For most small and mid-sized organizations, the reality of ‘moving to the cloud’ has been a gradual transition of on-premises resources to the cloud, with many now running hybrid environments.
To understand the reality of cloud security today for SMBs, Sophos commissioned a survey of 4,984 IT professionals across 31 countries whose organizations use Infrastructure as a Service (IaaS). This vendor-agnostic study was conducted by Vanson Bourne, a leading independent research agency.
The findings highlight considerable gaps in cloud defenses for SMB organizations together with opportunities for improvement. They also demonstrate the real-world benefits of strong cloud practice on an organization’s experience of cyberthreats.
The Cloud Is a Growing Target for Cyberattacks
As use of the cloud increases, so does the focus it receives from cyber criminals. The survey revealed major changes in IaaS users’ experience of cyberattacks over the last year:
- 56% experienced an increase in volume of attacks on their organization
- 59% experienced an increase in complexity of attacks on their organization
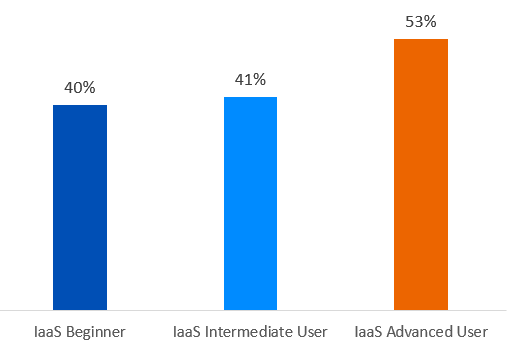
- 53% experienced an increase in impact of attacks on their organization
- 67% reported that their organization was hit by ransomware
It is clear that the challenge facing defenders in the cloud is increasing rapidly.
Strong Cloud Practice Reduces Threat Exposure
The good news is that advanced IaaS users are twice as likely to report a decrease in attack volume, complexity and impact over the last year than beginners. For example, 38% of advanced users reported that the impact of attacks had decreased over the last year compared to 19% of beginners.
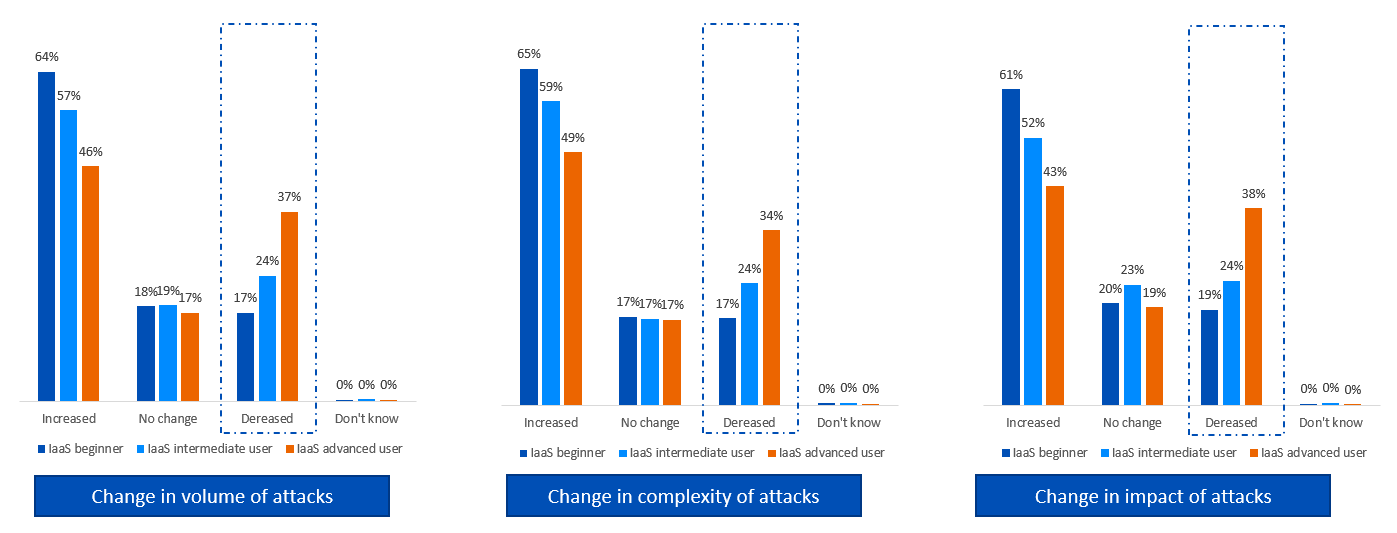
The data also reveals that advanced cloud users are far less likely to have experienced an increase in the volume, complexity, and impact of an attack; for example, 61% of beginners reported an increase in attack impact compared to only 43% of advanced users.
Attack Surface Weaknesses Revealed
Resource misconfigurations and unpatched vulnerabilities leave the door wide open for ransomware actors and other adversaries to get into your environment and carry out their attack.
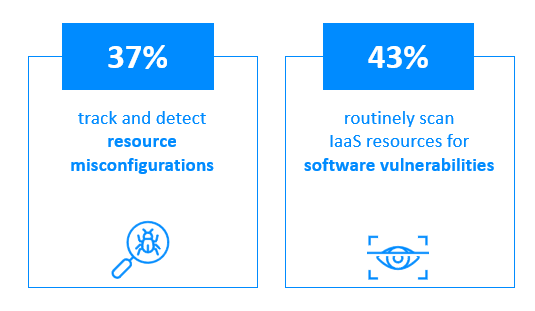
Unfortunately, most SMBs are highly exposed in this area. Only 37% of survey respondents said their organization tracks and detects resource misconfigurations in their IaaS infrastructure. What’s more, fewer than half (47%) said they routinely scan IaaS resources for software vulnerabilities.
IT Teams Are Blind to Resources and Configurations
Adversaries commonly exploit stolen credentials and access data to access and compromise accounts. Once inside an organization, it’s often fairly easy for them to escalate privileges and move laterally across the victim’s infrastructure to carry out their attack.
Having visibility of all your resources and their configurations so you can quickly spot compromise and then take action is an important element of an effective cloud security strategy.
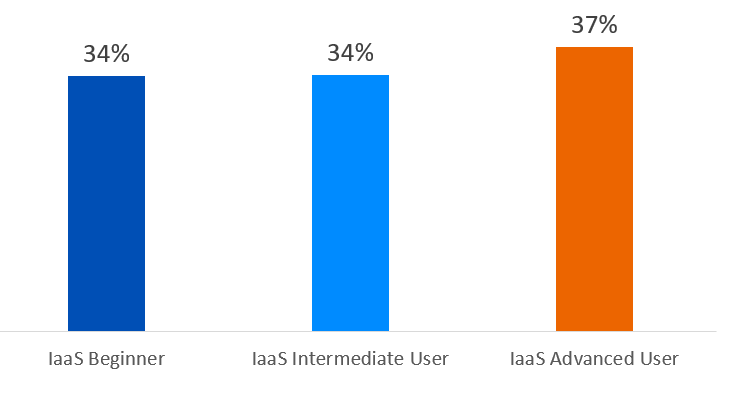
However, the survey reveals that this is a major security gap for almost two in three cloud users. Interestingly – and concerningly – there is little variation according to level of cloud experience: 34% of beginner and intermediate IaaS users have visibility of all resources and their configurations in their IaaS infrastructure, and this rises to just 37% for advanced users. This is a clear opportunity for organizations to elevate their cloud defenses.
24/7 Threat Detection and Response Capabilities
The reality is that not all threats can be prevented automatically as attackers increasingly exploit legitimate IT tools and unpatched vulnerabilities to avoid triggering protection solutions. Stopping today’s most advanced attacks requires a combination of technology and human expertise.
Threat detection and response is a 24/7 activity with adversaries conducting attacks at any time of day or night. However, the study revealed very few organizations have the necessary resources to hunt down and neutralize active adversaries around the clock.
In fact, only one in three (33%) IaaS users says their organization has the resources to continuously detect, investigate and remove threats in their IaaS infrastructure. And only one in four (40%) has processes in place to respond to IaaS infrastructure security incidents 24/7, with intermediate and advanced IaaS users a little better positioned than beginners.

As the challenges facing defenders continues to grow, many organizations are turning to managed detection and response (MDR) services, with Gartner anticipating that 50% of organizations will use MDR by 2025*.
Secure Access To Cloud Resources
The role of the firewall in securing access to on-premises resources is already well established. When it comes to securing the cloud, you need to apply the same principles you used for hardware firewalls to virtual firewalls.
Given the parallels between traditional and virtual firewalls it is perhaps surprising that the survey revealed that fewer than half of organizations have strong defenses in place here: only 40% have IPS in place to secure their IaaS infrastructure and just 44% use a WAF to protect web-facing applications and APIs.
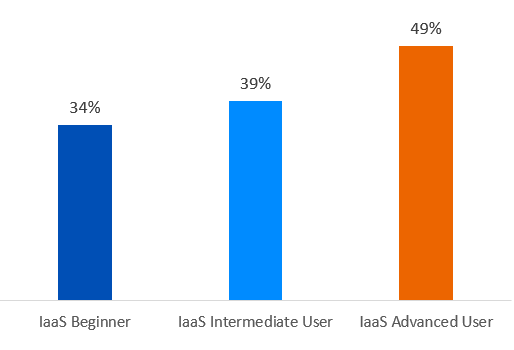
Interestingly, this is one area where we see advanced users reporting much higher adoption of best practices than beginner and intermediate users. Almost half (49%) of advanced IaaS users have IPS in place compared to 34% of beginners, and 53% of advanced users deploy WAF to secure their cloud-based resources compared with just 40% of those in the early stages of their IaaS journey.
To Sum Up
Just as the use of the cloud is an ongoing process of transition for many organizations, so is cloud security. Many of the principles are the same as for traditional on-premises security, with adaptations to reflect the differences in cloud usage and threat risk.
By addressing the security gaps highlighted in this research, small and mid-sized organizations can elevate their defenses and minimize their risk of experiencing a major cloud security incident.
How Sophos Can Help
Sophos is a global cloud security specialist, working with all leading cloud providers including AWS, Azure, Google Cloud (GCP) and Oracle. Today, Sophos secures over 530,000 organizations around the world and we are proud to be the only vendor named a Gartner Peer Insights Customers’ Choice for both endpoint and network security**. Our cloud security solutions include:
- Sophos Cloud Native Security (CNS) provides complete cloud security coverage, enabling you to protect all your servicers, from on-premises to single and multi-cloud, Windows to Linux.
- Sophos Firewall offers powerful network visibility, protection, and response to secure your public, private, and hybrid cloud environments. With preconfigured virtual machines in both Azure and AWS, you can be up and running quickly.
- Sophos MDR is our market-leading 24/7 managed detection and response service. We use the tools you already have in place, including your cloud provider telemetry, to identify and stop advanced, human-led attacks before they can impact your business.
For more information on Sophos solutions and to arrange a test drive, speak to your Sophos adviser or visit www.sophos.com.
* Gartner Market Guide for Managed Detection and Response 2021
**Gartner Peer Insights content consists of the opinions of individual end users based on their own experiences with the vendors listed on the platform, should not be construed as statements of fact, nor do they represent the views of Gartner or its affiliates. Gartner does not endorse any vendor, product or service depicted in this content nor makes any warranties, expressed or implied, with respect to this content, about its accuracy or completeness, including any warranties of merchantability or fitness for a particular purpose. Gartner Peer Insights Customers’ Choice constitute the subjective opinions of individual end-user reviews, ratings, and data applied against a documented methodology; they neither represent the views of, nor constitute an endorsement by, Gartner or its affiliates.