Thanks to Dorka Palotay of SophosLabs for her behind-the-scenes work on this article.
Hindsight is a wonderful thing.
With hindsight, few of us would ever fall victim to ransomware: most ransomware attacks rely on talking us past at least one security speed bump…
…and those speed bumps sometimes seem very obvious after the event.
Nevertheless, even the most careful and self-confident of us – and all of us who haven’t been hit by ransomware – need to admit that there are times when we’ve behaved online in a way that ended well, but more by accident than by design.
In other words, we’ve all opened emails and attachments that turned out to be unwanted but didn’t lead to malware, only to wonder afterwards quite what it was about the email or the document that made us trust it.
Winning your trust with a pack of believable lies, especially technical lies, is known as social engineering, and that’s how most ransomware works its way in.
A recent spam campaign in Germany shows up the sort of techniques that cybercriminals think up: this one introduced a new strain of ransomware calling itself Goldeneye, arriving with not one but two attachments, a PDF file and an XLS (Excel spreadsheet):
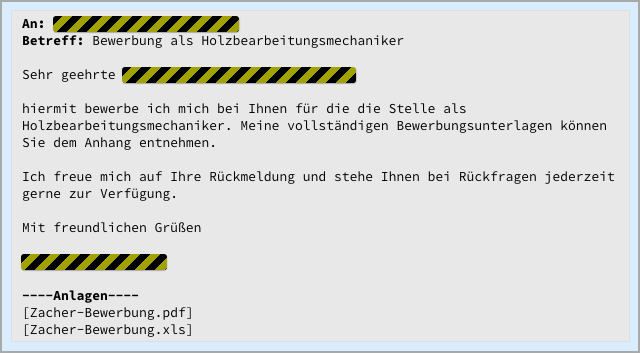
Even incautious users are worried about unexpected Excel files these days, which is presumably why these crooks included an unsuspicious, uninfected PDF file containing a polite job application (the word Bewerbung in the email subject means application), just to get the ball rolling:
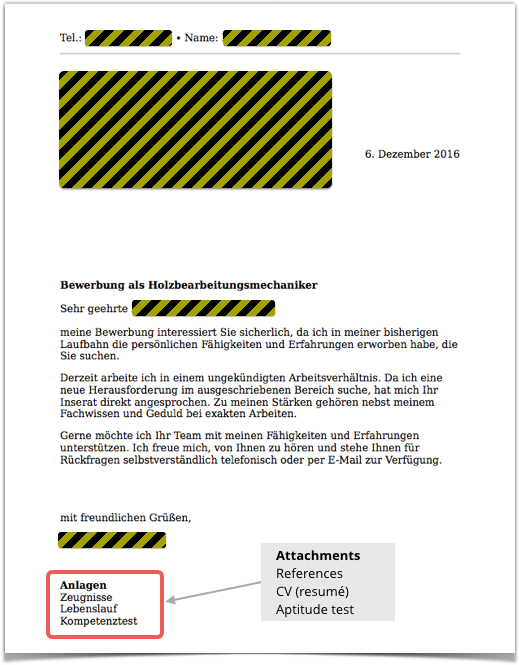
(We’ve redacted the details, because we assume that the crooks have stolen a real CV for verisimilitude, and we don’t want to name and shame the person whose personal information appears in the document.)
The second page includes a photograph of the alleged applicant, and the last page very politely points out that the Excel file contains the very details you might reasonably expect in a job application:
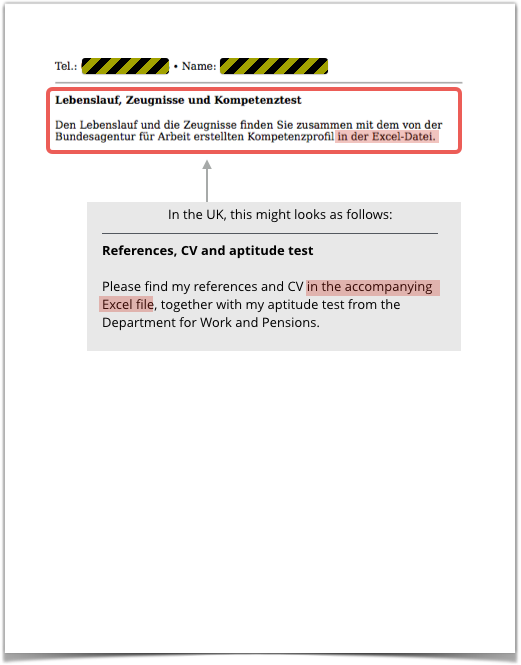
There’s no explicit demand to open the file, just an implicit suggestion that opening it, as any diligent HR person might do, will work out fine,
Simply put, the crooks are trying to make the email look like “business as usual”.
Even if you aren’t hiring right now, your company may be one of many that keeps the CVs of suitable applicants on file, so checking out their documents is not abnormal, and usually doesn’t lead to malware.
What next?
When you open the Exel file, you don’t see any personal information, but you do get a suggestion on how to bring up the claimed aptitude test information:
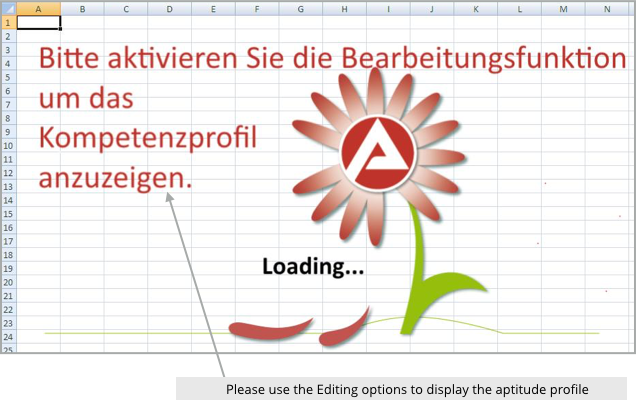
The crooks don’t openly ask you to do anything obviously risky, such “Enable macros” or “Turn off the default security configuration”, but they do encourage you to make a change to your Office settings, something that Excel will invite you to do because the file contains what are known as Visual Basic for Applications (VBA) macros.
The VBA programming language used in Office macros is a powerful system that not only allows a crook to control Word or Excel programmatically, but also to perform more general actions such as downloading an EXE file (Windows program) from the web, or saving data stored inside the Office file to disk as a program, and running it.
In other words, Office macros are potentially as dangerous as full-blown Windows executable files, so reducing security on the say-so of a spreadsheet like this one is a risky thing to do.
In fact, if you permit macros to run in this Excel file, you will quickly regret it: the VBA writes an embedded copy of the Goldeneye ransomware to disk and launches it.
You won’t see anything at first, but the malware soon starts encrypting the data files on your hard disk, leaving behind a series of files called YOUR_FILES_ARE_ENCRYPTED.TXT that tell you the bad news:
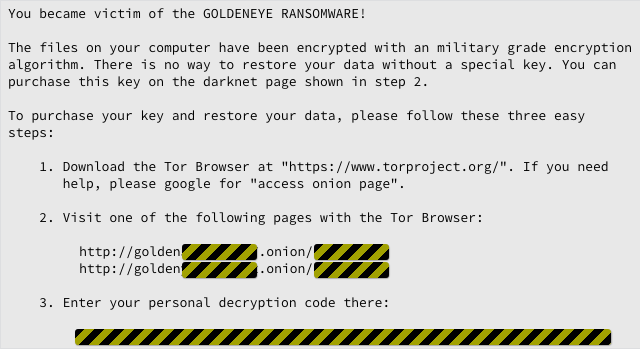
Most file-scrambling ransomware stops there, but Goldeneye goes into bat a second time, running a modified version of the Petya ransomware to encrypt the Master File Table (MFT) of your hard disk as well.
The MFT is the part of your disk that keeps track of which sectors belong to which files, making it vital to your hard disk:
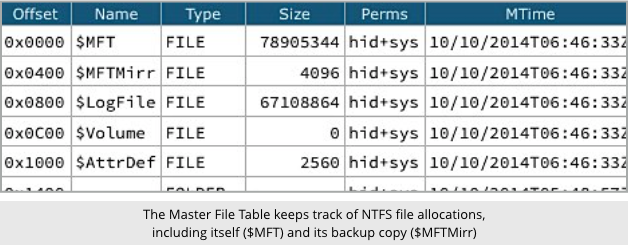
Without the MFT, your disk is like a whole library of books torn into a heap of individual pages and then thoroughly shuffled: the raw data is there, somewhere, but stitching it back together is so difficult as to be almost impossible.
Like Petya, Goldeneye reboots and pretend to be doing a disk check:
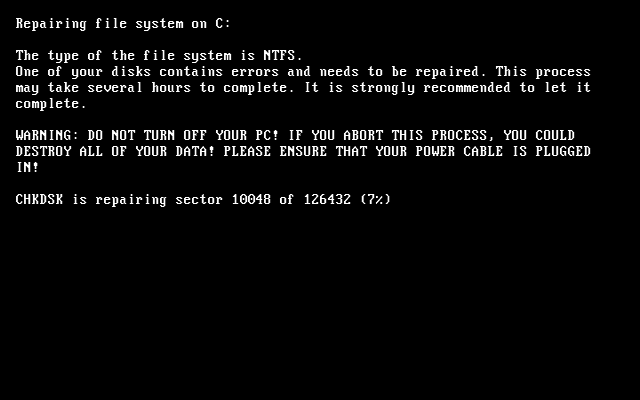
Once the “check” is finished, another reboot sounds the alarm with some dramatic ASCII art:

The skull flashes yellow and black to make sure you can’t miss it; when you press a key, you see a note almost identical to the abovementioned YOUR_FILES_ARE_ENCRYPTED.TXT:
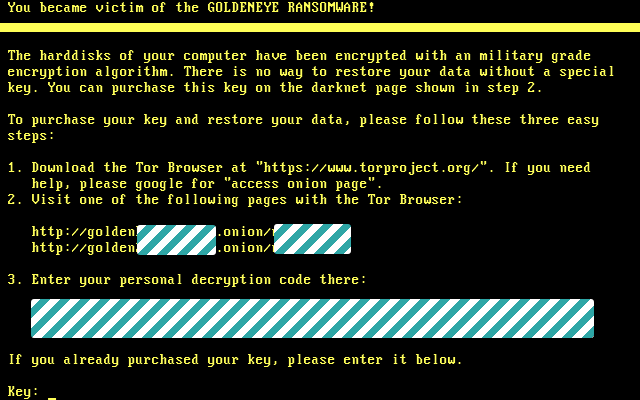
In case you’re wondering, given that we redacted the so-called personal decryption codes in the images above, the encryption is different for your files and for your MFT: the malware uses different algorithms and different keys each time.
In short, if you pay up to unlock your scrambled MFT so you can reboot into Windows, then, assuming the crooks actually send you the key…
…you’ll get back into Windows only to face the YOUR_FILES_ARE_ENCRYPTED.TXT pay page as well.
If you don’t have any backup, you get to pay up all over again.
Note. Sophos products block this malware as follows: Troj/DocDrop-PX, -QA and -QC (booby-trapped XLS files); Troj/Petya-AD, -AF and -AG (downloaded Goldeneye executables).
What to do?
When we checked, the crooks were demanding a fairly steep ransom of close to 1.4 Bitcoins ($1000) on each pay page, so a double-whammy Goldeneye attack could cost you $2000, and that’s if the crooks come through with the decryption keys:
As always, the best defence is not to get infected in the first place, so we’ve published a guide entitled How to stay protected against ransomware that we think you’ll find useful:
You might also enjoy our Techknow podcast Dealing with Ransomware:
LISTEN NOW
(Audio player above not working? Listen on Soundcloud or access via iTunes.)


wally
As I read this I got thinking…
With Goldeneye or similar beast that requires a trojan download, what would be the sequence of events if you went offline before opening. Would there be any flags such as a VB error?
After deleting the message could you safely connect to the net again; and if not, would delete, reboot, connect be okay.
Not hoping to try it, but since I’m not familiar with the under-the-hood of these things, I wondered what precautions might offer protection.
Paul Ducklin
There are numerous problems with relying on what you might call a “precautionary disconnect” to protect you, mainly that it gives a false sense of security. That’s because:
You can easily suppress any macro errors (it’a a feature built into the VBA language).
The VBA could be what’s called a dropper (where the malware executable is stored as a data array inside the macro itself) rather than a downloader (where the malware is fetched via the network).
The VBA program itself could be the malware, with no dropped or downloaded file needed.
For example, here’s some ransomware that is written in JavaScript and entirely self-contained. That’s not quite the same as VBA but it’s similar:
https://nakedsecurity.sophos.com/2016/06/20/ransomware-thats-100-pure-javascript-no-download-required/
Anonymous
Wait if the ransomware dosen’t connect to it’s command server how does it get the encryption key? Does it already have it in is code?
Paul Ducklin
Ransomware doesn’t *need* to call home to work. If it has a public key in it, then it can generate a random key to do the encryption, then encrypt the random key with the public key, and then only the private key can decrypt all the data. (The crooks keep the private key back at head office.)
The ransomware needs to convey the final public-key-encrypted lump of data to the crooks, and in this case it’s done by printing out a text-encoded blob. From the boot screen you need to type it by hand, but the end result is the same: you send it to the crooks and they use their private key to decrypt the file decryption key and that it what you buy.
Paul Ducklin
To explain. You may be wondering, “Why all the shenanigans involving a random file encryption key that’s then encrypted with the public key, which can then only be unlocked by the private key? Why not just encrypt the files with the public key directly?”
Answer: public key encryption, e.g. RSA, is zillions of times slower than conventional encryption, e.g. AES, and is typically used to encrypt only a few dozen bytes at a time. So the hybrid approach of a random symmetric key for the bulk encryption followed by the public key to encrypt the regular key for secure transmission is used almost universally in real-world encryption software, from HTTPS to ransomware.
Max
Wait the ransomware need to connect to a command server to ket the encryption key correct?
So if you lauch a ransomware on a system without internet what will it do?
And if you cut the connection before it can contact a command server does it just stop or keep trying until it get something?
Eric Valenzuela
Some ransomware will have both a builtin, default set of encryption keys, and the ability to call out to a CnC server. In that case, it may be easy to decrypt using the known encryption keys, but you have to have had the foresight (or luck) for that to have happened.
Georg
Hi Paul
does your Note
“Note. Sophos products block this malware as follows: Troj/DocDrop-PX, -QA and -QC (booby-trapped XLS files); Troj/Petya-AD, -AF and -AG (downloaded Goldeneye executables).”
mean that Sophos Virus Scan with an updated Virus-Database is able to block GoldenEye?
Greetings from Germany
Paul Ducklin
Yes. Here’s my laboratory Mac doing a scan of the samples we used to generated the visuals for this article. (Those filenames aren’t how the samples appear in the wild, of course :-)
duck@labmac:~/goldeneye$ sweep cunning*
Sophos Anti-Virus
Version 9.5.4 [Darwin/AMD64]
Virus data version 5.34, November 2016
Includes detection for 12413025 viruses, trojans and worms
Copyright (c) 1989-2016 Sophos Plc. All rights reserved.
System time 15:36:08, System date 09 December 2016
[. . .]
>>> Virus 'Troj/Petya-AF' found in file cunningly-disguised-EXE.exe
>>> Virus 'Troj/DocDrop-QA' found in file cunningly-disguised-XLS.xls
[. . .]
Keith Murphy
“In other words, we’ve all opened emails and attachments that turned out to be unwanted but didn’t lead to malware, only to wonder afterwards quite what it was about the email or the document that made us trust it.”
I guess this is something I will never understand. If I ever get an unexpected email, I contact the sender or delete it. If it is urgent or important, they should be calling me anyway, but maybe I am just old-fashioned.
What really amazes me is how much of this gets past email anti-malware scanners. It is incredible the things I have seen Google let through to my gmail account.
Paul Ducklin
Unfortunately, many people these days are doing jobs that pretty much necessitate opening emails from new senders – ask anyone in HR when there’s a recruitment push going on; anyone in sales (especially in months divisible by 3 :-); anyone in order processing; anyone in accounts payable (in a company that pays its bills, of course); and so on.
As for Gmail filtering, I can’t help you there. I don’t use Gmail.
As for dedicated email filtering products like, ahem, Sophos’s, we aren’t just looking for spam, but also analysing attachments so that even if a known sender submits something, we take it apart to see [a] if it’s malware or [b] if it meets policy. (All companies want to block malware; many companies have other blocklisting requirements as well, either for reasons of good taste, employee safety, regulatory compliance or simply because, hey, it’s their server and life’s too short, to put it in technical terms :-) As indicated above, we should spot both the XLS files and the EXEs they would download if you were to open them and authorise macros.
Dave Irwin
I have encryption turned off ,can they still encrypt my files ?
Paul Ducklin
Ransomware does its own encryption. So whether you are using Windows encryption or not typically doesn’t matter. If you are, your files just end up encrypted twice, but you only know one of the decryption keys :-(
Jim
A huge red flag exists that SHOULD prevent people from opening: the extension of the Excel file has to be either .xls or .xlsm. Everybody should have extensions turned on (c’mon, Microsoft, why isn’t this the default?). And, nobody should open one of those from email.
I know I personally do send some xlsm files via email; they’re part of the job. But, I always precede the email with either a phone call saying it’s coming shortly, or (if that’s not practical), an email warning that it’s coming.
procrash
Hi,
just a comment. I analyzed the stuff as well. It doesn’t seem that the Trojan is downloading anything after the excel spreadsheet activation. Where do you have this information from? It is wrong. Everything seems to be self contained in the email.
Another question. Is it really true that the victims have to pay the ransom twice? I thought the ransom guys send you an additional file decrypter when paying the ransom?
Paul Ducklin
Yes, the XLS file is a dropper (writes the EXE file from data stored in the XLS itself, not from data downloaded from somwhere else). Thanks for your comment…I’ve now made that fact clear in the article.
As for the double ransom…I suppose the crooks could give you two for the price of one. To be honest, I haven’t spent BTC 1.4 to find out (and the problem with “finding out” is that you can still only talk about your own experience, not what might happen to anyone else).
procrash
Thanks Paul. The ransom guys put my pseudo name in the decryption executable. Unbelievable. Bastards!
Today I received it. If you want I can forward it to you as well…