As you no doubt already know, because the story has been all over the news and social media recently, the widely-known and widely-used password manager LastPass last week reported a security breach.
The breach itself actually happened two weeks before that, the company said, and involved attackers getting into the system where LastPass keeps the source code of its software.
From there, LastPass reported, the attackers “took portions of source code and some proprietary LastPass technical information.”
We didn’t write this incident up last week, because there didn’t seem to be a lot that we could add to the LastPass incident report – the crooks rifled through their proprietary source code and intellectual property, but apparently didn’t get at any customer or employee data.
In other words, we saw this as a deeply embarrassing PR issue for LastPass itself, given that the whole purpose of the company’s own product is to help customers keep their online accounts to themselves, but not as an incident that directly put customers’ online accounts at risk.
However, over the past weekend we’ve had several worried enquiries from readers (and we’ve seen some misleading advice on social media), so we thought we’d look at the main questions that we’ve received so far.
After all, we regularly recommend our readers and podcast listeners to consider using a password manager, even though we’ve also written up numerous security blunders in password manager tools over the years.
So, we’ve put together six questions-and-answers below, to help you make an informed decision about the future of password managers in your own digital life.
Q1. What if my password manager gets hacked?
A1. That’s a perfectly reasonable question: if you put all your password eggs in one basket, doesn’t that basket become a single point of failure?
In fact, that’s a question we’ve been asked so often that we have a video specifically to answer it (click on the cog while playing to turn on subtitles or to speed up playback):
Q2. If I use LastPass, should I change all my passwords?
A2. If you want to change some or all of your passwords, we’re not going to talk you out of it.
(One handy thing about a password manager, as we explain in the video above, is that it’s much quicker, easier and safer to change passwords, because you’re not stuck with trying to concoct and remember dozens of new and complicated text strings in a hurry.)
By all accounts, however, this security incident has nothing to do with the crooks getting at any of your personal data, least of all your passwords, which aren’t stored on LastPass’s servers in a usable form anyway. (See Q5.)
This attack doesn’t appear to involve a vulnerability in or an exploit against the LastPass software by which crooks could attack the encrypted passwords in your password vault, or to involve malware that knows how to insinuate itself into the password decryption process on your own computers.
Furthermore, it doesn’t involve the theft of any personally identifiable “real life” customer information such as phone numbers, postcodes or individual ID numbers that might help attackers to persuade online services into resetting your passwords using social engineering tricks.
Therefore, we don’t think you need to change your passwords. (For what it’s worth, neither does LastPass.)
Q3. Should I give up on LastPass and switch to a competitor?
A3. That’s a question you will have to answer for yourself.
As we said above, as embarrassing as this incident is for LastPass, it seems that no personal data was breached and no password-related data (encrypted or otherwise) was stolen, only the company’s own source code and proprietary information.
Did you ditch Chrome when Google’s recent in-the-wild zero day exploit was announced? Or Apple products after the latest zero-day double play? Or Windows after any Patch Tuesday update in which zero-day bugs were fixed?
If not, then we’re assuming that you are willing to judge a company’s likely future cybersecurity trustworthiness by how it reacted last time a bug or a breach occured, especially if the company’s blunder didn’t directly and immediately put you at risk.
We suggest that you read the LastPass incident report and FAQ for yourself, and decide on that basis whether you are still inclined to trust the company.
Q4. Doesn’t stolen source code mean that hacks and exploits are bound to follow?
A4. That’s a reasonable question, and the answer isn’t straightforward.
Generally speaking, source code is much easier to read and understand than its compiled, “binary” equivalent, especially if it is well-commented and uses meaningful names for things like variables and functions inside the software.
As a somewhat synthetic but easy-to-follow example, compare the Lua source code on the left below with the compiled bytecode (like Java, Lua runs in a virtual machine) on the right:
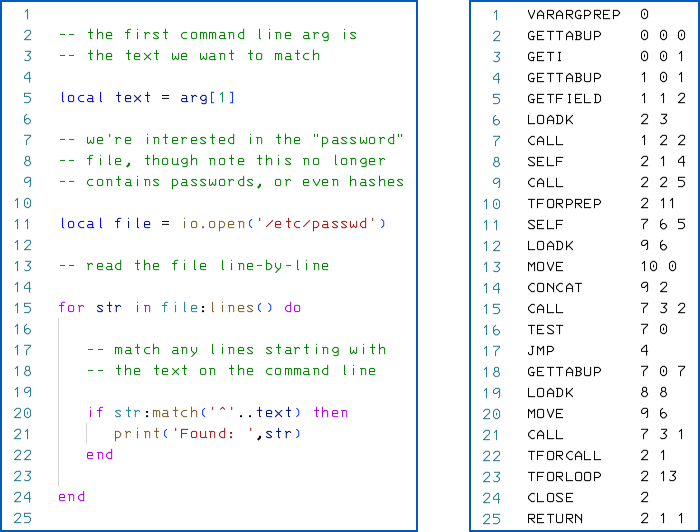
Right: Compiled Lua bytecode, as executed at runtime.
In theory, therefore, source code means it ought to be quicker and easier to determine exactly how the software works, including spotting any programming blunders or cybersecurity mistakes, and therefore vulnerabilities ought to be easier to find, and exploits quicker to devise.
In practice, it’s true that acquiring source code to go along with the compiled binaries you are trying to reverse engineer will rarely, if ever, make the job more difficult, and will often make it easier.
Having said that, you need to remember that Microsoft Windows is a closed-source operating system, and yet many, if not most, of the security holes fixed each month on Patch Tuesday were reverse engineered directly from precompiled binaries.
In other words, keeping your source code secret should never be considered to be a vital part of any cybersecurity process.
You also need to remember that many projects rely explicitly on making their source code public, not merely so that anyone can scrutinise it, but also so that anyone who wants can use it, modify it and contribute for the greater good of all.
Yet even mainstream open-source projects with liberal usage licences, and with potentially many eyes on that source code over many years, have required critical security patches for bugs that could have been spotted many times over, but weren’t.
Lastly, many proprietary software projects these days (examples include Google’s Chrome browser; Apple’s iOS operating system; the Sophos XG firewall; and thousands more widely-used hardware and software tools) nevertheless make extensive use of numerous open-source components.
Simply put, most contemporary closed-source projects include significant parts for which source code can be downloaded anyway (because licensing demands it), or can be inferred (because licensing requires its use to be documented, even if some modifications to the code were subsequently been made).
In other words, this source code leak may help potential attackers slightly, but almost certainly [a] not as much as you might at first think and [b] not to the point that new exploits will become possible that could never have been figured out without the source code.
Q5. Should I give up on password managers altogether?
A5. The argument here is that if even a company that prides itself on providing tools to lock up your personal and corporate secrets more securely can’t lock up its own intellectual property safely, surely that’s a warning that password managers are a “fool’s errand”?
After all, what if the crooks break in again, and next time it’s not the source code they get hold of, but every individual password stored by every individual user?
That’s a worry – you might almost call it a meme – that’s regularly seen on social media, especially after a breach of this sort: “What if the crooks had downloaded all my passwords? What was I thinking, sharing all my passwords anyway?”
Those would be genuine concerns if password managers worked by keeping exact copies of all your passwords on their own servers, where they could be extracted by attackers or demanded by law enforcement.
But no decent cloud-based password managers work that way.
Instead, what’s stored on their servers is an encrypted database, or “blob” (short for binary large object) that is only ever decrypted after being transferred to your device, and after you’ve provided your master password locally, perhaps with some sort of two-factor authentication involved to reduce the risk of local compromise.
No passwords in your password vault are ever stored in a directly usable form on the password manager’s servers, and your master password is ideally never stored at all, not even as a salted-and-stretched password hash.
In other words, a reliable password manager company doesn’t have to be trusted not to leak your passwords in the event of a hack of its databases, or to refuse to reveal them in the event of a warrant from law enforcement…
…because it couldn’t reveal them, even if wanted to, given that it doesn’t keep a record of your master password, or any other passwords, in any database from which it could extract them without your agreement and collaboration.
(The LastPass website has a description and a diagram – admittedly a rather basic one – of how your passwords are protected from server-side compromise by not being decrypted except on your own device, under your direct control.)
Q6. Remind me again – why use a password manager?
A6. Let’s summarise the benefits while we’re about it:
- A good password manager simplifies good password use for you. It turns the problem of choosing and remembering dozens, or perhaps even hundreds, of passwords into the problem of choosing one really strong password, optionally reinforced with 2FA. There’s no longer any need to cut corners by using “easy” or guessable passwords on any of your accounts, even ones that feel unimportant.
- A good password manager won’t let you use the same password twice. Remember that if crooks recover one of your passwords, perhaps due to a compromise at a single website you use, they will immediately try the same (or similar) passwords on all the other accounts they can think of. This can greatly magnify the damage done by what might otherwise have been a contained password compromise.
- A good password manager can choose and remember hundreds, even thousands, of long, pseudo-random, complex, completely different passwords. Indeed, it can do this just as easily as you can remember your own name. Even when you try really hard, it’s difficult to choose a truly random and unguessable password yourself, especially if you’re in a hurry, because there’s always a temptation to follow some sort of predictable pattern, e.g. left hand then right hand, consonant then vowel, top-middle-bottom row, or name of cat with -99 on the end.
- A good password manager won’t let you put the right password in the wrong site. Password managers don’t “recognise” websites just because they “look right” and have the correct-looking logos and background images on them. This helps to protect you from phishing, where you fail to notice that the URL isn’t quite right, and put your password (and even your 2FA code) into a bogus site instead.
Don’t jump to conclusions
So, there’s our advice on the issue.
We’re staying neutral about LastPass itself, and we’re not specifically recommending any password manager product or service out there, including LastPass, above or below any other.
But whatever decision you make about whether you’ll be better off or worse off by adopting a password manager…
…we’d like to ensure that you make it for well-informed reasons.
If you have any more questions, please ask in the comments below – we’ll do our best to answer promptly.

Jeff Puritz
I agree that PW Managers are worth the risk but IIRC this is the second time Last Pass has been breached and I honestly don’t recall any of the other PW Mgrs ever having been breached. So maybe there is more that Last Pass can do than just throw up their hands and claim “internet”?
Paul Ducklin
It will be interesting to see what followup comes from LastPass in this case. (It also makes me wonder, “How many other distributed development teams could fall foul of an outsider wandering into their Git-Fossil-CVS-Monotone-Mercurial-SVN-Darcs-Whateveritis source code control system?” With so much build and test automation these days, and “continuous everything” meaning there’s a real need to have instant-and-pre-authenticated access for lots of accounts, I suspect there might be lots of DevSecOps people right now wondering… have we gone too far trying to go far enough?)
I hope, as you do, that LastPass will soon enough publish a “how it happened, how we are going to stop it happening again, and how you can do the same to beef things up in your company” article.
The ability for crooks to get unauthorised access to source code is one thing… shareholders probably don’t like it (some cool trade secrets might get leaked), but it doesn’t usually mean instant danger to all customers. But unauthorised *modification* to source code is quite another problem, because that translates directly into “supply chain attack” in modern jargon.
If read-only source code access was possible by an attacker targeting a single incautious developer, one wonders how far away write access to said source code might have been? Once you’ve pulled off a supply chain attack via sneakily poisoned source code, you don’t need to hack any password or access codes. You can basically mint your own passwords for your own backdoors…
Hyua
This comment is interesting as it’s not really mentionned in the article : what if the attackers somehow managed to modify the source code, wouldn’t it become very risky to use Lastpass ? Moreover, it’s like a SaaS service, meaning we can’t just “not update” our software to prevent the “corrupted” source code from working against us
Paul Ducklin
That’s a question that you and I can’t really answer right now. In the absence of any public evidence showing clearly that there *was* a modification-type breach (e.g. the sudden appearance of suspicious code in binaries directly downloaded from LastPass), we have to accept LastPass’s claim that the source code was stolen, but not modified in situ as well.
(I am willing to assume for now that the words “took portions of source code” implies that this was what you might call a read-only attack.)
Let’s hope that the company quickly produces a report that confirms [a] that it has no evidence of malware or other unauthorised hacks inserted anywhere in the code and [b] why it has good reason to consider absence of evidence to be a strong indicator of evidence of absence.
Failing that, if the code *did* get changed after all, and LastPass can reliably enumerate the changes and roll them back, then we effectively end up in the same situation, with no malware out there (though there would be a lot of extra embarrassment for LastPass, and the additional cost of conducting further forensic research into the breach).
The ball is very much in LastPass’s court right now, but based on what they’ve said so far (for all that it’s very brief), I am assuming they are already fairly sure that the crooks got existing source code out but didn’t manage to sneak new code in.
If It turns out I am wrong then I will definitely update this article to let you know!
(Declaration of interest: I am not a LastPass user myself, so I don’t have any direct personal worries nagging me about this one :-)
Hyua
Paul,
Thank you very much for those insightful answers in the comments and interesting article.
Paul Ducklin
Thanks for your kind words. Glad you found the article and comments useful.
RAJENDRA G
Here the versioning system can be checked by the Lasspass team and if any code was modified and CVS can revert to any previous version of the source code. So it should be less of a worry about modified source code.
David
LastPass is one of the big if not the biggest fish. A real high value target. That other’s have not reported to have been breached may just be that it wasn’t nearly as news worthy. I would be dubious about others being immune.
James
Sophos Intercept X for Mobile includes a password manager. We’ll give you clearance to toot your horn about your own products in this case.
Paul Ducklin
Ha, I’ll let you mention it for me, thanks!
I didn’t mention it here because it’s a phone-only offering (it doesn’t work on desktops so it can’t form-fill laptop browser logins automatically, for example).
That makes it more of a phone password storage utility than a full-blown password manager. Indeed, we refer to it as a “Password Safe”, not as a “Password Manager”.
Having said that, it’s self-contained inasmuch as the password database isn’t held in the cloud unless you choose to copy it there or import it from there… it’s just a local, encrypted blob as described above, using the well-known format KDBX, as used by the open source password manager KeePass.
So it can interoperate with KeePass on, say, Windows, but we don’t have a Windows/Mac/Linux/Sophos Central password manager of our own.
Free for Androids and iDevices (see Google Play and App Store). As you say, a handy little utility baked into the Sophos Intercept X for Mobile security product… just search for that string.
Nigel
I would like to use the Sophos Password Safe on my Android phone, but it currently doesn’t support the latest KDBX v4.x file format, which is the default format used by KeePass v2.51.x.
Paul Ducklin
Thanks for the feedback. I’ll pass your comment to the developers…
mmmm
Does using 2FA with Password Manager lead to loosing access to your passwords if you loose your phone?
Paul Ducklin
That depends on what sort of 2FA system your password manager uses.
Most 2FA systems have a recovery process, for example a set of “backup codes” that you can print out and lock in a safe for emergencies, such as if you lose your phone.
Mrgigglenutz
Some 2FA can be on multiple devices so that you don’t need to rely on backup keys if the device is no longer available. I use Authy for 2FA and KeePass for my password manager. I went with Authy because it can be used in place of Google authenticate which has the same problem where it is only installed on one device. I don’t trust my passwords in a service like lastpass mainly because they are a huge target for hackers so I’d rather not put important data like that in the cloud. Instead I have many copies of my password file that are automatically synced and an offsite NAS I maintain as well as cold storage devices in a fireproof safe. Overkill but it works well and wasn’t hard to setup.
Dave C
The end goal of the attackers would be to create a saleable exploit kit that could successfully fake a valid client login to your blob on the server where lastpass stores it *and* to successfully decrypt your list of passwords.
Up until now, MITM attacks would have been pointless as without the proprietary algorithms used in the client app and the master password, the data transferred from the server to the client is meaningless.
But one of those clues may now be in reach, depending on what proprietary information was stolen. Any clue may help an attacker who has been working on this for some time, it might provide the breakthrough they are looking for. If you’re an important person with passwords to company servers, this is something that Lastpass will be keen to head off, and keep quiet about until they have changed the client end algorithm or whatever was in the “proprietary” code stolen.
Paul Ducklin
Let’s hope that LastPass has used well-documented and trusted crypto algorithms throughout, so that the source code reveals no
“home-made” solutions that might include unexpected security holes. The diagram of how the master key and password “blob” are encrypted (AES + PBKDF2 + SHA-256) suggests they are inclined not to knit their own.
Of course, the fact that open source software can’t contain “proprietary secrets” (or at least that if it does, anyone could in theory winkle them out if they wanted) is often given as an important benefit of open source.
Rob L
This isn’t the first security breach Lastpsss have had.
There have been many such incidents including the discovery of third party trackers in the Android app that could have allowed master passwords to be disclosed.
Only Lastpsss audits Lastpass’s code, and we have to take their word for it that it’s secure, as well as the hosting platform it’s on.
KeePassXC + Syncthing or similar seems like a good free and open source alternative.
Also the new Mooltipsass BLE authenticator. Open source and also does TOTP.
It is inexcusable that Lastpsss, a company dedicated to security solutions, should have to admit embarrassing security breaches. They of all people should know better. Your local florist or pizza shop gets compromised and suffers huge reputational damage and possibly fines and being thrown off their payment provider as a result. Lastpass: “Oh, well. We got sloppy, continue to be sloppy.” Sounds like they may have had a lucky escape. This time.
Paul Ducklin
To be fair, I suspect that if LastPass had suffered a data breach that exposed customer data or payment card info then they would have fallen foul of exactly the same regulatory processes as the florists or the pizza shops you allude to.
But, as you say, it’s your choice to decide whether this security incident is a step too far for you in continuing to trust them. (I don’t myself use LastPass so I don’t have to face that decision myself.)
As suggested in the article, however, the main point of this piece was not to rate LastPass or compare existing solutions… it was to ensure that people whose digital lives are probably now more secure through having adopted a password manager don’t go back to insecure password habits on the basis of misunderstandings about how a typical password manager works.
Notably, I’ve seen social media posts that invite people to assume that password managers can never be safe because they inevitably keep plaintext copies of all your passwords on their own servers somewhere (kind of like “hot wallets” are used to keep “live” cryptocoins online), where they might end up getting leeched in bulk.
Tony Gore
Good article on the issues. Nothing is ever safe. A password manager is really convenient – it generates more secure passwords than most people will, if they need to remember it. I hadn’t thought about the extra protection it provides against phishing sites. I have a few sites that I don’t ever store passwords for, because of the risk if they were compromised. Then it is a question of balancing the risk. I have to say though, that the holes I accidentally found in my banks security on a number of occasions, whilst not leading to the ability to directly access my account, were greater than using a password manager for most things. Ironically, the biggest failure I found was in a premium service supposed to protect personal information.
Someone who recently visited the US told me how shocked they were that when paying in a restaurant, they had to hand over their credit card and it was taken away to do the transaction, where it could easily have been cloned. So I wonder how many people accept this, which is a much higher risk than a password manager breach.
Paul Ducklin
When I worked at Sophos Australia, those little “folding wallets” in which waiters used to bring bills even had a special pocket at the top into which you could slide your credit card, which stuck out slightly to signal “I am ready to pay”. The waiter would then take the wallet and card back to a central till to process the transaction, after which you’d get your card back along with the slip, which you’d sign to authorise.
(Admittedly this is going back a few years. But Oz, like the US, was very late to the Chip-and-PIN party. It made me smile to see visitors from so-called developing economies, e.g. pretty much anywhere in Africa, freak out at being required, let alone permitted, to authorise their card payments with a scrawled signature, something they’d not been doing at home for years already on the grounds that it was clearly less secure. An intriguing reminder that “developed” countries aren’t always.)
Craig Dean
This is actually the 7th breach, and 6th in 8 years (see https://en.wikipedia.org/wiki/LastPass). It is more than enough for me to have decided to move to 1Password, which took no time at all.
What did take time was deleting my LastPass account. Firstly, I could not cancel the auto-renewal, whenever you clicked the button it just re-enabled the auto-renwal. Secondly, I couldn’t remove my payment information (credit card), finally the Delete Account functionality also did not work.
Calling the CSRs I was first told they couldn’t delete my account because they couldn’t verify me as the last 4-digits of my CC didn’t match. On a second call, they said the same thing until I pointed out I was sat in front of the computer and could see the digits on screen (based on their web page), then they said they couldn’t delete my account as CSRs I had to use the ‘broken’ web page.
Finally, I figured out that they’d added a “display:none” style to the form to hide it, and managed to delete it myself. [SENTENCE REDACTED].
I posted the workaround on Reddit for others to find (https://www.reddit.com/r/Lastpass/comments/x0ofll/workaround_lastpass_bug_preventing_you_deleting/)
s31064
One of the reasons I use KeePass is that it’s completely local. If somebody hacks into KeePass’s site (not that they probably bother since it’s all OSI certified OSS), nothing of mine is there. To put me at risk, they would have to hack into one of my devices, get past my master password/key, and then they’d have full reign over all of my passwords/accounts. Possible? Absolutely. Likely? Not really, and I’m pretty sure I’d be aware of it fairly quickly if it did happen. (At least I’d like to think so.)
Paul Ducklin
In a world of source code supply chain attacks, you can’t say that crooks would be uninterested in hacking an open source project’s web presence *simply because the source is already available*.
For example, poisoning KeePass’s official source code download distribution, even temporarily (hosted on Sourceforge, so it’s not their own site), would give attackers a way not only to inject unwanted code onto some users’ computers, but also to target the very people who consider themselves security conscious enough to rebuild their own versions from scratch every time.
You can argue that there’s a much better chance of spotting rogue modifications when you have the source to look at, yet plenty of open source projects have suffered from in-the-wild bugs that had been there for years where anyone could have seen them, but no one did.
As for running locally only, that’s my personal preference for password management too, so I get to chose which backup devices and servers I use to archive my encrypted password vault.
Having said that, I think you can run LastPass entirely offline, though (not a user myself) I suspect many if not most people choose it precisely so they don’t need to worry about the sort of security issues that you and I prefer to keep under our own control… horses, as they say, for courses.