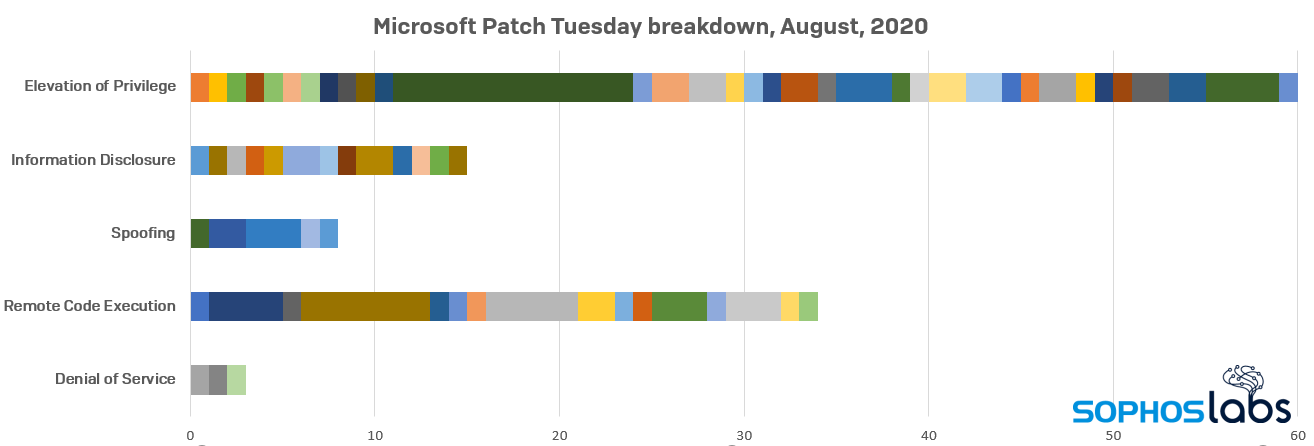
Microsoft has squished 120 bugs in this month’s release of software updates spanning its product lines. While the total number of bugs that have been fixed this month dropped slightly compared to last month, the number of critical bugs fixed this month was higher, at 32, compared to July’s 20.
All but one of those critical fixes addressed a remote code execution vulnerability that affected the .NET framework (CVE-2020-1046), media codecs (CVE-2020-1560, -1574, -1585) and engines (CVE-2020-1379, -1477, -1492, -1525, -1554), scripting engines (CVE-2020-1555, -1567, -1570), and the Edge browser’s PDF renderer (CVE-2020-1568). The only non-RCE critical vulnerability is a privilege escalation that affects the Netlogon component (CVE-2020-1472).
The bug that affects the Print Spooler isn’t critical, but both the relatively old code (the bug affects systems as mature as Windows 7) and its assigned CVE number are notable. The bug was a subject of a talk at the Black Hat Briefings which took place last week. This privilege escalation bug, classified “important,” picked up the most elite reference of the year: CVE-2020-1337. Someone has a sense of humor.

While readers can find the full details about every patch this month in Microsoft’s Security Update Guide Release Notes, and Servicing Stack Updates, and users can download patches manually from the Microsoft Security Update Catalog, the Offensive Research team passed along some notes about the patches they found most interesting.
Windows Spoofing Vulnerability
CVE-2020-1464
This vulnerability, formerly titled “Windows Authenticode Signature Spoofing Vulnerability,” has already been exploited in “in the wild” attacks. Authenticode is the component of Windows that validates cryptographically-signed binaries (eg., drivers) and executables. These are important because in latter-day editions of Windows 10, you can’t (for example) load driver files that have not been certified as valid by a legitimate signing authority.
Well, that’s an important security feature, since we’ve been observing for months that ransomware has been using a variety of bypasses to load unsigned driver files, which then are used to load the ransomware payload at a level where some endpoint security products are unable to prevent the ransomware from doing damage.
So while Microsoft has only classified this particular patch as “important,” and not “critical,” it’s actually quite critical that you install updates so your system cannot be abused in this way. Deferring the installation of this patch can have far reaching, negative consequences.
Scripting Engine Memory Corruption Vulnerability
CVE-2020-1380
As if we all didn’t need another reason not to use Internet Explorer anymore, something like this comes along. The bug is a Use After Free vulnerability, in the JIT compiler of Internet Explorer’s JavaScript engine. While bugs like this may lead to remote code execution and compromise if you visit the wrong website with Internet Explorer, we all know better than to use that browser, anymore. Right?
Right?
The bug itself is unremarkable and is similar to your average IE vulnerability that comes a dime a dozen.
If you’re still using Internet Explorer, and you aren’t teaching a lesson on computer history in a museum exhibit, please switch to a modern browser.
Windows dnsrslvr.dll Elevation of Privilege Vulnerability
CVE-2020-1584
the DNS Client network service’s main purpose is to cache DNS (Domain Name System) results, optimizing network communications. It’s enabled by default on Windows systems.
The bug (in the DNS Client’s dnsrslvr.dll library) is an Integer Overflow vulnerability that, when triggered, results in an undersized memory allocation, and a subsequent memory corruption. It’s the memory corruption that may lead to arbitrary code execution.
The vulnerable code path is reachable by the RPC (Remote Procedure Call) invocation of certain methods implemented by the DNS Client service. This can be done by applications running on the same system. Upon successful exploitation, an application may elevate its privileges to that of a network service – “NT AUTHORITY\NETWORK SERVICE” privileges.
This is only the second time a vulnerability has been reported in dnsrslvr.dll, the previous one (CVE-2019-1090) only having been discovered last year.
Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
CVE-2020-1587
The file afd.sys is the driver responsible for the Windows kernel’s side of Winsock (Windows Sockets) functionality. It has a Race Condition vulnerability: An attacker can attempt to “race” multiple threads into executing the vulnerable code concurrently. If the timing is precise, and the “race” is won, a Use After Free condition follows, and ultimately an attacker can run arbitrary code.
This bug was mitigated by the introduction of proper thread synchronization around the vulnerable code.
Despite the driver’s name and purpose, the bug itself is not part of networking code and is not reachable by network traffic. It is only triggerable by applications running on the same system. If such an application interacts with afd and successfully exploits the bug, it can escalate its privileges to Kernel privileges.
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
| CVE | SAV | IPS |
|---|---|---|
| CVE-2020-1380 | Exp/20201380-A | SID:9000225 |
| CVE-2020-1567 | Exp/20201567-A | SID:2303521 |
| CVE-2020-1570 | Exp/20201570-A | SID:2303522 |
| CVE-2020-1578 | SID:2303523 |
How long does it take to have Sophos detection in place?
We aim to add detection to critical issues based on the type and nature of the vulnerabilities as soon as possible. In many cases, existing detections will catch exploit attempts without the need for updates.