This morning I received a Skype message from a friend that I’d not heard from in quite a while. They didn’t have much to say though, they just sent me a link, out of the blue.
Being a career geek I’m no stranger to no-frills, taciturn, often blunt, communication with my peers… but this was from somebody friendly, somebody who worked in marketing for goodness sake.
There was no way this was legit.
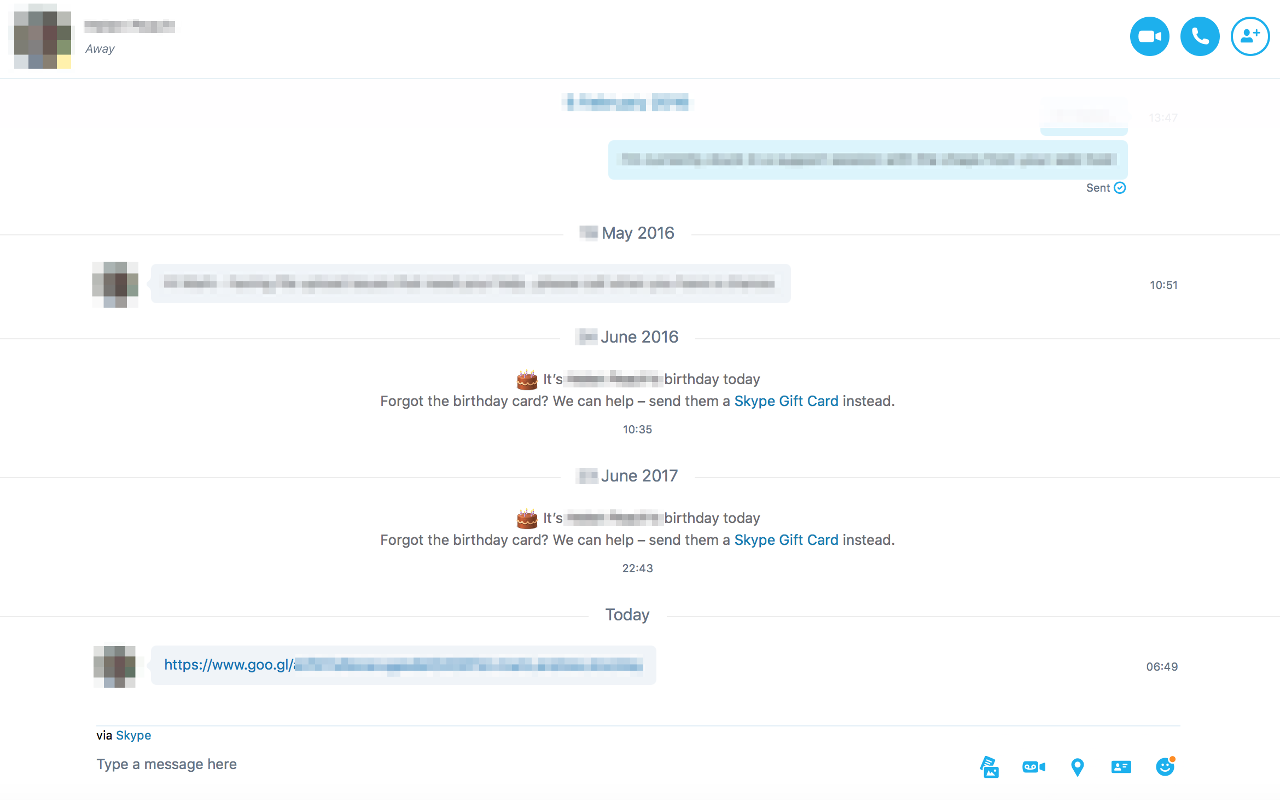
If you look closely you’ll see that the scammer’s have used Google’s soon-to-be-discontinued URL shortening service, goo.gl.
URL shorteners work by sending your browser through at least one HTTP redirect. They’re an obvious choice for somebody wanting to hide a phishy, scammy or otherwise iffy link because they’re a form of obfuscation that users have been trained to understand and trust.
In this case, the fact that the link comes from somebody you know adds an extra veneer of legitimacy.
Of course Google doesn’t stand for iffy links, so spammy goo.gl URLs are almost as easy to report as they are to create.
Crooks can get around that by using the shortener to redirect to another HTTP redirect, perhaps on a legitimate but compromised domain, before bouncing victims to a not-at-all-trustworthy-looking domain that’s hosting the scam.
With a little help from curl -I, I followed the chain of URL redirects to see where I’d end up.
There were two redirections in the chain before the final you-wouldn’t-click-it-if-you-saw-it Russian URL hosting an English language scam. The scam was the usual breathless guff and faux endorsements – in this case lies about the folks on Shark Tank – trying very, very hard to convince me that a turmeric diet pill can overcome my daily efforts to eat all the biscuits.
Must be some pill.
Much more interesting than the shortener at the start, or the scam at the end, was the URL in the middle of the redirect chain.
It turns out that its URL shortening service isn’t the only way that Google is assisting this scammer unwittingly.
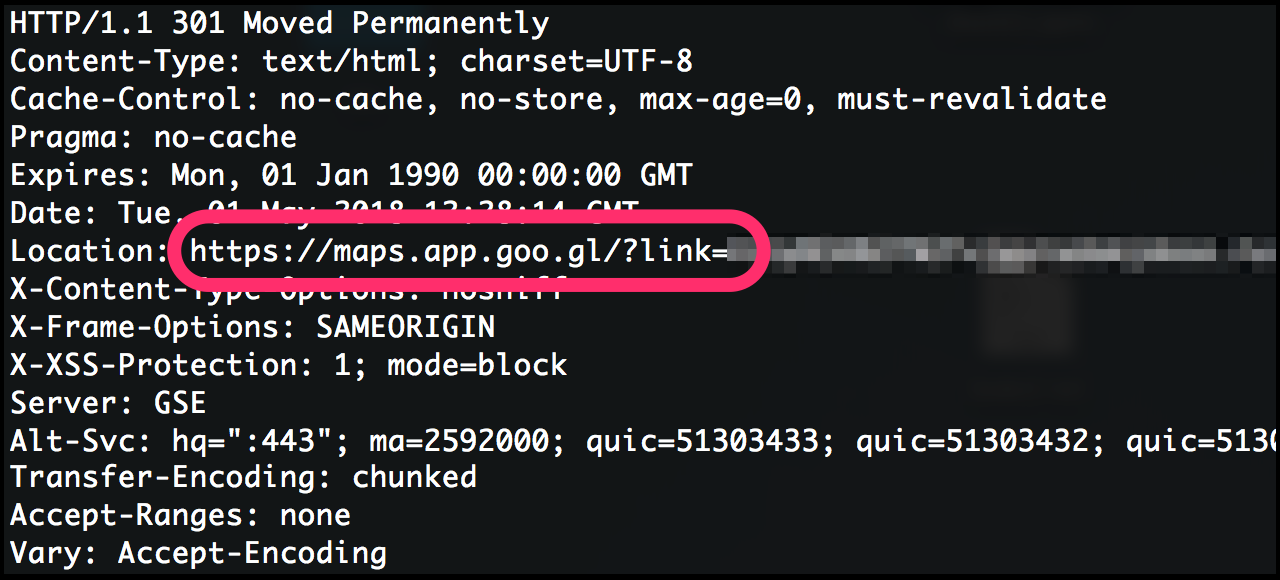
Between the legitimate Google URL shortener you’d probably trust, and the Russian URL you probably wouldn’t, the redirection chain bounces you through another Google URL belonging to Google Maps.
The crooks have turned a service designed for shortening and sharing Google Maps URLs into an impromptu redirection service for sharing whatever the heck they like, thanks to an open redirection vulnerability in the maps.app.goo.gl service.
Open redirect vulnerabilities allow attackers to abuse code that’s intended to perform an HTTP redirect to a specific something into code that redirects to anything.
For example, here’s a Google Maps URL that redirects to example.org:
https://maps.app.goo.gl/?link=https%3A%2F%2Fexample.org
Because this isn’t an official Google redirection service there’s no easy-to-use interface where the URLs can be reported.
The scammers also don’t have to risk unmasking themselves in the Google surveillance apparatus when they set up their URLs because they don’t have to use a Google-owned interface or API to do it, they can just concoct them at will.
Open redirects aren’t as dangerous as SQL injection, XSS or CSRF vulnerabilities but they are common, easily avoided and, undoubtedly, useful to crooks.
And not just for obscuring scam URLs.
Just last week I wrote about how open redirects on a multitude of US government websites are being abused to stuff Google Search results pages with links to porn sites.
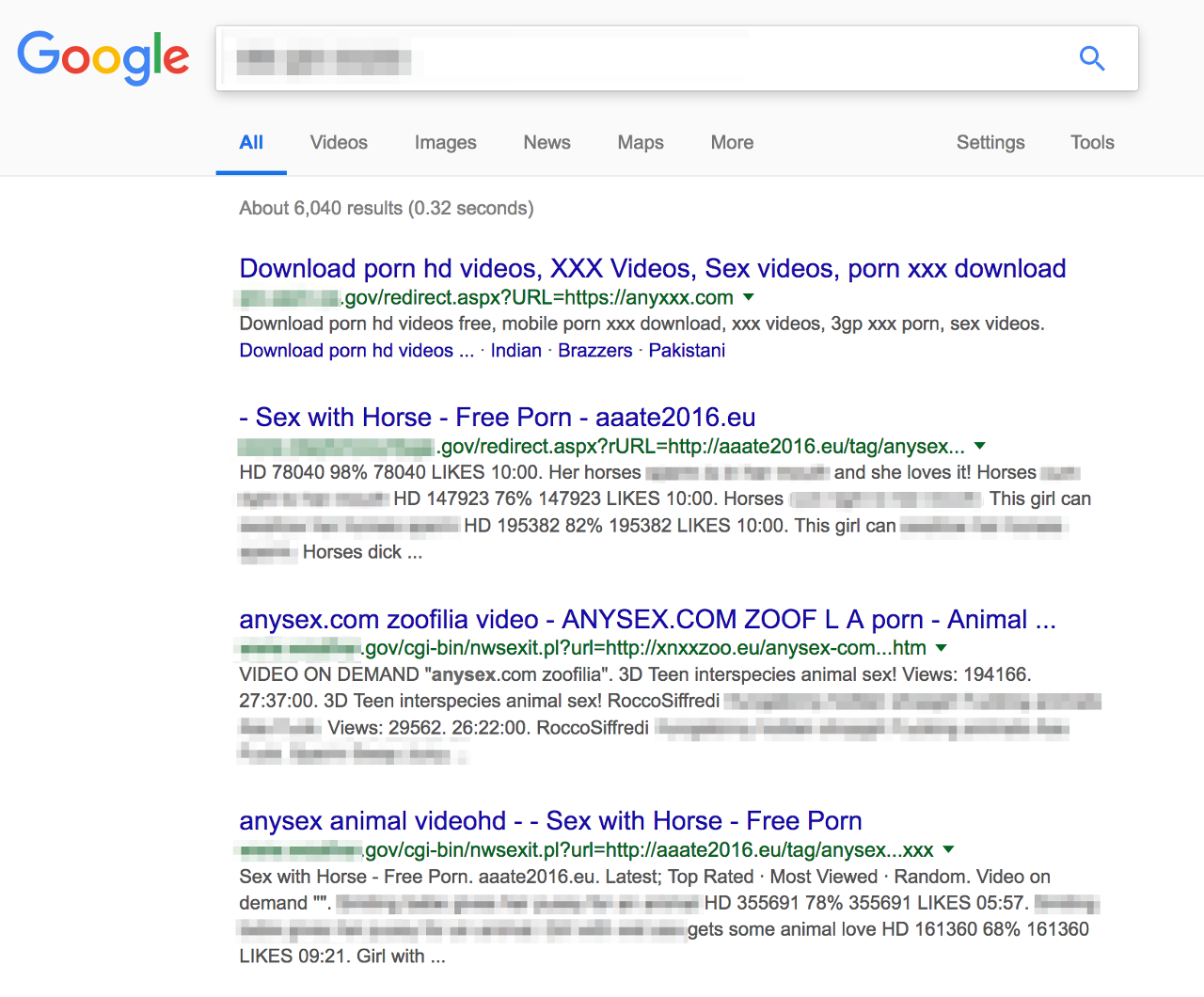
The lesson for Google is the same as it was for those government websites, and anyone else with code that allows HTTP redirects: Any and all user input should be treated as hostile until it has been checked and sanitised.
To avoid being abused, code that performs redirections should only send users to URLs that match a specific pattern or list of links thought to be OK.
In the case of Google maps that should be simple – if the URL in the link parameter isn’t a Google Map, there’s no reason to allow the redirection.
Google appears to have known about this flaw since September 2017.
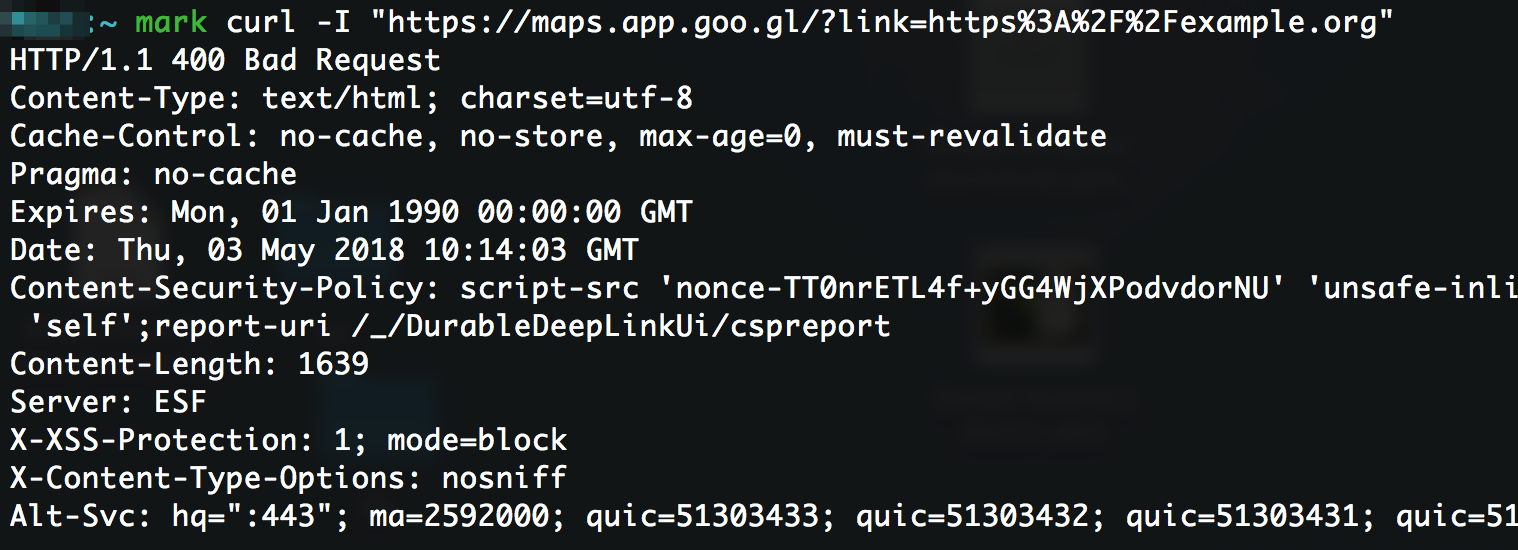
Update 2017-05-03
The issue appears to have been fixed! Attempts to redirect to domains other than Google Map’s own return a 400 Bad Request error.

Bryan
Holy smokes, if all the clever scammers were merely interested in being clever while earning an honest buck–by now we collectively would have cured cancer, colonized Mars, and convinced everyone in the middle east to hang out and sing songs together.
Steve
“Google appears to have known about this flaw since September 2017.”
Hmmm, that’s well over 90 days. I wonder why they didn’t publish that, like they do with other companies’ unpatched booboos?
Hypocrites.
Moe Salem Korayem (@Korayem)
Seems to me that it’s fixed. The link no longer works…
Mark Stockley
After I saw your comment I did a few quick tests. I get a 400 Error (Bad Request) for anything that doesn’t start maps.google.com. Result!
Mohnesh Kohli
Do you think it is still working in 2020 I just noticed that redirection is still working
[LINK REDACTED (maps.google URL plus parameters listing a new URL to visit)]
Paul Ducklin
Interesting.
Your link did work, but I couldn’t get it to redirect automatically. It gave an HTTP 200 OK response, plus a minimalistic web page along the lines of:
Redirect Notice
The page you were on is trying to send you to [new link REDACTED].
If you do not want to visit that page, you can [return to the previous page].
So instead of an instant redirection from a web page with a Google domain name, you get a Google web page (although it doesn’t have any branding on it) that visibly presents the new web page as a link in its own right. Which is not as bad…especially on a mobile phone, where the redirect parameters on the right hand end of the Google domain name might otherwise not be obvious – you hit an interstitial page where the new link you are supposed to visit is clearly showm.