Thanks to Fraser Howard, principal threat researcher with SophosLabs, for the research this article is based on.
Researchers have discovered a new remote-access Trojan (RAT) called Kedi, which can snoop on infected systems, steal data and evade security scanners. It was attached to a spear phishing campaign when it was first discovered last week.
The attacks appear to be targeted rather than widespread and Kedi certainly behaves as most RATs do. But it has more flexibility than most in how it communicates with its command-and-control (C2) center. Among other things, it can use Gmail to receive instructions and transmit data.
The spear-phishing hook
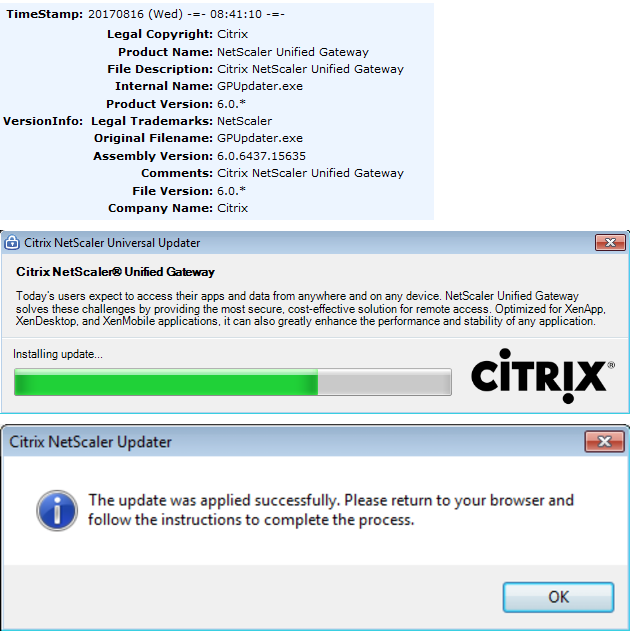
The payload is a 32-bit Mono/.Net Windows executable, written in C#. It masquerades as a Citrix utility, both in its resources (properties) and the splash screen displayed on startup:
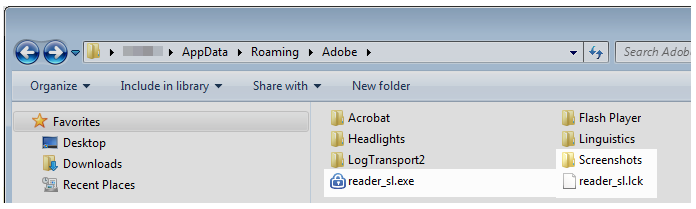
The payload installs itself into the %Appdata% within an Adobe folder. At that point, it’s masquerading as an Adobe file. The payload is accompanied by a lock file (.lck) and a folder into which it will presumably save screenshots.
Depending on its configuration, a registry startup hook might be added, making it look like this:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run “Adobe Updates” = c:\Users\<username>\AppData\Roaming\Adobe\reader_sl.exe
It creates an identifier for the infected endpoint using the MD5 of the machine name, and stores it in the Registry (as binary data):
HKCU\Software\Microsoft\Windows\CurrentVersion\Themes\DefaultVisualStyle “HR” = <md5 of machine name>
Features
The RAT has all the features a researcher would expect to find, including:
- AntiVM/anti-sandbox capabilities
- The ability to extract and run embedded secondary payloads
- File download/upload backdoors
- Screenshot grabbing
- Keyloggers
- The ability to extract usernames, computer names, and domains
Most of these features are command-driven.
Encrypt/decrypt process
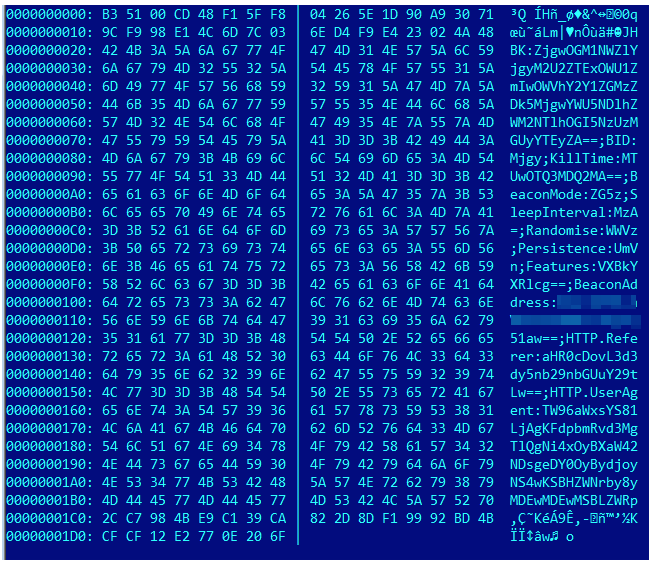
To get things started when first run on a machine, the RAT contains some default configuration data.
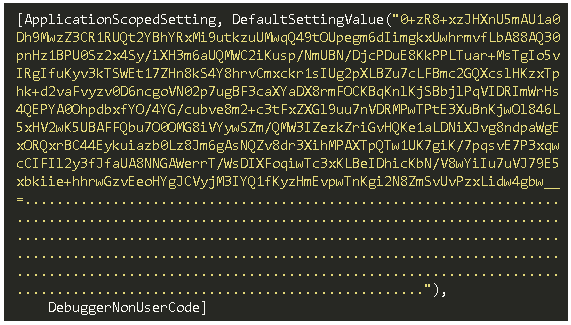
After trimming and base64 decoding, the data appears to be encrypted:
Code analysis reveals that the RAT protects its configuration data with a simple xor-based encryption loop. It contains an embedded PDF, the SHA256 of which is used as the key string in the decryption loop:
Gmail to command-control
Central to pretty much all RATs is their ability to call home and transfer data between attacker and victim. Kedi is a particularly interesting case because it can do this using Gmail – specifically, the Basic HTML version. It can also talk to its C2 using DNS and HTTPS.
Using Gmail to receive instructions from its C2, Kedi navigates to the inbox, finds the last unread message, grabs content from message body and parses commands from this content. To send information back to command and control, base64 encodes the message data, replies to the received message, adds encoded message data and sends its message.
It’s interesting to see how attackers keep trying to be more inventive in their approach to call home and make it harder for the good guys to detect and block its activity, Howard said.
Defensive measures
As noted above, this does not look like a widespread attack. But that’s cold comfort if you’re the one who’s targeted. For any type of malware, we recommend the following:
- Keep your operating system and applications patched, because the crooks try the easy ways in first.
- Keep anti-virus active and up-to-date, because the crooks update their tricks all the time.
Since this looks like a case of spear phishing, the best way to avoid the trap is to:
- Be careful what you click. If you click through from an email to a website that wants any personal information, don’t fill it in. Go to the website yourself by typing the address in your browser. If you receive links in emails that come from a someone you don’t know, don’t click.
- Check the address bar for the correct URL. The address bar in your web browser uses a URL to find the website you are looking for. The web address usually starts with either HTTP or HTTPS, followed by the domain name. The real websites of banks and many others use a secure connection that encrypts web traffic, called TLS (Transport Layer Security) or HTTPS (Hyper Text Transfer Protocol Secure). If you are expecting a secure HTTPS website for your bank, for example, make sure you see a URL beginning with https://before entering your private information. That said, it’s not hard to get an TLS certificate – so check the full URL of the website you’re visiting and check it’s not a fake URL using, say, a digit 1 in place of the letter L.
- Read Don’t fall for phishing and spear-phishing.

Anonymous
I am confused why there is a picture of a degu instead of a rat
Paul Ducklin
The reason is…
…errr (thinks on his feet)…
…the reason is that it’s a play on words and DEGU stands for Download, Execute and Grab Utility, like RAT means Remote Access Trojan.
(I made that up. I wondered myself why the “rat” in the picture was so small. Now I know :-)
Steve
Great reply! Thanks for that, I needed a good laugh just now. :)
Anonymous
I was wondering if that would be pedantic to point that out but glad I wasn’t the only one to notice!