Once a threat actor is on an endpoint, EDR solutions are often the only obstacle between them and their objective – whether that’s deploying ransomware, installing malware, accessing data, or launching further attacks.
As a result, threat actors regularly look for ways to disable security products: escalating privileges if necessary to try to kill processes and services, running EDR killers, and a host of other techniques.
Tamper protection – a mechanism designed to stop threat actors from interfering with security products, usually enforced by a kernel-mode driver – is therefore a critical part of any security suite, and many vendors, including Sophos, have developed some form of it.
In line with our previous efforts to provide transparency around our kernel drivers and content update architecture, and our commitment to CISA’s Secure By Design initiative, we wanted to briefly explain our tamper protection feature and how it works.
What does tamper protection do?
As the name suggests, Sophos’ Tamper Protection is designed to prevent manipulation, either by unauthorized users or malware, of the Sophos product. It’s an added, but critical, protection on top of what we consider to be our main role: defending the operating system and its applications – and, by extension, users.
Tamper Protection is enabled by default; Sophos aims for secure-by-default configurations and Tamper Protection is no exception. While it can be turned off by an authorized user, we encourage users to only do so when they need to change the local Sophos configuration or uninstall an existing Sophos product. Secure defaults are an important design principle, as not all organizations have the time or expertise to lock down their environments – creating opportunities for attackers.
Crucially, only a Sophos Central administrator can turn off Tamper Protection, and must have the necessary password, which is generated automatically by Central and is only accessible to authorized users with appropriate security roles and multi-factor authentication (MFA), such as a passkey or an authenticator app. By design, no local or domain administrator can override this, or turn off Tamper Protection unless they’re also a Sophos Central administrator and have the unique device tamper protection password.
Our philosophy here is that changes to Tamper Protection and threat protection policy should not be made by the same accounts used for routine IT management. Instead, we support role-based administration, enabling the separation of day-to-day IT from critical security controls.
Tamper Protection prevents the following:
- Changing on-device settings for threat protection, including on-access scanning, suspicious behavior monitoring, web protection, and Sophos Live Protection
- Disabling Tamper Protection
- Uninstalling the Sophos agent software
- Reinstalling the Sophos agent software
- Stopping Sophos processes
- Stopping Sophos services
- Changing Sophos service configuration
- Deleting or changing Sophos files or folders
- Deleting or changing Sophos registry keys.
Closing the gaps
We’re conscious that threat actors are constantly looking for new ways to interfere with security products. For instance, updates or reinstallations can lead to protections being temporarily disabled, providing a gap for attackers to get a foot in the door and try to disable tamper protection systems. With our integrated approach to endpoint protection, threat engines, and MDR services, we maintain a unique end-to-end view of modern attacks, feeding insights directly back into development.
Moreover, with everything we build, our objective is security by design – including update mechanisms and Tamper Protection. So, for example:
- We deliberately don’t use MSI for endpoint installation or updates. Instead, Sophos Endpoint powered by Intercept X uses a proprietary update system designed to prevent interruption of protection
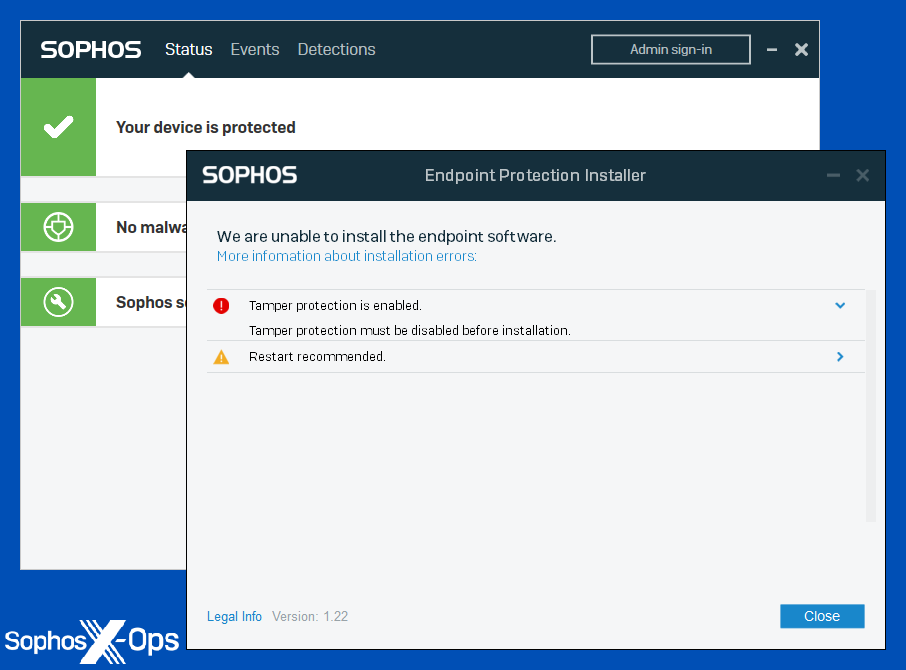
- As noted above, Tamper Protection is on by default, and remains active during updates, upgrades, and downgrades. Its protection extends to processes, services, software components, configuration files, registry keys, and unauthorized uninstallation and reinstallation
- Component updates occur in parallel, with existing components handling operations until handoff is complete – resulting in zero downtime in protection throughout the update. Core drivers and services only upgrade via reboot, eliminating runtime tampering risks.
Figure 1: Sophos Tamper Protection prevents unauthorized upgrades/downgrades—even from other Sophos installers
However, we never assume that our defenses are perfect. We have participated in an external bug bounty program since December 2017, and we regularly test our Tamper Protection through internal engineering reviews, external red-teaming, and real-world threat intelligence. This is part of our security investment: continuously improving the parts of our systems that real attackers might try to exploit.
Conclusion
Our aim is to ensure the entire protection and update surface resists tampering, even from attackers with full system access.
Effective tamper protection must assume that attackers have administrative rights, understand how your security products work, and will exploit any predictable gap. Sophos Endpoint is designed to resist such attempts without relying on temporary exceptions or post-failure recovery. Protection remains active throughout all operations, including updates. This represents our broader Secure by Design approach, where system integrity takes priority over deployment convenience.