What would you like with your latte? Cocoa? Cinnamon? Sprinkle of cryptocurrency mining piggybacking off your free Wi-Fi?
Recent visitors to a Buenos Aires Starbucks didn’t actually have a choice: instead, a 10-second delay was foisted on them when they connected to the coffee shop’s “free” Wi-Fi, as their laptops’ power secretly went to mine cryptocoins (of which the Starbucks customers received nary one slim dime, of course).
The mining was noticed by Stensul CEO Noah Dinkin, who took to Twitter on 2 December to ask Starbucks if it was aware of what was going on. He included a screenshot of the code.
Dinkin said in his tweet that the code was mining bitcoins, but it was actually CoinHive code, which offers a JavaScript miner for generating a cryptocurrency called Monero that’s an alternative to Bitcoin.
Hi @Starbucks @StarbucksAr did you know that your in-store wifi provider in Buenos Aires forces a 10 second delay when you first connect to the wifi so it can mine bitcoin using a customer’s laptop? Feels a little off-brand.. cc @GMFlickinger pic.twitter.com/VkVVdSfUtT
— Noah Dinkin (@imnoah) December 2, 2017
Unauthorized cryptocurrency mining has been around for years, typically showing up in malware. And this isn’t the first time we’ve seen uninvited cryptominers that specifically generate Monero, which is similar to Bitcoin but designed for even greater privacy. That privacy has reputedly made it popular on the dark web, and it’s why the WannaCry authors preferred it to their bitcoins.
Another recent case: one or more malware creators made around $63,000 in five months by invading unpatched IIS 6.0 servers to install their miners. To install the miner, they first hijacked the servers by exploiting the CVE-2017-7269 vulnerability: a good example of the importance of keeping up with patches.
It’s one way to make money. In fact, the torrent site The Pirate Bay, in true pirate fashion, recently planted CoinHive JavaScript code on visitors’ browsers, mining search pages to generate Monero without asking for permission or informing them.
When visitors smelled a cryptomining rat, an admin ‘fessed up. The rationale: hey, it’s this or ads, we gotta make rent money somehow!
We really want to get rid of all the ads. But we also need enough money to keep the site running. Do you want ads or do you want to give away a few of your CPU cycles every time you visit the site?
At any rate, Starbucks confirmed the mining on Monday, saying that it took the issue up with its internet provider to make sure its customers’ processing power isn’t siphoned off any longer:
As soon as we were alerted of the situation in this specific store last week, we took swift action to ensure our internet provider resolved the issue and made the changes needed in order to ensure our customers could use Wi-Fi in our store safely.
— Starbucks Coffee (@Starbucks) December 11, 2017
Judging by the “it’s not our Wi-Fi” statement a Starbucks spokeperson gave Motherboard, it sounds like Starbucks wasn’t knowingly on board with the CPU sucking:
Last week, we were alerted to the issue and we reached out to our internet service provider – the Wi-Fi is not run by Starbucks, it’s not something we own or control. We want to ensure that our customers are able to search the internet over Wi-Fi securely, so we will always work closely with our service provider when something like this comes up.
What to do?
- Watch your CPU. Check Activity Monitor on a Mac or Task Manager on Windows. If your laptop has fans, you might hear them revving up to deal with the extra heat generated by a heavily-loaded CPU chip.
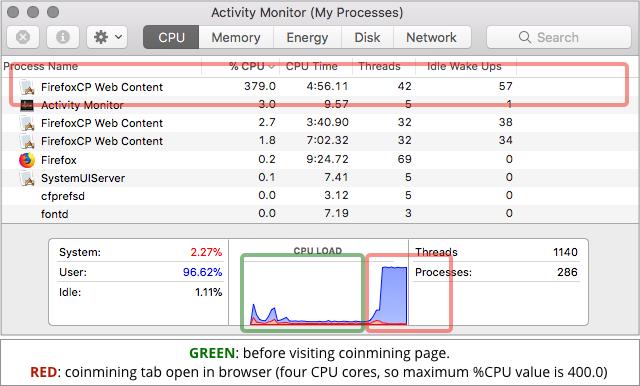
- Consider a plugin to control JavaScript. Security-conscious Naked Security commenters regularly mention NoScript, a popular free tool that lets you keep control over intrusive JavaScript, Flash, and Java in your browser.
- Find out if your anti-virus detects coinmining tools. For example, Sophos web filtering blocks coinmining sites to prevent the coinmining JavaScript from loading in the first place.
- Patch promptly. Crooks who can break into your servers could add cryptomining code to leech ‘free money’ from all your website visitors, leaving you to bear the brunt of any complaints.

RHartes
Great post Lisa, thanks for investigating.
cpagetheauthor
“PUAs aren’t malware – they can be blocked or allowed as you choose.”
Okay… so HOW do we block PUAs? Sophos isn’t telling.
Paul Ducklin
Actually, that part of the article wasn’t quite right. I’ve amended it so that bit now reads, “…Sophos web filtering blocks coinmining sites to prevent the coinmining JavaScript from loading in the first place.” Hope that’s clearer. Web filtering is part of our firewall products, as well as built into our Windows and Mac endpoint products, where we refer to the relevant component by the moniker “web protection” (if you want to know what to look for in the GUI :-)