 Ask around and IT professionals will tell you that one of their top security concerns can be summed up with the acronym PEBCAK – Problem Exists Between Chair and Keyboard.
Ask around and IT professionals will tell you that one of their top security concerns can be summed up with the acronym PEBCAK – Problem Exists Between Chair and Keyboard.
It’s a tongue-in-cheek way of saying security breakdowns are caused by users.
Many people are susceptible to social engineering attacks and phishing emails, have bad habits like using weak passwords, and leave themselves open to cyberattacks by not taking steps to secure their software and devices.
Many possible solutions have been looked at – training programs and tools that use false phishing emails, minimum password lengths, millions spent on public awareness campaigns – but the user problem persists.
Now Fujitsu, the Japanese technology giant, thinks it has found an answer in social psychology.
Fujitsu claims that its technology can assign security countermeasures based on a user’s psychological profile and risk tendencies – warning them ahead of time, before an attack can be carried out successfully.
Fujitsu’s psychology experiment
Fujitsu and Fujitsu Laboratories announced recently that they have developed the “first technology” for identifying users susceptible to cyberattacks based on their personality traits and computer usage behaviors.
Fujitsu says its technology can tailor security countermeasures to individual users and organizations – for example, by sending warning messages to users who often click on URLs in suspicious email messages, or escalating the threat level of suspicious emails sent between departments with virus-prone users.
To develop the technology, Fujitsu studied a diverse sample of 2000 of its own employees, half of whom had experienced a cyberattack.
These employees filled out a social-psychology questionnaire that the company used to identify the personality traits and behaviors of people likely to suffer three types of attacks: virus infections, scams (such as phishing), and data leakage.
A smaller sample of 250 workers were analyzed by logging their behaviors when using their computers – such as their interactions with their keyboard and mouse, how they respond to false computer freezes, and their clicks on links in emails.
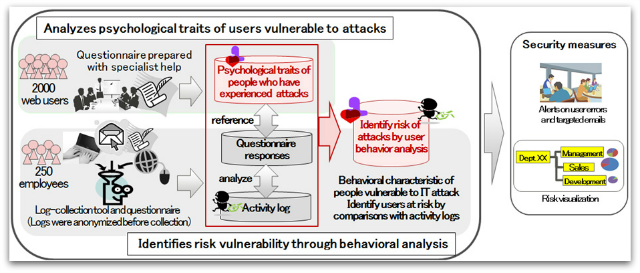
Among the company’s findings – people who prioritize benefits more than risks are at greater risk of a virus attack, while those with higher confidence in their computer abilities are a greater risk for data leakage.
Someone who prioritizes benefits over rewards, for example, would be more likely to click on links or open attachments without considering the potential for downloading a virus or visiting an infected webpage.
Could it work?
Computer-based behavioral profiling is becoming very popular – recent research has found that algorithms can be more accurate at identifying personality traits and predicting behaviors than a person’s closest friends.
Fujitsu says its behavior-based security tool can recognize what types of risks an individual is prone to, and direct countermeasures most appropriate to that person.
For example, according to IDG News Service, the tool can display individualized warnings such as “You are vulnerable to being scammed. Be careful.”
However, it’s not yet clear how effective these warning messages can be – in itself a subject of much psychological research – because people have a tendency to ignore warning messages or become immune to them.
The tool can also show a user their relative vulnerability to cyberattacks compared to other departments in their company, a form of social influence (which some research has found to be less effective than previously thought).
There’s lot of potential here, but we don’t know yet how accurate this kind of user profiling is, or how effective – “needs more study” seems to be the prescription for this brand of security.
Fujitsu – which plans to offer the technology commercially for enterprises in 2016 – says it is continuing its research.
In the meantime, watch out for PEBCAKs, and make sure you have layers of security to defend against the inevitable human failures.
Image of psychedelic background brain courtesy of Bruce Rolff and Shutterstock.com.
