Microsoft released 53 updates on Tuesday, classifying 18 as critical, while Adobe fixed 107 bugs, nearly half of which are also classified as critical.
By Jason Zhang
Two software titans threw a patch party on Tuesday, and the whole world was invited.
Microsoft released fixes for Windows and 14 other Windows-adjacent software packages, including an update to the Flash plugin for Edge. Most of these updates were classified as critical fixes to dangerous bugs. When Windows offers to reboot and install the patches, don’t hesitate.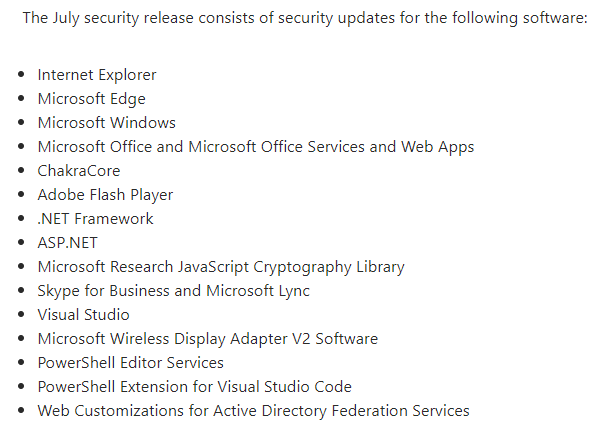
Meanwhile, Adobe released updates that addressed an astonishing 107 vulnerabilities affecting its marquee PDF and Flash packages, the first update in two months to Acrobat and Reader. The company also published updates for Adobe Connect and Adobe Experience Manager. From our analysis of the vulnerabilities, and testing in the lab, we’ve determined that the following six vulnerabilities show the most cause for concern. Fortunately, they’re all resolved in these Adobe updates that you can, and should, get right now.
From our analysis of the vulnerabilities, and testing in the lab, we’ve determined that the following six vulnerabilities show the most cause for concern. Fortunately, they’re all resolved in these Adobe updates that you can, and should, get right now.
Microsoft’s own guidance on the Adobe Flash update states that, as a workaround, if for some reason you are unable to patch, you could also just disable Flash entirely in Edge or IE by setting its ActiveX kill bit in the registry.
The patches that address Windows vulnerabilities updated a wide array of operating systems and service pack levels, but it also means there may be upwards of 20 variations on the patch for a single vulnerability. All told, Microsoft released 803 separate update packages, 237 of which address bugs in Windows.
The Adobe update details page lists nine categories of vulnerabilities that they address in these updates. Eight of those categories are considered critical, but the ninth category, of Out-of-Bounds Read, is only classified as “Important.” That said, it’s the only category that addresses vulnerabilities documented in 53 separate CVE reports. It’s a long list, almost too long to display on one screen.
Nearly all of this month’s Patch Tuesday bugs were reported by researchers through the Zero Day Initiative.
Sophos detection
In addition to generic exploit detection capabilities with Sophos Intercept-X, the following detection has been released to strengthen Sophos AV protection against those vulnerabilities which require attention, and the following signatures have also been added to the Sophos IPS to guard against these exploits:
| Sophos AV | Sophos IPS | Description |
| Exp/20185028-B | Sid:9000581 | FILE-PDF Adobe Reader CVE-2018-4957 Information Disclosure |
| Exp/20185040-A | Sid:1060814120 | FILE-IMAGE ImageMagick SGI File Handling Buffer Overflow |
| Exp/20185052-A | Sid:47129 | FILE-IMAGE Adobe Acrobat Pro malformed CEL heap overflow attempt |
| Exp/20185061-A | Sid:47139 | FILE-OTHER Adobe Acrobat EMF out-of-bounds read attempt |
| Exp/201812789-A | Sid:9000635 | FILE-OTHER Adobe Acrobat Pro EMF Alphablend memory corruption attempt |
| Exp/20185008-A | Sid:47127 | FILE-FLASH Adobe Flash Player malformed ActionSetTarget record information disclosure attempt |