 If you like to keep connected while you’re up in the air, you should be aware that the in-flight Wi-Fi service Gogo is pulling what some are characterizing as a man-in-the-middle attack by issuing fake digital certificates as a way to throttle high-bandwidth websites.
If you like to keep connected while you’re up in the air, you should be aware that the in-flight Wi-Fi service Gogo is pulling what some are characterizing as a man-in-the-middle attack by issuing fake digital certificates as a way to throttle high-bandwidth websites.
Google Chrome security team engineer Adrienne Porter Felt first noticed the bogus SSL certificate while trying to get to the (Google-owned) YouTube site during a flight.
Instead of receiving the Google-issued certificate she expected, she got one from Gogo, with a red-letter warning saying that it came from an untrusted issuer.
She tweeted the certificate late last week and asked just what, exactly, was Gogo up to?
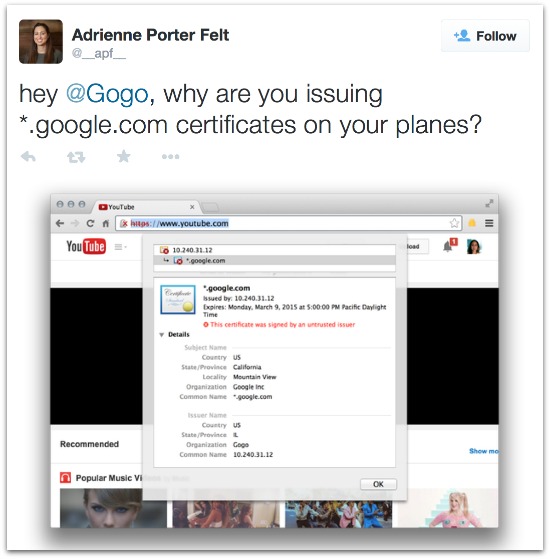
hey @Gogo, why are you issuing *.google.com certificates on your planes?
It’s understandable why she’d be concerned and why privacy and security experts are reaching for the aspirin.
While modern-day browsers, including Chrome, will flag a bogus certificate, the practice of issuing fake certificates could, at least in theory, set Gogo up to be in the same position as the man in the middle of a man-in-the-middle (MitM) attack, issuing fake security certificates that allow it to view passwords and other sensitive information exchanged between users and YouTube – or whatever other service Gogo might use the technique to block.
The way it’s supposed to work is that the SSL/TLS protocol ensures a route for secure communication with the use of SSL certificates, making it difficult for sensitive data such as credit card numbers or passwords to be intercepted.
In order to succeed, a MitM attack requires an attacker to set up a mutual authentication between two communicating parties.
Cryptographic protocols provide some form of endpoint authentication – Secure Sockets Layer (SSL) is typically used to authenticate one or both parties, with a mutually trusted certificate authority – specifically to block MitM attacks on users.
Snooping on someone’s communications would require an attack on that SSL certificate.
In response to Felt’s text, Gogo Executive Vice President and Chief Technology Officer Anand Chari released a statement saying that the broadband provider is absolutely not stealing users’ private data.
Rather, the rigged certificate is all about enforcing the company’s no-streaming policy, he said.
Gogo uses several techniques to block or limit video streaming, he said, including a recent off-the-shelf tool that proxies secure video traffic in order for Gogo to block it.
In fact, Chari said, the use of the technique to “shape bandwidth” only affects some secure video streaming sites and doesn’t affect “general secure internet traffic”.
It’s meant to ensure that all those who want to use Gogo get a fair shake at a decent browsing experience, and not as a way to grab users’ private information, he said:
We can assure customers that no user information is being collected when any of these techniques are being used. They are simply ways of making sure all passengers who want to access the internet in flight have a good experience.
Felt says that she wasn’t actually trying to stream video when she received the false certificate and was instead only trying to fix a broken YouTube page:
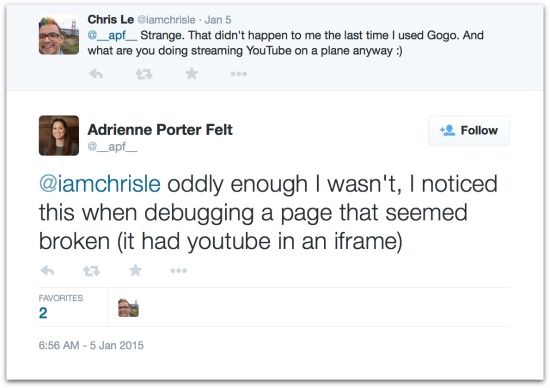
@iamchrisle oddly enough I wasn't, I noticed this when debugging a page that seemed broken (it had youtube in an iframe)
The security engineer herself doesn’t believe that Gogo is up to anything maliciously MitM-ish, though she did tell the Google account manager to kill active sessions:
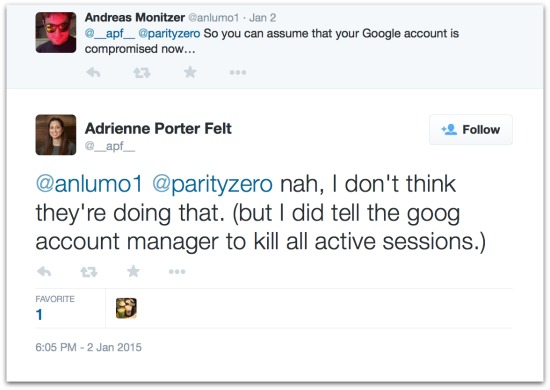
@anlumo1 @parityzero nah, I don't think they're doing that. (but I did tell the goog account manager to kill all active sessions.)
If a Google security engineer isn’t worried about this, perhaps we can all unhunch our shoulders a bit?
Or perhaps not.
After all, Gogo was recently caught bragging about how it goes above and beyond to enable the US to snoop on passengers.
Perhaps we should still keep a watchful eye out – not just on Gogo, but on any company that feels justified in falsifying SSL certificates a la malicious attackers.
Image of plane courtesy of Shutterstock.
