Millions of “sextortion” spam messages sent between September 1, 2019 and January 31, 2020 generated nearly a half-million US dollars in profits for Internet criminals. The messages told recipients that their computers had been hacked, that the sender had captured video of them visiting pornographic websites, and threatened to share the video with the targets’ “friends” if they didn’t pay—asking for as much as $800 USD worth of Bitcoin (BTC) to be transferred to a wallet address.
The flow of that digital currency reveals that many of the operators behind these sextortion scams are connected to a much larger criminal digital economy. Though there were some smaller players involved in these spam campaigns, the movement of the BTC deposited in many of those wallets shows the campaigns were linked to other criminal enterprises—either funding other illicit activity or providing a way to convert the BTC to hard cash.

We shared wallet data extracted from these spam campaigns with CipherTrace, Inc., to get more insight into the flow of digital currency connected to them. The wallet addresses used by the scammers to extract payments from victims were found to have made transactions with dark web marketplaces, stolen credit card data hawkers, and other elements of the cybercriminal economy. Other funds were quickly moved through a series of wallet addresses to be consolidated, put through “mixers” in an attempt to launder the transactions, and converted to cash, goods and services through other channels.
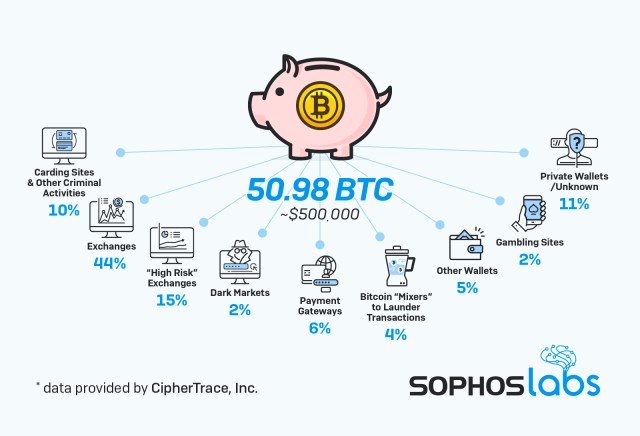
While the sextortion scams themselves were hardly innovative, the cryptocurrency flow wasn’t the only thing that suggested a certain sophistication behind some of the attackers. Many of the messages relied on a number of technically interesting obfuscation methods to try to slip by spam filters. And while the vast majority of recipients either never saw the messages or didn’t pay, enough saw and fell for the ploy that wallets associated with the messages pulled in 50.98 BTC during the five month period. That amounts to roughly $473,000, based on the average daily price at the times the payments were made, and an average of $3,100 a day.
It’s raining spam
Sextortion messages are a staple of low-level Internet scammers. They require relatively little technical skill to send, and do not require the actual compromise of the target’s computer. That is because the email addresses targeted by the scam and the passwords sent as proof to the victims are collected from published usernames and passwords from old website breaches, widely published on the Internet. (Using password managers, not re-using passwords across accounts, and using services such as HaveIBeenPwned.com or Google’s Password Checkup can protect people from the use of old passwords by attackers.)
Compared to sophisticated ransomware campaigns (which can bring in millions of US dollars worth of cryptocurrency from a single victim), the return from sextortion scams is relatively small. But they are still a significant source of income for the spammers behind them, and cost relatively little to run. They also provide a steady stream of income for the botnet operators whose networks of compromised computers act as the launchpad for these campaigns.
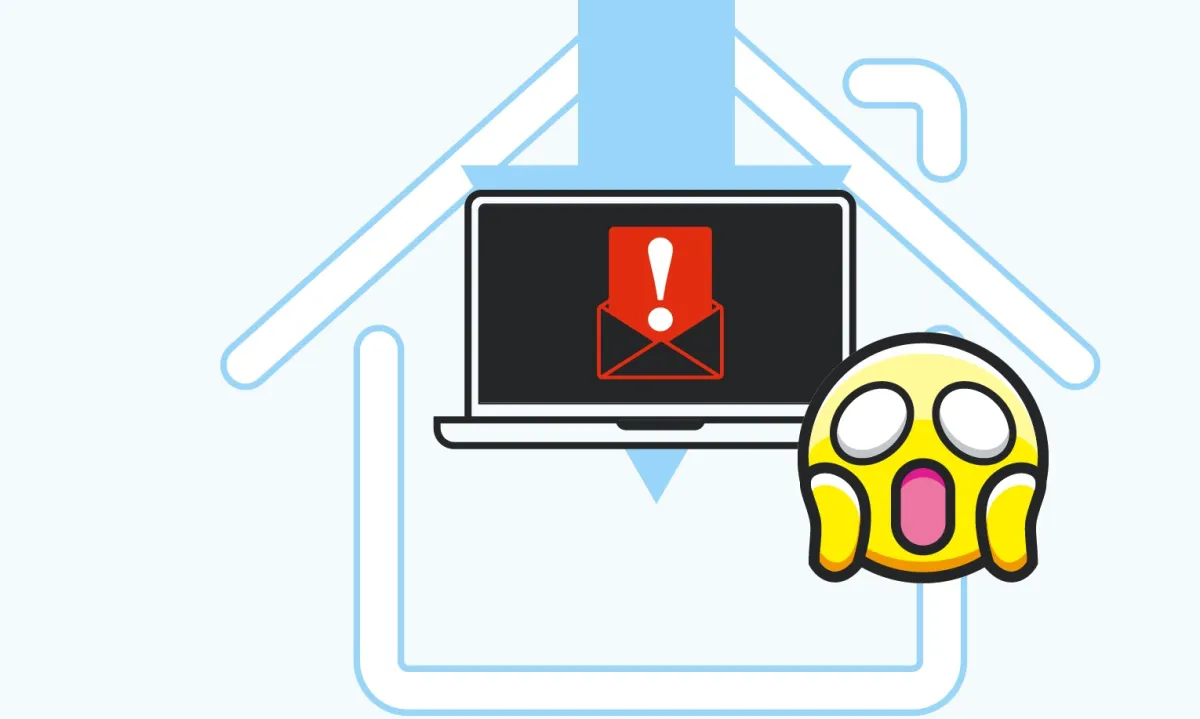
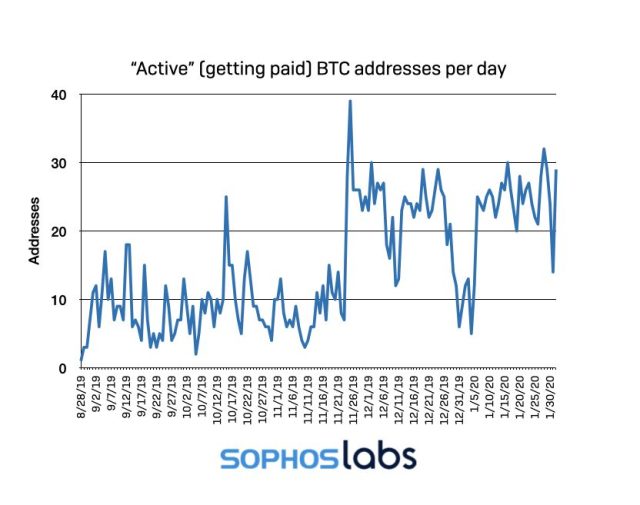
During the period between September 1, 2019 and January 31, 2020, we witnessed a series of unusual spikes in sextortion spam message traffic. As with many other types of spam campaigns, the sextortion messages came in relative short bursts instead of a continuous stream of messages. But these particular bursts made up a outsized proportion of the spam traffic we observed during the period observed. While sextortion made up an average of 4.23% of all our observed spam traffic over the period, there were five days when it made up over a fifth of all spam we observed. And the sextortion emails on just three days in October accounted for over 15 percent of all spam between September and January.
We observed around a dozen “spikes,” most of them during the autumn. These spikes usually lasted 1-3 days, and more than half of them happened on weekends (Friday, Saturday and Sunday). Another sign that the scammers behind these messages prefer to send their messages when their targets might not be at work: while the campaigns were largely low-volume during December, they picked up between the 24th and 26th. There were some outliers, however, including a spike on January 8 that consisted largely of a campaign with extortion messages written in German.
As with many spam campaigns, the sextortion messages were launched from botnets using compromised personal computers all around the world, with PCs in Vietnam providing the greatest single share (7%). Some of the messages demonstrated some new methods being used by sophisticated spammers to evade filtering software.
While we had seen previous campaigns use images to display the extortion demand in order to evade text detection, we found few examples of image-based obfuscation in September to January waves. Instead, the spammers used a variety of other techniques to hide the text of their messages from simple parsers:
- Breaking up the words with invisible, random strings
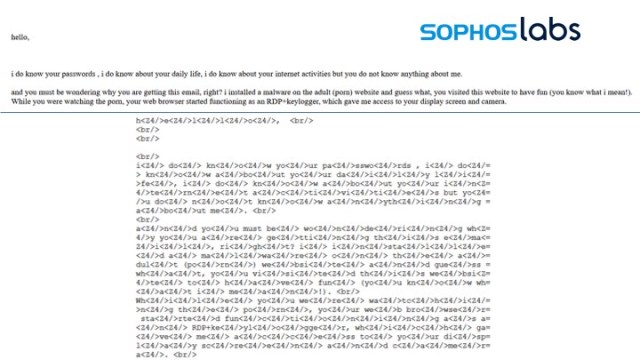
Top: message as seen by recipient. Bottom: Encoded text in message data - Using encoded non-ASCII characters (such as Cyrillic letters) that look similar to “regular” characters to humans, completely different when read by a machine:
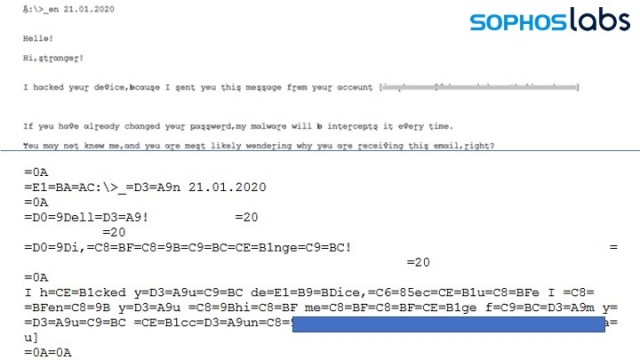
Top: message as seen by recipient. Bottom: Encoded text in message data - Using invisible white garbage text to break up the message text.
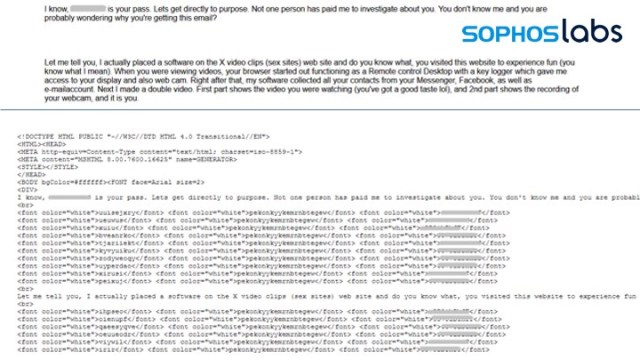
Top: message as seen by recipient. Bottom: Encoded text in message data - In one message (the example shown earlier in this report) the message text was “concealed” in HTML style tags outside of the body of the message.
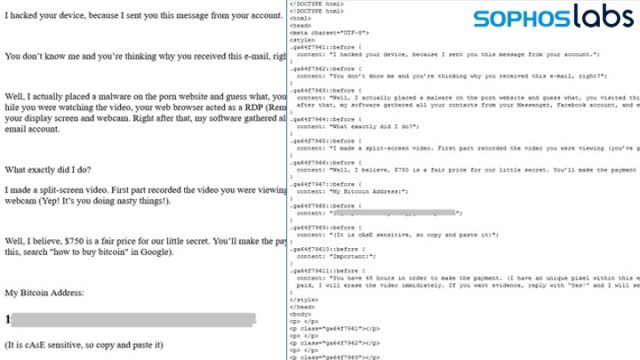
Left: Message as seen by recipient. Right: HTML encoding of message, showing content in “style” tags.
Cashing in on fear
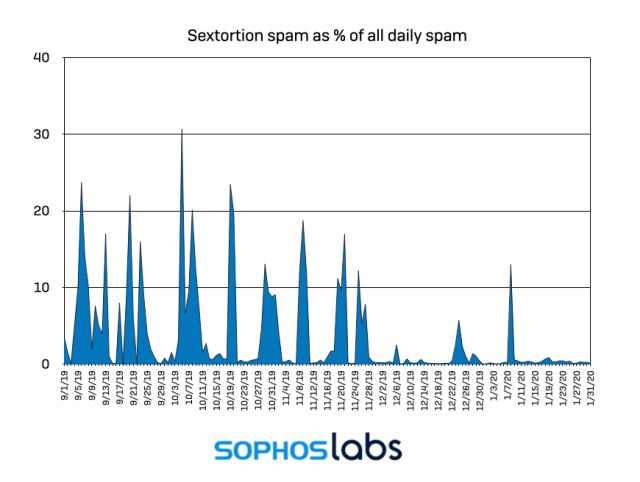
In addition to the often-obfuscated threat, each of these emails carried a Bitcoin wallet address for victims to use in directing payments. Clearly, the majority of these individual efforts to scare targets into paying was in vain—while we found nearly 50,000 unique Bitcoin wallet addresses in the sextortion messages we intercepted, only 328 received payments at any point in time until early February—meaning only a half a percent of each message volley convinced recipients to pay.
While a relatively tiny fraction of the total, these wallet addresses received more than 96 BTC, which is (or was) worth a few hundred thousand US dollars, depending on when we check the price of BTC/USD. Some of this activity predates the spam campaigns, however.
Looking at the payments made during the sextortion campaigns may give a more accurate picture of what they yielded. During the five month period, 261 of the wallet addresses received 50.98 BTC . Multiplied by the average of the daily price on the day the payments were made, that comes to $472,740.99, which is as close to the actual amount of victims paid as we can get. On average, the active wallets received 0.19534962 Bitcoin per address, or $1,811.27.
The operators regularly cycled through new wallet addresses with each new campaign.The average “lifespan” of all the addresses found within sextortion messages was 2.6 days before they disappeared from observed spam. The 328 “successful” wallets—those that received payments— had more extended lives, lasting 15 days on average.
Through our collaboration with CipherTrace, we were able to determine that the 328 Bitcoin addresses with a history of payments were connected to 162 clusters of addresses tied to individual Bitcoin wallets. While a majority of these wallets only had one address, there were 4 wallets that had more than 10 addresses from our list associated with them.
Let the BTC flow
Of the 328 “active” addresses we identified, CipherTrace connected 12 to online cryptocurrency exchanges or other wallet services. Some of the exchanges had been previously identified by CipherTrace as “high risk” exchange services with little in the way of the “know your customer” requirements, making them well-suited as cryptocurrency laundering points for criminals. These previously attributed addresses were not used in further tracing the flow of funds from the campaigns, because exchanges often combine customer funds together in their deposit pool—making it untenable to track specific blockchain transactions further.
The CipherTrace Inspector product identified 476 output transactions from the 316 addresses. The most frequent destinations for transactions were:
- Binance, a global BTC exchange (70 transactions).
- LocalBitcoins, another BTC exchange (48 transactions).
- Coinpayments, a BTC payment gateway (30 transactions).
- Other wallets within the sextortion scheme, consolidating funds (45 transactions).
- There were 54 transactions to addresses that could not be attributed—likely private non-hosted wallets.
It’s important to point out that the exchanges mentioned above (as well as other exchanges) are unknowing participants in these deposits of funds. Because of the way blockchains are designed, there is no way for exchanges to block deposits to their addresses.
Overall, the payments from sextortion wallets were distributed as shown below:
CipherTrace performed further analysis on the 316 addresses by tracing the other addresses connected to them by transactions, going out a maximum of 3 transaction “hops” from the original address. Of those addresses, 305 had at least one outbound transaction. The trace of those transactions revealed 7 distinct groups of address clusters within the group, tied together by transactions. In some cases, those clusters were connected to other criminal transactions:
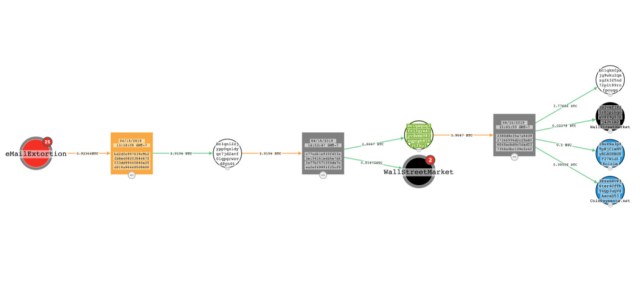
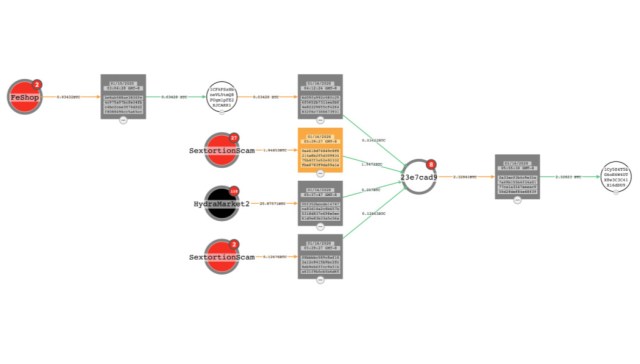
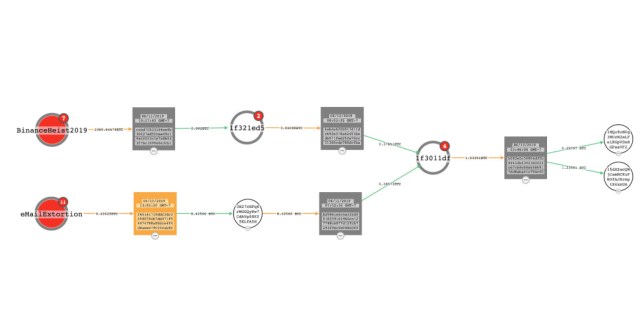
There were 13 addresses among the 328 passed to CipherTrace that did not have traceable outbound transactions. But for the remainder, whoever was behind the wallets did not let their cryptocurrency spoils sit for long. Based on the date of the first input (when the first extortion payment transaction occurred) and of the last output (when the last of the value of the wallet’s Bitcoin was drained) from each of the remaining 305 wallets, CipherTrace calculated an average “lifespan” of approximately 32.28 days.
Removing the most long-lived outlier wallets from the group—9 addresses that persisted for more than 200 days—the majority of the addresses had an average lifespan of 19.93 days. For 143 of the addresses, where there was only one input and one output transaction, the wallets were cashed out on average within 8 days—with the exception of two that were left untouched for over 100 days.
Where’s the money now?
Tracking where physically in the world the money went from these sextortion scams is a difficult endeavor. Out of the 328 addresses provided, CipherTrace determined that 20 of the addresses had IP data associated with them, but those addresses were connected to VPNs or Tor exit nodes—so they were not useful in geo-locating their owners.
Where wallet-emptying deposits occur can sometimes offer a hint to the location of scammers, because some exchanges restrict what Internet address blocks they can be accessed from. But even geographic restrictions on some of the exchanges used are ineffective for locating the people behind the wallets, much for the same reason—VPNs or Tor could be used to bypass IP-based restrictions to those exchanges. Most of the deposits went into global exchanges.
Given that some of the transfers were used to obtain stolen credit card data or other criminal services—probably including more botnet services for sending spam—the payouts from the sextortion campaigns are funding yet another round of scams and fraud. After all, even in the criminal world, you have to spend money to make money.
Sophos would like to acknowledge the contributions of analysts at CipherTrace, Inc. , to this report.
nina ogaard
Great article!
Abigail
I received hundreds of these messages with various Bitcoin wallet addresses over the last year or so. (Obviously did not send any money to them.) I’d be glad to forward a few of them if there is any type of investigation ongoing.
gallagherseanm
We’re always happy to get spam for research. If you can forward them with header information, that would be helpful. I’ll email you.
Chad
How could I forward the email I received yesterday to you?
Deborah Matthews
so i actually got one of these messages JUST LAST WEEK (april 2020)… and they were demanding $3000 in bitcoin… so for future reference, who (where?) exactly does one report these spammers to? thanks…
gallagherseanm
Reporting the source address doesn’t help, since these emails come from forged sources. You can report the Bitcoin addresses to https://www.bitcoinabuse.com/.
EF
Can send new email if you wish for research. Received today for 2000 bitcoin, but bitcoin abuse doesn’t recognize the address though Coinbase does.
DZ
I hesitate to do that. These people are using unique From Names, and fairly unique bit coin addresses. They know this stuff is old. So, they imagine that many are dead e-mails. But if you post on that site the From + bit coin address, they may have a database of what e-mail address got the From + bit coin. If they read it they know the email address is active. So, they may keep pecking at you like a chickens in a barn yard that gets ganged up by other chickens.
S Korsh
I just got one of these yesterday 4.22.2020. Just a few edits on it but now asking for $2000. Must be more expensive to run the scam now.
Rachel
I get these regularly, is it more helpful to offer the information to you for research or file a claim on the bitcoin abuse website or both?
P.C. LIU
I have got many of these but sadly i deleted them all.
I do remember some of them are not text but a email with a single embeded image.
Koşuyolu kiralık daire
This is awesome article. Thanks for share.
April
I just received one via text. Same scam?
gallagherseanm
It may be similar, but these attacks are copied by many actors.
BB
I received one via text today. I went on FTC and several have report the text route also.
Ann
I received one of these today. Here is what it said:
This is a copy of what was randomly sent to my cell phone using telephone [redacted].
“I require your complete attention for the next 24 hours, or I will certainly make sure you that you live out of embarrassment for the rest of your lifetime. I know pretty much everything about you. Your present facebook contact list, mobile phone contacts plus all the digital activity from previous 139 days. My spyware ended up being triggered inside your device which ended up logging a beautiful footage while you were masturbating by activating your camera. I have the full recording. In the case you think I ‘m messing around, just reply proof and I will be forwarding the particular recording randomly to 4 people you’re friends with. Would you be able to gaze into anyone’s eyes again after it? I doubt it… I’m going to make you a 1 time, non negotiable offer. Buy $ 1000 in BTC and send it to this address [redacted] (copy-paste-it) (If you don’t understand how, lookup how to acquire BTC. Do not waste my important time). Immediately after you send out this ‘donation’ (let’s call this that?), I will go away for good and under no circumstances make contact with you again. I will delete everything I have got in relation to you. You may proceed living your current regular day to day lifestyle with no concern. You have got 1 day to do so”.
Why people.do this is beyond me
gallagherseanm
For the same reason those “Nigerian Prince” emails lasted for so long–because enough people believe the messages to make them profitable.
Lisa
I received the same txt yesterday. It is being reported on FTC site and also on twitter. I wish this would be on the news to warn everyone.