SophosLabs researcher Gabor Szappanos is back with another installment in the ongoing saga of PlugX.
SophosLabs researcher Gabor Szappanos is back with another installment in the ongoing saga of PlugX.
As regular readers will remember, PlugX is the nickname of a large family of malicious software associated with Advanced Persistent Threats (APTs).
By metaphorical extension, PlugX also refers to the group behind the creation, evolution and worldwide dissemination of this malware.
We aren’t entirely sure exactly where the PlugX crew is based.
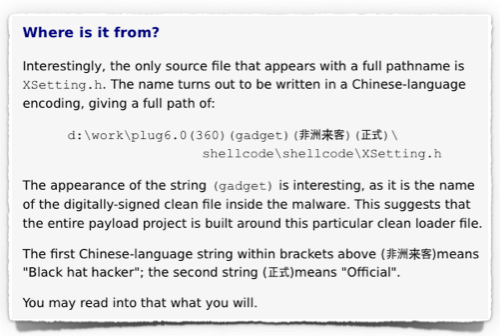
However, right back in back in May 2013, we made the following observation about what we then called “PlugX Version 6.0” (yes, malware samples have version numbers, too):
And we concluded, back then, by saying:
Sadly, perhaps, we were correct, and remain correct in 2015.
The PlugX team, whom we dubbed a “malware factory,” has kept at its task, and shows no signs of letting up.
Ironically, in a recent analytical article, Szappi concluded that many so-called APT actors aren’t actually that advanced.
At least, they don’t use advanced techniques to infect your computer in the first place, but that’s as much because they don’t need to as because they can’t.
→ Unfortunately, new exploits aren’t only bought and sold by reputable companies that use them to improve security, but are also available in the cyberunderground, ready to be used to violate security. APT attackers don’t actually need to know how to come up with exploits themselves. They need only know where to go shopping.
Why burn an brand new exploit when your target is still using an unpatched version of Microsoft Word from a year or more ago?
As Szappi wrote earlier this year:
The APT players lack deep skills of exploitation... If security researchers and system administrators follow and act upon vulnerability announcements, they are likely to be prepared for these groups.
Despite all this, one should never underestimate the malware authors mentioned in this report. They develop sophisticated Trojan families, and they manage to deploy them successfully to high profile organizations. The fact that they are not the masters of exploitation doesn't mean that they are any less dangerous.
But they are not omnipotent either. Understanding their limitations helps us to prepare our defences.
PlugX revisited
You can read more about their latest efforts in Szappi’s most recent paper, entitled PlugX goes to the registry (and India).
Of course, the APT threatsters aren’t only targeting Indian organisations, as a sample of Szappi’s latest decoy documents reveal.
“Decoys,” remember, are innocent documents – perhaps even interesting or important ones – that malware pops up on screen after it has infected your computer.
They serve as a distraction intended to convince you that the poisoned attachment or dodgy download you just opened really was what it claimed to be.
Szappi also looks at some of the technical evolutions in various APT malware families, such as storing malware code in the registry instead of on disk, and using new arrangements of shellcode to gain a foothold on a victim’s computer.
Shellcode is the name given to executable (binary) program code that is buried inside otherwise-innocent data files.
By booby-trapping those data files to trigger a known bug, attackers are often able to trick the operating system into running the data file as if it were a program, turning the shellcode from meaningless data into the start of a malware infection.
The verdict
Another fascinating insight into the persistence of the actors behind Advanced Persistent Threats.
TIPS FOR PROTECTION
What to do?
• Patch early, patch often!
Many APTs rely on vulnerabilities long after they’ve been patched, because the attackers know that their exploits work reliably on unpatched computers. They only need one weak link to get a foothold inside your organisation. Consider using patch assessment tools to look out for failed operating system and application updates.
• Watch that email!
Many APTs rely on believable-sounding but booby-trapped attachments that cover their tracks with realistic decoy documents that appear after you are infected. Consider being more restrictive about accepting documents, spreadsheets and so forth from untrusted sources.
• Turn on HIPS!
Many security products include an additional Host Intrusion Protection System layer that watches for, and blocks, suspicious behaviour, for example after opening a dangerous attachment or downloading risky software. Try it now if you haven’t looked into HIPS yet.