Looking for advice on how to remove Superfish? See our instructions here: How to get rid of the Lenovo “Superfish” adware.
 The controversy of the week is Superfish, which is the name of a marketing company that, amongst other things, produces software called Visual Discovery.
The controversy of the week is Superfish, which is the name of a marketing company that, amongst other things, produces software called Visual Discovery.
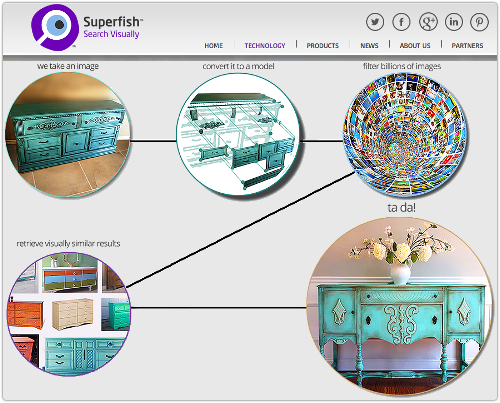
As far as we can tell, Superfish’s claim to fame is “visual search.”
That seems to involve analysing images that come your way, matching them against a giant database of images in the cloud, and putting in front of you a bunch of similar images.
For example, if you’re looking at an ad for a chest of drawers, Superfish, going by the example on its own website, can help you find a matching sideboard (credenza).
You may be able to guess where this is going.
If you install the Superfish software to monitor which websites you visit, and what’s in them, it can keep its eye out for related sites, all based on images instead of relying on old-fashioned keywords.
So, instead of selling clicks to potential advertisers based on the words you read, Superfish can sell clicks based on the images you see.
That sounds OK, assuming that you are aware that Visual Discovery was installed onto your computer, and assuming that the software keeps track of your browsing in a way that doesn’t put your online privacy and security at risk.
The Lenovo situation
Unfortunately, for many users of Lenovo computers, that wasn’t the case.
From October 2014 to December 2014, Lenovo shipped Superfish on a number of its consumer notebooks…
…and it turns out that the software does indeed represent a security risk.
That’s because Visual Discovery doesn’t just work inside your browser to see what you are looking at.
The product includes what’s known as a proxy: in other words, a component that intercepts network traffic outside your browser so it can keep track of what you are up to.
Visual Discovery is implemented as what’s called an LSP (Layered Service Provider) or a WFP (Windows Filtering Platform) filter, and plugs into the part of the operating system that deals with network traffic.
Pros and cons of filters
LSPs and WFPs aren’t inherently evil: in fact, many security products, including Sophos Anti-Virus, use filters as a way to watch out for the websites you’re visiting.
That means they can warn or block you if you try to go somewhere that is known to be dangerous, such as a website infected with malware.
The advantage of a filter over a browser plugin is that a filter’s processing applies to all software that connects through it, so you don’t need a separate plugin for every browser.
In theory, that means better coverage with less to go wrong.
The disadvantage of an filter is that it sees the content of network before it reaches your browser, so HTTPS (secure) web pages appear as a stream of encrypted data.
A browser plugin, however, sees the content after it has been unscrambled by the browser for display.
The Superfish approach
Instead of treating your HTTPS traffic as sacrosanct, and leaving it alone so it remains end-to-end encrypted all the way from the server to your browser, Superfish uses keybridging, also known as Man in The Middle, or MiTM.
The Superfish MiTM works pretty much as the name suggests.
When your browser connects to, say, https://example.com/, the connection is handled directly by Visual Discovery.
Your encrypted connection actually terminates inside Superfish’s filter.
The filter then connects onwards to https://example.com/ and grabs the content on your behalf (that’s why this sort of software is called a “proxy”), using an HTTPS connection of its own.
Of course, that means the HTTPS replies from example.com actually terminate inside the filter, too, so your traffic is unencrypted, both outbound and inbound, with the result that Superfish can read it.
Ironically, if the filter were to pass the now-already-unencrypted data on to your browser, your browser wouldn’t know what to do with it: you originally made an HTTPS connection, so your browser is expecting an encrypted stream.
To solve this problem, the filter re-encrypts the data, and passes it back to you. (This process involves decrypting with one key and re-encrypting with another, which is where the name keybridging comes from.)
Your browser thinks it made an end-to-end encrypted connection, and in a sense it did, except that the other end of the connection was not the example.com server – it was the Superfish filter on your own computer.
The certificate problem
At this point, you’re probably thinking, “But wouldn’t that sort of interception be obvious? Surely I’d see a warning?”
In theory, that’s exactly what ought to happen.
HTTPS traffic is signed by a digital certificate that identifies the company that owns the website you’re connecting to, and that certificate is signed, or vouched for, by a Certificate Authority, whose identity is pre-programmed into your browser as a “trusted advisor.”
For example, when you visit Naked Security (this is using Firefox on OS X 10.10), you see something like this:
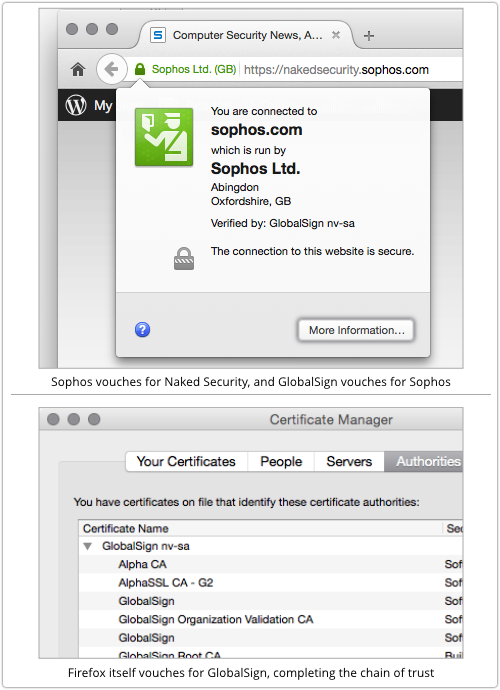
Naked Security’s certificate is owned by Sophos; Sophos’s right to represent itself as Naked Security is vouched for by GlobalSign; and GlobalSign’s right to vouch for Sophos is vouched for by Firefox.
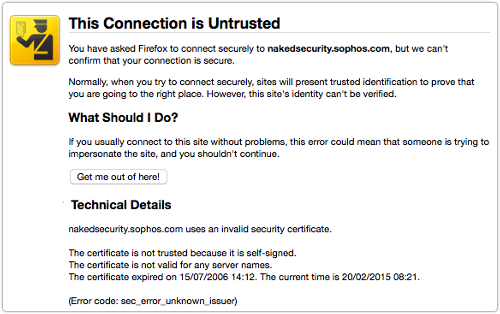
If you visit a site where the chain of trust in the certificate is not in good order, for example because you have been forced through a MiTM imposter, you’ll usually see a warning notice, perhaps like this:
The Superfish solution
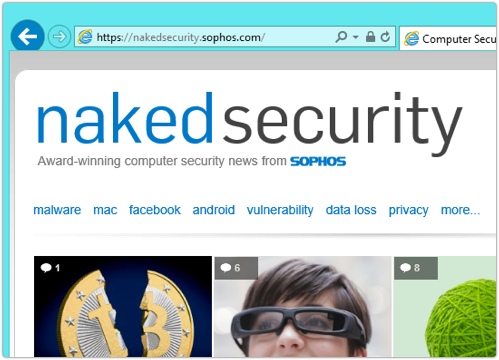
If you browse to Naked Security on a Windows computer with Superfish Visual Discovery installed, you don’t get a warning.
That probably makes you think that you have trustworthy end-to-end encryption with our site:
But if you click on the HTTPS padlock to dig into the certificate details (this is using IE 11 on Windows 8.1) will you see something very unusual:
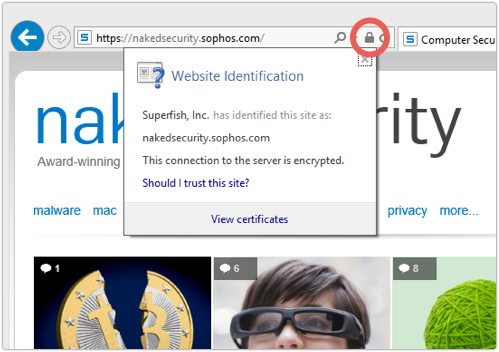
As we saw above, Sophos’s official Naked Security certificate is signed by GlobalSign, by explicit arrangement between the two companies.
So, who authorised Superfish to sign for Sophos as well?
Why didn’t a warning pop up?
The answer is that, at install time, the Superfish software vouches for itself to Windows by setting itself up as a trusted Certificate Authority.
Now it can create fake certificates for any site it likes, at any time, and then unilaterally sign those certificates to make them trusted, too:
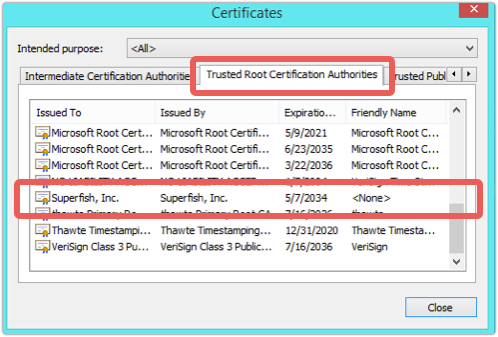
So all your traffic to and from Naked Security, or Outlook.com, or your bank, passes through Superfish’s MiTM layer, where it is temporarily decrypted and re-encrypted.
Granted, that content ends up decrypted inside your browser anyway, but having it unscrambled in more places than is strictly necessary is a needless risk.
And, of course, you have to trust Superfish not to do anything untoward with that decrypted data, either by accident or design.
On those grounds alone, we recommend that you uninstall the Superfish software if you find it on your computer:
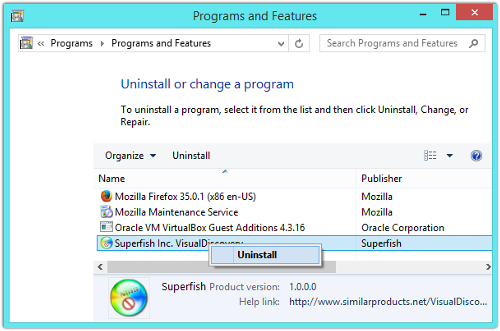
Lenovo obviously agrees, because it has stopped using Superfish, promised never to pre-install it again, and published its own removal instructions.
It gets worse
As you’ve probably already realised, for Superfish to present the fake Naked Security certificate you see above, it had to generate and sign that certificate automatically, in real time, when you first tried to visit our site.
(There’s obviously no way that Superfish could predict all the sites you might use, so it can’t have ready-made fake certificates installed in advance.)
In cryptographic terms, the software needs to carry around a copy of the Superfish private signing key, even though private keys are supposed to be kept private and secure.
And it does, as you will find if you dig around in the memory of the running Superfish software:
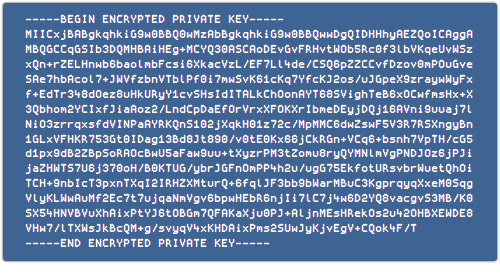
Fortunately, the private key is itself encrypted, or password protected.
Otherwise, any crook who dumped a copy of it would immediately be able to use it to sign his own fake certificates.
These would automatically be trusted on your computer, because Superfish registered itself with Windows as a Trusted Root Certification Authority.
Cracking the key
Sadly, for Superfish to use that private key itself in real time, the password needs to be stored somewhere.
And it is: it’s buried in the Visual Discovery software.
In fact, it’s the name of the company from which Superfish licensed the MiTM software module, all in lower case:
The text of the password appears unencrypted in memory when Visual Discovery is running, which is how various SSL security researchers recovered and verified it.
→ When you try to crack a cryptographic key, you usually start with a list of the most likely passwords, in what’s known as a dictionary attack. You can use a regular dictionary for a collection of everyday words, or a list that is obviously associated with the target you’re trying to crack, such as the in-memory text of the LSP process here.
Note that Superfish’s private key can be used for more than just signing HTTPS certificates.
It can also be used for code signing, which is where you vouch for a program (or even a device driver that runs inside the operating system itself) in the same way that HTTPS certificates vouch for websites.
That means the Superfish certificate could be abused by cybercrooks not only to trick you into trusting a fake website, but also to trick you into trusting any software that you download from it.
The bottom line
Superfish’s software represents a security risk.
You should look to see if it’s installed on your computer and remove it if it is there.
Go to Control Panel | Programs | Programs and Features.
Right click and choose Uninstall to get rid of it.
Then you should delete the Trusted Root Certification Authority certificate that it installed, so that no-one else can abuse it later on.
(For detailed removal advice, please see: How to get rid of the Lenovo “Superfish” adware.)
NB. Sophos products detect this software as a Potentially Unwanted Application (PUA) called SuperFish-A, of type Adware. If it is already installed on a Windows computer, Sophos Anti-Virus can get rid of it.