It should be no surprise this time of year that criminals are once again taking advantage of our focus on taxes and our hope to get some money back from the government. In this day and age we may need to update the old Benjamin Franklin adage “Nothing can be said to be certain, except death and taxes” to include phishing and malware.
This year is certainly a little different in that we are not just seeing phishing attacks, but also document attacks that are delivering ransomware strains like Locky.
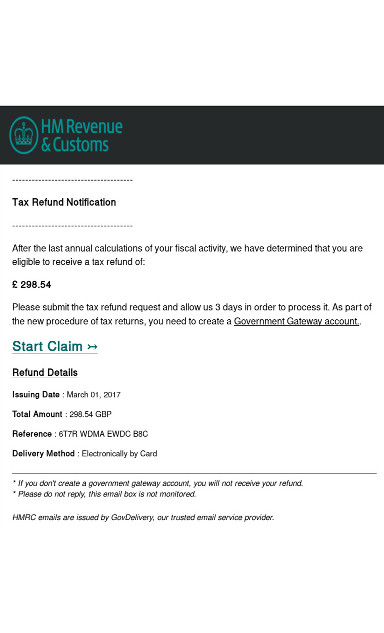
If you are a subject of Her Majesty living in the UK, you may see phishing attacks that are quite convincingly mimicking HMRC. This year they mostly promise refunds due for modest amounts to get you to click the link.
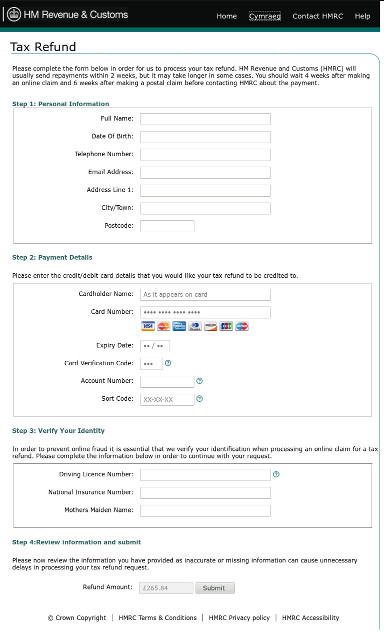
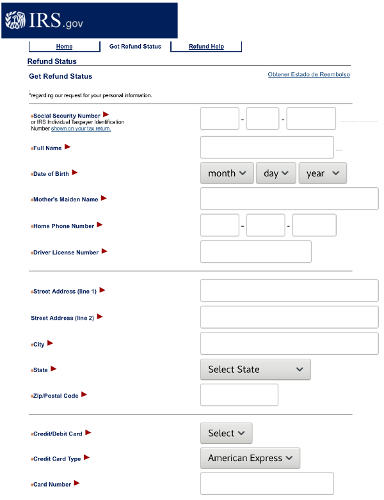
If you were convinced to click through, you would be delivered to a seemingly legitimate site asking for your name, address, phone, credit card details, mother’s maiden name and ID numbers. Interestingly, the link to the Welsh version of the site was broken.
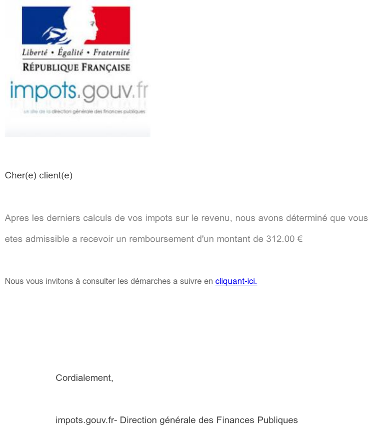
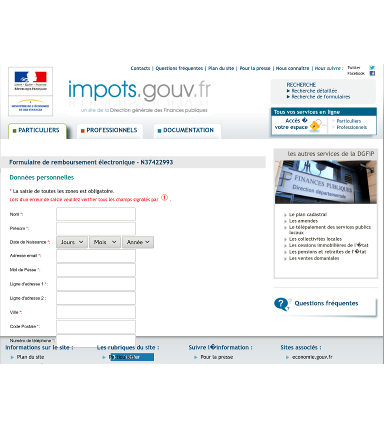
We are seeing similar lures for France as well. The emails and web sites are quite well crafted and you could understand how people may become victims.
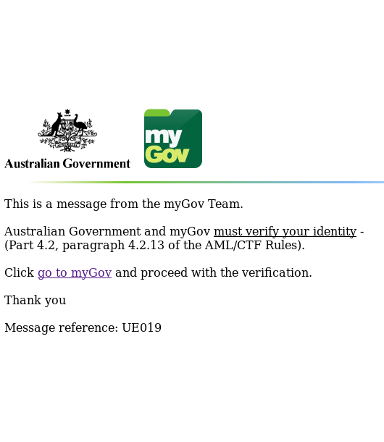
It isn’t tax season yet in Australia (although, even so, we have seen a few ATO phishes), but that isn’t stopping phishers from targeting Australia’s MyGov accounts. Sadly, the consolidation that makes government services easier to access for residents also attracts criminals. The only way to know this one isn’t real is to realize it shouldn’t be on a compromised Italian WordPress site.
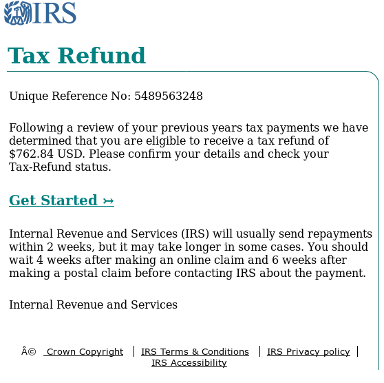
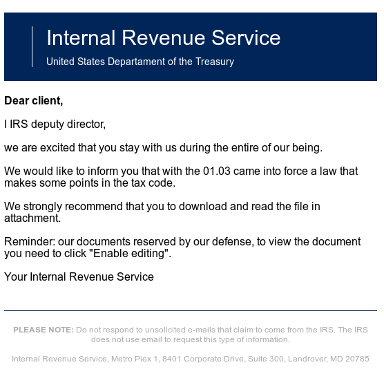
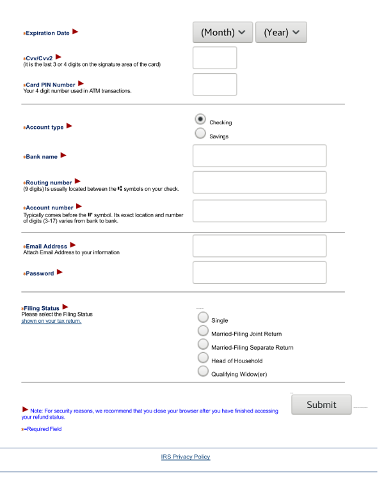
Lastly, the Americans. Too big an opportunity to pass up, as we have been seeing both phishing and document attacks since Friday April 7, leading to information theft and ransomware. The left email leads to data theft (copied from an HMRC phish, note the “Crown Copyright”); the right contains a .docx attachment with a malicious macro and script.
The phishing attempt here asks for a lot more information than needed for simple tax fraud, including credit card PIN, driver’s license, and email password, which means they are likely using this information for full-fledged ID theft as well.
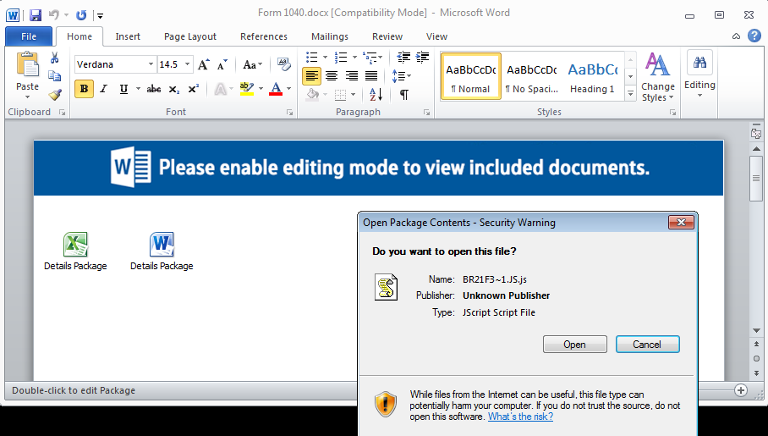
The document attached to the second IRS scam follows a familiar pattern for those following the scourge of ransomware-poisoned Office documents. It asks you to enable a macro that decodes a JavaScript file that retrieves a copy of Locky ransomware from a compromised blog.
There’s nothing special about tax season; we need to stay on our toes all year round. This is just a reminder that these tricks can be very sophisticated and we need to stay vigilant. Your tax agency will never email you a refund, and if you have any questions, always contact them through their official government websites.
Sophos detects the malicious document as Troj/DocDl-IPH and payload as Mal/Generic-S, and these emails are blocked by Sophos email products. Sometimes phishing can only be prevented through careful habits and we can help with that too. Sophos Central now offers Sophos Phish Threat to teach and test your security awareness initiatives, including a free 30-day trial.