The website and Twitter account for sleek electric automaker Tesla Motors was taken over and defaced on Saturday, as was Tesla CEO Elon Musk’s personal Twitter account.
The first bump in the road came around 1:52 pm PDT, when a tweet from the Tesla account declared that it was under the control of its attackers.
Those attackers changed the account name from “Tesla Motors” to “#RIPPRGANG”.
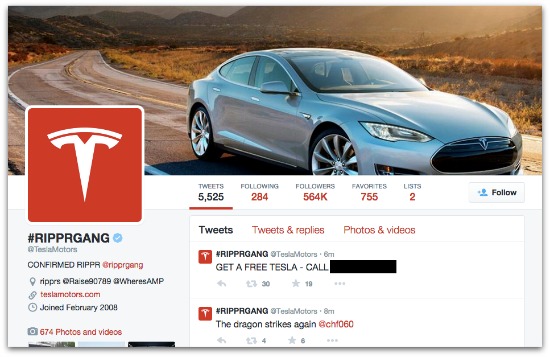
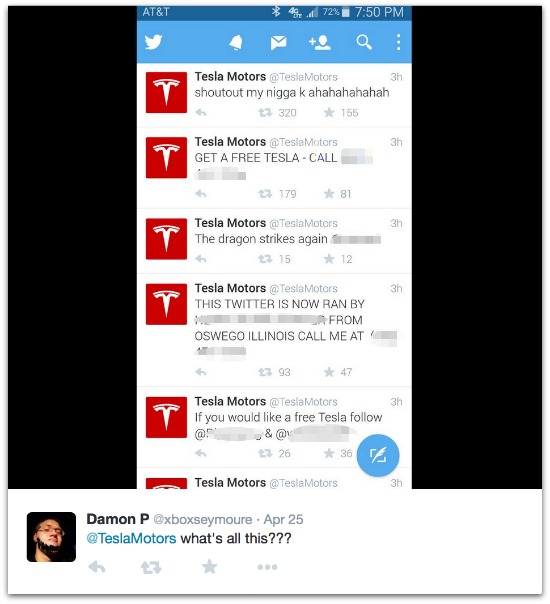
The hijacked account began promising free Teslas if you followed certain Twitter accounts or called a phone number belonging to a computer repair shop in Illinois.
Twitter user @xboxseymoure captured a string of the attackers’ tweets, which as of Monday had been wiped off the recovered account.
Tesla’s site was also defaced around the same time by the same group.
According to CBS San Francisco, site visitors were redirected to a website showing an “expletive-laden ranting video” which played over a photoshopped picture of a boy’s face on Osama Bin Laden’s body behind the wheel of a Tesla. It was branded “Hacked by Autismsquad.”
Within a half hour, Tesla was apparently aware of the situation, since the site had been taken offline.
But an apparent wrestling match ensued over the next few hours as the hijacked page came back multiple times, Tech Crunch reports, and the Twitter account continued to emit messages that apparently came from the attackers.
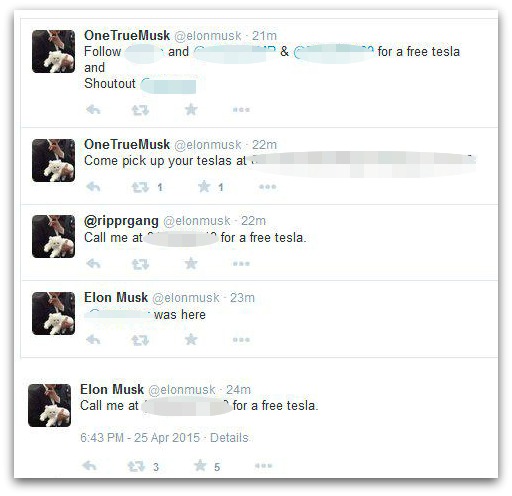
Some of the Tweets the attackers sent out from Musk’s account:
As of Monday, Tesla hadn’t responded to media questions about how the attack was pulled off, or whether the security of its servers had been compromised.
What we do know is that two-factor authentication (2FA) is a strong preventative measure against getting accounts taken over.
Twitter is an extremely popular target when it comes to account hijacking.
It’s full of high-profile accounts whose owners would suffer acute embarrassment if they’re taken over, including government organisations, celebrities and big companies.
Heck, even Twitter itself isn’t immune, as was evidenced by the takeover of Twitter CFO Anthony Noto’s account.
Many high-profile accounts are typically updated by multiple people, and hence, may well be more likely to have limp, easy passwords that the whole team can remember – or ones that the team sends to each other via email/texting or that are scribbled onto sticky notes and slapped onto monitors.
Twitter in February put out a tool, called TweetDeck Teams, to help such accounts stop password sharing and hopefully fend off hijackings. If you share an account with someone else, make sure you use this tool.
And, as we say too often here on Naked Security, make sure you pick a proper password.
