Lots of people still think of phishing as a type of scam that arrives by email.
That’s because most phishing attacks do, indeed, arrive in your inbox – sadly, spamming out emails is cheap and easy for crooks, and it delivers results simply because of the volume they can achieve.
But phishing isn’t only about email – it’s a scamming technique that applies to every form of electronic messaging, including social media, instant messaging…
…and even, or perhaps especially, good old SMS texts.
One of the delightful simplicities of SMS is that it was designed back when mobile phones first came out, and thus when network bandwidth was limited.
So SMSes are short, simple, and text-only, and this stripped-down nature actually makes them ideal for crooks.
Messages sent via SMS unexceptionably use a brief and direct style that means crooks don’t need to master the grammatical niceties of English to create believable texts.
The brevity of SMSes also means that shortened or unusual-looking URLs are commonplace, so we’re more inclined to accept them than we would be if they showed up in an email.
Even though services such as Skype, WhatsApp, Instagram and Snapchat have become the first-choice messaging apps of today’s youngsters, SMS has never gone away, because every phone, on every network, in every country, still supports it.
In the UK, for example, most pay-as-you-go mobile plans throw in ‘unlimited SMSes’ as an incentive to attract users to their plans – you might not need SMS any more, but it’s certainly handy to have an all-you-can-eat SMS buffet thrown in with every basic deal.
And which sort of company is most likely to contact you via SMS?
Why, your mobile phone provider, of course!
They know the message will get through, because they manage your account, and they know your phone handset will definitely be able to display it.
Like this:
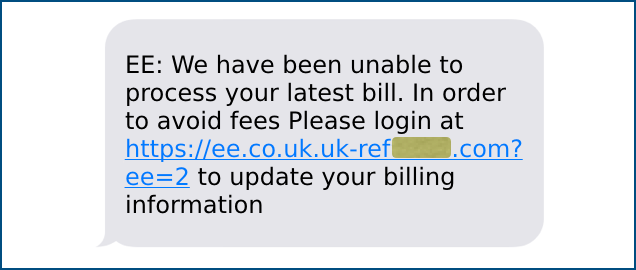
OK, so you ought to spot this as a scam, because the crooks have messed up the English slightly (we’re not going to give them a free grammar lesson here, but a few tweaks would improve the looks greatly), and because they have, of necessity, created a bogus domain that’s visibly different from the genuine one.
The crooks can’t use the domain name ee DOT co DOT uk, of course, because that’s the real deal and would take you to mobile provider EE’s genuine website.
But the crooks can put ee DOT co DOT uk at the left-hand end of an innocent-looking domain name of their own for a touch of realism.
And in this case, they’ve registered the name uk-ref[redacted] DOT com, which doesn’t look entirely out of place, given that EE is a UK company, and this scam is aimed at users in the UK.
For a German provider, the crooks could just put de- at the start of their domain name, or use ca- for Canada, and so on.
In this case, the crooks haven’t done any targeting of their attack – the member of our team who received this phish wasn’t actually on EE’s network, so they were in no doubt that it was fraudulent.
But EE is one of the UK’s biggest mobile providers, so a significant minority of recipients will see a message that does match their network.
In theory, the first few digits of each number would have given the crooks a good guess at each network provider, so targeting this SMS scam to each recipient’s home network would have been fairly easy. That would have avoided ‘false positives’ where the recipients realised at once that they were being scammed. On the other hand, number-to-network directories aren’t always 100% correct, and some users have multiple SIMs, so the crooks may have decided instead to avoid ‘false negatives’, where they might miss out on potential victims by needlessly leaving them off the list. When the cost of sending 100,000 messages is not significantly higher than sending 10,000 or even 1000, there is little reason for the crooks to hold back.
As you can see, the crooks seem to be paying heed to the old adage that you catch more flies with honey than with vinegar.
Although this scam is trying to trick you into logging on in order to avoid something bad, the crooks aren’t squeezing you too hard.
The crooks are fraudlently claiming that they’re trying to bill you, which is something that you expect to happen every month if you’re on a contract, but they’re not threatening to cut you off if you DON’T PAY RIGHT NOW, and they haven’t littered their message with SPELING MISTEAKS, outrageous DEMANDS and too many EXCLAMATION POINTS!!!
The crooks even said “please”, and are offering you a reasonable-sounding chance to correct the mistake before you rack up late payment fees.
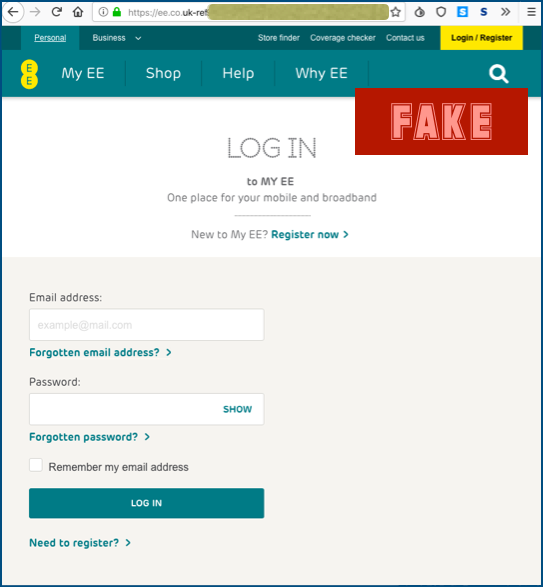
Of course, if you click through you will need to log on, as you might expect if you want to check your user profile and your billing data, and the crooks present an almost-perfect ripoff of the real thing:
For reference, EE’s real login page looks like this [2019-10-16T10:00Z]:
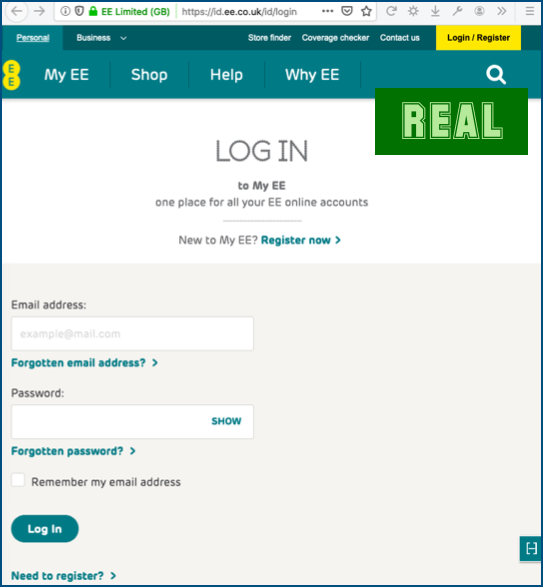
The site shown above was hosted via a cloud-based web service that handily provides its customers with a basic web server that’s already configured with an HTTPS certificate, so your browser shows you a padlock, thus avoiding an alert of an unencrypted site.
Happily, this password-stealing site was quickly and widely blocked by cybersecurity companies and browsers, and has now been taken down, but anyone who inadvertently put in their password would immediately have passed it to the crooks.
What to do?
- Change your password as soon as you can. If you think you just gave away your password by mistake, go and change it on the real site right away. Don’t wait to see what happens – get there before the crooks do. Don’t risk getting locked out of your own account, trying to convince your service provider that you aren’t the crook!
- Look for obvious mistakes in messages. The crooks have upped their game and make fewer mistakes than they used to, but they still need to use bogus domain names, and they often make some mistakes. If any evidence of phishiness is there, make sure you act on it.
- Don’t login via links sent from outside. Bookmark each provider’s logon page for yourself, or use a password manager that ties passwords to specific URLs. That way you won’t get suckered into visiting a fake login page that a crook pre-selected for you.
- Report phishing scams – please do your bit to help everyone else. You can report potential cyberthreats – files, emails and URLs – to Sophos via our Submit a Sample page. In the UK, report phishes to law enforcement via Action Fraud. In the USA, use the FBI’s Internet Crime Complaint Center.
By the way, given that it’s Cybersecurity Awareness month, we’ve been publishing a light-hearted poem each day on @NakedSecurity – and below you’ll find some gentle advice about not letting your guard down when the crooks are out to get you.
Whatever you do, don’t be this guy…
I can spot a phish for miles
— Naked Security (@NakedSecurity) October 10, 2019
You’ll never catch me out.
I know when you’re deceiving me -
There’s never any doubt.
But tell me that I’ve won a prize,
A $50 thrill,
And suddenly my guard goes down,
I’ll click, I really will. #NCSAM #BeCyberSmart pic.twitter.com/QXKaUzxHqI

Andrew
Um… You sure it wasn’t a state entity? The text itself could’ve hacked the phone already, and the whole phishing message could have been misdirection.
I mean… It’s what I would’ve done.
Paul Ducklin
Yes. I’m sure. Reliably exploitable remote code execution (RCE) bugs in the major mobile phone apps that handle SMSes are extremely rare. IMO, no one would risk burning one in a broad-brush attack of this sort.
K
“Messages sent via SMS unexceptionably use a brief and direct style that makes it much easier to get the spelling and grammar right.” – hmm, not sure that logically follows..
Paul Ducklin
I see your point – I think what I meant is that the style of SMSes makes it easier to come up with text that doesn’t look obviously wrong. (Being “not obviously wrong” is not the same as actually being grammatically correct :-)
I think I’ll edit that sentence. Thanks for the comment.
zeke
Dear Paul
Hello.
Paul, to provide feedback on Sophos Home for Mac is a bit of nightmare. That is the prob with big organisations. I have been very impressed with Sophos (as a curious dilletante). Magnificent programme, smooth, stable, lots going for it. One little prob, however : sophos home for mac impacts web speed in a noticeable manner. Looking for all those urls in that vast list takes time. Is there not a way of simplifying this. I mean: I want to use a mac that behaves like a mac )i.e. it is FAST and efficient) I do realise that there are some drawbacks to performance if one seeks security…but, after a while, with delays in lookups, you get fed up….sad but true :/ When is sophos integrating that marvelous Intercept X tech on sophos home, a miniature version, far more efficient….lol. Well, I guess you can see what i mean. In my op, of all the AVs, sophos is the best by far…but it needs to improve on web performance and on loading of Application Pane (delay of a few secs…its just not mac, these delays…)
Best wishes
zee
Paul Ducklin
Thanks for the comment.
As for your suggestions – we’ll pass them on to the Sophos Home team… if you would like us to pass on your email address too, which we won’t do without your say-so, please let us know by emailing tips@sophos.com.
Jezer
Hi Paul, the Mobile operators in the UK and USA would like the people to forward messages into the shortcode 7726. Phishing by SMS comes in on shortcodes and normal looking mobile numbers so the quicker its reported the quicker we see the first of a new wave of phishing by SMS and the quicker its closed down.
It is important to state criminals are using Phishing by SMS in tandem with other contact methods including missed calls and emails to build that all important credibility to trigger the unthinking response.
Paul Ducklin
Thanks for the comment. You’re right: 7726 spells out SPAM and, in the UK at least, the regulator (Ofcom) promptes its use for reporting unsolicited messages:
https://www.ofcom.org.uk/phones-telecoms-and-internet/advice-for-consumers/problems/tackling-nuisance-calls-and-messages/spam-texts
In the case of outright scams (where the intention is clearly to defraud you or get hold of private data illegally, not merely to pester you in violation of the rules), I’d still recommend reporting to Action Fraud or to IC3 (shorthand for the FBI’s Internet Crime Complaint Center), because you’re dealing with a more devious and dangerous sort of criminality…