Microsoft’s regular clutch of updates takes on the greatest importance this month as the company releases a fix for a critical-severity bug (currently being referred to by its vulnerability designation reference, CVE-2021-40444) that’s currently being exploited, in Microsoft Office documents, as well as significant patches for Microsoft products and cloud services. Microsoft’s patches also prevent four other critical bugs from being exploited: Two in Windows services; one in Azure Sphere; and one in an open source project Microsoft created for Linux called Open Management Infrastructure (OMI).
Update (2021-09-17): We’re now aware of active exploitation of the bugs affecting OMI (CVE-2021-38645, -38647, -38648, and -38649) following disclosure by the company Wiz, who originally discovered and reported the bugs to Microsoft, and now refer to the vulnerabilities collectively as OMIGOD. Any version of OMI below v. 1.6.8-1 is not only vulnerable, but are under active exploitation by automated attackers, allegedly from the Mirai botnet. If you run Linux virtual machines in Azure, or have installed any of the software listed in the additional guidance by Microsoft about this bug, we’ve included additional details below.
In addition to the regular Patch Tuesday updates, users of Apple iOS devices are now able to download a major firmware update that aims to mitigate a serious “zero click” vulnerability on iPhones and iPads that can be abused to load malware. There’s more coverage of this bug on Naked Security, and users of Sophos Mobile for iOS devices will receive a notification starting today urging them to patch their devices as soon as possible.
The update can take from 15 minutes to an hour to complete, so make sure you have a bit of time and a place to plug in your phone while updating.
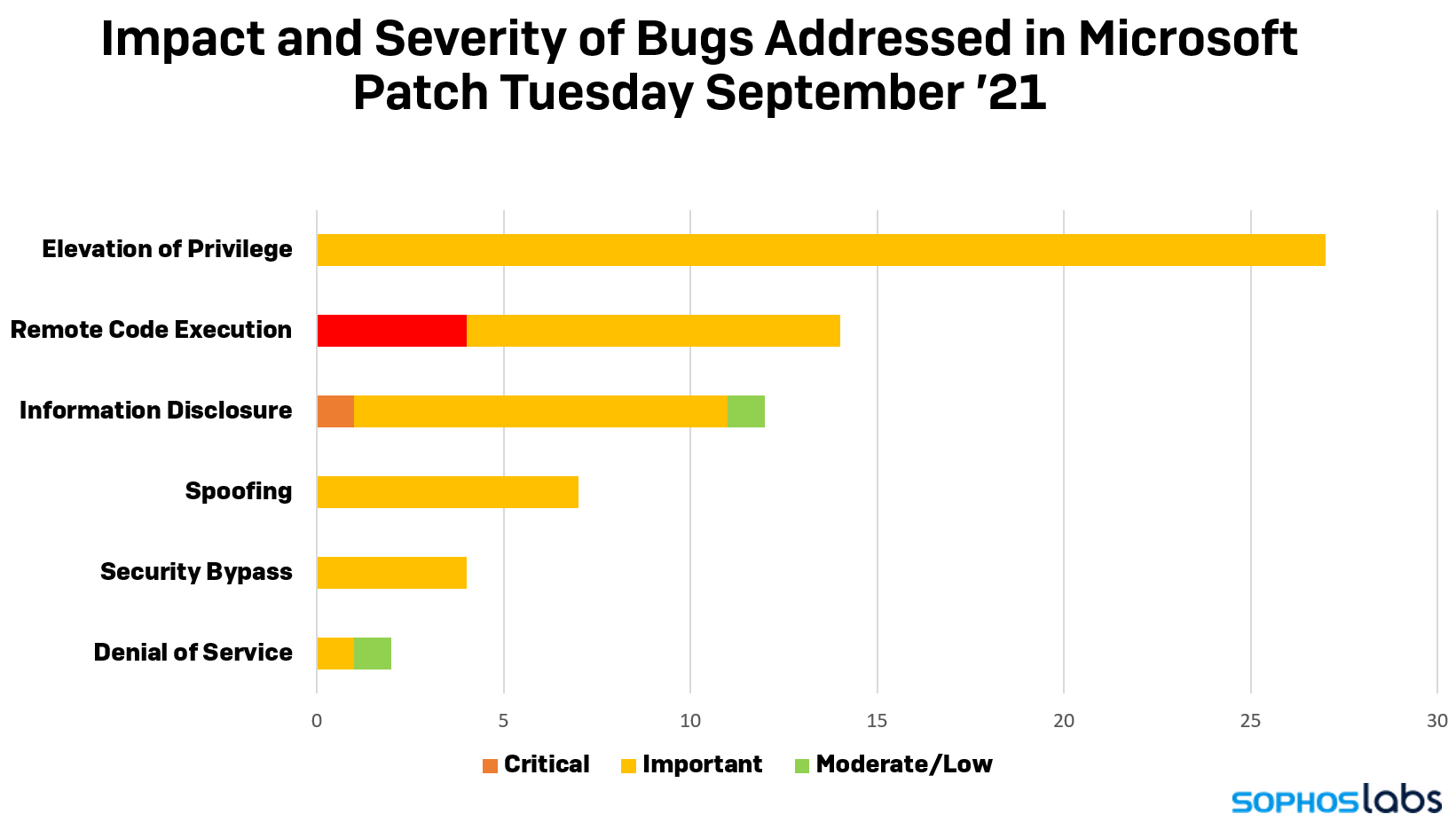
The company released a total of 67 fixes to Microsoft products. The largest number of fixes (27) were to repair problems that an attacker might use to raise their own privilege level on a computer, while the second largest number (14) address the ability of an attacker to execute arbitrary code on a victim’s computer.
All but one of the critical vulnerabilities fall into the Remote Code Execution category, including the -40444 bug, which was given the catchy nickname Microsoft MSHTML Remote Code Execution Vulnerability. As this bug is already being exploited, and as both criminals and security analysts appear to be experimenting with new exploits of the bug, the SophosLabs team has been working to coordinate protection across our products. We’ve detailed some of our findings below.
The non-RCE critical vulnerability is an information disclosure bug that affects Azure Sphere (CVE-2021-36956), a platform Microsoft created that is intended to add a security layer to Internet-of-Things (IoT) devices.
Microsoft also fixed bugs affecting its Edge browser on both the Android and iOS platforms. Users of that browser on those devices will, necessarily, have to obtain their fixed versions from the relevant app store for their device, both of which are subject to a vulnerability that Microsoft describes as “spoofing,” about which the company gave no further details.
The critical vulnerabilities affecting Windows itself (CVE-2021-36965 and CVE-2021-26435) apply to a component called the WLAN AutoConfig Service, which is part of the mechanism that Windows 10 uses to choose the wireless network a computer will connect to, and to the Windows Scripting Engine, respectively. The company provided no additional information prior to the Patch Tuesday release deadline about the mechanism by which these bugs execute code on a system.
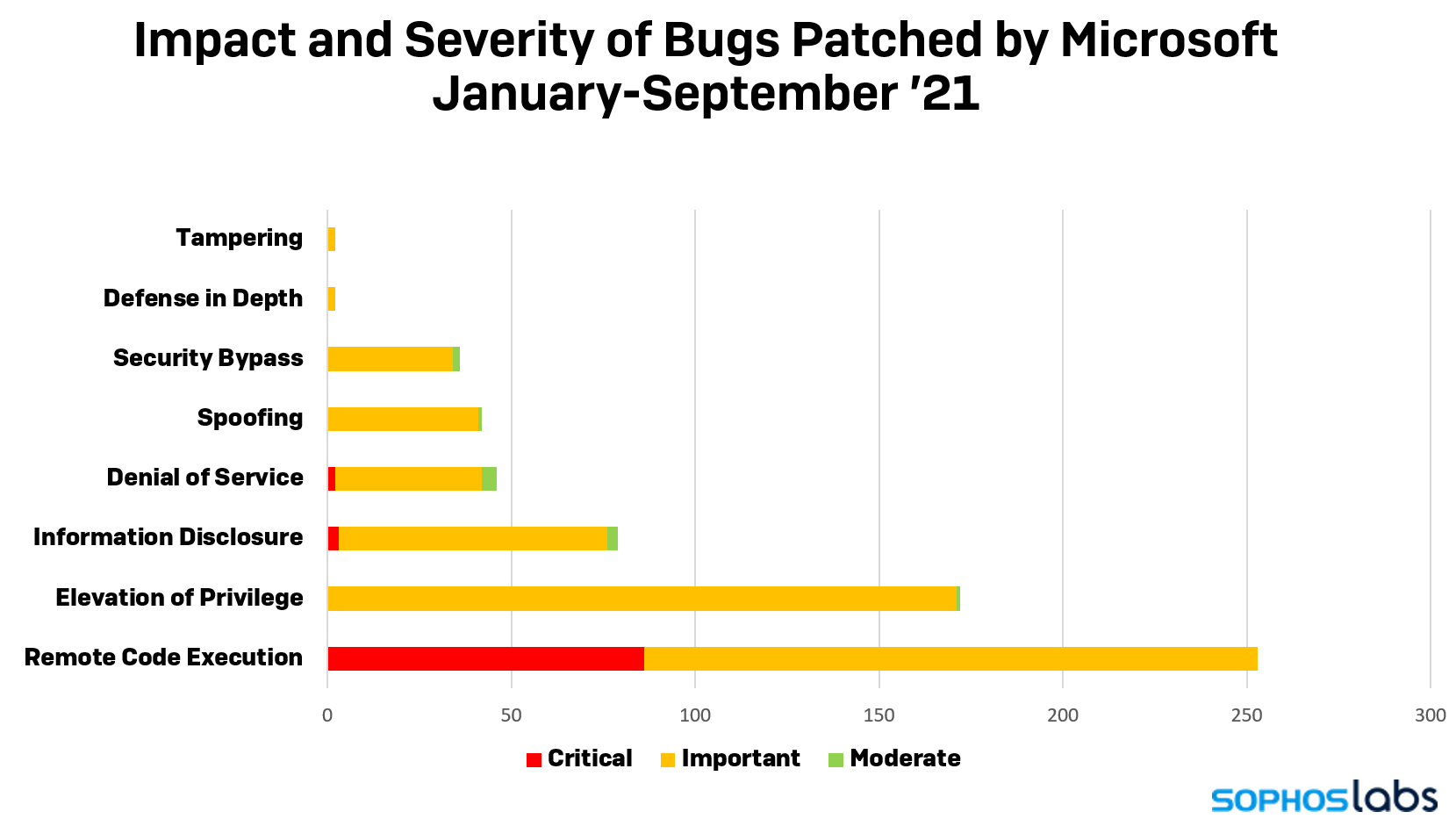
Windows users who may not be willing to wait for automatic updates to install themselves can manually download the appropriate cumulative update bundle for their CPU architecture from the Microsoft Update Catalog website. As of today, in calendar year 2021, Microsoft has issued patches to fix 632 vulnerabilities in their products.
This month’s bugs to watch
MSHTML RCE (CVE-2021-40444)
After this bug was discovered and became public knowledge on September 7, security researchers and analysts began swapping proof-of-concept examples of how an attacker might leverage the exploit. Unfortunately, the high profile of this bug means that attackers will have taken notice and are likely to (possible already have) begin exploiting the vulnerability.
The bug involves the MSHTML component of Microsoft Office, which (among other things) can render browser pages in the context of an Office document. In the exploitation of the bug, an attacker creates a maliciously-crafted ActiveX control, and then embeds code into an Office document that calls the ActiveX control when the document gets opened or previewed.
The stages of the attack are, in general terms:
- Target receives a .docx or .rtf Office document and opens it
- The document pulls down remote HTML from a malicious web address
- The malicious website delivers a .CAB archive to the target’s computer
- The exploit launches an executable from inside the .CAB (usually named with a .INF extension)
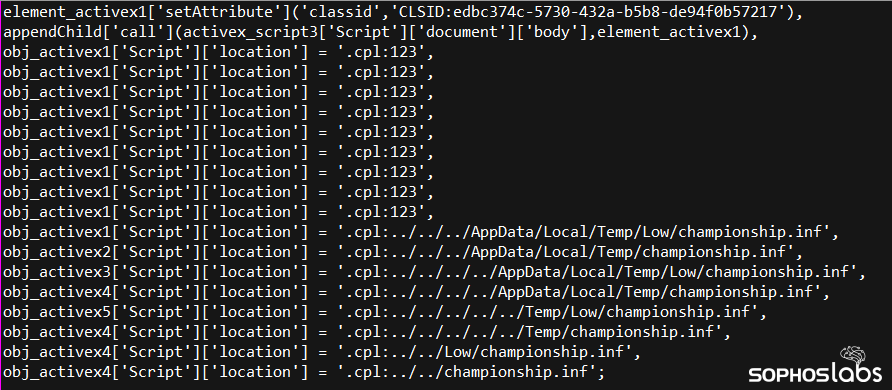
If it sounds confusingly complicated, it really is: The malicious scripting uses the built-in handler for .cpl files (Windows Control Panel) in order to run the file with an .inf extension (which is actually a malicious .dll) extracted from the .cab file.
Several people have not only crafted functional proof-of-concept (PoC) exploits, but a few have created and published “builder” tools that anyone can use to weaponize an Office document. The original version of the exploit used Microsoft Word .docx documents, but we’ve already spotted some versions that use .rtf file extensions.
We’ve also become aware of attackers using the techniques not only to launch .exe files, but also malicious .dll files, using rundll32. There’s no reason to believe the exploit won’t expand their range to other Office document types, as well.
We’ve summarized a list of the things network administrators can do to mitigate the problem that Microsoft published in their advisory about the bug, but the only true way to defeat this problem is to install the update that makes it go away, permanently. While Microsoft (like the rest of us) only heard about the bug a week ago, they’ve taken great pains to hurry this fix for the Patch Tuesday release.
In the meantime, given what we know about how the exploit looks on a targeted system, the Labs team has been hard at work developing new signatures to detect a range of known examples as well as behavioral detections that should help catch new variants that will likely emerge over time. These will also likely be updated as time goes on.
| Signature | What it detects |
|---|---|
| Exp/2140444-A | Malicious .docx with the exploit |
| Troj/JSExp-W | Remote HTML accessed by .docx |
| Troj/Cabinf-A | Malicious .cab archives loaded by HTML |
| Troj/Agent-BHRO & Troj/Agent-BHPO | Executable payloads inside a .cab |
| Troj/DocDl-AEEP | Malicious .docx files |
| Evade_26b | Exploit behavior |
Open Management Infrastructure (OMI)
CVE-2021-38645, CVE-2021-38647, CVE-2021-38648, and CVE-2021-38649
The OMI is an open-source version of Microsoft’s WMI designed to run on Linux systems. In the Azure cloud service, Microsoft automatically installs OMI when customers configure virtual machines for management tools, such as Azure Automated State Configuration or Azure Desired State Configuration. For on-premises VM or bare-metal installations, users can install OMI manually by adding the software from its Github repository, or by installing the SCOM extension. Three of the bugs permit privilege escalation, and the fourth allows attackers to perform unauthenticated remote code execution (RCE).
As of September 17, 2021, Microsoft have published additional guidance about mitigating these vulnerabilities, because the software may not update automatically in all cases, and there are already public PoCs and a botnet appears to be exploiting the bug in an automated fashion to install cryptocurrency miners on vulnerable VMs. New virtual machines created in Azure will no longer be vulnerable, but users will have to install updates to SCOM installations and other extensions manually. Microsoft also recommends that VM operators restrict access to the ports commonly used by OMI (1270/tcp, 5985/tcp, and 5986/tcp).

Windows Redirected Drive Buffering Subsystem (RDBSS)
CVE-2021-36969, CVE-2021-38635, CVE-2021-38636, CVE-2021-36973
This driver is present in all modern versions of Windows, and acts as a go-between for the filesystem and I/O processes that want to read from or write to the filesystem. Three of these four vulnerabilities can lead to an inadvertent disclosure of sensitive information, and the fourth may be an avenue to elevation of privileges.
Windows Common Log File System Driver
CVE-2021-36955, CVE-2021-36963, CVE-2021-38633
Windows uses the Common Log File System (CLFS) Driver to collect and manage Event Logs generated by a wide range of applications and system processes. The bugs affecting this component would permit an attacker, hypothetically, to elevate their privileges, giving themselves additional permissions to make changes to the targeted computer. As this driver exists on all currently-supported versions of Windows, it’s a particular area of concern. The company considers these bugs to be more easily exploitable, on average, though they haven’t seen evidence of such activity yet.
Detection guidance
In addition to the specific static and behavioral detections listed above, Sophos has released the following protections against newly-disclosed vulnerabilities:
| CVE | SAV |
|---|---|
| CVE-2021-36963 | Exp/2136963-A |
| CVE-2021-38633 | Exp/2138633-A |
| CVE-2021-39836 | Exp/2139836-A |
Sophos will update this table as needed with additional protection measures or signatures, if needed.
