 In our series on the current state of ransomware, we previously looked at CryptoWall and TorrentLocker. In this post, we’ll examine a variant called CTB-Locker.
In our series on the current state of ransomware, we previously looked at CryptoWall and TorrentLocker. In this post, we’ll examine a variant called CTB-Locker.
CTB-Locker is a ransomware variant that encrypts files on a victim’s hard disk before demanding a ransom be paid to decrypt the files.
CTB-Locker is noteworthy for its high infection rates, use of Elliptic Curve Cryptography, Tor and bitcoins, and its multi-lingual capabilities.
Infection Vectors
The authors of CTB-Locker are using an affiliate program to drive infections by outsourcing the infection process to a network of affiliates or partners in exchange for a cut of the profits.
The affiliate model is a tried, tested and very successful strategy at achieving large volumes of malware infections. It has been used to generate huge revenues for fake antivirus, click fraud schemes, and a wide variety of other types of malware. It is now being used to distribute ransomware in general and CTB-Locker in particular.
The affiliate scheme for CTB-Locker was first publicly highlighted by the researcher Kafeine, in mid-2014. A 2015 Reddit post claims to be from an actual participant of the affiliate program and provides interesting insight into its workings.
The CTB-Locker authors use a similar strategy to many exploit kit authors by offering a hosted option where the operator pays a monthly fee and the authors host all the code. This makes becoming an affiliate simple and relatively risk-free. The Reddit poster claimed to make 15,000 (presumably dollars) a month, with costs of around 7,000. The author also mentions that he only focuses on victims from “tier 1” countries such as the US, UK, Australia and Canada, as he makes so little money from other regions that it is not worth the time.
Using an affiliate model for distribution means that there are a wide range of different infection vectors for CTB-Locker. We have seen it be distributed through several exploit kits including Rig and Nuclear. However, it is through malicious spam campaigns that the majority of CTB-Locker infections have been observed.
The most commonly seen spam campaigns that distribute CTB-Locker use a downloader component known as Dalexis or Elenoocka. The spam messages themselves follow a wide variety of formats, including missed fax messages, financial statements, overdue invoices, account suspensions and missed mms messages. Here are several examples:
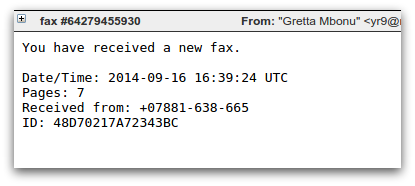
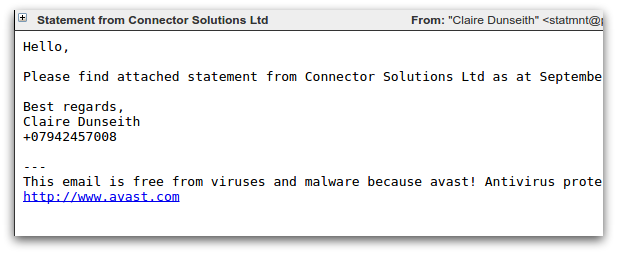
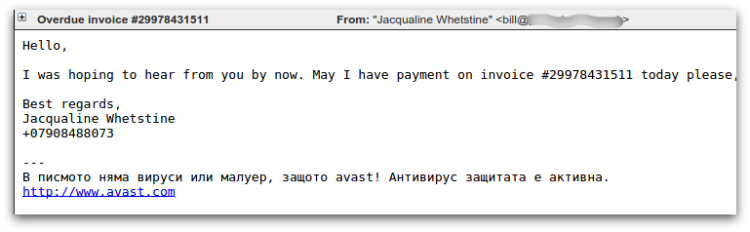
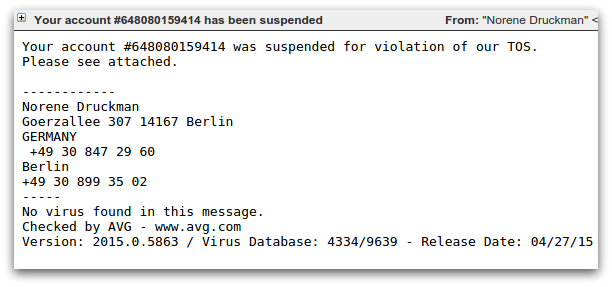
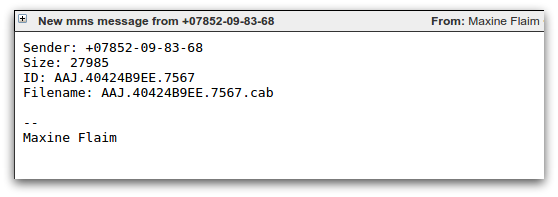
A large proportion of modern day malicious spam arrives as an exe file inside a zip or rar archive. An unusual aspect of Dalexis is that it almost always arrives in a less common archive, typically a cab file.
The archive contains the malicious sample itself, often with a .scr extension and a further archive that contains a decoy document that will be displayed to convince the victim that the attachment was harmless.
The malicious Dalexis sample uses several techniques in an attempt to avoid sandboxes and automated analysis systems, including sleeping for a period of time. Dalexis then downloads the CTB-Locker sample over HTTP in an encrypted form, decodes and executes it.
Execution
When CTB-Locker executes, it drops a copy of itself to the temp directory and creates a scheduled task to enable reboot persistence.
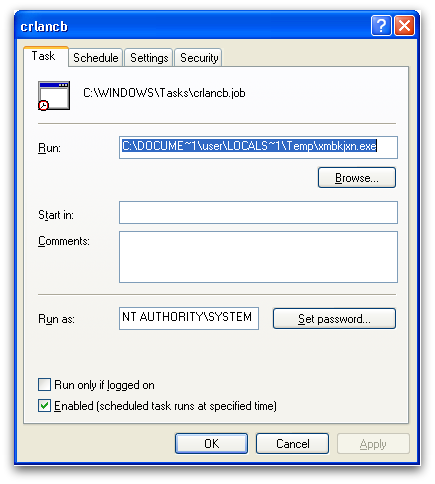
The file system is then iterated through and all files with extensions that match CTB-Locker’s extension list will be encrypted. The desktop background image is changed and CTB-Locker overlays the ransom message and a clickable interface onto the center of the screen.
Unlike some crypto-ransomware variants, CTB-Locker does not require an active internet connection before it starts encrypting files.
Encryption
CTB-Locker stands for “Curve-Tor-Bitcoin-Locker.” The “Curve” part of the name is taken from its use of Elliptic Curve Cryptography (ECC). ECC is a form of public key cryptography based on elliptic curves over finite fields. Its strength is derived from the elliptic curve discrete logarithm problem. Most file-encrypting Ransomware that uses public key cryptography tends to use RSA, which is based on prime factorization. A benefit that ECC has over RSA is that equivalent security levels can be achieved with much smaller key sizes. For example, a 256-bit ECC key has equivalent security to a 3072-bit RSA key.
The key size advantages that ECC offers may have been a contributing factor in the author’s decision-making process, as they embed a public key into the malware sample and a smaller key takes up less space.
CTB-Locker uses a combination of symmetric and asymmetric encryption to scramble files. The encryption itself is carried out using AES and then the means to decrypt the files are encrypted with the ECC public key. This ensures that only the CTB-Locker authors who have the corresponding private key are able to decrypt the files. For a detailed analysis of the encryption scheme used by CTB-Locker see, this analysis from “zairon.”
CTB-Locker will encrypt files with the following extensions:
pwm,kwm,txt,cer,crt,der,pem,doc,cpp,c,php,js,cs,pas,bas,pl,py,docx,rtf,docm,xls,xlsx,safe,
groups,xlk,xlsb,xlsm,mdb,mdf,dbf,sql,md,dd,dds,jpe,jpg,jpeg,cr2,raw,rw2,rwl,dwg,dxf,dxg,psd,3fr,accdb,
ai,arw,bay,blend,cdr,crw,dcr,dng,eps,erf,indd,kdc,mef,mrw,nef,nrw,odb,odm,odp,ods,odt,orf,p12,p7b,p7c,
pdd,pdf,pef,pfx,ppt,pptm,pptx,pst,ptx,r3d,raf,srf,srw,wb2,vsd,wpd,wps,7z,zip,rar,dbx,gdb,bsdr,bsdu,
bdcr,bdcu,bpdr,bpdu,ims,bds,bdd,bdp,gsf,gsd,iss,arp,rik,gdb,fdb,abu,config,rgx
This list has been expanded as newer variants have been released.
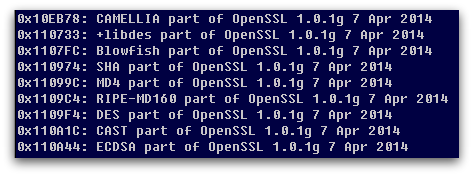
Originally, encrypted files all had a “.ctbl” extension, however, that was soon changed to have a random extension. It appears that the authors have borrowed at least some of their encryption code from OpenSSL, as large amounts of related strings can be found in the unpacked code.
Network Communication
Since CTB-Locker can start encrypting files without having to contact a command and control server, there does not need to be any network communication until the victim attempts to decrypt their files.
When this happens, all communications are carried out over Tor (this is where the “Tor” from Curve-Tor-Bitcoin-Locker comes in), usually through proxy websites that act as relays to the Tor Hidden Service that hosts the back-end infrastructure.
When a victim has paid the ransom, CTB-Locker will contact the command and control server, sending a block of data that contains the information needed to derive the key that will decrypt the victim’s files. This block of data can only be decrypted with the master key stored on the server.
Ransom Demand
When all the victim’s files have been encrypted, the ransom message is displayed by changing the desktop background and by overlaying the centre of the screen with the main ransom demand and clickable interface.
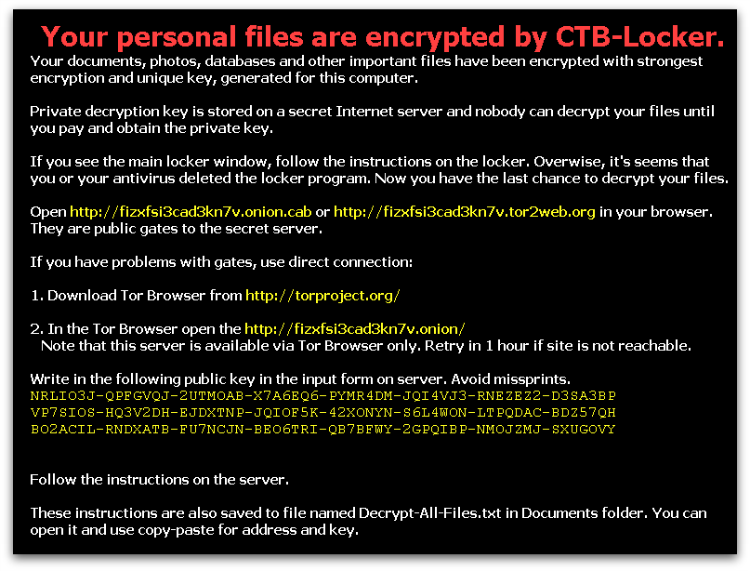
This screen informs the victim that “Your personal files are encrypted by CTB-Locker,” they are told that they have “96 hours to submit payment,” and they are warned that any attempt to remove the malware from the infected system will result in the decryption key being destroyed – this time limit was lower in earlier versions. The victim can click the “Next” button to start the decryption process or the “View” button to see the list of encrypted files.
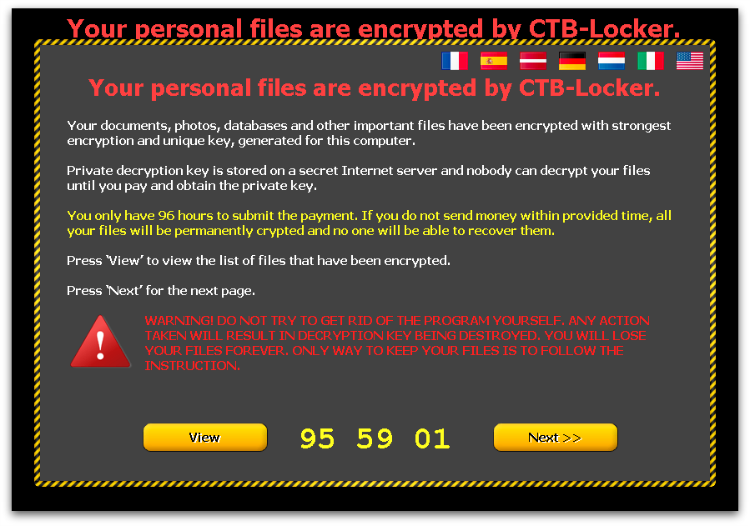
CTB-Locker is highly multi-lingual with the ransom note offered in a variety of languages, accessible through the various flag icons at the top of the screen. The choice of languages appears to be at least partially customizable by the affiliate who has purchased this particular CTB-Locker instance, and the available options have grown over time. A recent sample had the following language options – English, French, German, Spanish, Latvian, Dutch and Italian.
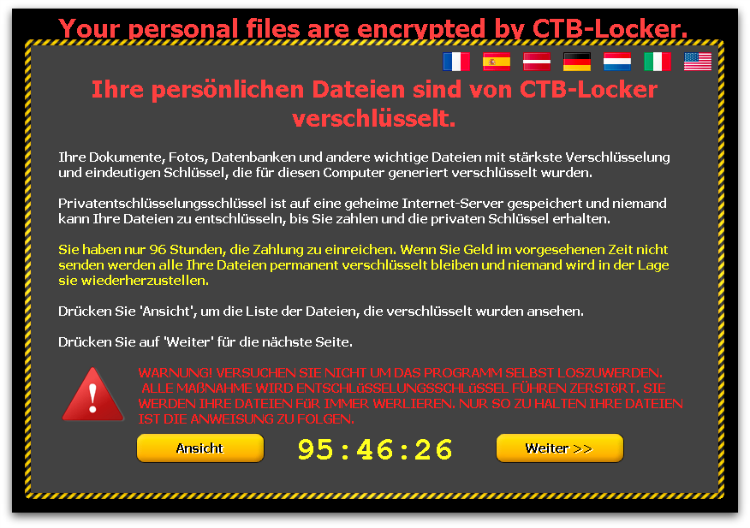
Latvian is an unusual language option, as Latvia is not generally seen as a major target for ransomware and other types of crimeware. This possibly represents the authors looking to break into new markets where awareness is lower, or perhaps the particular affiliate has local knowledge and is better able to launch a successful campaign in that country.

Recent variants of CTB-Locker also offer a way for the victim to verify that their files can be decrypted by unscrambling five randomly selected files for free. This appears to have been introduced as a way to gain the confidence of the victim and increase the likelihood that the full ransom will be paid.
Ransom Payment
When the victim clicks through the ransom interface they are given detailed instructions on how much to pay and how to pay it.
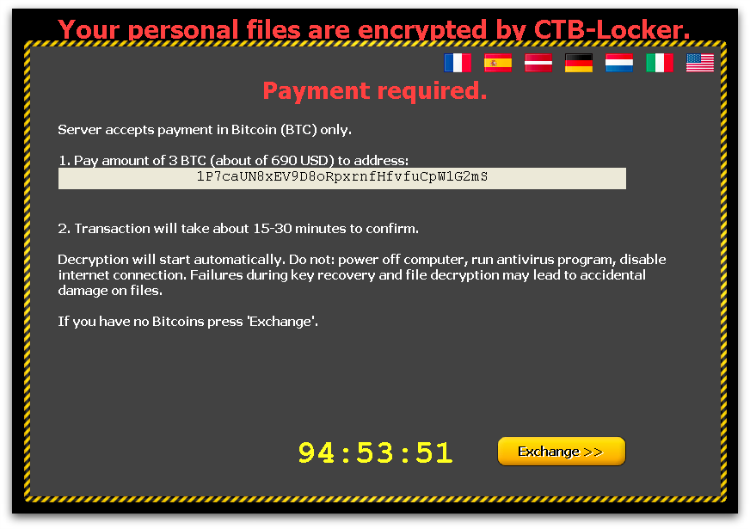
CTB-Locker requires Bitcoins (BTC) to pay the ransom (“Bitcoin” in Curve-Tor-Bitcoin-Locker). The exact amount of BTC is set by the affiliate who has purchased CTB-Locker, though the authors give guidance to help set the ransom amount at a level that is likely to generate maximum revenue. Figure 12 above shows an example demanding 3 BTC. An approximate equivalent amount in the local currency is also displayed – e.g., 690 Dollars or 660 Euros.
One downside to using Tor hidden services is that reliability can be an issue, meaning that the command and control server cannot be reached when the victim attempts to pay the ransom.
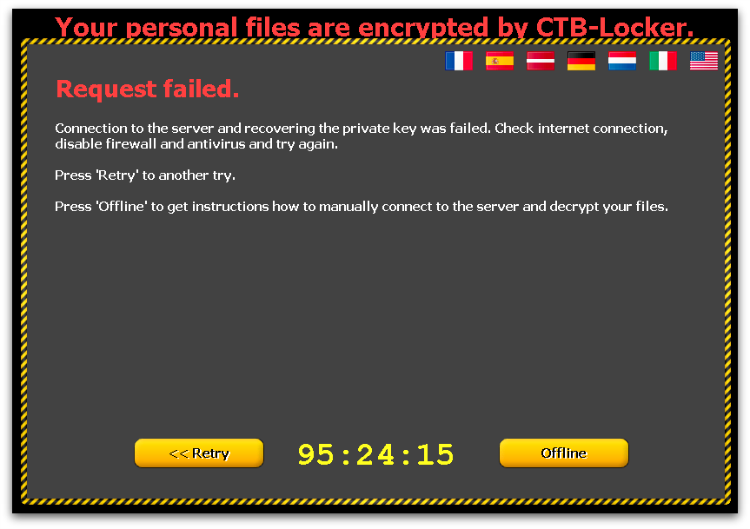
In an attempt to combat this, CTB-Locker attempts to use multiple different Tor proxy servers to reach the hidden service, and also offers manual instructions should the malware sample be removed from the infected machine. These involve visiting the Tor hidden service through a web browser and pasting into a form the public key that the victim is given.
Reliability
Reading through various public support forum postings suggests that in many cases paying the ransom will result in CTB-Locker decrypting the victim’s files. The “Test Decryption” feature is a good indicator that decryption is possible.
However, the victim must still trust that the cybercriminals will make good on their promise after handing over the ransom amount in BTC. There is also the possibility that the server components that host the private keys needed to perform decryption will be taken down, temporarily or permanently, which can make decryption impossible. In that circumstance it is likely that the cybercriminals will continue to accept ransom payments despite knowing there is no way to decrypt the victim’s files.
Statistics
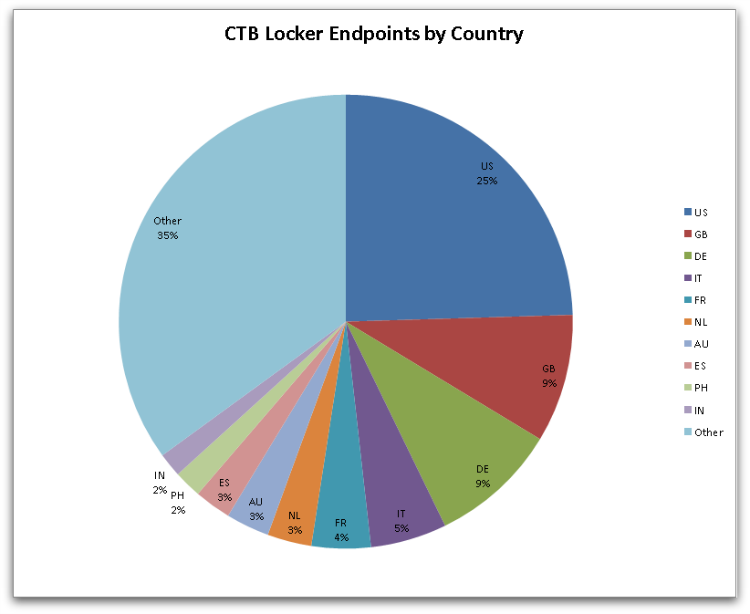
CTB-Locker infections are mostly seen in Western Europe, North America and Australia. These are generally speaking the tier 1 countries described in the Reddit post mentioned above. Victims in these countries appear to be targeted based on the ransomware author’s previous experience of successful payments.
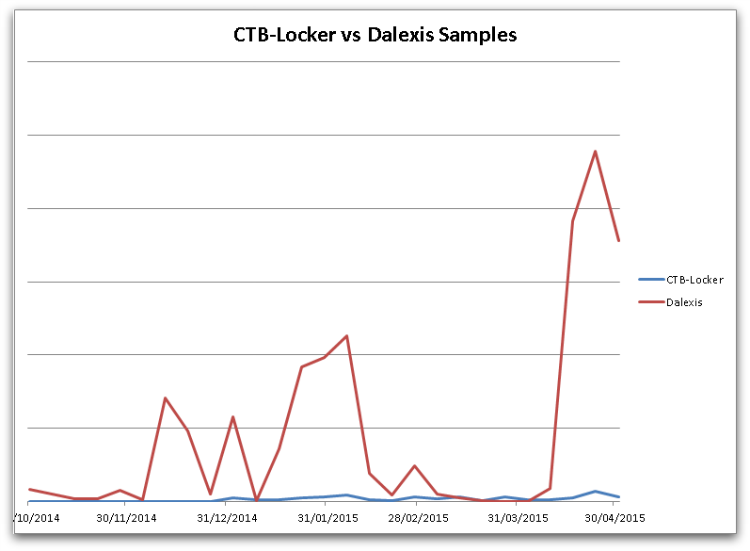
When looking at numbers of samples we can see that the number of actual CTB-Locker samples is much lower than the number of Dalexis samples that are used to download CTB-Locker. This makes sense since the downloader is spammed out in extremely large volumes, which allows security products to add detection very quickly. Making each sample unique by changing a small amount in each file increases the likelihood that some checksum-based protection solutions will fail to detect all of the samples.
Protection
Sophos protects against CTB-Locker at execution with HPmal/Ransom-N, and statically with an array of detection names including: Troj/Ransom-AKW, Troj/Onion-D, Troj/Filecode-B, Troj/HkMain-CT.
Sophos detects the Dalexis/Elenoocka downloader with an array of detection names including: Troj/Agent-AMTG, Troj/Agent-AMKP, Troj/Cabby-H, Troj/Agent-AIRO, Troj/Agent-AMNK, Troj/Agent-AMNP, Troj/Agent-AMOA, Mal/Cabby-B.
These HIPS signatures often don’t require any updates as they detect on the unpacked memory code irrespective of files on disk that are either packed, obfuscated or encrypted.
Having Sophos HIPS technology enabled is strongly recommended to block ransomware proactively.
If you suspect you’ve been compromised by ransomware, you can remove the malware using our Free Virus Removal Tool. Sadly, there’s not much you can do to get your files back except to pay the ransom – the encryption is too strong to crack.
Apart from having your antivirus up to date, there are additional system changes to help prevent or disarm ransomware infections that a user can apply.
1. Back up your files.
The best way to ensure you do not lose your files to ransomware is to back them up regularly. Storing your backup separately is also key – as discussed, some ransomware variants delete Windows shadow copies of files as a further tactic to prevent your recovery, so you need to store your backup offline.
2. Apply windows and other software updates regularly.
Keep your system and applications up to date. This gives you the best chance to avoid your system being exploited using drive-by download attacks and software (particularly Adobe Flash, Microsoft Silverlight, Web Browser, etc.) vulnerabilities which are known for installing ransomware.
3. Avoid clicking untrusted email links or opening unsolicited email attachments.
Most ransomware arrives via spam email either by clicking the links or as attachments. Having a good email anti-virus scanner would also proactively block compromised or malicious website links or binary attachments that lead to ransomware.
4. Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
We’ve seen many malicious documents that contain macros which can further download ransomware silently in the background.
5. Install a firewall, block Tor and I2P, and restrict to specific ports.
Preventing the malware from reaching its call-home server via the network can disarm an active ransomware variant. As such, blocking connections to I2P or Tor servers via a firewall is an effective measure.
6. Disable remote desktop connections.
Disable remote desktop connections if they are not required in your environment, so that malicious authors cannot access your machine remotely.
7. Block binaries running from %APPDATA% and %TEMP% paths.
Most of the ransomware files are dropped and executed from these locations, so blocking execution would prevent the ransomware from running.
Cihan
Does anyone decrypt his/her files infected by CTB-Locker ? However, extention of my files are “.vaegran” thanks in advance.
Anonymous
Use ShadowExplorer to recover your files. However, this will only work when windows systems-security is activated.
In my case, it worked on C-Drive, but not on my D-Drive.
Anonymous
I am a professional photographer. A few weeks ago my computer was attacked by CTB-LOCKER the one with the black screen and code KEY. Proven Data Recovery has been able to identify the VARIENT of the virus I have. It is – RSA-2048 CTB-Locker encryption virus.
They want 2,600 for the decryption of 300 image files that this virus has encrypted on a SD CARD. The computer still reads close to 900mb of data on the card and I have been told by multiple sources that there is a chance my images are still there, but I have had no luck and it’s going to take me quite some time to come up with this money so in mean time I am exploring other options and learning more about computers and code than I would otherwise have never cared to.
It angers me to no end that people can actually even do this. That they can hurt total strangers in this away. Hurt their jobs. Effect their lives just for the sake of doing so and then dangle our data in front of us so we freak out and jump. I refuse to pay this RANSOM and it is frustrating to no end that the supposed GOOD GUYS want WAY THE HELL MORE!! It’s very backwards to me and does not seem right. It is almost impossible to get a simple strait answer from people in this area and there is a lot of double talk and I have bad a couple people remote access my computer and I see them try things even I have tried.
The files that are blocked were never on my hard drive. I didn’t even have time to make a hard copy. One moment they were find and the next they were encrypted. I have done 2 system restored and a factory restore and computer has updated protection but the files remain locked on my card.
Is there any effective decryption for CTB-LOCKER – RSA-2048 CTB-Locker encryption virus
What are the odds? Is it even worth saving all this money for these people? He did ID the variant. Even that came as a shock. It’s all I have to go on. Maybe, if you think you have a solution for me of course I would be willing to work put pay arrangement but I would need to see at lest SOME proof. Maybe do one or two that I can see. There are 300 on the card and I am really quite desperate for this material, or to be told convincingly and enough times that all hop is lost. I am not at that point yet.
Thanks for your time
Sincerely
Scott
switch-case
I think its fair to assume that without obtaining the decryption key it is almost certain you will not see the material again.
TAPBACKGAMER
oof thats sad man 😭