No organization sets out to become a victim of cybercrime. But if there are security gaps in terms of misconfigurations, exposed assets or unaddressed vulnerabilities, it is likely that cyberattackers will find and exploit them, and it could be months or even longer before the victim finds out what’s happened. Sophos’ incident responders help businesses to identify, block and mitigate the impact of attacks. As a result, they see at first-hand how cybercrime affects victims.
Total security is a myth
The standard cybersecurity maxim is that defenders need to be right all the time, while an attacker only needs to be right once. This is a demoralising message for IT security teams and only partially true. You need layers of security that can break the attack chain in different places. This approach matters because attackers are becoming very skilled at disguising themselves to avoid arousing the suspicion of security teams and triggering detection.
They do this by, among other things, abusing legitimate IT tools to bypass security technologies, scan computers and move laterally through the network. In addition, they regularly compromise existing admin accounts so they can hide in plain sight. If they are stopped in their tracks, they will try something else.
This brings us to one of the most significant aspects of cyberattacks and one that victims often underestimate: you are not fighting code; you are fighting people.
Hands on keyboards
While the initial breach may be automated and possibly opportunistic, once the attacker has a foothold inside your network, it is often a person who operates the tools and attack and they are targeted and determined.
In one incident witnessed by incident responders, an adversary tried to compromise a victim through four different attack methods in the space of just 15 minutes. After all attempts were blocked, the attacker tried using the often-unprotected route of RDP, at which point they revealed the IP of the computer they were using and identified themselves to the security team. Game over.
The challenging thing for victims is that the frequent use of legitimate tools by attackers means IT security teams have to be extra vigilant about discovering whether or not these tools are being used for malicious purposes.
How long have attackers been in your network?
According to incident responders, most victims believe a breach happened just before the visible part of the attack, ie. ransomware, took place, when this is actually rarely the case. In fact, the attackers are likely to have been in the network for considerable time, hiding under the radar while scanning systems, installing backdoors, stealing information, and securing persistence so they can pick back up/resume? after a reboot. These are all security issues that victims will have to check for and mitigate to fully recover from an attack, adding pressure to an already stressful situation.
The part of the attack that most often alerts victims to the presence of an intruder is the launch of ransomware. This is the point at which the attacker has probably done everything they want to do in the victim’s network and is ready to break cover and make some noise. In other words, the implementation of ransomware generally marks the end of an attack not the beginning.
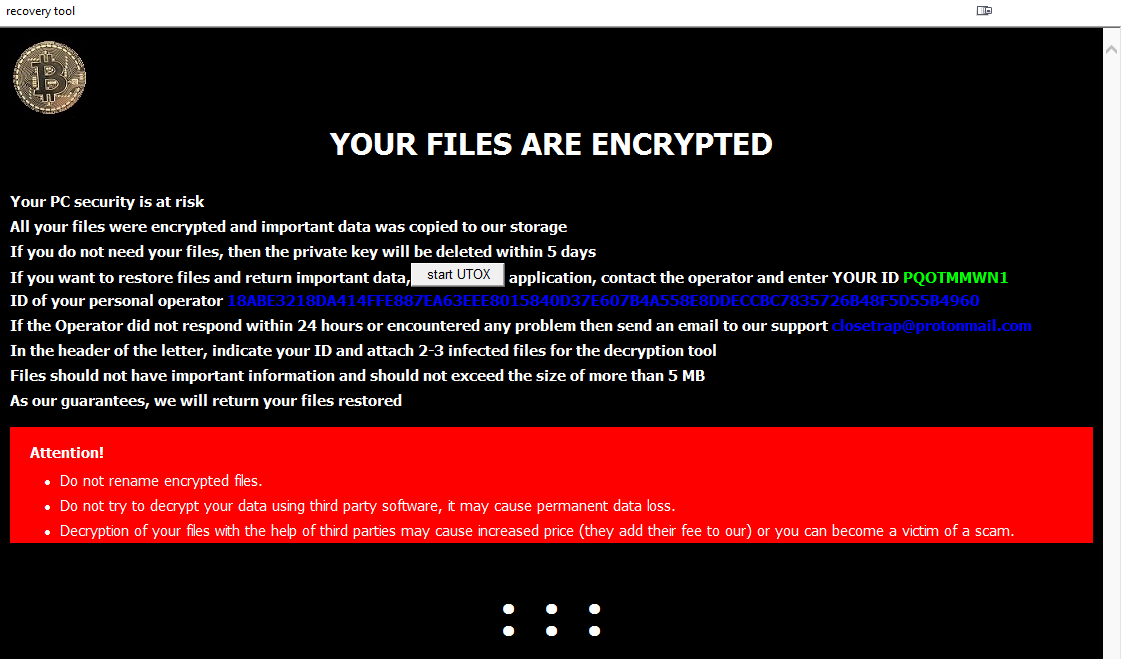
Rampant ransomware
Around 90% or so of the attacks seen by incident responders involve ransomware and the impact of the attacks are often devastating, particularly for organizations where there is real-world impact. This includes healthcare entities, where a successful attack means cancelled operations, lost X-rays, encrypted cancer scan results, and more.
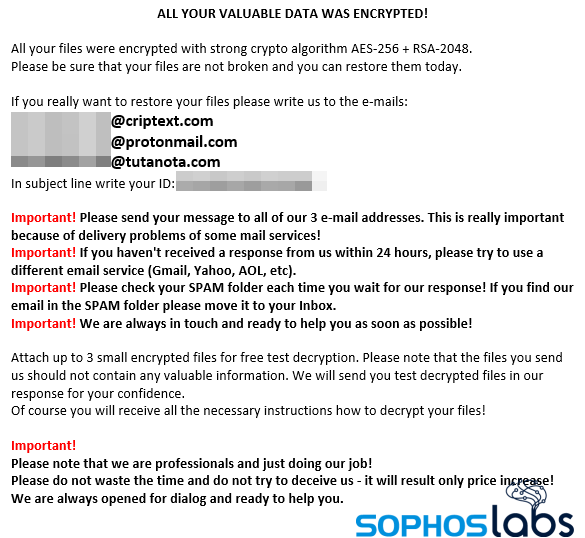
Some victims feel they have no option but to pay the ransom, for example those whose online or otherwise accessible data backups have been deleted by attackers. Other organizations refuse to pay, no matter what the circumstances. Some worry more about the reputational impact of stolen data being exposed than about paying for decryption keys. The ransomware itself ranges from the business-like and sophisticated to low grade and messy. Incident responders have learned that while all attacks are exhausting and intimidating for victims, they sometimes reveal mounting stress and anxiety on the part of the attackers too.
One example of this was an organization hit by the ransomware-as-a-service offering REvil/Sodinokibi. Overnight, the attackers encrypted 90% of the company’s servers and the business ground to a halt. The attackers had gained access to the company’s critical financial systems and took full advantage of this in their ransom demand communications.
The first ransom demand for $3 million USD arrived within a day. The accompanying note sought to justify the cost by listing the company’s various income streams, the fact that it was eligible for a loan from a named bank, the potential costs of the impact of the ransomware, and the monthly repayments if the company took out a loan from the bank to pay the ransom. The note also pointed out that the company’s tax declaration did not seem to fully match its actual revenues. None of this achieved the desired result since the business, which didn’t have anti-ransomware insurance in place, declined to pay.
Matters escalated quickly. Further emails with threats poured in and started to target individual employees with details of their personnel records. Then the whole company received an email exhorting them to persuade their senior executives to pay the ransom, which by then stood at $8 million USD. Finally, the attackers started to phone the by then worn out IT team, telling them to read their email and pay.
The victim never paid. They restored what they could and took the hit as the attackers dumped three loads of company data online. The company is still in business.
The challenge of rebuilding
Incident responders note that many victims struggle to understand how ransomware moves through the organization. There is a general assumption that it spreads outwards in all directions when in fact it is strategically deployed to a pre-selected list of machines. Further, the attackers don’t just target documents and other data, they get as close as they can to ‘bricking’ the machines without actually doing so. They leave just enough capability for the victim to be able to boot the machines and see the ransom note.
What this means for victims is that recovery doesn’t begin with restoring backups and then addressing what else the attackers accessed or stole. It often starts with the significant challenge of rebuilding all the affected machines and the difficult task of identifying where the adversary launched the attack from and whether they still remain inside the network.

Building a better security guard
As attacks become stealthier and better at abusing legitimate tools and processes, the value to victims of human-led threat hunting is clear. Threat hunting complements the advanced algorithms of next generation security software with 24/7 human expertise that can evaluate the nuances of an attack in a way software can’t.
It’s like having CCTV: cameras alone can record and may deter a crime, but they can’t actively stop it. It’s the security guard watching the CCTV live who can take action. Too many IT security teams still turn up to work one morning to discover what has been done to them, rather than to learn what could have happened, but didn’t.

ctyeurogold.wordpress.com
I don’t even understand how I stopped up right here, however I thought this post used
to be great. I do not understand who you are however certainly
you’re going to a well-known blogger in the event you are not already.
Cheers!