It doesn’t matter how sophisticated your software is, users will always find a way to fail you.
It took DARPA smarts, government money and a cadre of dedicated developers and academics to build Tor, a weapons-grade privacy tool that’s like an impregnable lock for your website and browser.
And users keep finding ways to leave the keys under the mat…
…under signs saying “secret key under mat”.
Luckily, Sarah Jamie Lewis is on hand to dig them out of their self-made holes. Lewis is a Dark Web crusader on a mission to make the internet’s anonymous annex live up to its billing.
She scours the Dark Web with her OnionScan tool searching for those signs, welcome mats and keys.
She cares too much about anonymity for naming – but she’s not above a bit of shaming.
Today Lewis aimed her shame-o-matic at “Mr. [redacted] a European application developer” who entertains a sideline selling drugs on the Dark Web.
It wasn’t that she was upset about his illegal activities mind you, it was his bone-headed attempt to set up a Dark Web site that attracted her Twitter-ire.
The business website has his full name and full portrait picture of him…this one really isn't fair.
— Sarah Jamie Lewis (@SarahJamieLewis) October 18, 2016
Lewis explains in her latest Dark Web Diary that “Mr. [redacted]”‘s Dark Web sideline was exposed by his web server’s leaky server-status page:
… I present the case of Mr. [redacted] a European application developer who has taken it upon himself to sell drugs on the side.
… for what ever reason, he hosts the site for his newly founded application development business on the same server as his drug business.
This means the server-status leak not only exposes the location of the server hosting the drug advertisement. It also points directly to the identity of the man behind it all.
Such leaks are nothing new – I reported on leaky server-status pages on regular sites in 2012 and on the Dark Web earlier this year – but they continue to be a problem.
Server status pages are generated by the Apache web server’s mod_status module to help people understand how their sites are performing. Leaks occur when the pages are inadvertently made available to the rest of us.
On an ordinary website, a server-status page will expose any private data that’s contained in the URLs that its users are visiting, bypassing the protection of HTTPS. On rare occasions, that private data can even include users’ session IDs and passwords.
On Dark Web sites things get far more serious.
If you run a Dark Web site and a regular website on the same server, as “Mr. [redacted]” and many others do, then both addresses will appear in that server’s server-status page, like this:
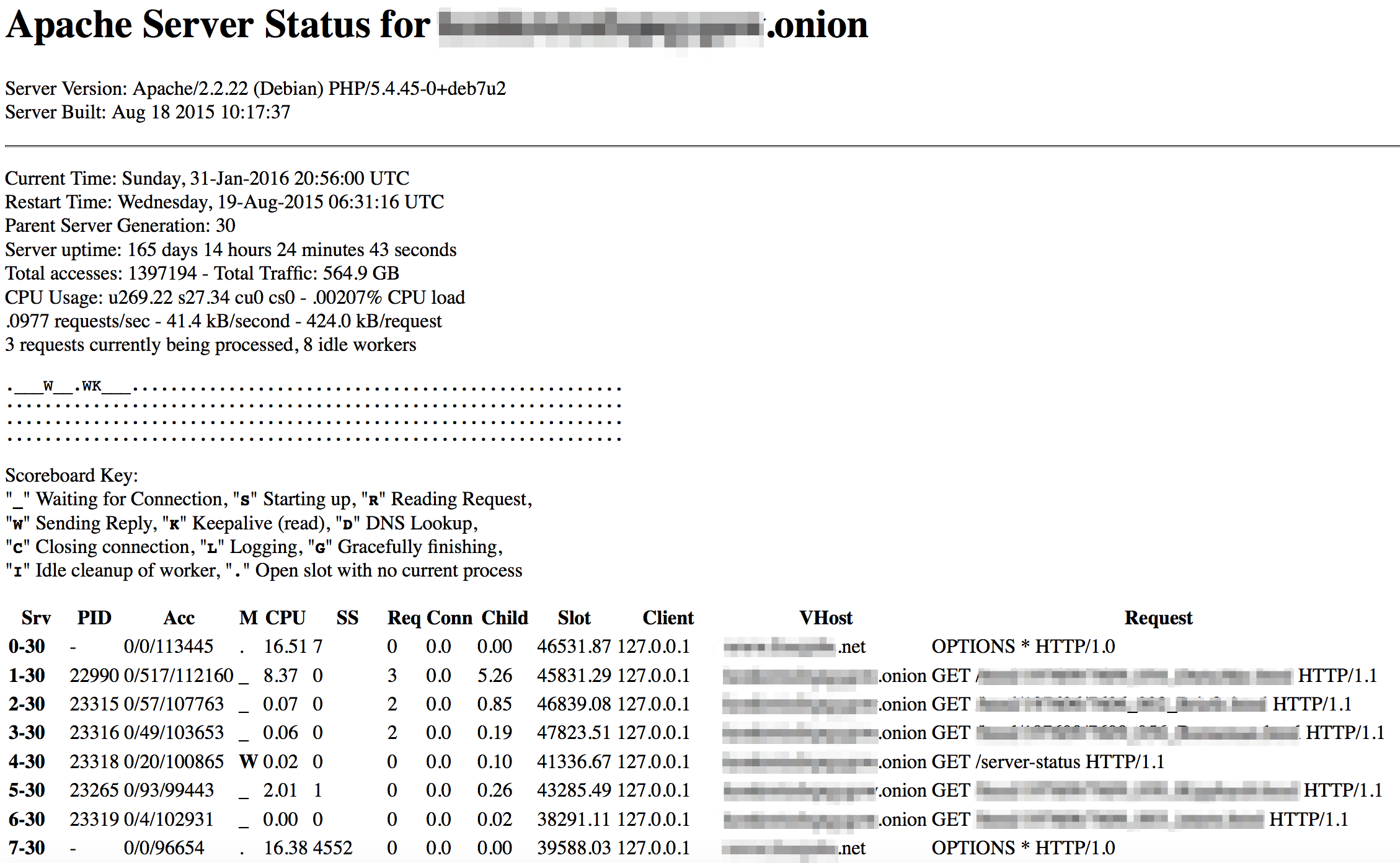
In the screenshot above you’ll see two addresses listed under VHost, the hidden site ending in .onion and the regular site ending in .net.
The regular website isn’t anonymous – you can find its IP address and location easily. Since it shares that IP address and location with the Dark Web site on the same server, the Dark Web site is no longer anonymous either.
And if you think that’s not giving law enforcement enough to go on already then you can always do what “Mr. [redacted]” did and put your name, address and photograph on the regular website too for good measure.
Thanks to a quirk in the Apache server configuration, leaky server-status pages are actually much more common on Dark Web sites than they are on regular sites.
By default, Apache server-status pages are kept away from prying eyes and are only visible to users on the localhost machine – the machine the server is actually running on.
Exposing a server-status page on the regular web therefore takes some effort – you actually have to get into the configuration and screw it up.
On the Dark Web the opposite is true – your server-status page is exposed unless you get into the configuration and fix it.
That’s because the Tor daemon (the software that makes your website ‘Dark’), runs on localhost so your website receives all of its traffic as if it’s coming from localhost, affording everyone the privilege of being able to view your server-status page.
Lewis’s regular Dark Web scans show that about 6% of hidden services are exposing some server-status data:
I have been on a vendetta of sorts since the beginning of 2016 to try and reduce the number of hidden services exposing mod_status.
Sadly, the needle has not moved much and still, as of the time of writing this article, 6% of hidden services expose some level of information through mod_status.
If you’re running any kind of website using an Apache web server I suggest you turn off mod_status unless you know you need it.
If you’re running a .onion site and you and your users are expecting to be anonymous then you probably owe it to everyone to read the manual, and don’t leave the key under the mat.

Anonymous
Double face palm