Here’s a good guess: a month ago, you’d never heard of a company called Mossack Fonseca.
Here’s another guess: you have now.
You know they’re a legal and trust services company, that they’re headquartered in Panama, that they were founded in 1977, and that they recently suffered the mother of all data breaches.
Actually, from what we now know, the company didn’t so much suffer a data breach as endure one.
According to a story by Forbes, the stolen data has been available to “more than 400 journalists” for at least a year, and arrived in a series of “humongous data troves that came in incrementally.”
Apparently, 2.6TB of data was stolen in the breach, which would probably work out somewhere between 3,000,000 and 300,000,000 printed pages, assuming you could feed in the paper fast enough.
No one did feed in any paper, of course: the stolen data was organised digitally in the cloud, where journalists with the right credentials, literally and figuratively, could access it.
Printed or not, the breach has gone into history as The Panama Papers.
Damage control
Mossack Fonseca, as you can probably imagine, has published dozens of damage-control articles and FAQs, creating a special website called mossfonmedia.com for the purpose.
As an almost amusingly ironic aside, if you try to visit this site securely using HTTPS, you’ll get a web certificate error thanks to a self-signed certificate that expired more than a year ago:
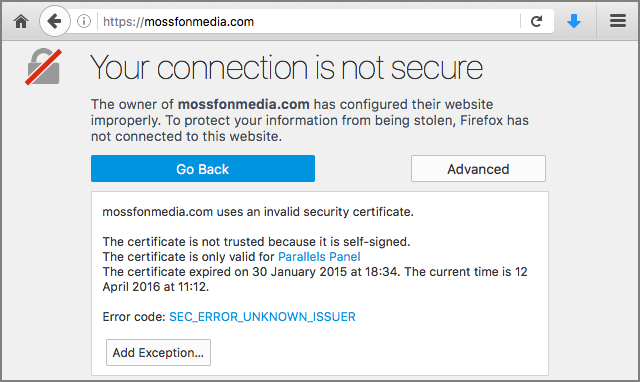
If you ignore the security warnings, just as Mossack Fonseca seems to have done in a more general way for the past year or two, you’ll find plenty of reading material.
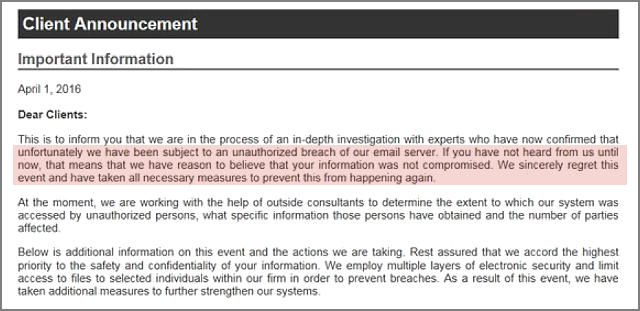
But the only official comment we’ve seen on the breach itself is this one, published by Mossack Fonseca shortly after the stolen data was first publicly used to name and shame some of the company’s high-profile customers:
Unfortunately, we have been subject to an unauthorised breach of our email server. If you have not heard from us until now, that means we have reason to believe that your information was not compromised. We sincerely regret this event and have take all necessary measures to prevent this from happening again.
Is this likely?
With 2.6TB of stolen data, apparently including paperwork right back to 1977 when the company was founded, presumably now digitised and stored in some sort of content management system (CMS), it’s hard to imagine how an email server breach alone could have led to a compromise on this scale.
If it’s unlikely, why try to blame what sounds like a single, limited breach?
You might think that the obvious answer is that Mossack Fonseca is trying to hide something, but that’s unlikely too. (From the size of the breach, there doesn’t seem to be anything left to hide.)
The problem with a truly enormous breach, especially if it took place right across your network over an extended period without anyone noticing that anything was wrong, is that you may never be able to figure out exactly what happened.
After all, if you didn’t notice at the time, you probably weren’t collecting the sort of log data that would let you notice, so you won’t have the evidence you need to help you work backwards to the cause.
And even if you do have log data, but you didn’t keep your eye on it at the time, you may never know how accurate it is, because the crooks might have suppressed it at key moments, or tampered with it, or you might have been collecting the wrong stuff.
What happened?
We can still only guess what happened.
We know from Mossack Fonseca’s official statement that their email server was definitely hacked, so we can be sure that one of the company’s critical externally-facing servers was insecure.
Finding other security holes is unsurprising, and equally disappointing, but doesn’t mean that any now-known holes were used, or even needed, for the thieves to get in.
Nevertheless, as we suggested in a recent article, a compromised mail server, or even a single compromised email account, could have been enough of a crack in the defences to let crooks run rampant inside the network without any further hacking.
Your email email server isn’t the whole castle, but it probably contains the keys to the castle for any crook who cares to take the trouble to look.
Passwords and password reset links, for example, are often sent by email; so are account details; contact details of IT staff who can help if you get stuck; handy organisational charts and internal phone directories; login information for newly created accounts; the results of security audits (a lot quicker than probing for vunerabilities yourself); and so on.
All in all, the goose that lays the golden eggs of social engineering.
💡 LISTEN NOW: Increasing your resilience to social engineering ►
Having said that, a company called WordFence recently looked at two other important parts of Mossack Fonseca’s server infrastructure.
The company’s main website uses WordPress; according to WordFence, the WordPress setup included a buggy plugin that could be used to get unauthorised access.
(Buggy WordPress plugins often get forgotten when the main WordPress installation gets patched, leaving the whole server at risk of a complete hack.)
WordFence also noticed that Mossack Fonsecsa’s customer portal, where exactly the sort of data revealed in the breach was stored, was running a long-outdated version of Drupal.
Indeed, the Drupal version noted by WordFence was 7.23, which predates by some distance the notorious Drupal 7.32 patch dating back to October 2014.
The Drupal 7.32 patch was notorious because crooks almost immediately used the 7.32 update to figure out which holes had been patched using the patches as a sort-of instruction manual for how to break into as-yet-unpatched servers.
According to Drupal, attacks using the newly-disclosed hole started “within hours” – a hard timeframe to beat, given that Drupal doesn’t have an automatic updating process, and even the keenest sysdamins sometimes need to sleep.
What to do?
In articles of this sort, we usually finish off with list of tips you can try.
This time, we’ll just point out that, however the Panama Papers were actually breached, it looks as though Mossack Fonseca missed out on the very basics of server security, by not closing known holes that were already part of the crbercriminal armoury.
So we’ll leave you with the pithy words of Naked Security’s Mark Stockley:
The answer to, “What happened?” is, “We don’t know.” But they’ve got a vulnerable plugin that lets you open a root shell and their web server is on the same network as their email server, so it could be that. Same lesson as Sony Pictures: just do the stuff you know you should be doing.
Read Similar Articles
4 Comments
Comments are closed.

Sprtye
Of course it could happen.
I’ve dealt with many small businesses who demand communication:
with unencrypted email or with some personal gmail, hotmail or worse yet a Yahoo mail account.
Trying to deal with these people is a real pain as one must copy documents and mail or physically take them the business in question.
Then they scan these documents and put them on a networked pc !!?!!?!!
Paul Ducklin
Scan them on one of those combo printers that keeps temporary files on a FAT-formatted hard disk…who know’s what’s still on it when it gets sent back for servicing.
treFunny
Work done after hours for updates/patches is the most important… sadly very few c-level execs understand this, they just want teh internetz to work.
Mahhn
The sad part is that the breach is getting press, but the crooks that were exposed are not, least not in the US. SNAFU.