It can get a bit overwhelming for the average person to understand all the security-related best practices they might hear about online or at work. This one is certainly worth harping on about though: credential reuse.
Using that same easy-to-type password on every website and service you use practically rolls out the red carpet for an attacker into your online life.
So if there’s one thing we suggest to everyone that will go a long way to improve their overall security, it’s using a password manager.
We’ve covered password managers in the past, and generally, our focus has been on some variant that stores your password data in the cloud, which means all that crucial data is on someone else’s computer.
Understandably, many Naked Security readers have balked at this entire idea – Why should my online security be at the mercy of a third party that may, or may not, secure my data as well as I’d like?
It’s a reasonable question – and there is an answer: KeePass.
The nitty gritty on KeePass
KeePass is an open-source password manager that does all the things you’d expect a password manager to do at the very least – it stores all websites and service credentials in a highly-encrypted vault that can only be unlocked with one Master Password, which becomes the only password you need to remember.
But a key difference between KeePass and cloud-based password managers is that KeePass is software you run locally – not an online service – and your KeePass vault is something you store in a location of your choosing.
That can be on a hard drive, a portable USB key, or even a cloud service you subscribe to. It’s up to you where your password vault goes and who has access to it.
Keeping the password vault off the internet actually makes it highly portable. A version of KeePass can be downloaded and run directly without needing to formally install it anywhere (for example, from a USB key).
A great example of this would be a work-owned computer where you don’t have admin privileges to install any software on the core system. If you have a KeePass instance and your password vault on some kind of portable storage, you can take your passwords with you anywhere, regardless of whether you have internet access or not.
In an interesting twist, many KeePass users actually advocate storing a master copy of the password vault online somewhere as a backup and to make syncing and updating the vault across devices easier.
The reason this doesn’t raise any hackles for the Never-Cloud crowd is that they don’t have to play along. The KeePass vault file is itself encrypted, so if you do keep a backup in the cloud and your online storage is breached, the KeePass file is useless without the master password. (To be fair, this is also the argument many cloud-based password managers make about how they store user password vaults.)
The beauty of open-source software like KeePass is in the numerous community-contributed extensions and plugins. For instance, there are a number of plugins that allow KeePass to integrate with your browser – auto-filling login forms or capturing credentials as they’re typed.
Other plugins bring interesting functionality to the table – one of my favorites cross-checks your saved credentials with those on Troy Hunt’s haveibeenpwned.com to let you know, well, if you’ve been pwned (if your credentials have been a part of a major known data breach). But that’s just scratching the surface here; truly, it’s plugins all the way down:
KeePass’s portable vault can also be used by other applications, extending your access to passwords beyond the desktop.
For example Sophos Mobile Security and Sophos Secure Workspace can both act as KeePass apps for smartphones. Both allow you to use, edit, import and export KeePass files, and Sophos Secure Workspace can even work with multiple local or cloud-based vaults.
With great power comes great responsibility – and, perhaps unsurprisingly given its flexibility, KeePass is quite complex by design. It has incredible capabilities, official and user-contributed, that give it a great deal of extensibility.
Just about every possible thing that someone might want in a password manager is in there, somewhere. For an easy example, this is what you see when entering a credential set:
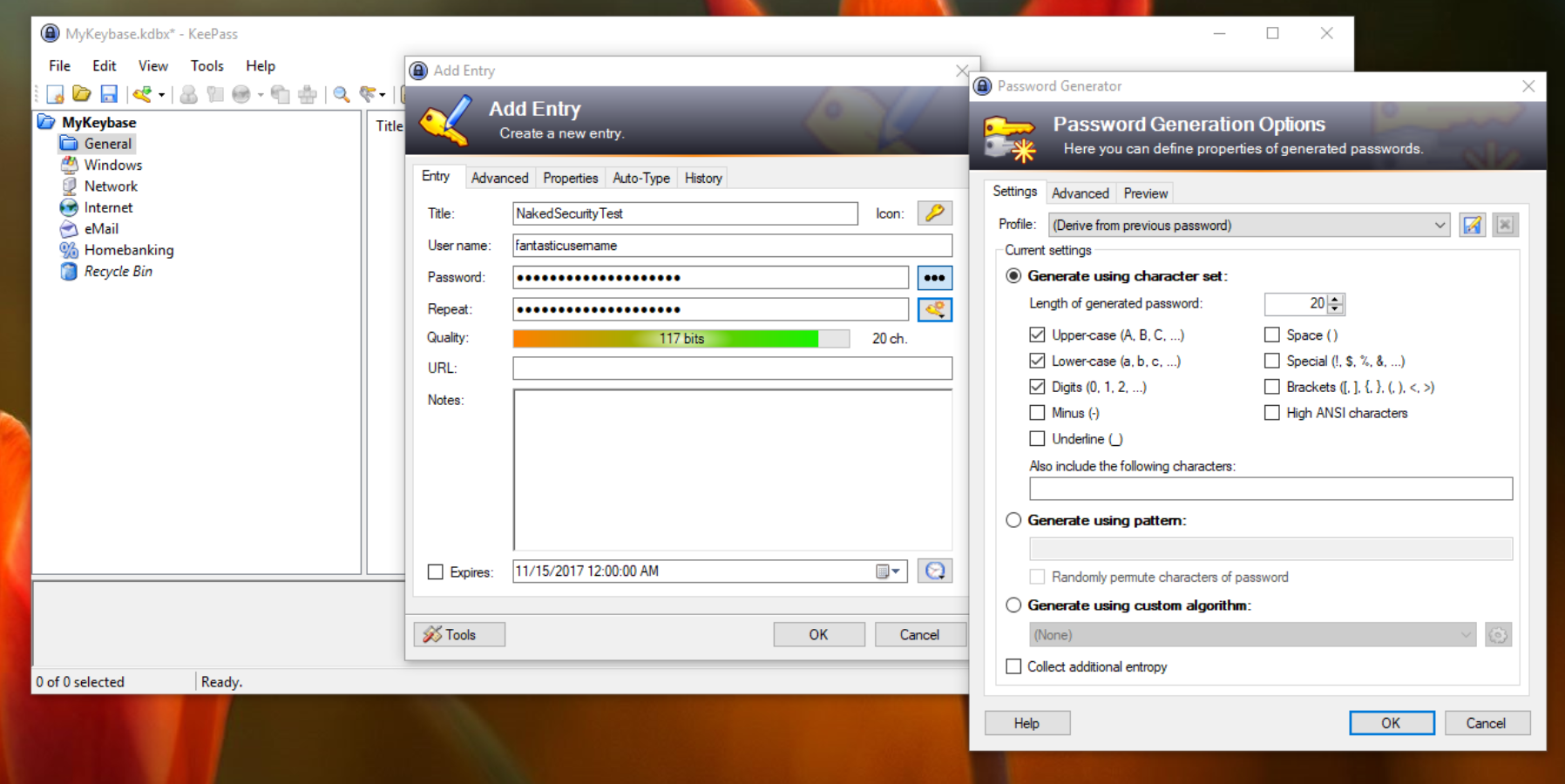
One wonders what the average person thinks “collect additional entropy” means. To be honest I’m only vaguely familiar with it, though this support forum post cleared it up:
Basically every password generator has such an option, and some people would complain if KeePass wouldn’t have one. I don’t see much value in it though…
Ah, okay.
Speaking of support forums, if you’re the type to tinker first and read documentation later there are plenty of rabbit holes to go down. And yes, there are FAQs, help docs and support forums, but beyond the basics, a well-crafted online search will help to figure this all out.
I suspect this may be a non-issue for most people reading this, but the kind of horsepower KeePass provides might not be appropriate for anyone who gets freaked out by complexity, or just needs a bit more hand-holding with technology in general – especially if they’re already struggling with the concept of password managers to begin with.
But for those of us who want the most amount of control over our passwords and how they’re stored, and are comfortable with the slightly higher barrier to entry than a consumer-grade cloud-centric password manager, KeePass makes a lot of sense.
We know from past articles that many of you are KeePass fans. If you have any favorite features, extensions or plugins, please share them with us in the comments below.

Kwazii
I rather use Sophos products like Mobile Workspace and Mobile Security, both have full built in Secure Password Manager which is compliant with KeePass file format :)
FLEO
I subscribe to the KISS principle. I’ve been using a password manager for almost 20 years now, have never used a password generator and the passwords I create are all total gibberish, only limited by applications’ and web sites’ password parameters (ie; length, special characters, etc.). I don’t need nor want any plugins or anything else for that matter that could possibly compromise my password manger.
mickyhol
I use the android app for keepass as well as the pc version. With the vault stored on my favourite cloud provider I can access, create and update my passwords anywhere. Handy and safe.
io
Glad to see Sophos giving KeePass exposure. I’ve been using the client for 5 years now – it’s a simple or complex as you need it to be. I love the Auto-Type and History features.
mrstick2000
I currently use the non-subscription, non-cloud version of 1password, which I have used for 4 or 5 years now. Usability and integration-wise, how do the two compare?
BM
Putting your trust in KeePass and the organization that developed the open source code is one thing. However, trusting plugins and each of the developers of each of those one uses, opens up magnitudes more vectors of attack.
Brian T. Nakamoto
Yes, who vets the third-party KeePass clients?
Axel
Couldn’t you say the same for closed source password manager providers along with all their developers?
Arno Pijnappels
I like the KeeOTP extension which helps on also entering 2FA numbers.
Mahhn
Sounds great with having backups of the password DB, and I’m sure it works for most people, but it’s a single point of failure for all accounts. Without a password manager you would only loose control of one account if there is a compromise. Unless you are using the same password for everything, which is a main reason for people to use a manager, so it’s easy to have multiple passwords – but in reality, there is only one still (to access them all).
One Ring to rule them all…
I’m so jaded by reality
DasKreestof
Keepass also supports the use of a key file to get into your encrypted password database. I keep copies of my database and key file on a USB key, and every device I use. I keep a backup of the database only on a cloud service. I do not back up the key file to the cloud service. If an attacker had access to my database, and my password, they still can not open it without the key file.
Because I have backups of the keyfile at both home and work, I’m fairly protected from losing it.
richardartes
Great tip, thanks, I didn’t know that.
Mahhn
Good info, thank you.
rokenbecord
Just be careful you’re using the latest versions. [URL removed]
Mark Stockley
Sound advice, applies to all software though, not just versions of KeePass from 2012 ;)
l0l0l0l0l0l0l0l0l0l
I’m sorry, but there is NOTHING complex about KeePass unless you find it hard to remember your master password and you still can’t master copy and pasting.
Tom
I have to disagree. What I found to be a pain-in-the-you-know-what is that I would store the encrypted vault on a personal cloud computer, but if I made an update to a password, then I would have to go to all my phones and tablets and update the file that existed on the phone. LP and 1P at least offer to update the file on the fly.
But again it depends if you trust a third-party to store your encrypted vault with.
Kent Thomas
you can set it to auto sync. then you don’t have that issue.
Kent Thomas
I have been using now for 5 years. it is on my phone, tablet, and laptop. I keep another copy on a flash drive. All three are set up to sync up to a common database on a ftp site, that I maintain. I also keep current copies on my business server, and home server. It is very easy to set up with firefox, had some issues getting it to work with chrome. On problem which I don’t really consider a problem, is at times it will generate a password a web site will not accept, so I have to de-tune it. I find this especially true with banks, give them a complicated password and it gets rejected.
@pblakez
I use KeePass and others, the plugins in KeePass always worry me who is auditing the code in those, seems an ideal place to add an exfiltrator
Wilbur
I have been using KeyPass for years and it meets my needs without using any of the plugins. As “DasKreestof” said above, use of a keyfile protects backups, so a database, minus keyfile, could be stored on (say) Dropbox without excessive risk of compromise. I have seen people criticize the keyfile as “useless” since the keyfile is stored on the device used for access, but that misses the point of protecting a backup/remote copy. Another huge plus for KeyPass is availability on many different platforms and operating systems. I use it on OS X, Linux, iOS and Windows.
Laurence Marks
> collect additional entropy
Entropy is a measurement of the degree of disorder. Entropy is always increasing. Think of a wine glass, knocked from the table and shattered. This happens every day, but you never see the shards of a wine glass spontaneously assemble themselves into a whole glass.
Cryptography depends on very random numbers. If you were to plot them on a scatter plot, the graph area would be uniformly gray. If they were less than purely uniform, a code-breaker could figure out the cryptographic key. So let’s say they take
–the middle 16 digits of the 32-digit number of milliseconds since the computer was started
–multiplied by the middle 32-digits of the 60-digit number of Ethernet packets received
–divided by the middle 16 digits of the 32-digit number of Ethernet errors received
–times the number of milliseconds from January 1, 1970 until today.
Now, suppose you want a number with even better randomness. You select the option to “collect additional entropy” and you could be instructed to “wiggle the mouse” causing
–divided by the number of ‘mickeys’ your mouse has moved since the instruction
And then you are instructed to press the spacebar twice causing
–plus the number of milliseconds between the two spacebar presses.
Probably more than you wanted to know.
Len
Getting a working app for macOS is not simple. Looks like they want you to run an exe under some sort of emulator named Mono or Wine. Links to native mac files are on unfamiliar web sites. Can anyone help?
jkwilborn
Wine is an implementation of Windows running under a Linux type system. I believe that would open up the machine to windows malware… IMHO..
thedrogsofwar
When I was using KeePass (recently switched to LastPass), I used KeePassX on my Macbook and that worked fine. It’s listed in the “Contributed/Unofficial KeePass Ports” section under the official windows downloads on the KP site.
Justin
I have used Keepass since 2007. It’s an excellent piece of software and simple to use. I would not use any add-ons/plugins/extensions as they could easily compromise security.
Andrew
I’ve been using Keepass and KeepassX for years. On BSD systems, android tablets and phones and on my m$ laptop as well. I’ve been really happy with it. It’s not complex in the slightest. As far as I’m concerned if you consider this too complex, then perhaps computers are not for you.
Richard Sierakowski
Unlike commercial key mangers the code to KeePass is fully published and only that provides transparency as you can see what the code is doing. Don’t use plugins unless you see their code.
KeePass is ethical, fully peer reviewed code and that makes it just the best.
Richard
Paul Ducklin
Depends how much you trust those “peers”. The aura of presumed perfection that surrounds a lot of open source projects is just that – an aura. Many eyes over many years didn’t make the Heartbleed bug in OpenSSL shallow, for example… and TrueCrypt ended its life shrouded in a still-unexplained mystery.
Having the source code can indeed be a comfort – I am not calling for security through obscurity – but doesn’t ipso face make the product better and safer.
Keith A Roberts
Yes.
Was told about this at work and I’m fan of it, especially because you can use it to generate passwords for you when creating a new entry.
Now using KeePassX at home with Linux Mint 18 out of the box.
Sam
I use two plugins. One is a random passphrase generator, the other simply grabs a websites icon. I am a long time Keepass user and advocate.
Marvin
KeePass’s portable vault can also be used by other applications, extending your access to passwords beyond the desktop.
That is an attractive feature that I would like to see elsewhere. My password manager controls browser passwords but not email client passwords. So my point of vulnerability is my email – which can be used to reset passwords!
Paul Ducklin
Email 2FA FTW!
Marvin
I can see how 2FA would work with webmail (for things like gmail, but not so sure about other email hosts) – but then my existing password manager handles passwords on my browser!
If I am using an email client like say Thunderbird to manage a number of email accounts (POP and IMAP both with SMTP) polling the accounts every 10/15 minutes, how do I implement 2FA?
It would seem either I trust the password store in the email client and just look to the 3rd party password manager to control the master password, or I don’t trust the email client store and every time it polls an account it pops up the password dialogue – which I then want the 3rd party password manager to complete (and send the continue key stroke). I am not sure how 2FA fits into these scenarios without a lot of inconvenience every 10/15 minutes.
Chris
I’m a great fan of KeePass and use it at work and home. My one tip is to override the default auto-type sequence and change it to ‘{UserName}{TAB}{Password}’. The default sequence is the same but also has ‘{ENTER}’ on the end . I love the auto-type feature, but every now and again it gets things in a muddle and sends the output to the wrong window. When that wrong window is the company-wide IRC channel it’s a bit embarrassing! Removing the ‘{ENTER}’ takes this danger away – you still get the username and password auto-typed, but you get to check where it’s been sent before hitting enter yourself.
David
Sounds great. But if it is not cloud based how to do multiple members of a small business access it? and how does it sync? We are a business of 4 people.
Paul Ducklin
You could consider having one person “in charge” and circulate/share pre-encrypted password databases via a cloud-based file sharing service…
…or, given your situation, you might be better served by a cloud-based password manager to start with. You might find this a useful article to help you consider the cloud-versus-non-cloud argument:
https://nakedsecurity.sophos.com/2017/11/24/cloud-password-managers-would-you-use-one/
Tom Swift
I’ve been using KeePass for as long as I can remember. We just recently started using it at work, and what we’re doing is simply putting the kdbx file on a file server share. Works great.
Kent thomas
If your company computers are networked, then a copy of the database can be stored on one machine and shared. I keep a copy on our companies server, and then each machine in the company syncs to that database. If they are not networked, and have internet access, put a copy up on a google drive and share access to it. My personal copy resides on my laptop, syncs to our company server, google drive. It also syncs to my phone, two tablets, and my home server, when in range. If you can cut and paste into an application, you can save our passwords, etc on your keepass database.
5dlaxk
I use the KeePass Agent plugin to keep my SSH certificate pairs. It links to PuTTY for automatic secure passwordless access via SSH.
I like the auto sync feature which updates my android from my pc and visa versa. Via a cloud repository.
I like the “Lock on Desktop sleep”, or on switch user.
I intend to implement the extra USB key file security that DasKreestof suggests above.
I use a pronounce-able password generator, not for all passwords, though i acknowledge it makes passwords less secure. Sometimes I have to type them in.
All the plugins are open source and I check download hashes.
I’ve used this for decades and have 950 entries and counting.
5dlaxk
The best bit is keepass2android top notch application. It uses its own keyboard to prevent clipboard hijacks among many other things. I even donated to the developer.
Happy to debate the PC usability though. I’m recommending LastPass for my wife…