Phone booths: they’re so retro. So inextricably tied to Clark Kent and the quick donning of leotards.
Wherever you find them, payphones seem antiquated in this era of cellular telephones.
But in a sprawling metropolis such as New York, even though they’re outdated, they’re still ubiquitous.
What to do with all that infrastructure?
In New York, you replace them with Wi-Fi hotspots.
On Monday, the city finally launched LinkNYC: a plan, first announced in November 2014, to convert more than 7000 payphones into hotspots linked into a wireless network covering all of the city’s five boroughs.
The Verge first spotted a “beta” Link hub outside a Starbucks at Fifteenth and Third, near Manhattan’s Union Square.
According to LinkNYC’s FAQ, each hub will offer free services like high-speed Wi-Fi, phone calls, touchscreen web browsing, and device charging.
There will be over 7500 Links installed over the coming years to form what NYC Mayor Bill de Blasio claims will be “the fastest and largest municipal Wi-Fi network in the world – accessible to and free for all New Yorkers and visitors alike.”
As Naked Security’s Paul Ducklin noted in our Advent tip #20, free Wi-Fi can be especially handy for travelers.
For example, it’s a lifesaver when you disembark from an overseas plane trip and find that your mobile phone company hasn’t enabled roaming yet, and you need to call for your ride.
Free Wi-Fi can also help you out if you’re faced with a gigabyte’s worth of security updates while on the road, but you have only a few hundred megabytes of mobile data left.
Yes, fast, free internet access can be manna from digital heaven – but only if you keep your wits about you.
We’ve listed some of the risks of free, open Wi-Fi before, and they’re worth repeating here:
- The hotspot could be run by anyone, and there’s almost no way of telling who that might be.
- Anyone in the vicinity, whether they’re on the network or not, can “sniff” (eavesdrop on) and record all your network traffic.
- Your DNS requests, which turn server names into network numbers, are visible to anyone, so even if you subsequently use secure HTTPS connections only, the services you’re using are nevertheless revealed.
- The hotspot can send you bogus DNS replies, redirecting you to imposter servers, blocking your access to security updates, and more.
In addition, free hotspots often rely on a login page, rather tellingly known as a captive portal, where you have to first sign up for the service, even if your plan once online is to hop onto your own Virtual Private Network (VPN) to keep your network traffic secure.
Basically, a VPN encrypts all your network data before it leaves your phone or laptop, sending the scrambled stream of data back to your own network and decrypting it there before it gets sent to the internet.
But back to those portal pages, which intercept all your network traffic until you’ve signed up, thus standing between you and that nice, safe VPN.
While you’re in the captive portal’s “network jail,” you’re subject to all the risks listed above – and more.
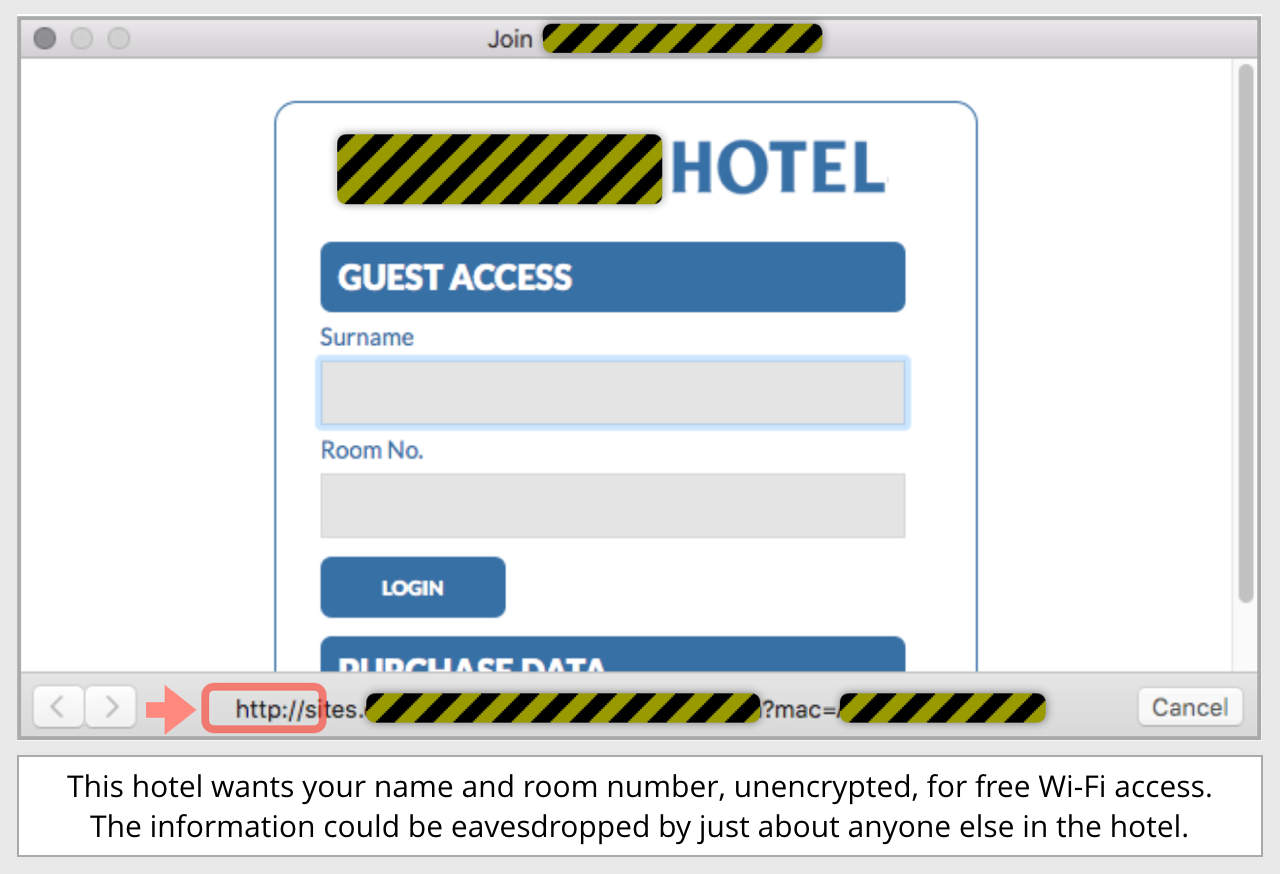
For example, Naked Security’s Paul Ducklin recently documented a Wi-Fi security hole at a hotel in which he stayed, where getting access to the network required you to confirm that you were a registered guest by entering your name and room number.
But that was done over an unencrypted HTTP connection, so anyone in the vicinity could sniff those logins and build up a guest list. (One commenter on that story pointed out that he’d recently asked a hotel to replace his room keycard – for which the security check was to give a name and room number.)
And Paul reported being caught out by a captive portal again – ironically while we were discussing this very article.
He was in a historic building in which mobile network penetration was very poor, but there was a surprisingly generous free Wi-Fi service to make up for it, offering a whopping 40GB of free data each month.
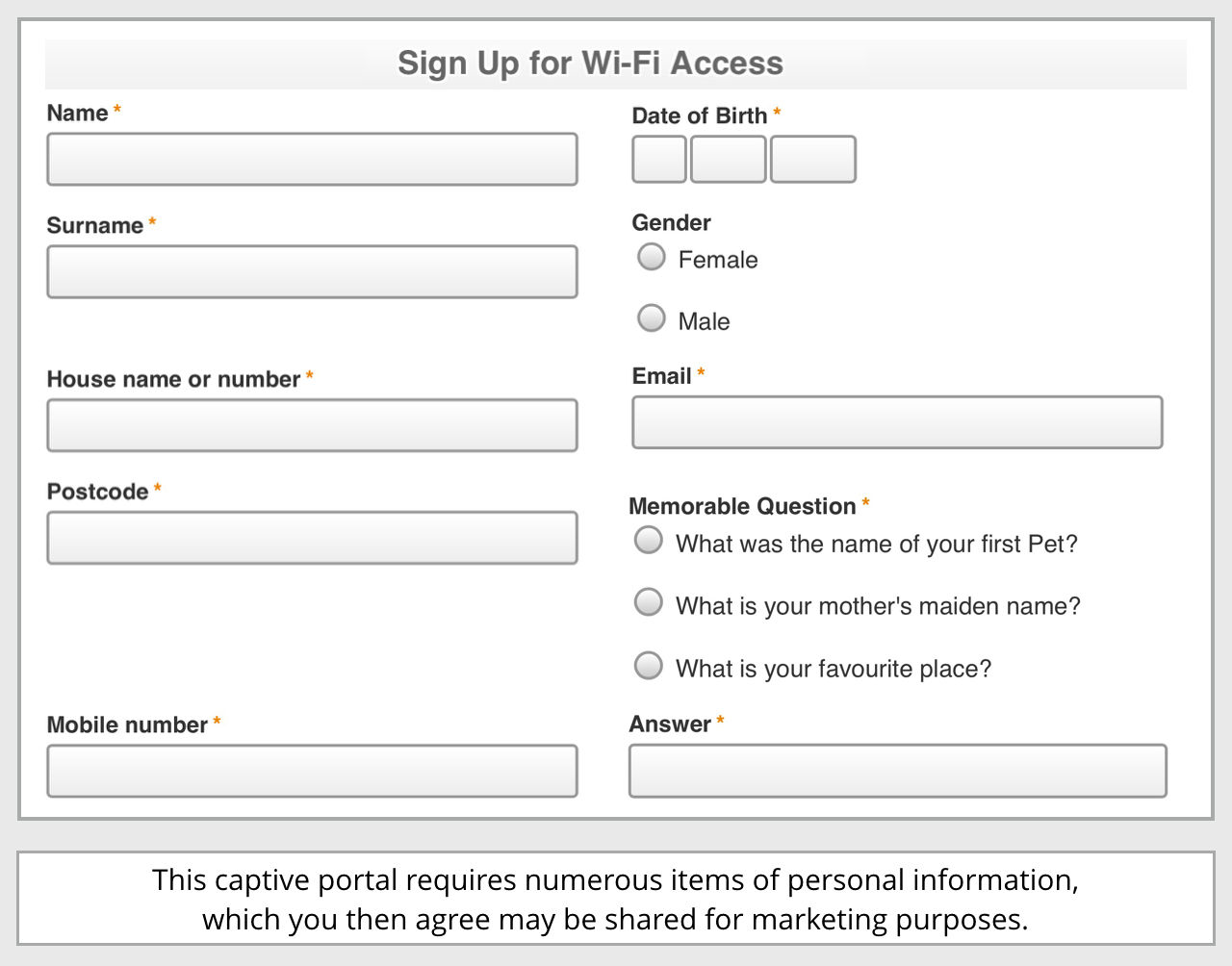
But there was a price – the sign-up process (which, at least, was encrypted using HTTPS) asked for personally identifiable information (PII), including full name, address, mobile number, email, date of birth and even a “memorable answer” to one of three security questions.
Also, the signup process included an explicit condition that “you can use this service so long as you agree that [the network operator plus its group companies] and selected third parties my use your information to communicate with you for marketing purposes.”
In other words, your name, address, email birthday and more will almost certainly end up being shared around.
Which brings us back to LinkNYC: as The Verge noted, there was a bit of a ruckus when it was found that one of the companies involved in the hubs, Titan, had implanted Bluetooth beacons in the test hubs.
This is technology that potentially could have been used not only to push ads, but also to track people in the street by logging the time they passed each Bluetooth beacon, and recording details about their device.
(That might sound familiar if you’re a Londoner, given the city’s history with spying rubbish bins.)
The LinkNYC beacons were removed shortly after their existence was made public, at the request of City Hall.
Another of the companies involved in LinkNYC, CityBridge, has emphasized that it takes security and privacy seriously, and that it’s created a “forward-thinking policy”, but it hasn’t yet published the policy, the details of how it handles encryption, or anyything else about the system.
A LinkNYC spokeswoman told me that this first Link is for testing purposes, not for public use, yet.
More details on features and functionality will be released next week.
Hopefully, those forthcoming details will help us to figure out what kind of risks users might face with LinkNYC.
More details should come in handy for judging the risks users will face during that “shields down” period while they sign up for, or sign into, the network.
Remember, as explained above, that captive portals usually put you in a bit of a security Catch-22: you can’t connect to your VPN to cloak your traffic until after you’ve done a little bit of uncloaked browsing.
During that time, even if you are careful what you do inside your browser, background apps on your phone or laptop may give away information about you, your device, the settings on your device, and more.
Best to look that gift horse in the mouth!
LinkNYC promises encrypted communications and talks about taking security and privacy seriously, so hopefully it’s not giving away Wi-Fi that has holes in it.
The proof will be in the pudding…
Image of pay phone courtesy of Shutterstock.

vikasbhatiauk (@vikasbhatiauk)
I live in NYC and i have seen some phoneboxes with the “covers” removed exposing the hardware that supports the phone. It wont take long for people to realize that and put in place MITM type devices.
Anonymous
This is a “Hacker’s Heaven,” personally I do not trust NYC will take the necessary measures to secure the WiFi hotspots. However, being an Cyber Security Professional it would be great if there was a Security Operations Center open to support the infrastructure and provide jobs to other Cyber Security Professionals.
Not
If you don’t like the conditions attached to a “free” service, then don’t use it. Anything else is just whining about your choice.
Paul Ducklin
We’re not whining, of course. We’re just reminding you to balance the costs against the benefits. And to read the small print.
In Lisa’s words, “Best to look that gift horse in the mouth.”
Porkies
“In other words, your name, address, email birthday and more will almost certainly end up being shared around.”
Of course with free wi-fi you can probably tell absolute porkies when asked for this PII. If your email has to be usable you can always use a disposable one from the likes of abine or blur. Most sites don’t check that the answers are sensible – I think one site has me born sometime in the 1800s! My bank allows me to give totally false answers to some questions, so for instance “What is your favourite place” could have a non-place as an answer – you could answer “Donald Trump”.
Paul Ducklin
Indeed, but for many of these services, the mobile number has to be yours (or at least under your control), as you often get an activation code via SMS.
So, if you do make up nonsense, it’s still associated with your account – tied to you by phone number – and so the responsibility remains yours. So make sure you choose a decent password, where a login has to be created, and keep track of your answers in case you want to kill off the account in future. (Contract phones are inevitably tied to you, and in some countries, pre-paid mobiles also require proof of ID and address for activation.)
Ronin Akechi
There’s no such thing as “free”. You can bet that taxpayer money is being spent to the benefit of the companies setting up the infrastructure. You can also bet that there will be profit made on the back end as well– whether through advertising or use of your personal information, etc.