Looking through the SophosLabs spamtraps recently revealed an interesting malware distribution campaign.
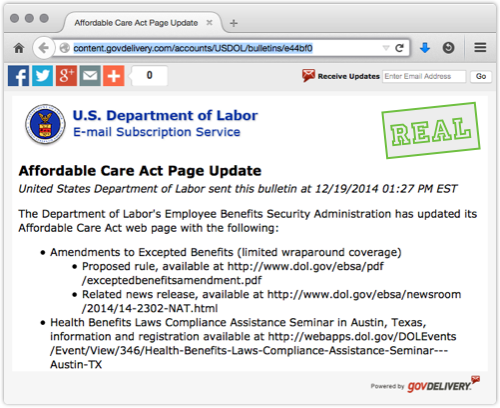
Late in December 2014 the US Department of Labor issued an email bulletin that looked like this:
That’s a perfectly useful notification, documenting a routine update to US Health Care regulations.
Indeed, this sort of email subscription service can be considered a good example of legislative transparency, helping interested parties to keep up with changes without requiring them to keep digging through mounds of documentation looking for updates.
Unfortunately, official emails and web bulletins are also a handy source of believable content for spammers, phishers and scammers.
They provide professionally written text, usually free of the grammatical and orthographic abuse that gives away many phishing emails.
The have a look-and-feel with which many people will be familiar.
Additionally, they provide logos and artwork that not only look right, but also originate from the official servers.
In this case, the crooks have come up with this phish:

Hovering over the (admittedly rather unlikely-looking) FOLLOW THIS link should give the game away.
Instead of being hosted on a dol.gov server, like the real Department of Labor documents, this one is “hosted” on the website of a Turkish nutrition business.
Judging by the URL that the crooks have used, it looks as though they’ve camped in a subdirectory on the server that belongs to a WordPress plugin.
If so, that plugin is presumably one that either has not been correctly configured, or, more likely, has not been patched against known security holes.
What happens next?
If you are genuinely unsuspicious, or decide to “take a look” just in case, you will be redirected to a corporate webinar hosting platform and urged:

The PDF file you are offered has the vaguely believable name of health_coverage_webcast.pdf, but it is no such thing.
That’s not the filename-and-extension but just the filename.
What you end up with is the double-extensioned file health_coverage_webcast.pdf.scr.
The ending .SCR usually denotes a screensaver, which is actually just a special sort of Windows program.
Of course, just as there’s no PDF (and no webinar), there’s no screensaver either.
Instead, you end up with a downloader program that infects your computer with a variant of the Vawtrak banking malware, detected by Sophos products as Mal/Vawtrak-H.
Vawtrak is a notorious family of malware that we covered in some detail late last year.
As SophosLabs botnet expert James Wyke wrote:
The Vawtrak botnet is [...] being used as part of a Crimeware-as-a-Service (CaaS) business model where the output of the botnet can be adjusted on demand, with financial data effectively being stolen to order.
He wasn’t joking when he said:
Rest assured, SophosLabs will continue to monitor this threat.
For more information
• Learn more: ‘Vawtrak’ malware becomes more evasive
• Read our report: Vawtrak – International Crimeware-as-a-Service
• Learn more: How bots and zombies work
• Listen to our Techknow podcast: Understanding Botnets
![]()
(Audio player above not working? Download or listen on Soundcloud.)