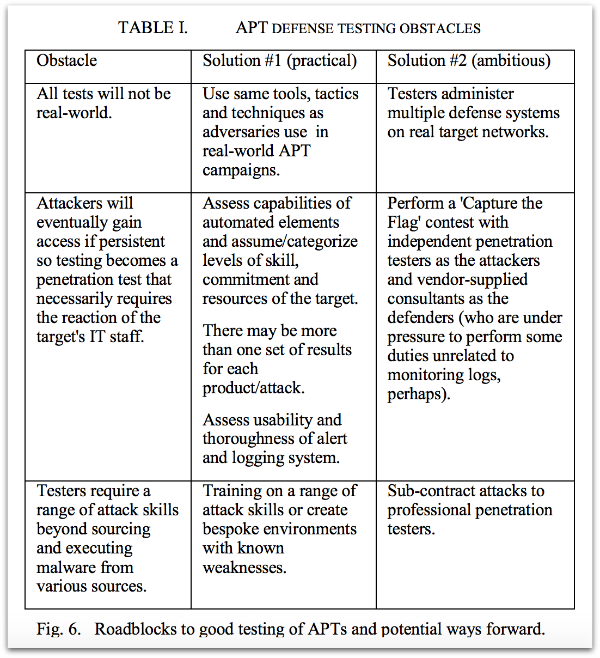
Of course, this description of the research paper and its conclusions is leaving a lot of detail out, and we don’t want to steal thunder from the real security experts.
Gabor has been researching APT malware such as PlugX, on the trail of malware authors like “Objekt,” and tracking malware campaigns like the “Rotten Tomato” campaign, for years – and this research paper is built on that foundation of experience.
The paper is full of detailed yet easy-to-comprehend definitions, and interesting descriptions of attack scenarios and defenses. Plus it gives a step-by-step deconstruction of the obstacles to APT tests, with reasonable and well-considered answers to those issues.
Finally, the paper provides a way forward that might just help independent testers and security vendors come up with an agreed-upon testing regime that will help the security industry measure security products that defend against targeted attacks, leading to better security products and better protection for customers.
Go check out Gabor’s paper now – it’s a free download and no registration required.
About SophosLabs
SophosLabs is the global network of threat centers staffed by Sophos researchers and analysts.
Keep up to date with our latest industry-leading research and technical papers, expert opinion, and security advice at Naked Security and right here on the Sophos Blog.
Sign up for our Sophos Blog newsletter by entering your email address in the field at the top right of the blog’s webpage. Follow us on your favorite social media networks, chat with us in our forums, download our informative podcasts, or sign up for our RSS feeds.