DDoSecret – a journalist collective known as a more transparent alternative to Wikileaks – published hundreds of thousands of potentially sensitive files from law enforcement, totaling nearly 270 gigabytes, on Juneteenth.
That date – 19 June – is a holiday that celebrates the emancipation of those who were enslaved in the US. There’s currently a push to make the date into a national holiday – a movement bolstered by the nationwide Black Lives Matter (BLM) protests.
DDoSecrets, which refers to itself as a “transparency collective,” has dubbed the release BlueLeaks.
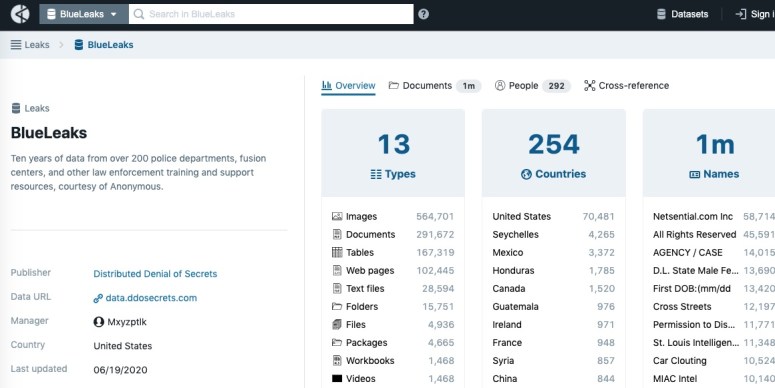
On Friday, DDoSecrets said on Twitter that the BlueLeaks archive indexes “ten years of data from over 200 police departments, fusion centers and other law enforcement training and support resources”, including “police and FBI reports, bulletins, guides and more.”
Fusion Centers are state-owned and operated entities that gather and disseminate law enforcement and public safety information between state, local, tribal and territorial, federal and private sector partners.
DDoSecrets published the data in a publicly accessible, searchable portal that says it contains more than 1 million files, such as scanned documents, videos, emails, audio files, and more.
The collective said that the source of the data was Anonymous: the label that some hacktivists have used when taking actions against targets such as the hospitals involved in the Justina Pelletier case, revenge-porn site publisher Hunter Moore, and, more recently, attacks on the Atlanta and Minneapolis police departments following police killings of Black men.
Information security reporter Brian Krebs says that he got his hands on an internal analysis dated 20 June, from the National Fusion Center Association (NFCA), that confirmed the validity of the BlueLeaks data.
The NFCA said that the data appears to have come out of a security breach at Netsential, a web-hosting company based in Houston. Netsential provides web hosting for many US law enforcement agencies and fusion centers.
According to the alert, the dates on the files actually go back further than 10 years. They span nearly 24 years, from August 1996 through 19 June, 2020. The files include names, email addresses, phone numbers, PDF documents, images, and a large number of text, video, CSV and ZIP files.
The NFCA alert said that some of the files also contain highly sensitive information, including “ACH routing numbers, international bank account numbers (IBANs), and other financial data, as well as personally identifiable information (PII) and images of suspects listed in Requests for Information (RFIs) and other law enforcement and government agency reports.”
Krebs talked to Stewart Baker, an attorney and former assistant secretary of policy at the US Department of Homeland Security (DHS), who said that the BlueLeaks data isn’t likely to give anybody much insight into police misconduct. Rather, it’s more likely to expose sensitive law enforcement investigations and even endanger lives, he told Krebs:
With this volume of material, there are bound to be compromises of sensitive operations and maybe even human sources or undercover police, so I fear it will put lives at risk.
Every organized crime operation in the country will likely have searched for their own names before law enforcement knows what’s in the files, so the damage could be done quickly. I’d also be surprised if the files produce much scandal or evidence of police misconduct. That’s not the kind of work the fusion centers do.
For its part, DDoSecrets says that it’s politics-free:
We aim to avoid any political, corporate or personal leanings, and to act as a simple beacon of available information. As a collective, we do not support any cause, idea or message beyond ensuring that information is available to those who need it most – the people.
The collective has two criteria for publishing data: The data has to be of public interest, and it’s got to be capable of being verified. The group says it ensures anonymity for those who provide information that hasn’t previously been disclosed. DDoSecrets often passes the data it receives on to journalists or “other figures best positioned to interrogate it.”
A quick look at Twitter posts shows that since Friday, figures have most certainly been interrogating the BlueLeaks data:
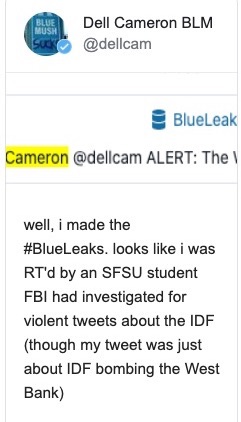


Gabriel
With so many hacks and leaks, it is getting to where individuals protecting their PII is pointless. I have 2FA on every account possible and try to avoid sites that do not support it, I have unique passwords for every site, but everyone else is leaking the data anyway. So far, I have had my I have had my name, address, phone number, social security number (which can’t be changed), email addresses, account logins, passwords, and more leaked by everyone else while I protect it. Makes me wonder if someone could come up with something like salted and hashed passwords for SSN. Your SSN gets comprimised, we can change it because that is not your true SSN. Your SSN is just a virtual link to your true SSN which is protected and never publicly exposed provided that the government actually protects it.
Bryan
+1 I like the idea a lot Gabriel.
Inner Cynic Bryan rains on the parade:
If that project were undertaken then whatever repository guarded† the true numbers would become a favorite of sorts among targets.
I wonder how long it could withstand external breach attempts?
Probably better/longer than against internal bribe attempts.
† subsequent of course to the massive expense, overhead, and PITA to convert and correlate literal tons of documentation on 330M people
Craig
Make it so that the “real” SSN is never accepted for anything official. Only temporary SSN’s, which of course would be mathematically linked to the real Id values.
Bryan
Right. That was Gabriel’s idea.
However that approach’s Achilles Heel would be that SOMEwhere, there’d need to be a storage “vault” of sorts with the true numbers.
It would convert “1234” to “48fhH3q459ala34” via some mechanism, likely a simple lookup table.
That storage facility that would be the high-value target.