One cybersecurity catchphrase you’ll hear these days is that “X is the new ransomware”.
That’s because the ransomware scene is no longer clearly dominated by long-running, well-known “brand names” (so to speak) such as CryptoLocker, TeslaCrypt or Locky.
In other words, many people are convinced that ransomware has had its day, is dying out, and new threats are taking over.
A popular value for the variable X in the equation above is cryptojacking, where crooks sneakily insinuate cryptocurrency mining software onto your computer or into your browser.
Rather than snatching away your files, like ransomware does, cryptojackers steal your processing power and your electricity instead.
This means that the crooks earn a tiny bit of money from every victim for as long as they’re infected, rather that taking the all-or-nothing approach of ransomware, where victims face a stark choice: pay and win, or refuse and lose.
The thing is, neither cryptojacking, nor indeed any other cyberthreat, is the “new ransomware”.
If you must know, RANSOMWARE is the new ransomware.
As often happens in the world of cybercrime, old threats stay with us for ages, and new threats simply add themselves to the mix rather than taking over. (Do you seriously think that we’ll ever see the end of spam, for example?)
This year, we’ve seen a carefully orchestrated ransomware campaign known as SamSam, where the crooks have settled on a new mode of operation.
Instead of blasting out one copy of the malware out to thousands of potential victims over a day or two, the crooks blast thousands of copies of the malware onto computers inside a single organisation, pretty much all at once…
…and then, almost casually, they offer a “volume discount” to fix the entire company in one fell swoop.
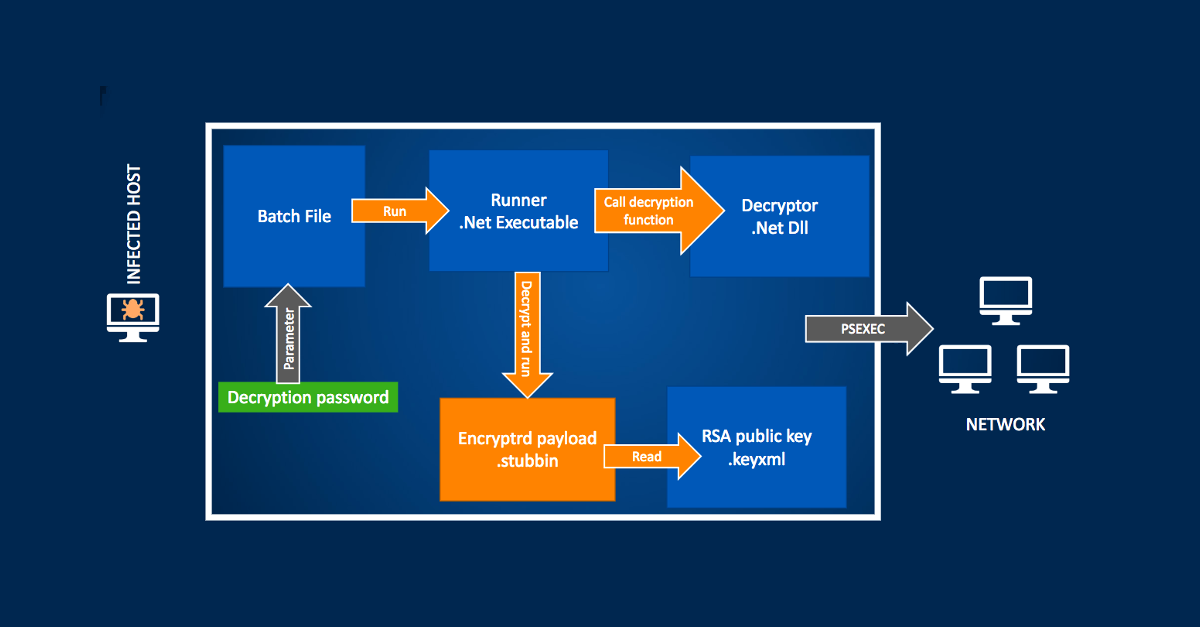
SophosLabs just published an intriguing technical paper about the SamSam menace, and in the sample discussed in the paper, the malware includes a BAT file that lets the crooks set their price point for each attack:
@echo off
SET runner=mswinupdate.exe
SET password=%1
SET path=xxxxxxxxxx
SET totalprice=5
SET priceperhost=0.8
The prices above are denominated in BTC (Bitcoin), with BTC0.8 being the cost to decrypt an individual computer, and BTC5 being the price of a “master key” to decrypt as many as you want.
The Bitcoin prices seem to be adjusted, based on the BTC-to-US$ exchange rate at the time of the attack, so that the all-you-can-eat discount price works out at about $45,000 each time.
At the equivalent of $7,200 per PC, but “just” $45,000 to decrypt your whole company, it’s almost as though the criminals are doing you a favour!
We don’t know why the price is $45,000. For all we know, that number was picked because it’s below certain reporting thresholds, or because the crooks want to pick the highest value they dare without getting into corporate board-level approval territory. All we can say is that $45,000 is a lot of money.
Learn more about this new trend in ransomware by reading the paper now. (No registration required.)

Bryan
(Do you seriously think that we’ll ever see the end of spam, for example?)
Bill Gates recently built a program to permanently block 100% of spam with no false positives. All I had to do was forward the email to 20 people within ten minutes.
I should see my check from Microsoft any day now.
Bryan
Wow. Manual distribution. It’s the closest thing I’ve heard of to malware developers performing actual *work* to “earn” their money.
PS: typo in “thousads of copies of the malware”
Paul Ducklin
Sadly, a lot of the “manual” distribution work can be automated, of course. (For example, if you’ve managed to wangle yourself a domain admin login via a forgotten RDP portal with poor security, and you’ve mapped out a list of writable C$ shares across the network, you can just feed that list into a script to infect all of them pretty much in parallel.)
Oh, I fixed the spello – thanks!
Randall Mueller
just a few things i found, intalls turbomailer, downloads ps.exe, executed wintaskini.exe via powershell, brute forced local user in domain admin account. Used tsclient, but crashed a few times and left behind .dmp files from it..
they encrypted even “system” owned files, that I as an Admin on domain, and local admnistrator box have no acces to make changes. or they changed the owner on folders. They even encrypted winapp folder and apps, and interestingly, adobe reader folder had owner as system and the decrypter had no rights .. i so far have not found the .bat files, but our eset was catching the early process on machines where a powershell scrypt was being run via the now owned domain admin user, they then shut down the server and stopped local eset from blocking on each machine..
havnen’t has yet figured out how they got in.. found a resting place on a skype server, but it had been updated for eternal bule, but not meltdown (due to so many issues seen).. I just want what tool they use to have access to machines that even our “lansweeper” is blocked from accessing..
Paul Ducklin
Remember that if you are investigating because of a ransomware event (very noticeable!), any malware leftovers you find afterwards might very well relate to other attacks – either the same crooks along their journey to a big SamSam demand, or other crooks who were there earlier, on the grounds that if there’s a hole in the fence, who knows how many people knew about it?
We do sometimes find evidence of multiple attacks when helping people dig deeply into what caused a ransomware incident – it’s hard to be sure, unless you are willing to spend plenty of time doing a full-on forensic-type analysis, what left-behind detritus cane from which attackers, and when.
Having said that, it sounds as you are doing the right thing and trying to find as many holes as possible you can now close, based on the fact that where cybercrooks are concerned, lightning really can strike the same place twice. Some people just pay the ransom (or restore a backup), delete the infection and carry on without considering, “What really happened?”