Network traffic encryption levels continue to steadily increase. In the last year, the percentage of pages loaded over HTTPS as reported by Google has increased from 82% to 87% on the Windows platform. It’s even higher on Macs at 93%. At this rate, we are not far away from a 100% TLS-encrypted Internet.
In this second in a series of articles on making the most of the great new features in XG Firewall v18, we’re going to specifically focus on resources available to you in order to make the most of the new Xstream TLS 1.3 inspection solution in XG Firewall v18.
Xstream TLS inspection
In our last article, we covered the Xstream architecture and the new Xstream DPI engine in XG Firewall v18. The new TLS inspection solution is a key component of the new architecture and provides decryption for TLS/SSL-encrypted traffic with native support for the latest TLS 1.3 standard.
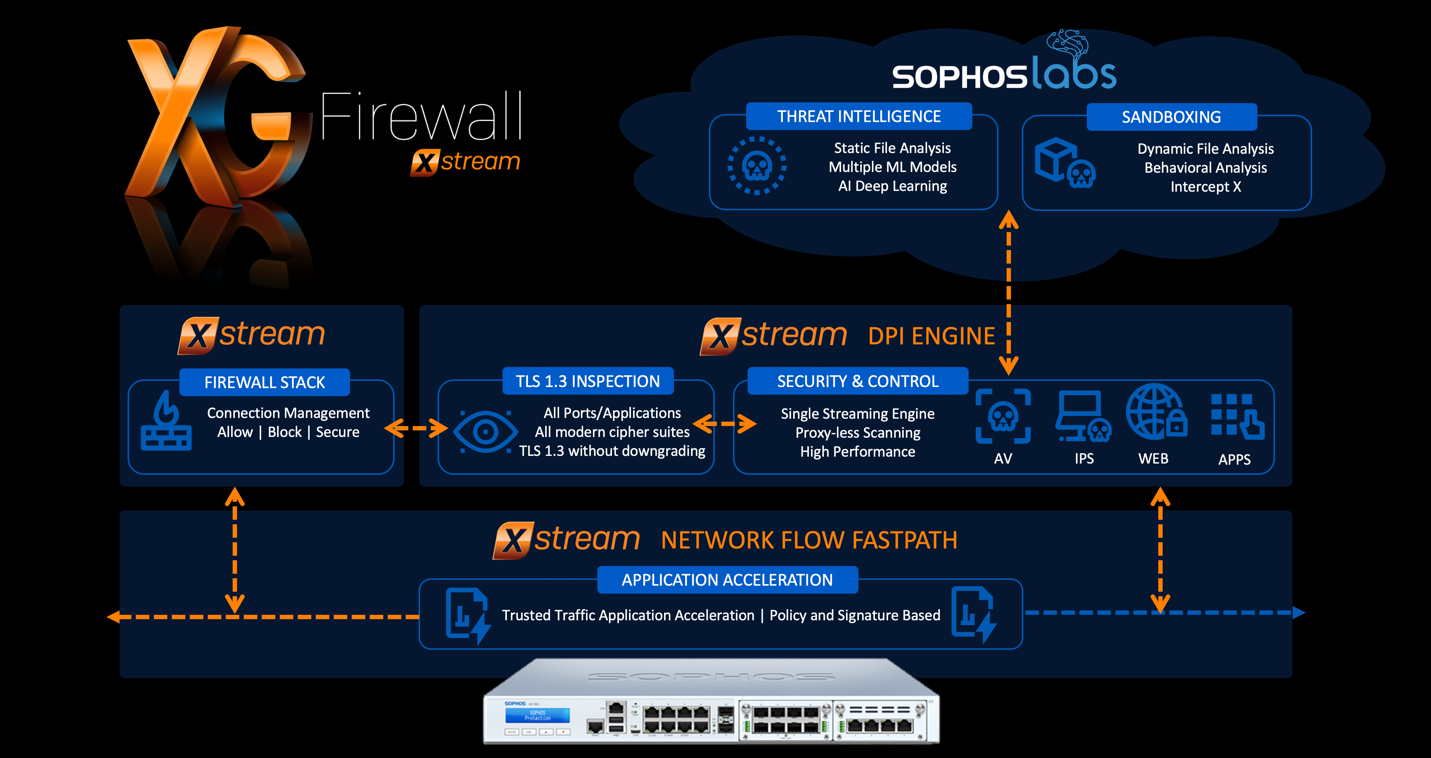
With most traffic flows transiting the firewall now encrypted, TLS inspection is absolutely critical to opening up this enormous blind spot to enable the firewall to do its job and inspect content coming into the network. As we will discuss in our next article in the series, the DPI engine can be extremely effective at identifying new zero-day variants of ransomware and other threats, but only if it’s able to inspect the traffic unencrypted.
How it works
Encrypted traffic flows destined to be examined by the new DPI engine are passed to the TLS inspection engine for decrypt before being inspected. After inspection, the flow is re-encrypted and sent on to its destination. If you’re interested in learning more about how TLS encryption and inspection works, and why it’s important, I suggest reviewing these two great assets on the topic:
The new Xstream TLS inspection engine in XG Firewall v18 offers a number of compelling benefits that make it the ideal solution for today’s modern encrypted internet:
- High performance –with high connection capacity
- Unmatched visibility into encrypted traffic flows and surfacing errors
- Easy tools to deal with errors and handle exceptions with just a few clicks
- Support for TLS 1.3 without downgrading
- Support for all modern cipher suites with robust certificate validation
- Inspection of all traffic, being application and port agnostic
- Powerful and flexible policy tools, enabling the perfect balance of performance, privacy, and protection
Getting started with TLS inspection
As we mentioned in the last article, taking advantage of the new TLS inspection engine in XG Firewall v18 is super easy. It essentially requires checking one box in your firewall to activate it and then creating a rule on the new SSL/TLS Inspection Rules tab as shown below.
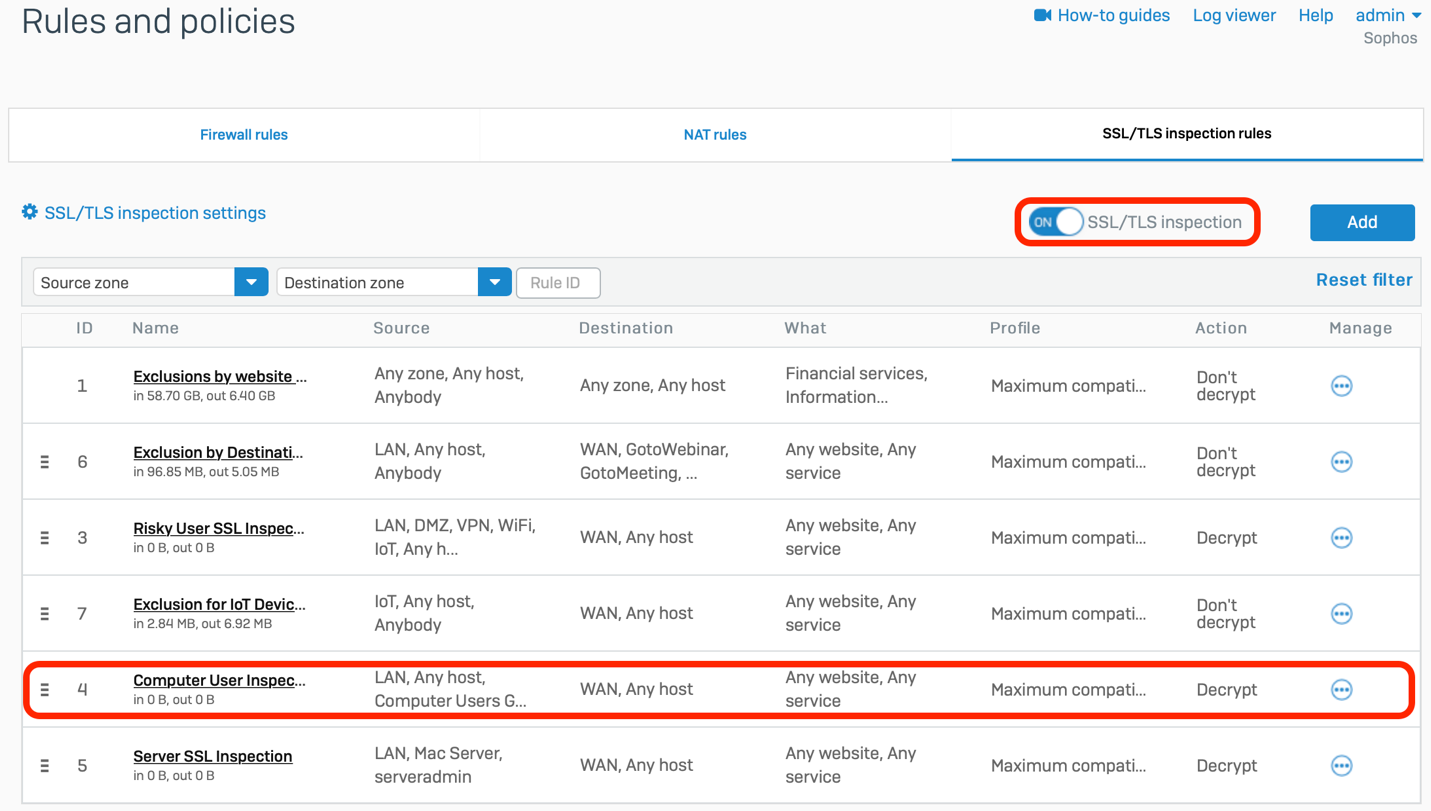
For a quick five-minute overview of how to create your own SSL/TLS inspection rules, watch this short how-to video:
For a detailed explanation and step by step guide for creating SSL/TLS inspection rules and decryption profiles, check out the online documentation:
- SSL/TLS inspection rules
- Decryption profiles
- SSL/TLS inspection settings
- Deploying the SSL CA certificate
It is recommended that you start gradually with TLS encryption, with a limited sub-estate of your network or a few test systems. This will allow you to build your expertise with the new TLS inspection solution and explore the new rules, logging, reporting, and error-handling options.
Not all applications and servers fully and properly support TLS inspection, so watch the Control Center for errors and take advantage of the convenient built-in tools to exclude problematic sites or services. Your XG Firewall comes with two pre-packaged TLS inspection rules out of the box that make exclusions easy. By default, they exclude trusted domains known to be incompatible with TLS decryption such as iCloud, some Microsoft domains, and others. You can easily customize these rules directly through the widget on the Control Center as issues arise, or through updating those exclusion rules directly.
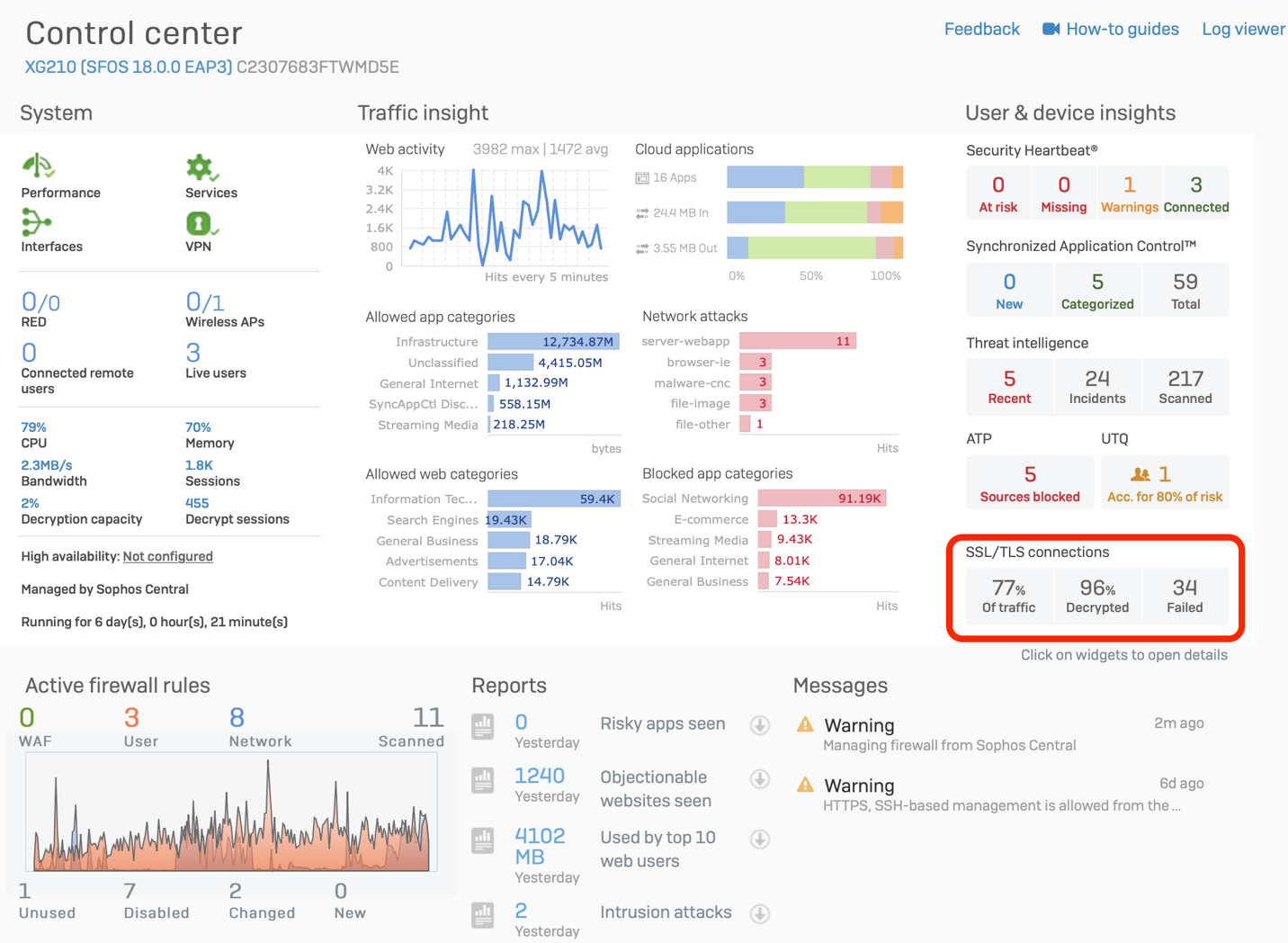
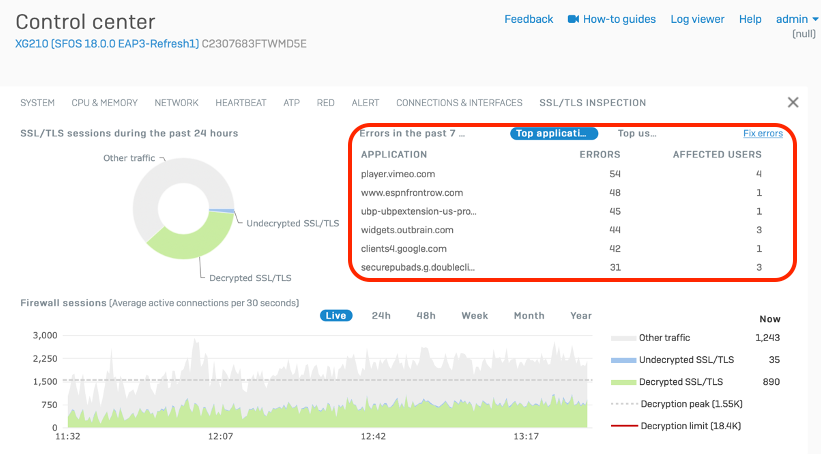
Once you’re comfortable with the DPI engine and TLS inspection, we recommend applying it more broadly across your network. When you’re ready for broader TLS inspection and wish to push the CA certificate out to more systems, we recommend using the wizard built into the Microsoft Active Directory Group Policy Management tools to make this task quick and easy.
As you roll out TLS inspection more broadly, carefully monitor your firewall system performance metrics to ensure your hardware is not a bottleneck. While the Xstream architecture in XG Firewall v18 offers tremendous performance gains for TLS inspection, going from inspecting 0% of encrypted traffic to 80-90% of your TLS traffic may have an impact on performance depending on your firewall’s normal load.
If your firewall could benefit from some extra headroom, consider a hardware refresh to a current higher-capacity model. You definitely don’t want to risk NOT inspecting TLS traffic given the rate at which hackers and attackers are utilizing this enormous blind spot to their advantage.

Here’s a summary of the resources available to help you make the most of the new features in XG Firewall v18, including Xstream TLS inspection:
